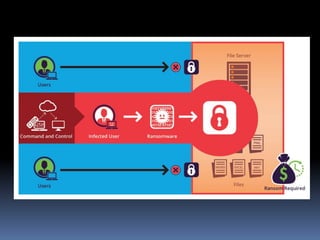
This document provides an overview of cyber threats and ransomware prevention. It defines a cyber threat as an activity intended to compromise the security of an information system by altering the availability, integrity, or confidentiality of the system. It notes that in today's connected world, new risks emerge daily and connecting to the internet opens the possibility of hacker attacks. The document outlines different types of attacks like phishing, man-in-the-middle attacks, and ransomware. Ransomware is defined as malicious software that restricts access to a device and demands ransom payment, usually in cryptocurrency. The document recommends defensive steps to prevent ransomware like using malware detection, backup solutions, forensic analysis with machine learning, and not paying