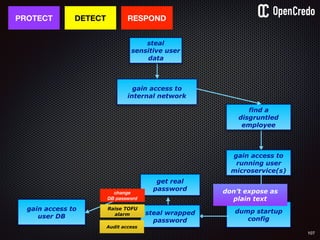
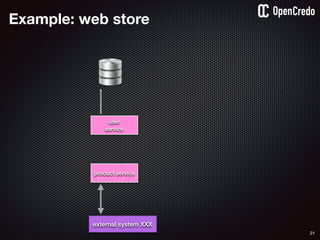
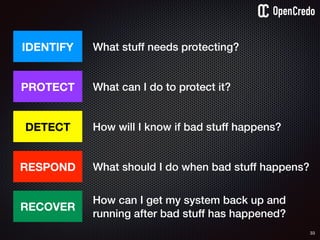
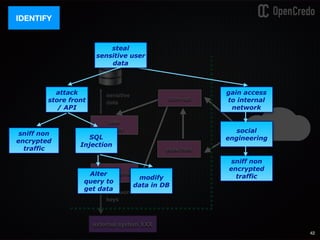
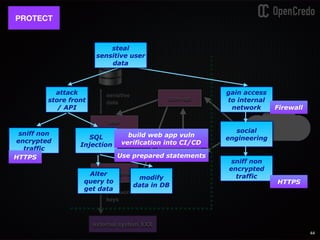
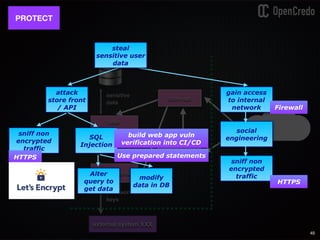
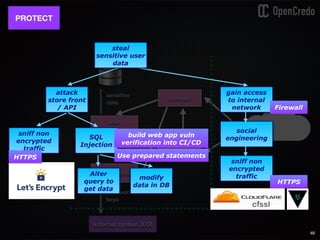
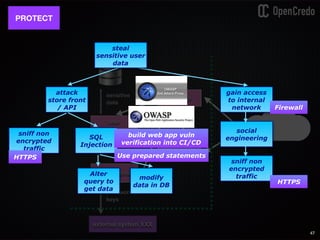
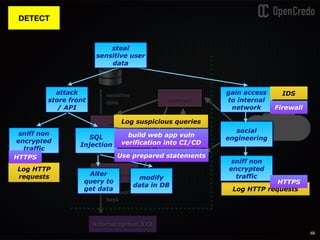
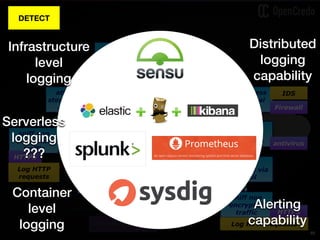
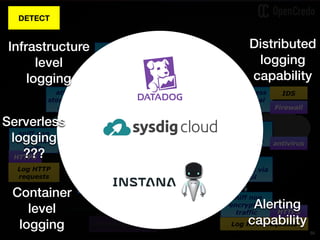
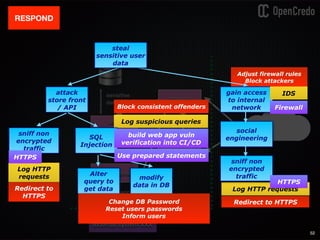
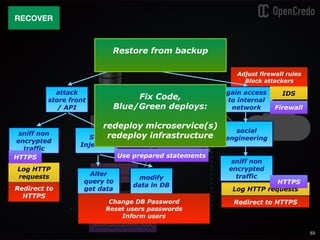
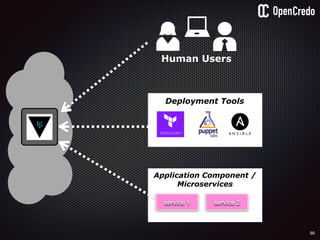
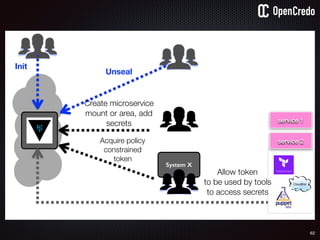
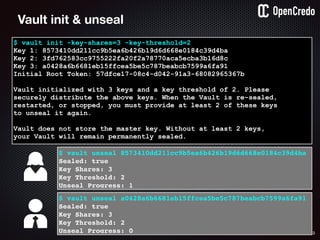
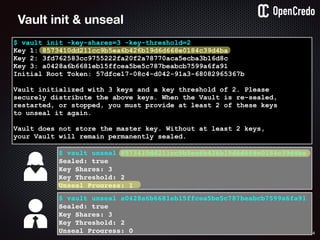
The document discusses the integration of security within microservices, emphasizing the importance of incorporating security as a core component of the development process (DevSecOps). It outlines a framework for assessing security challenges using the NIST Cybersecurity Framework, detailing steps such as identifying, protecting, detecting, responding, and recovering from threats. Additionally, it showcases the use of Vault for managing sensitive data and secrets in microservices, including setup instructions and examples of secure practices.

