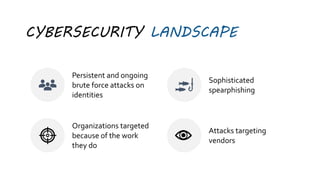
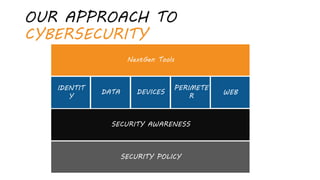
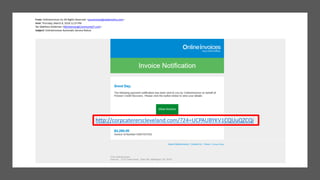
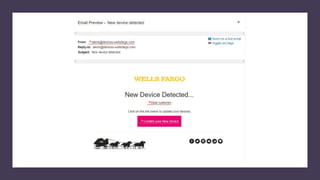
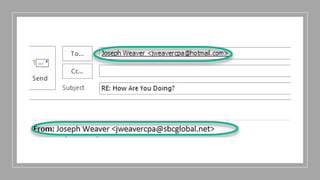
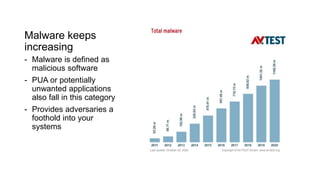
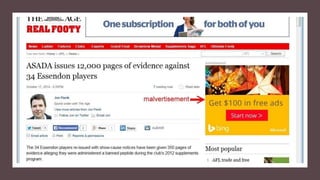
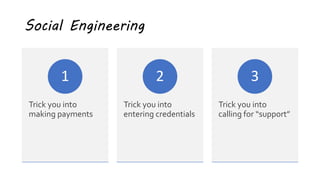
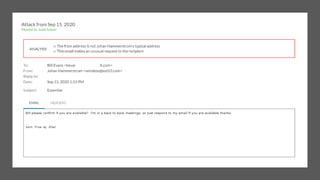
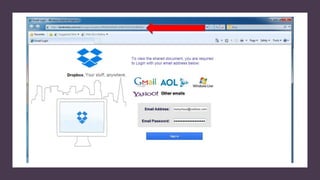
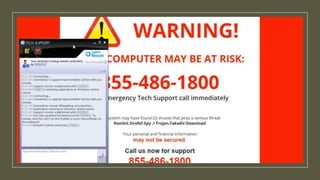
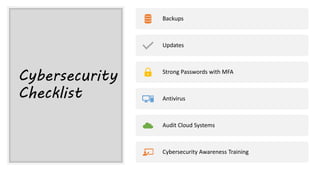
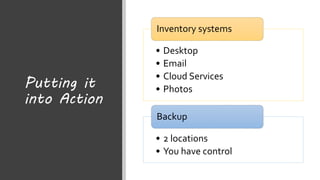
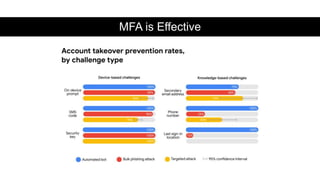
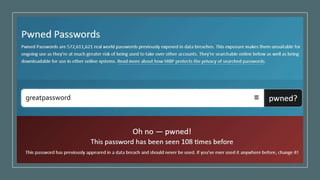
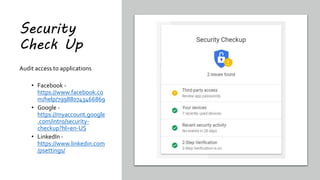
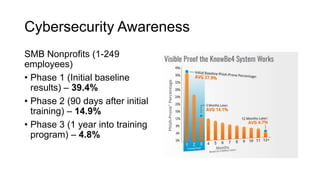
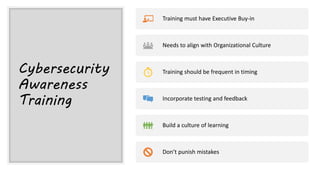
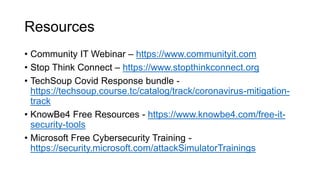
This document summarizes a cybersecurity training webinar for nonprofits. The webinar covered the current cybersecurity landscape including persistent brute force attacks and sophisticated spearphishing targeting organizations. It discussed new security tools available and common contemporary attack examples like phishing, malware, and social engineering. The presentation emphasized the importance of the human firewall through cybersecurity awareness training and individual steps like enabling multi-factor authentication and using a password manager. It provided resources for moving forward with both individual cybersecurity practices and formalizing organizational controls.