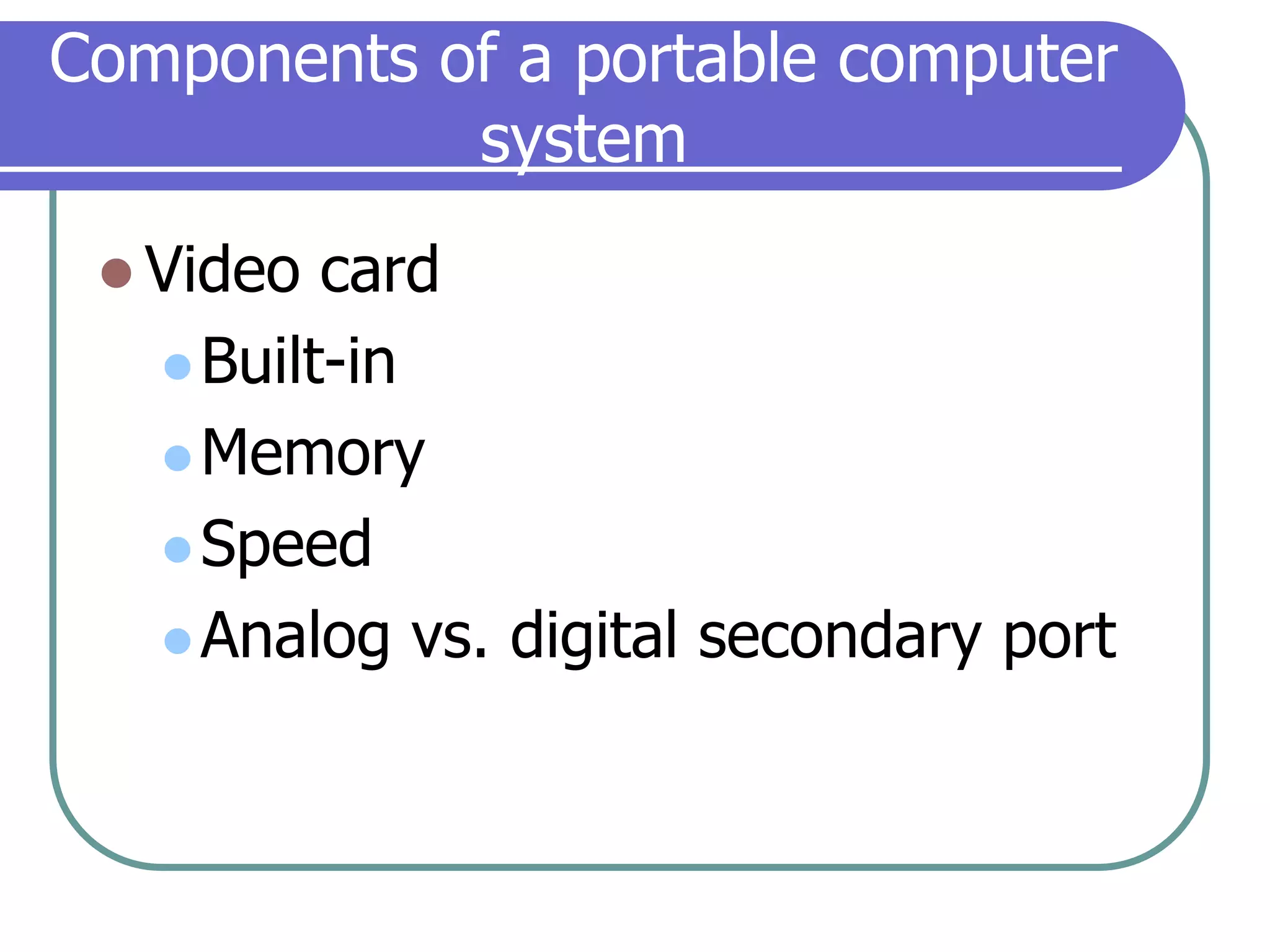
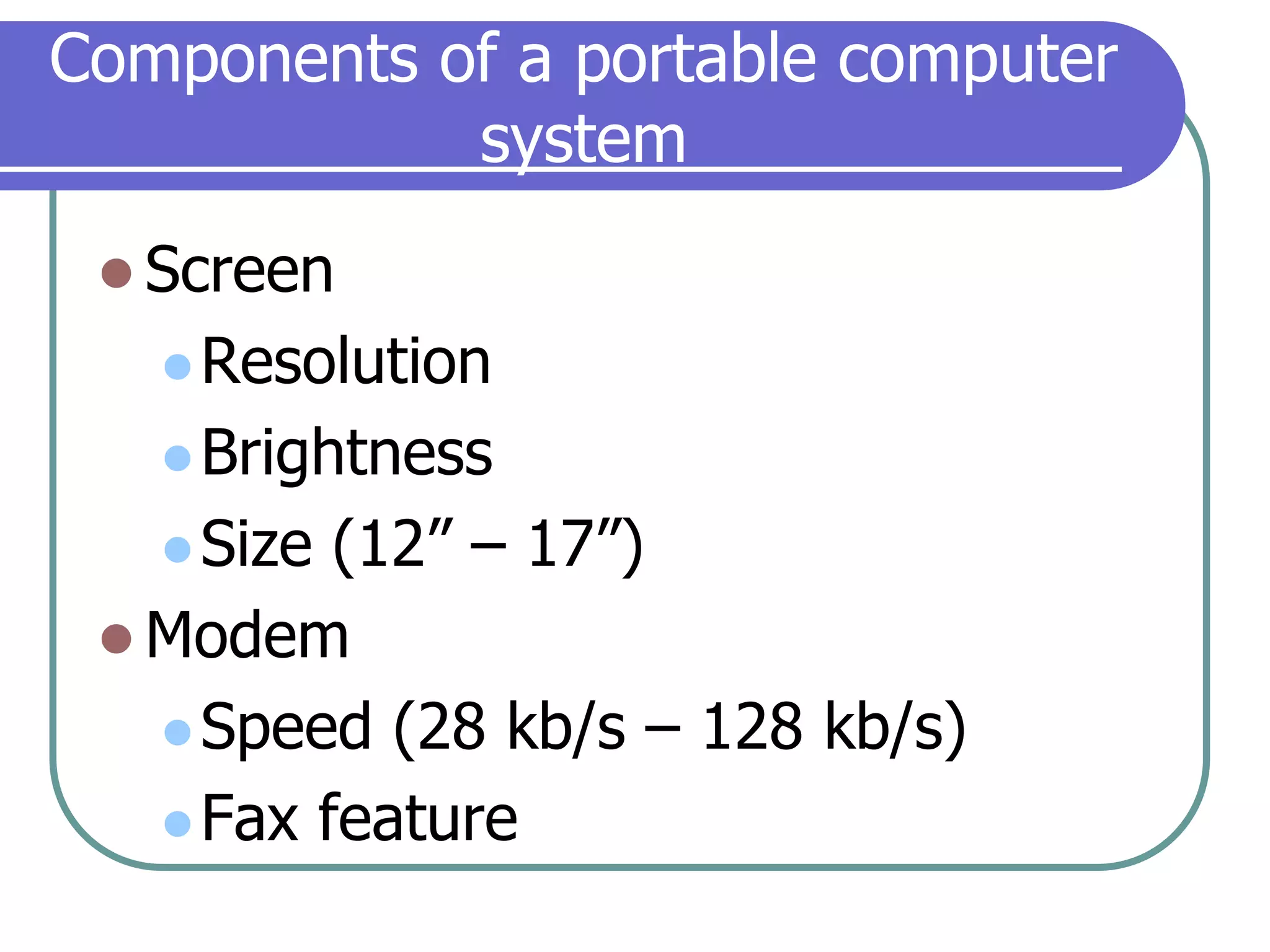
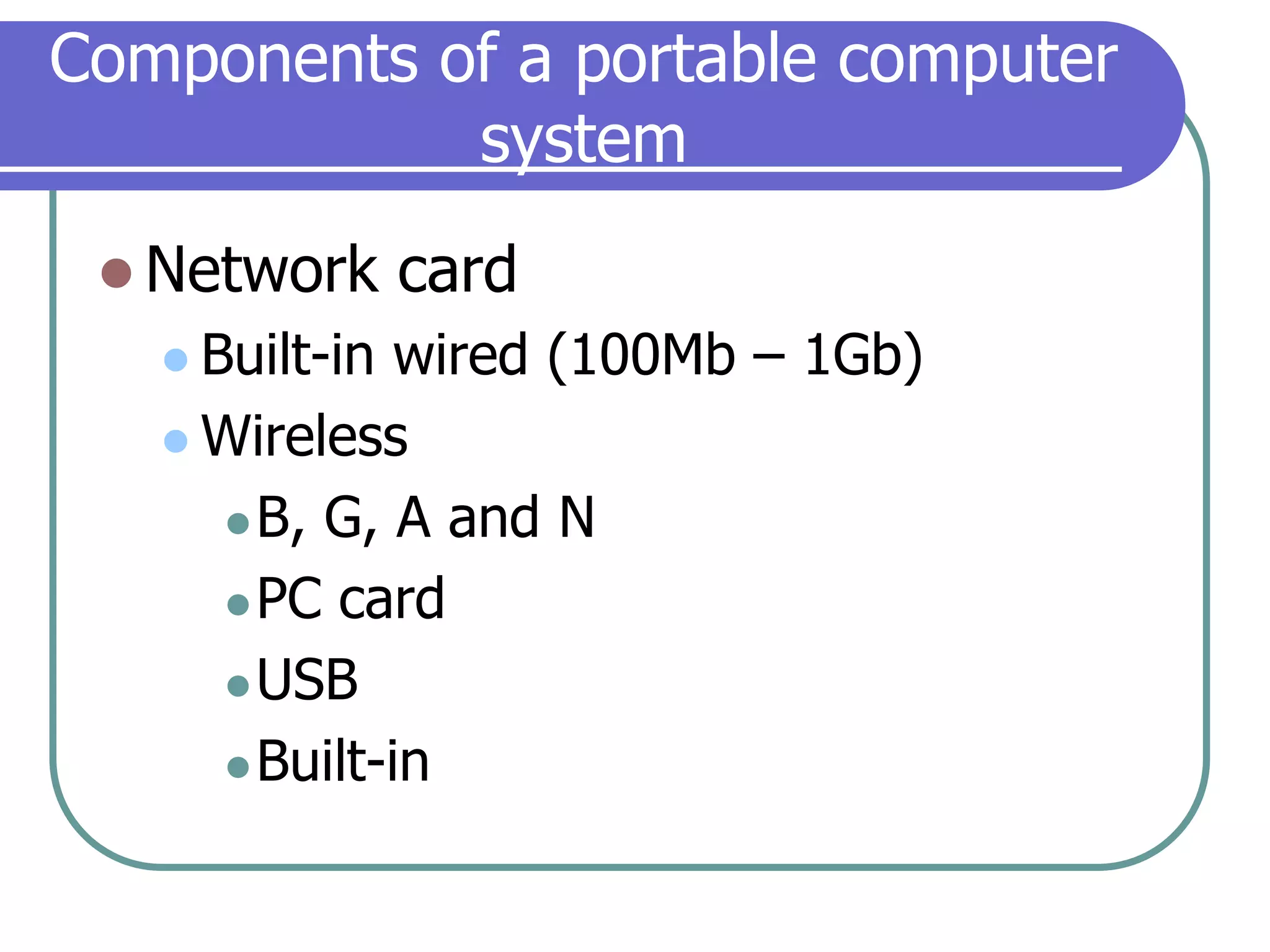