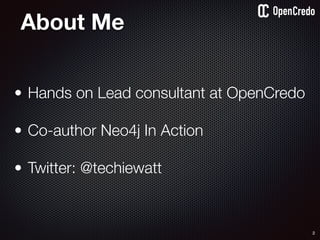









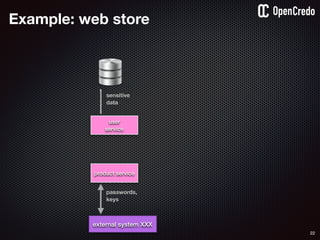
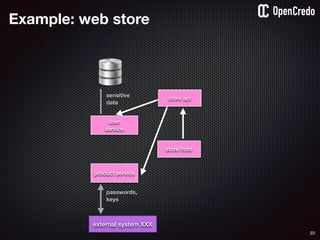
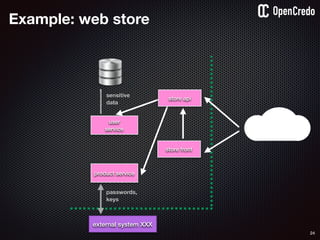

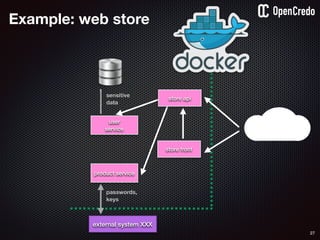
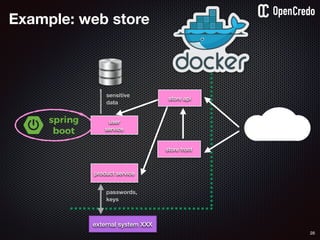
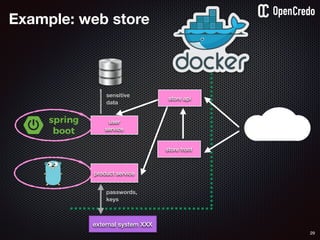


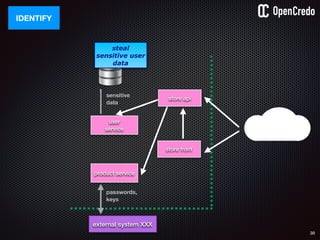
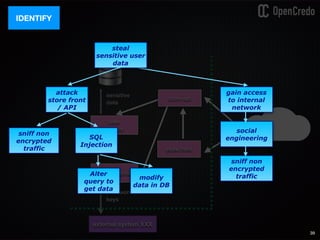
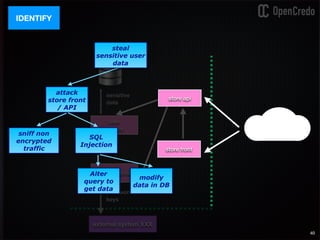
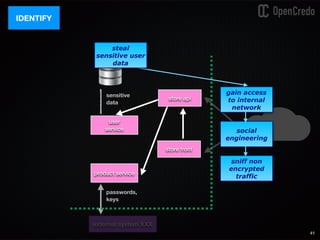






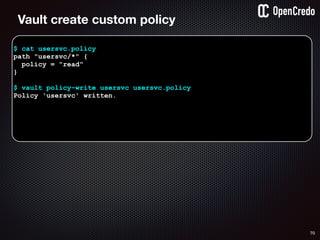
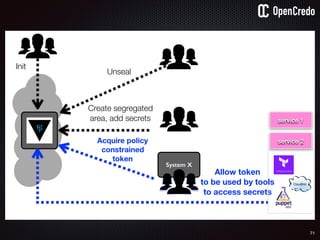


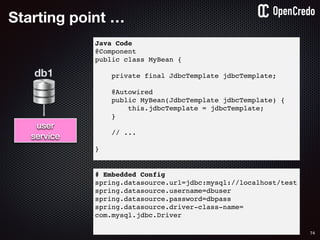
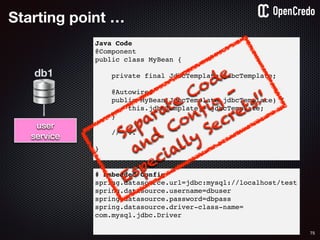

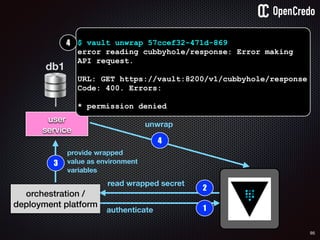
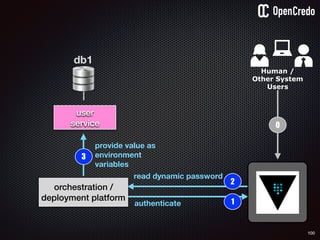
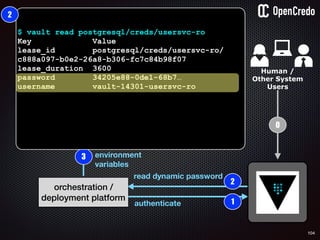
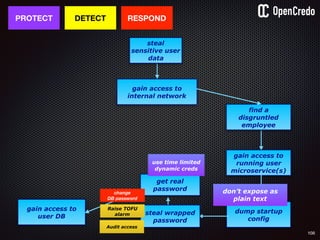
