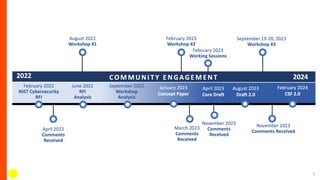
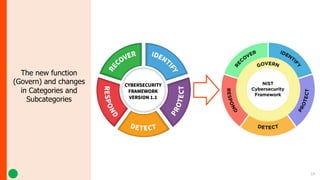
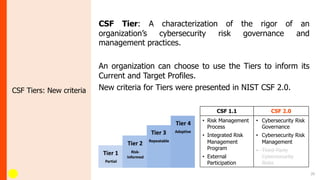
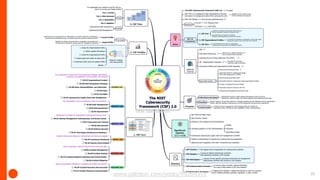
NIST has updated the Cybersecurity Framework to version 2.0 (CSF 2.0). Key changes include a new "Govern" function, updated categories and subcategories, and expanded guidance on using profiles and implementation examples. CSF 2.0 also emphasizes supply chain risk management and alignment with other frameworks. The update aims to reflect the evolving cybersecurity landscape and help organizations better manage cybersecurity risks.