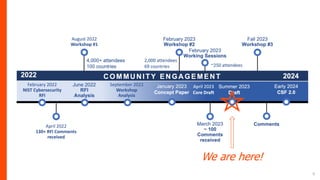
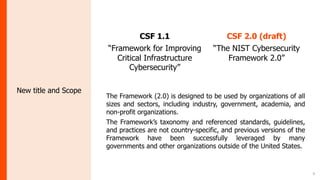
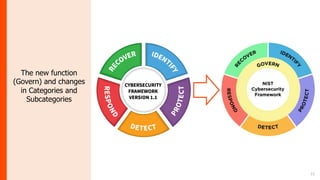
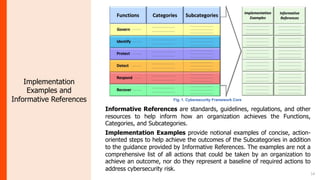
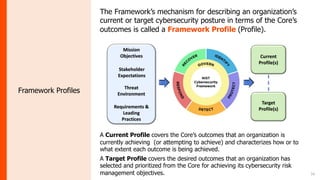
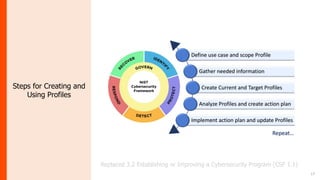
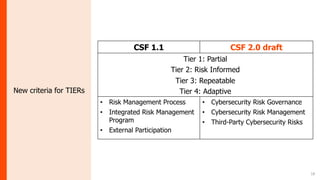
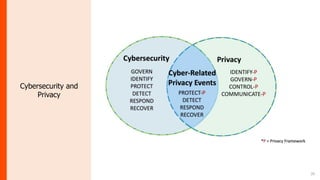
The document summarizes the journey of the NIST Cybersecurity Framework from version 1.1 to the upcoming version 2.0. It provides an overview of the key components of version 1.1 and the motivation for an update. Version 2.0 includes significant updates like a new "Govern" function, changes to categories and subcategories, more implementation guidance, and an emphasis on supply chain risk management. The draft of version 2.0 is available for public comment through November 2023, with the final version planned for early 2024.