![79
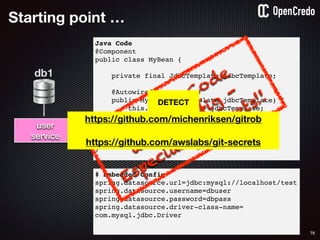
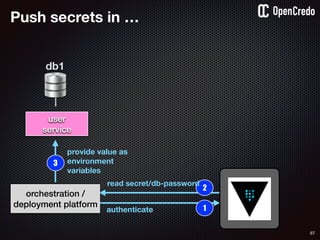
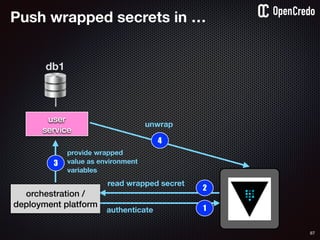
user
service
db1
1authenticate
2
read secret/db-password
orchestration /
deployment platform
3
provide value as
environment
variables
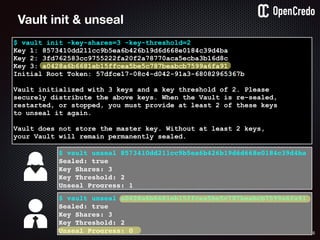
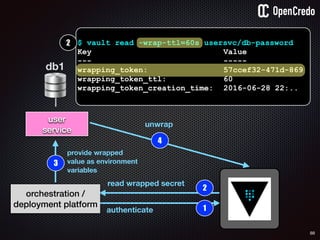
$ vault auth e2d0a065-xxxx-yyyy-zzzz
Successfully authenticated! You are…
token_policies: [default, usersvc]
$ vault read usersvc/db-password
Key Value
--- -----
refresh_interval 2592000
value MyClearTextPassword
1
2](https://image.slidesharecdn.com/nickiwatt-securitymicroservcesandvault-160718162411/85/Microservices-Manchester-Security-Microservces-and-Vault-by-Nicki-Watt-75-320.jpg)
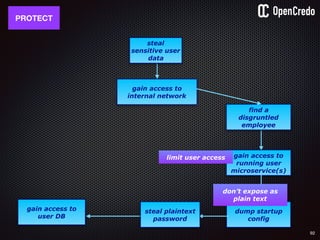
