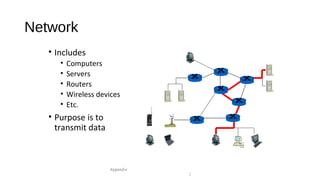
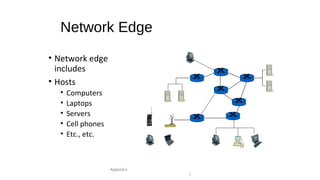
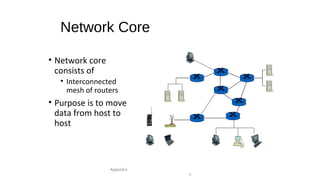
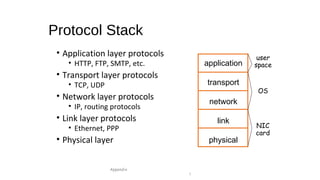
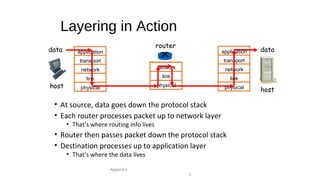
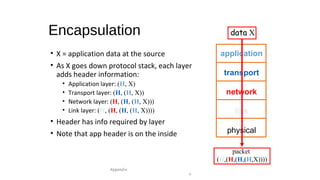
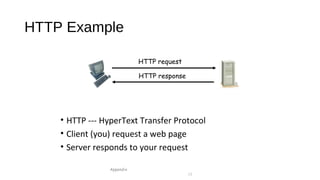
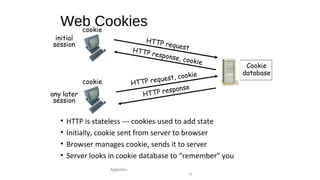
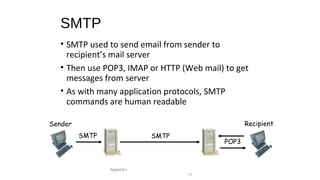
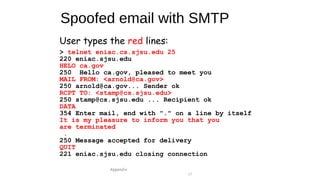
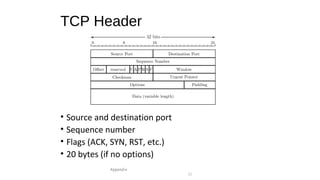
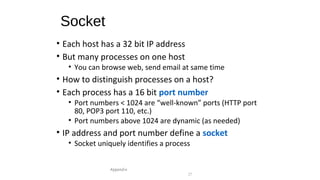
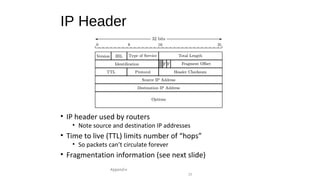
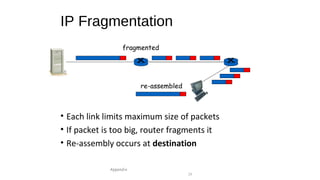
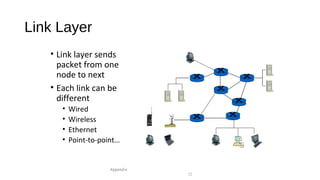
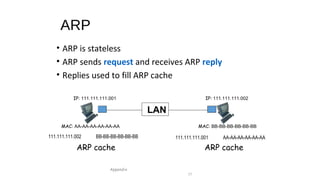
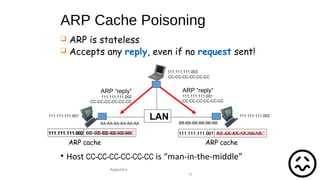
The document provides an overview of networking concepts across different layers of the networking model. It discusses that a network includes interconnected devices like computers, servers, routers and wireless devices. The network core consists of routers that route data between hosts using protocols like IP. Modern data networks are packet switched, where data is divided into packets that are transmitted independently.