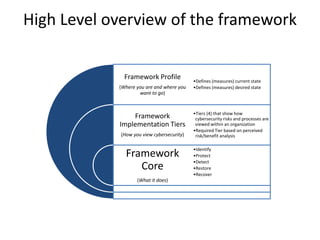
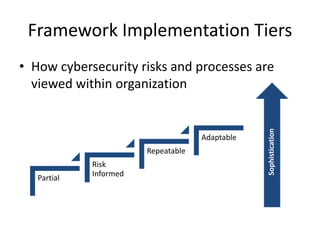
The document outlines the objectives and components of the NIST Cybersecurity Framework (CSF), emphasizing its role in assessing and improving organizational security postures. It describes key elements such as the framework core functions—identify, protect, detect, respond, and recover—alongside implementation tiers that reflect the organization’s risk perception and management. The CSF enhances communication around cybersecurity by providing a structured approach to measure and achieve desired security outcomes while aligning with existing regulations and standards.