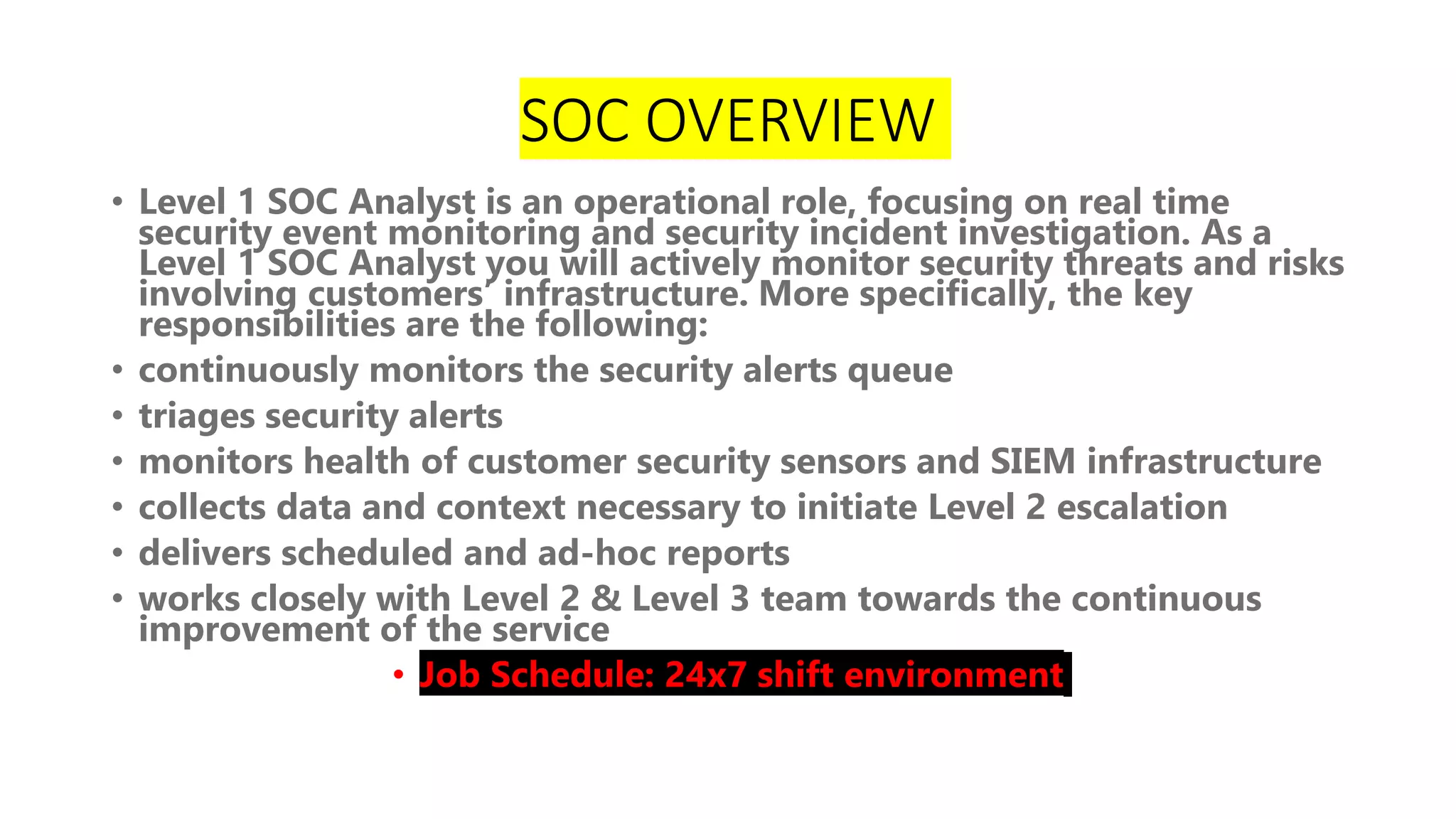
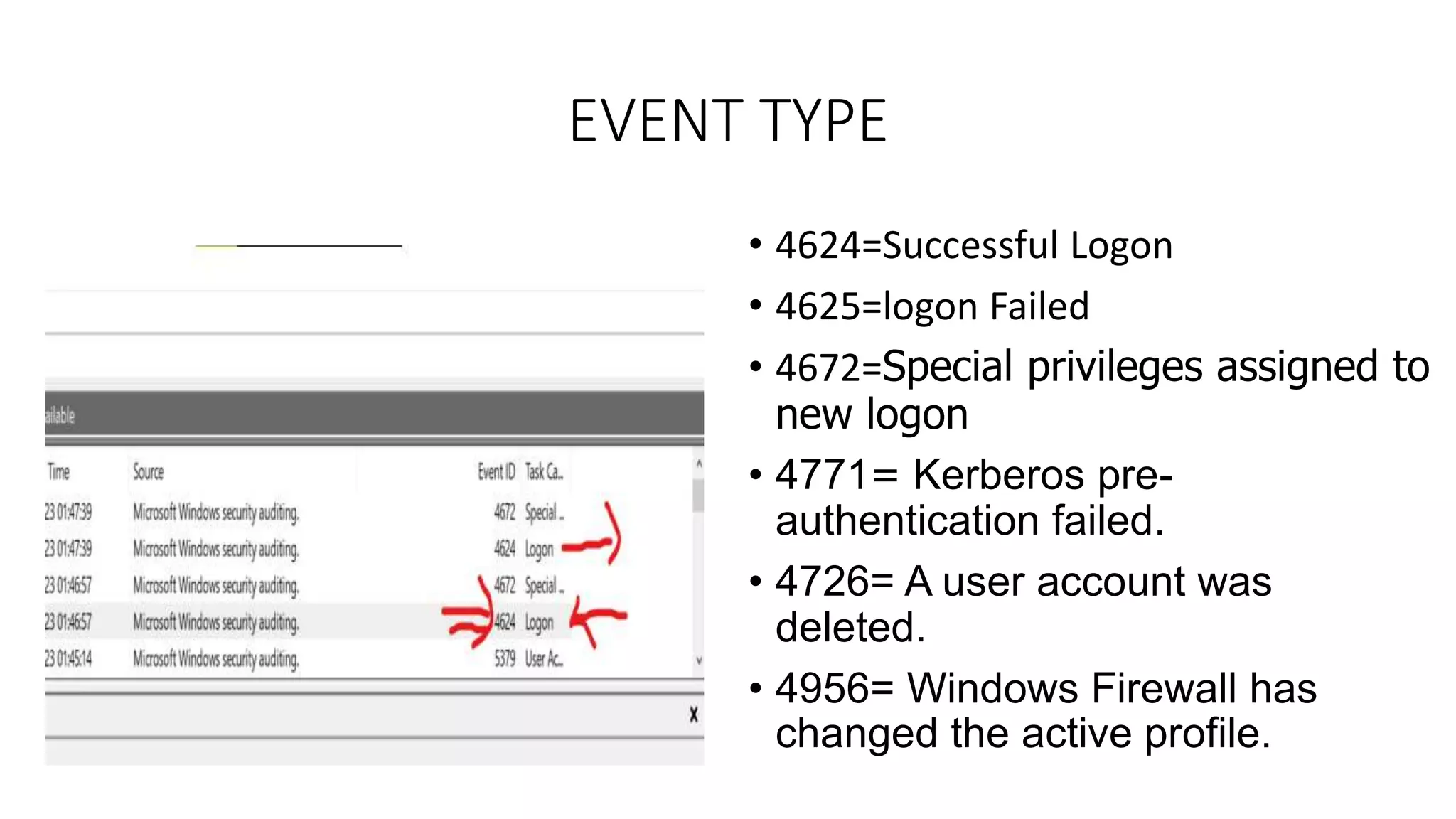
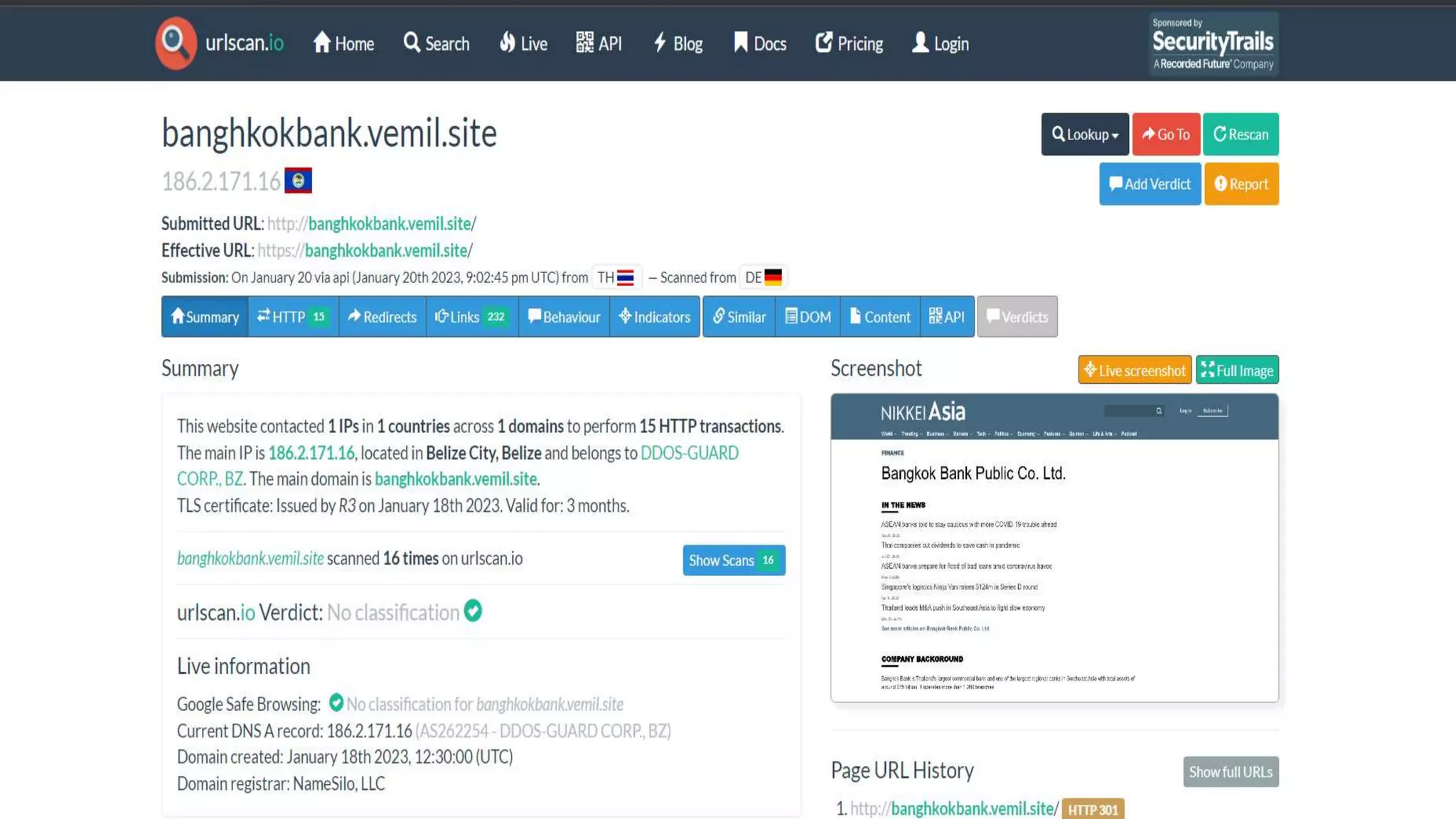
The document discusses blue teams and the role of SOC analysts. It defines a blue team as a company's cybersecurity employees housed in a SOC, made up of highly skilled analysts who work to defend and improve organizational defenses. Different roles in a blue team are outlined, including SOC analysts, threat hunting, threat intelligence, malware analysis, and digital forensics. The responsibilities of an entry-level SOC analyst are described, along with common SIEM tools and example event types monitored. Finally, it suggests ways for SOC analysts to learn and grow in their careers.






![Different Teams in Blue Team IN MNC
SOC Analyst[L1,L2,L3]
Threat Hunting
Threat inteiligence
Malware Analyst
OSINT Investigator
DFIR](https://image.slidesharecdn.com/blueteam-230304085328-638d2f2e/75/Blue-Team-8-2048.jpg)