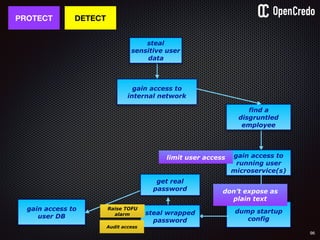
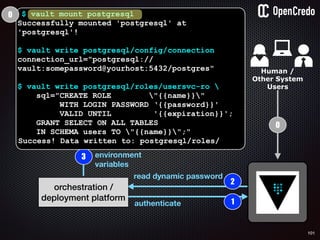
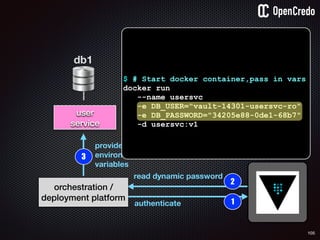
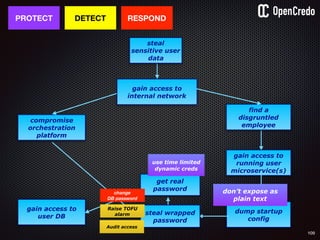
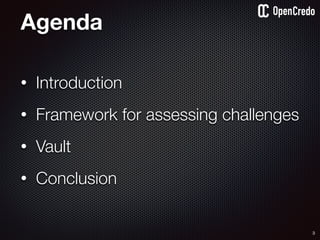
![83
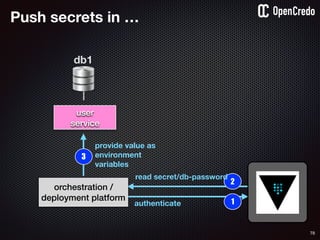
gain access to
internal network
find a
disgruntled
employee
dump startup
config
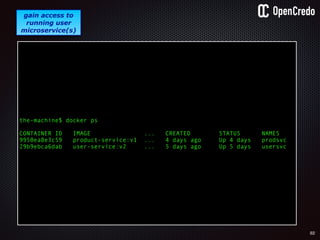
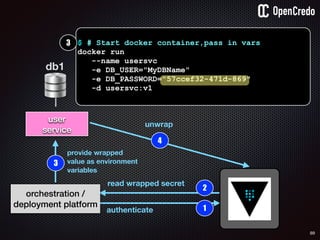
the-machine$ docker inspect 29b9ebca6dab
[
{
"Id": “29b9ebca6dab147991201a5c61b72d3d546885ca8fd…”,
"Created": "2016-06-27T21:26:16.126414991Z",
"Args": [
"-jar",
"UserService"
],
"Config": {
"Hostname": "29b9ebca6dab",
"Env": [
“DB_USER=MyUserName",
“DB_PASSWORD=MyClearTextPassword",
“VAR1=something-else“
],
"Cmd": [
"java",
"-jar",
"UserService"
],
...
