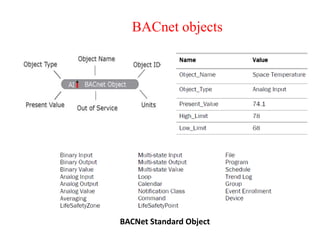
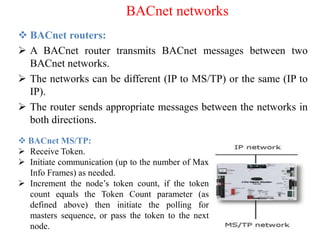
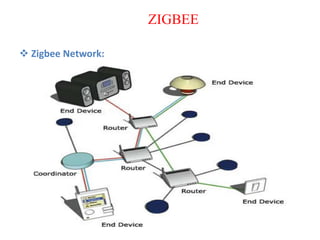
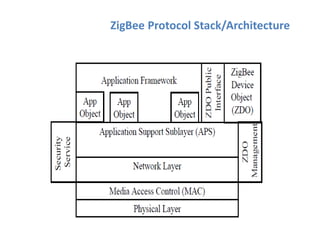
The document discusses various protocols and security aspects related to IoT. It provides details on protocols such as IEEE 802.15.4, BACnet, Modbus, KNX, Zigbee etc. It also outlines vulnerabilities in IoT like unauthorized access, information corruption, DoS attacks. Key elements of IoT security discussed are identity establishment, access control, data security, non-repudiation and availability. Security requirements and models for IoT are also mentioned.