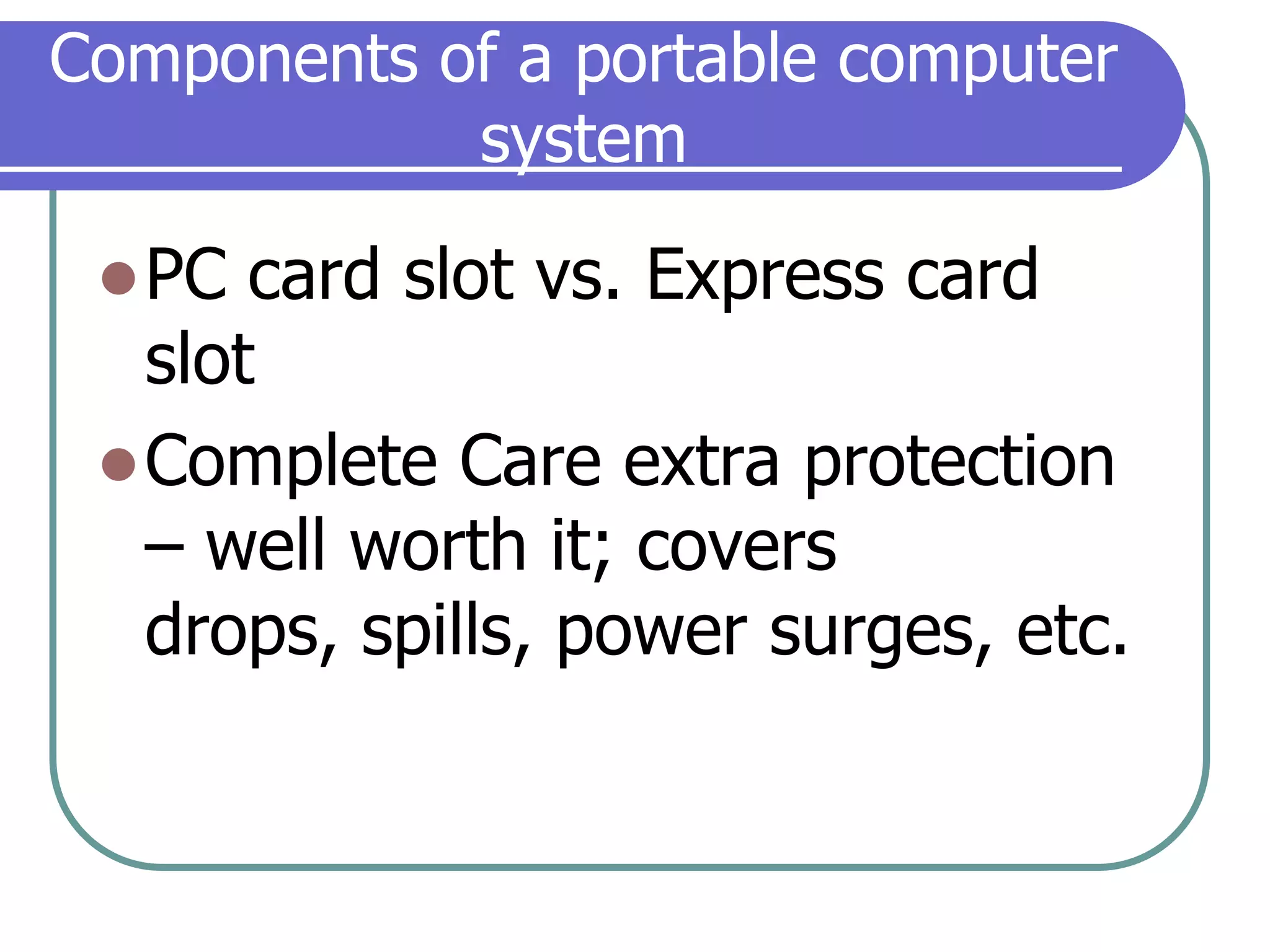
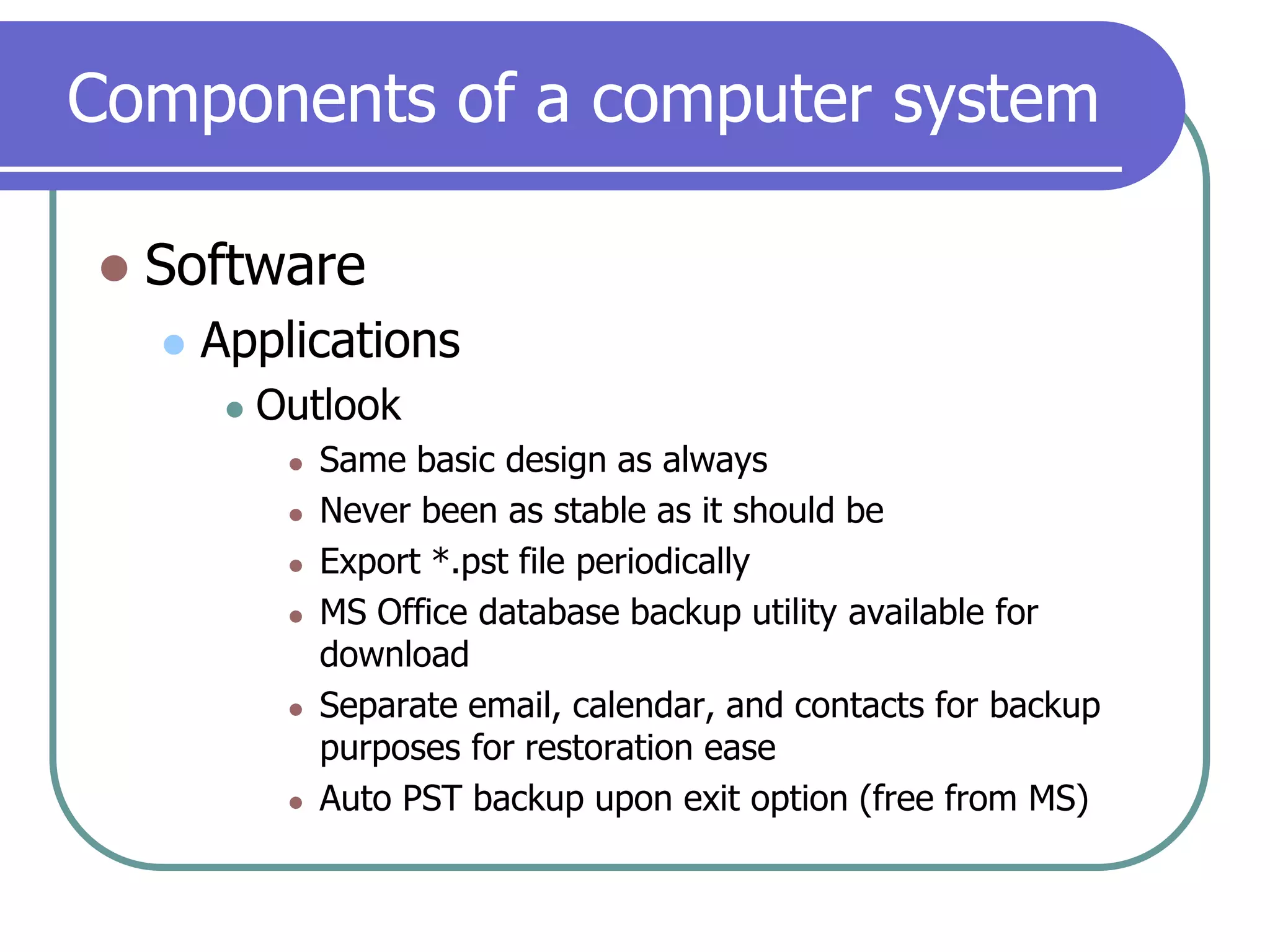
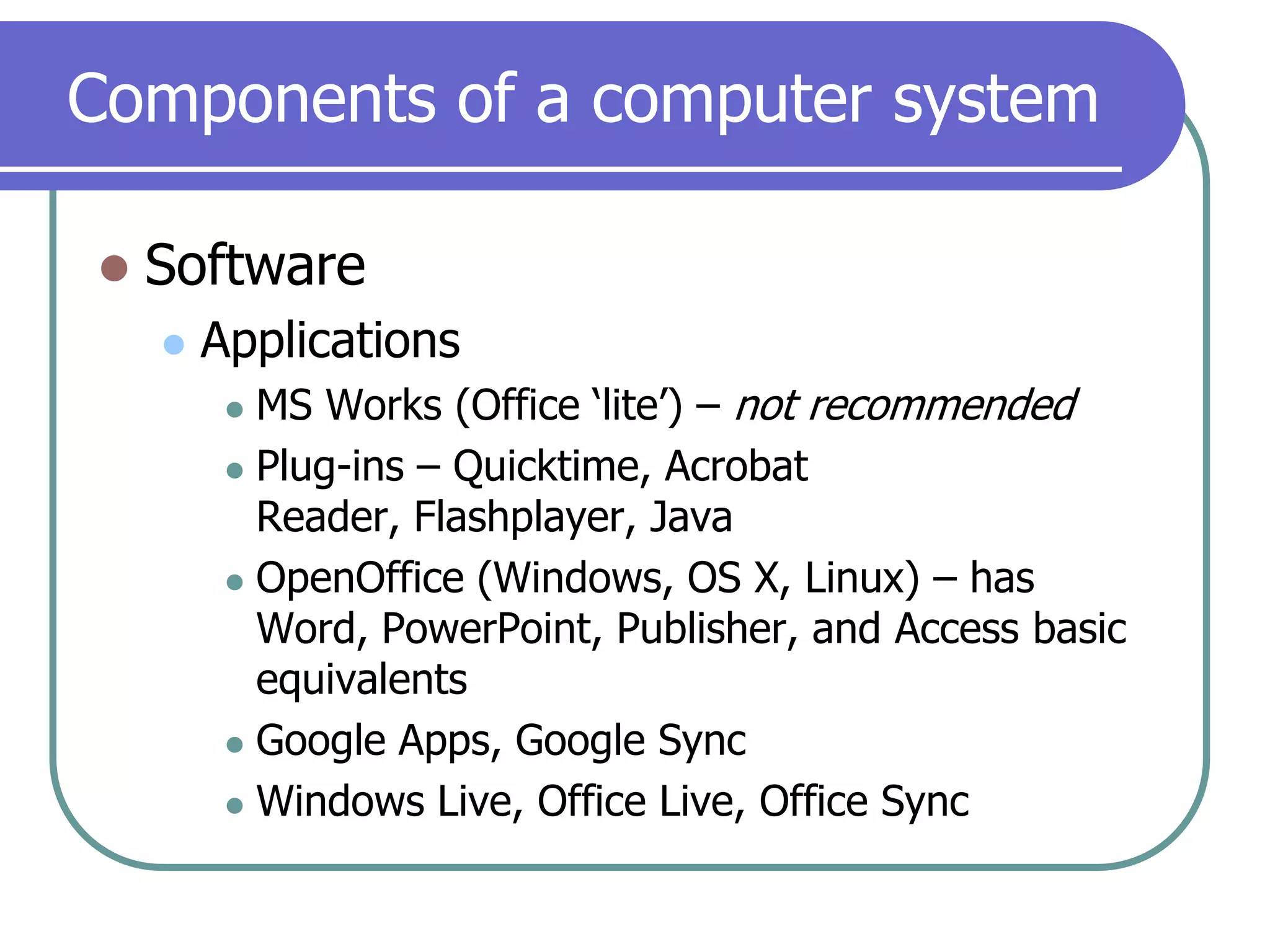
