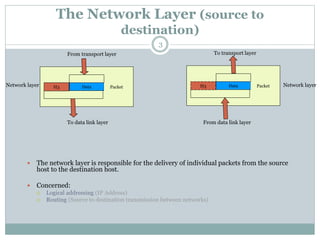
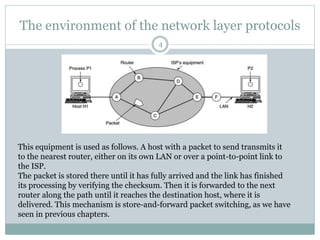
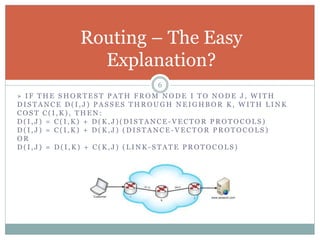
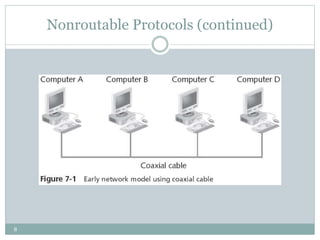
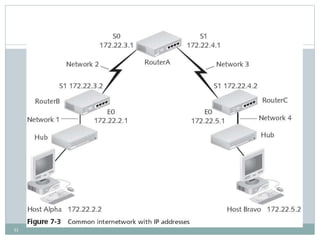
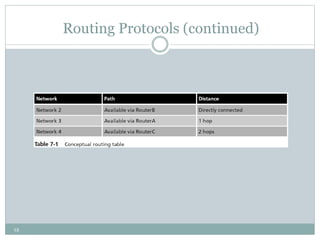
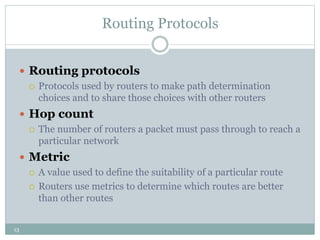
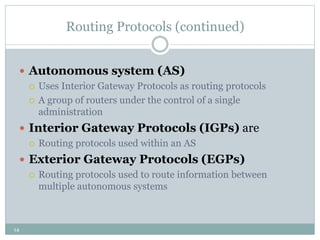
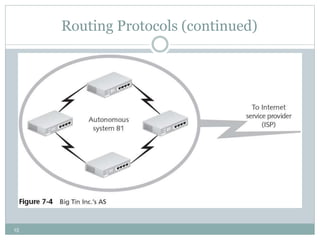
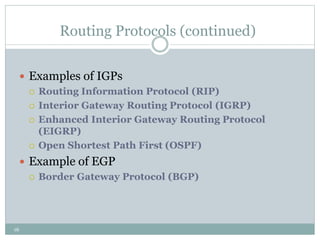
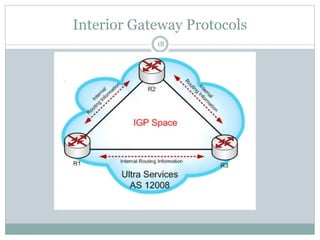
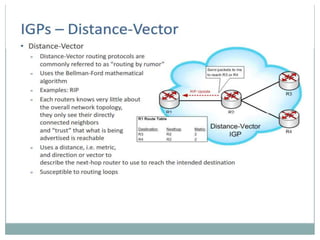
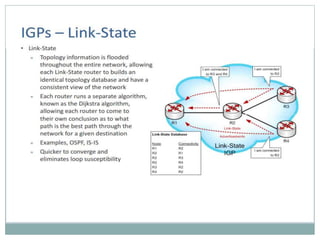
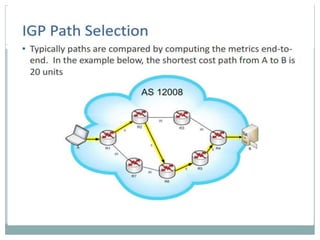
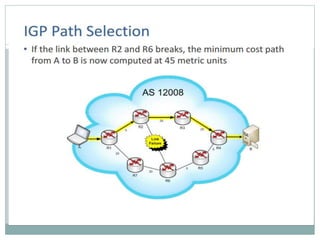
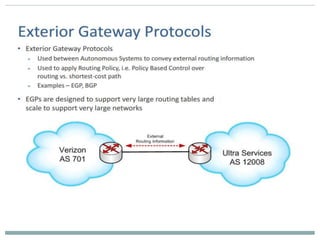
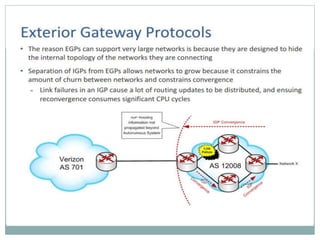
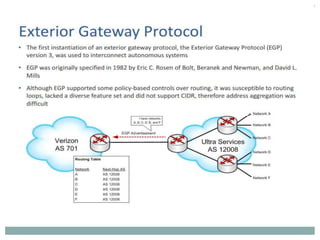
The document discusses the functions of the transport and network layers in networking. The transport layer is responsible for ensuring data is delivered correctly and efficiently from the source to the destination, while the network layer focuses on routing individual packets from host to host. Key concepts include error-free channels, packet switching, routing protocols, and the distinction between datagram and virtual-circuit networks.