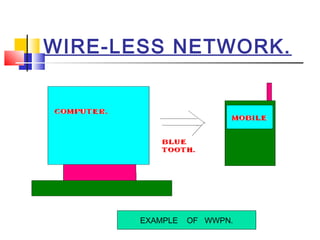
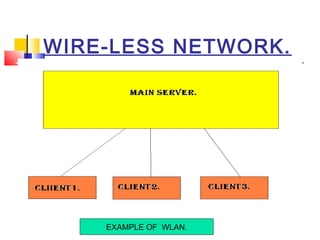
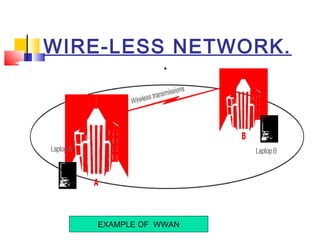
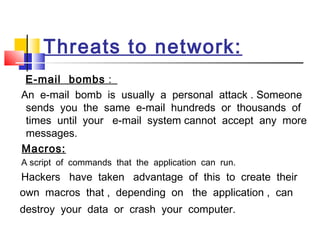
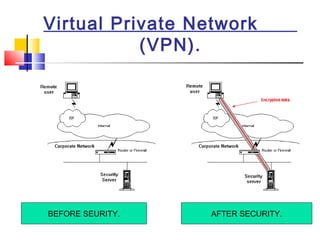
This document discusses wireless network security. It defines wireless networks and their types, including wireless personal area networks (WPAN), wireless local area networks (WLAN), and wireless wide area networks (WWAN). It also discusses why security systems are needed for wireless networks, describing common threats from hackers, viruses, spam, and more. Finally, it outlines some methods for securing wireless networks, such as using virtual private networks (VPN), firewalls, Internet Protocol Security (IPSec), and authentication, authorization, and accounting (AAA) servers.