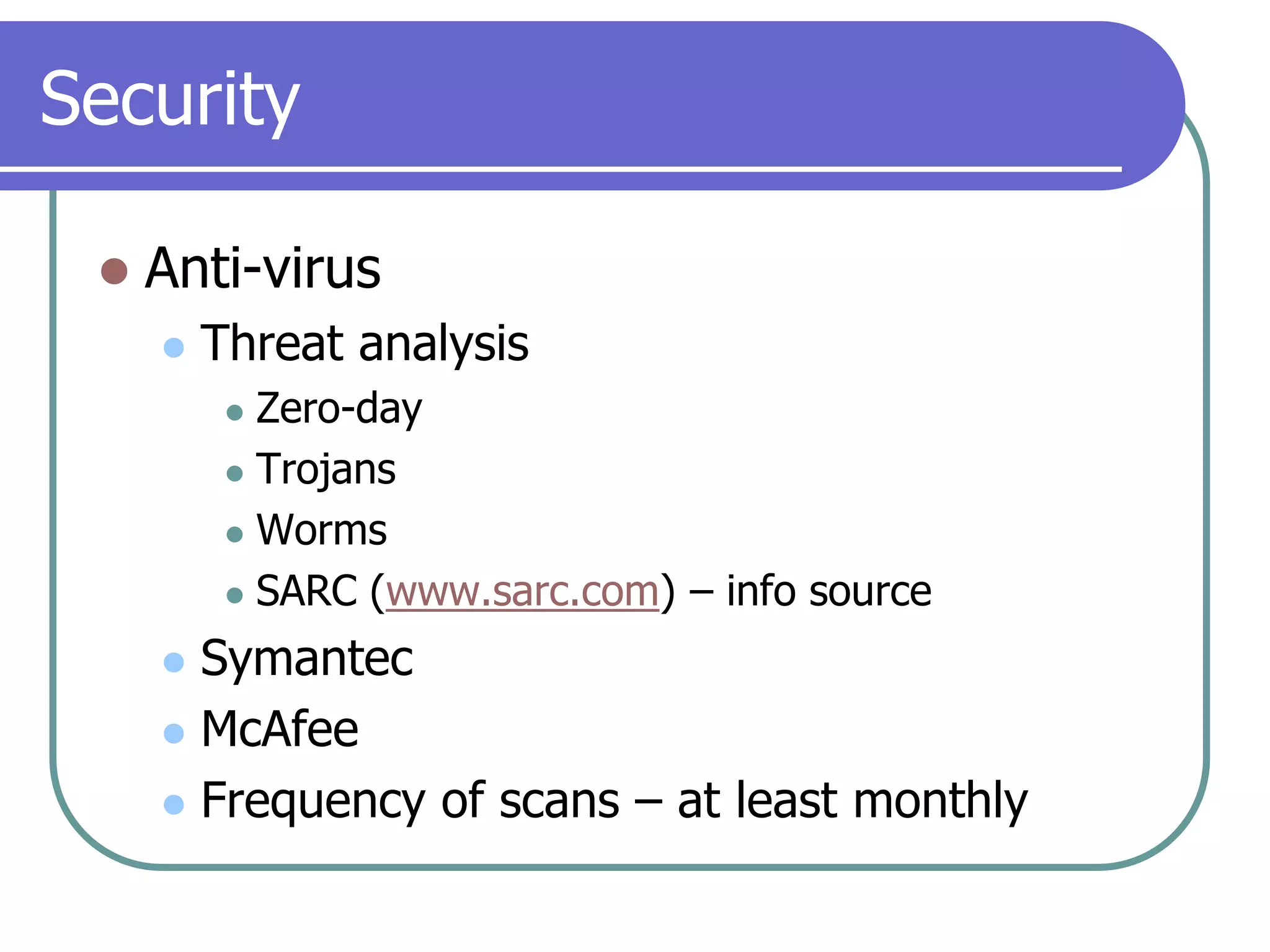
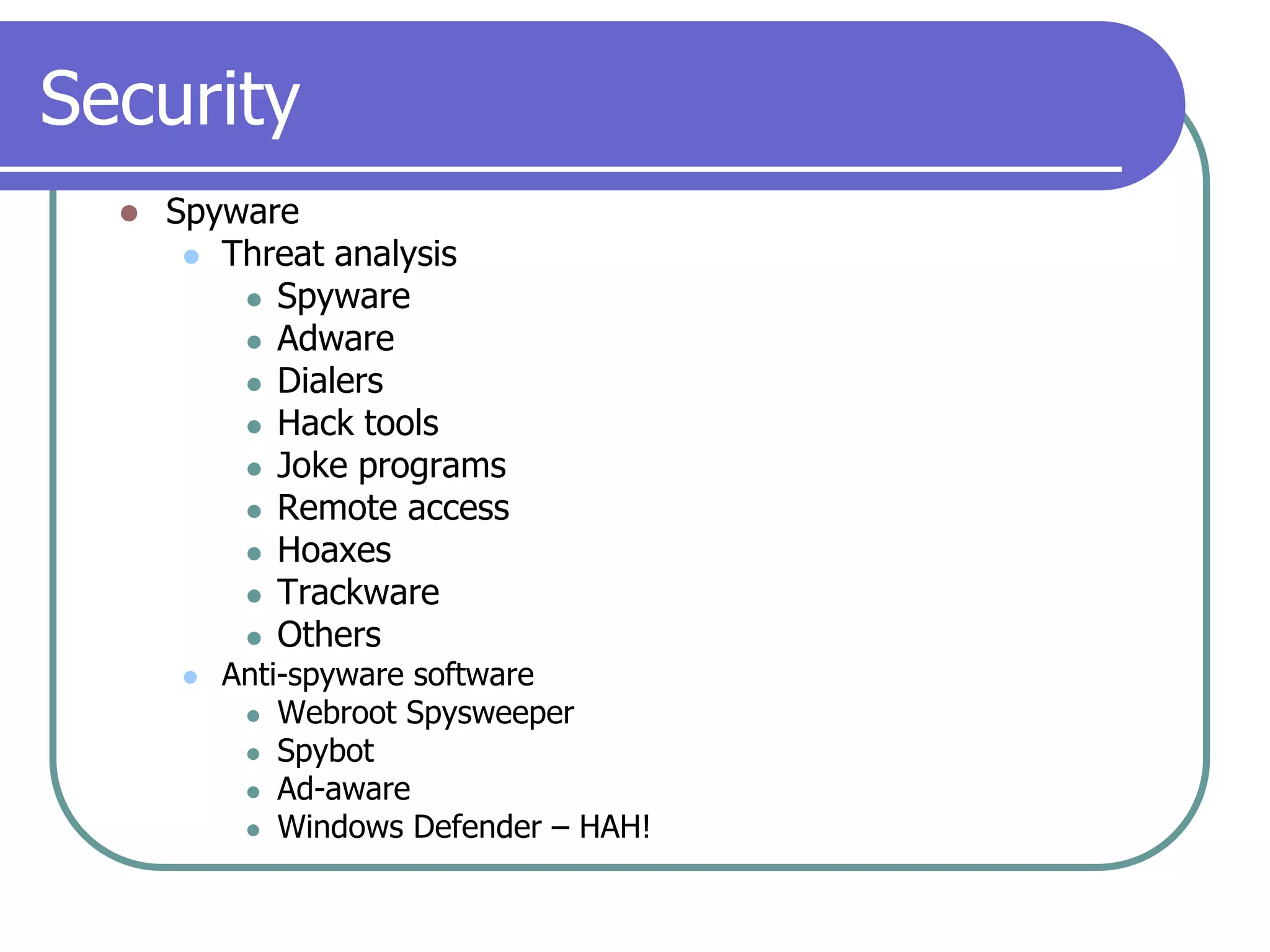
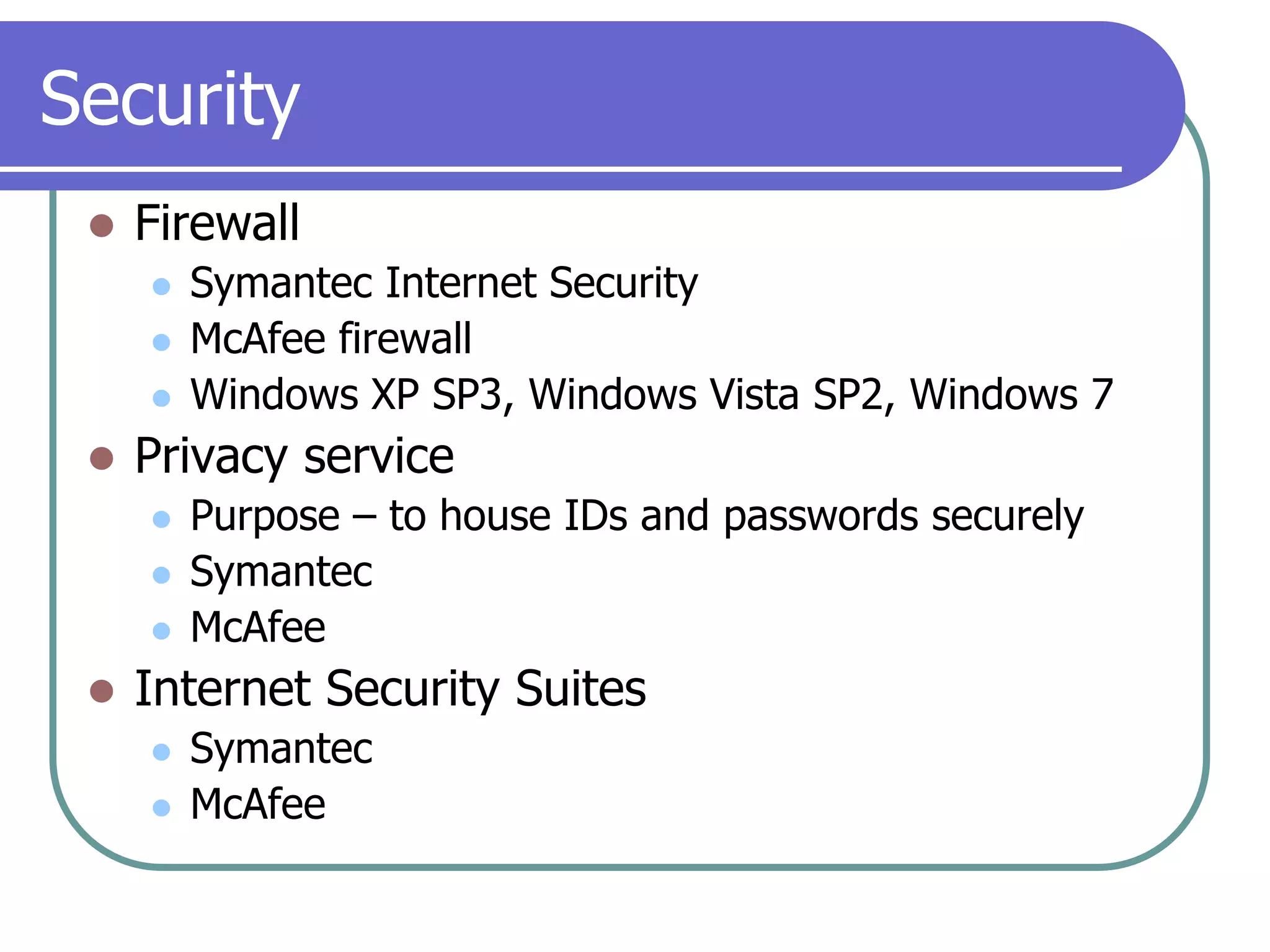
