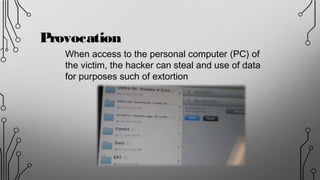
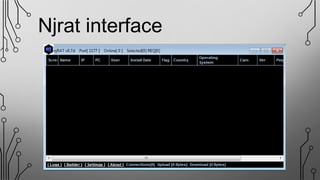
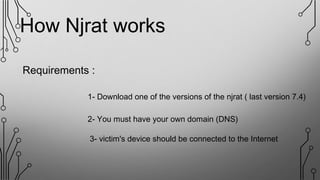
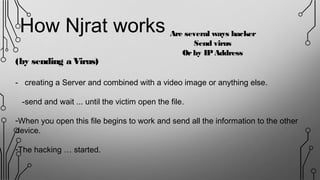
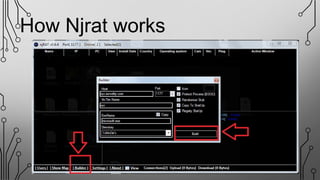
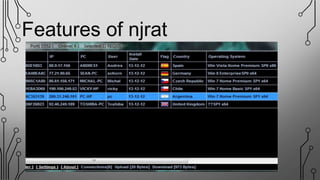
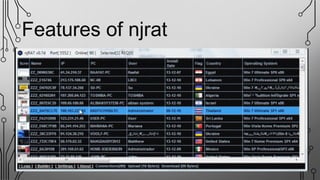
NJRAT is a remote access tool (RAT) that allows hackers to gain unauthorized access and control of victims' devices. It works by sending a virus payload that installs itself when opened by the victim. Once installed, the NJRAT server gives the hacker full control over files, programs, cameras, microphones and more on the infected device. Key features of NJRAT include encrypting the virus, bringing back device info, controlling the device in multiple ways from the server, and small server size. To protect devices, users should use antivirus software, avoid opening files from unknown sources, only use licensed software, and not use hacking tools for unethical purposes.