}
]](https://image.slidesharecdn.com/nickiwatt-securitymicroservcesandvault-160718162411/85/Microservices-Manchester-Security-Microservces-and-Vault-by-Nicki-Watt-79-320.jpg)
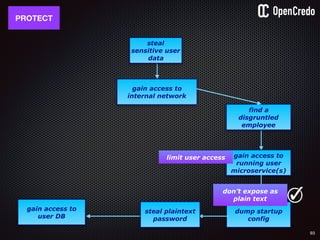
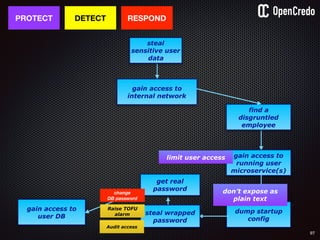
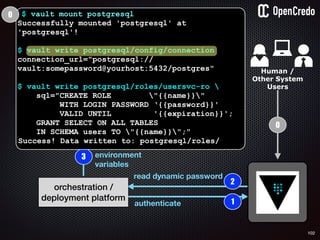
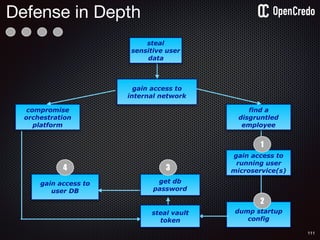
![84
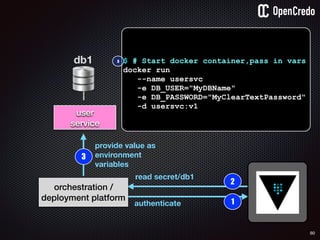
gain access to
internal network
find a
disgruntled
employee
the-machine$ docker inspect 29b9ebca6dab
[
{
"Id": “29b9ebca6dab147991201a5c61b72d3d546885ca8fd…”,
"Created": "2016-06-27T21:26:16.126414991Z",
"Args": [
"-jar",
"UserService"
],
"Config": {
"Hostname": "29b9ebca6dab",
"Env": [
“DB_USER=MyUserName",
“DB_PASSWORD=MyClearTextPassword",
“VAR1=something-else“
],
"Cmd": [
"java",
"-jar",
"UserService"
],
...
}
]
steal plaintext
password](https://image.slidesharecdn.com/nickiwatt-securitymicroservcesandvault-160718162411/85/Microservices-Manchester-Security-Microservces-and-Vault-by-Nicki-Watt-80-320.jpg)
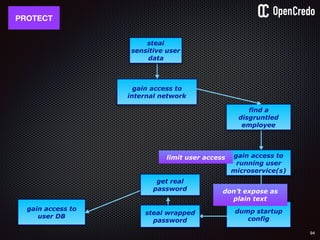
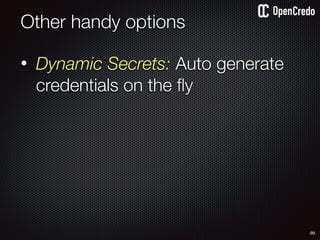
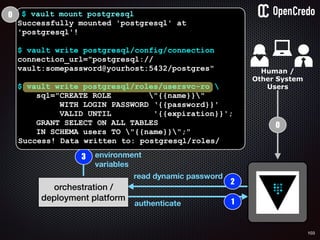
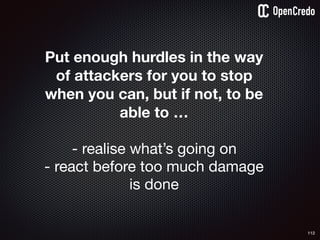
![91
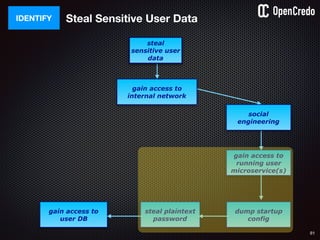
dump startup
config
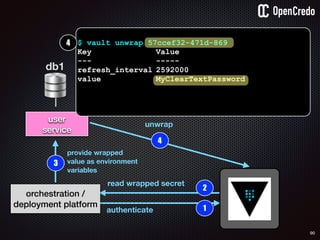
the-machine$ docker inspect 29b9ebca6dab
[
{
"Id": “29b9ebca6dab147991201a5c61b72d3d546885ca8fd…”,
"Created": "2016-06-27T21:26:16.126414991Z",
"Args": [
"-jar",
"UserService"
],
"Config": {
"Hostname": "29b9ebca6dab",
"Env": [
“DB_USER=MyUserName",
“DB_PASSWORD=57ccef32-471d-869",
“VAR1=something-else“
],
"Cmd": [
"java",
"-jar",
"UserService"
],
...
}
]](https://image.slidesharecdn.com/nickiwatt-securitymicroservcesandvault-160718162411/85/Microservices-Manchester-Security-Microservces-and-Vault-by-Nicki-Watt-88-320.jpg)