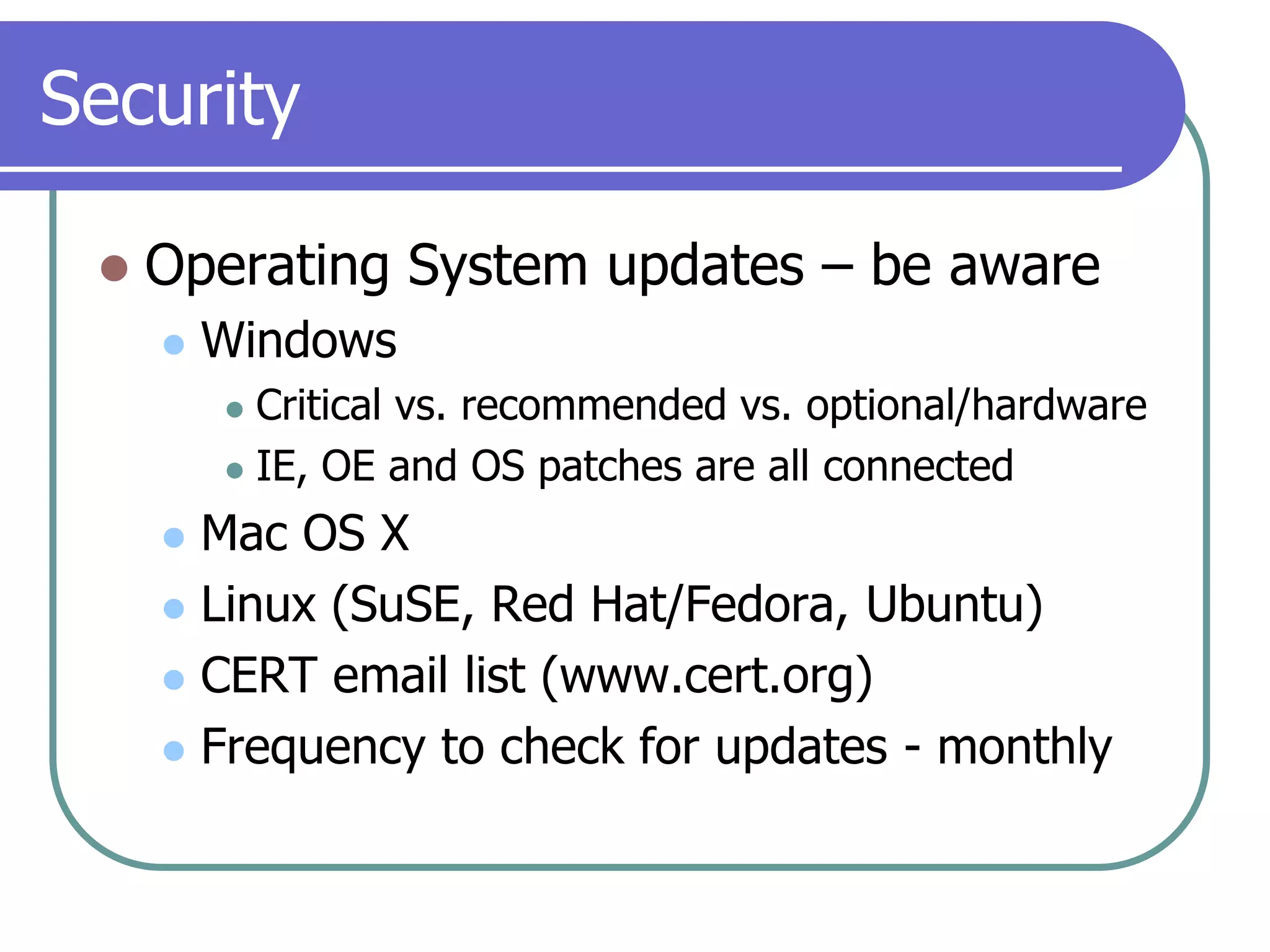
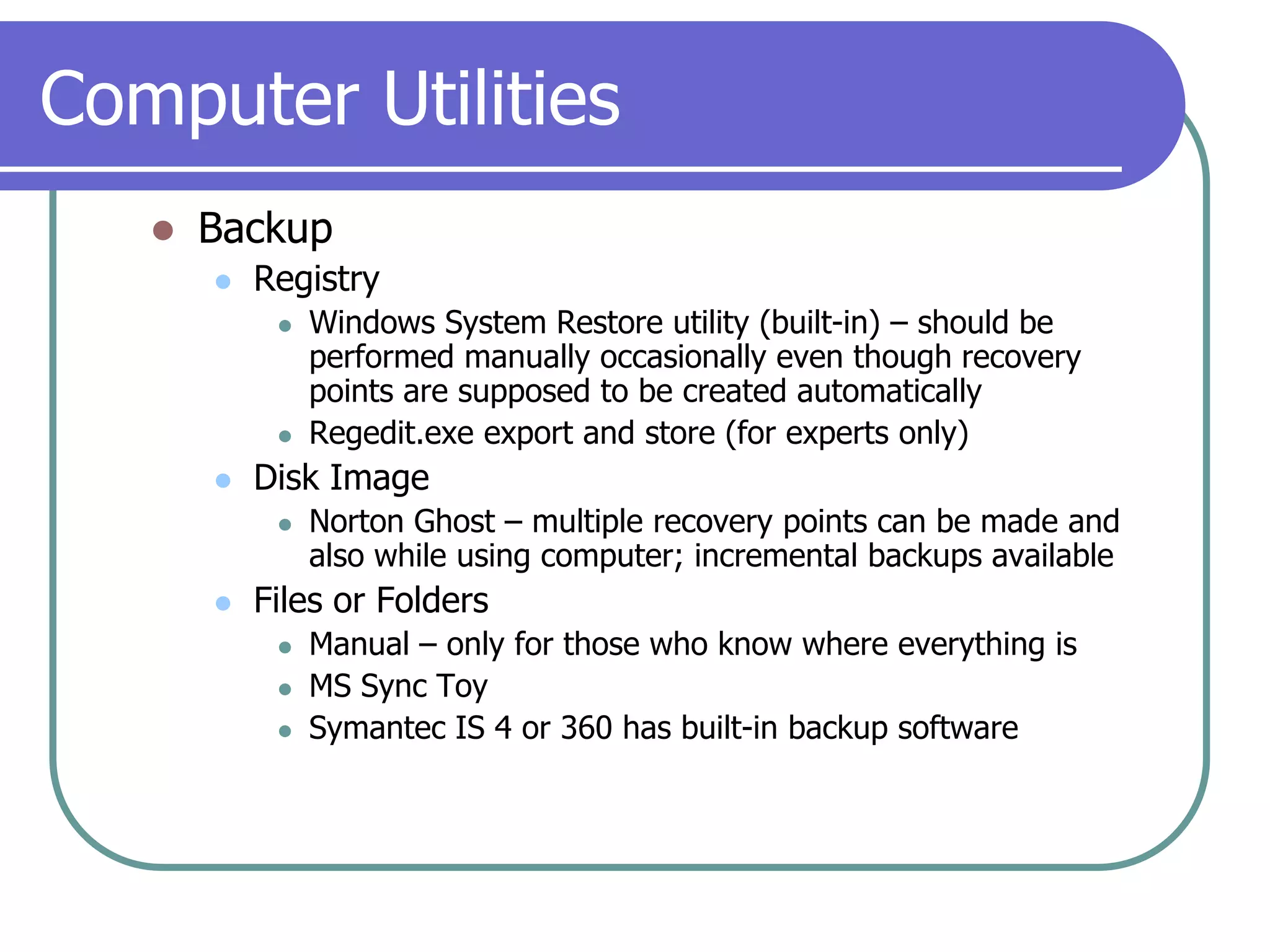
This document provides an overview of a seminar on computer basics and maintenance. It discusses buying a computer and components like hardware, software, security, and operating systems. It emphasizes that maintaining a computer is like maintaining a car - you need to shop carefully, buy the right options and warranty, and do regular maintenance and backups to keep it running well over time. Security topics covered include viruses, spyware, identity theft, firewalls, and browser safety.