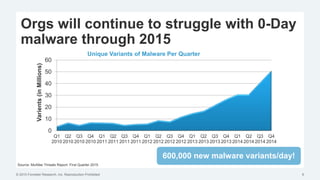
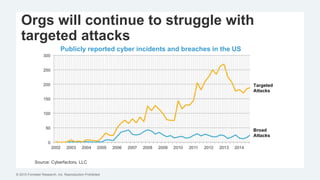
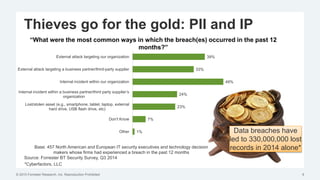
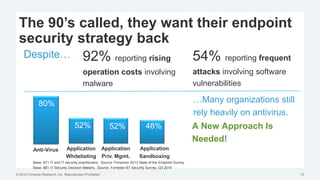
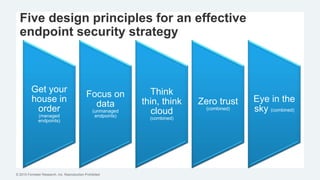
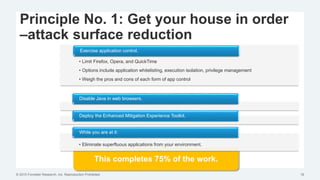
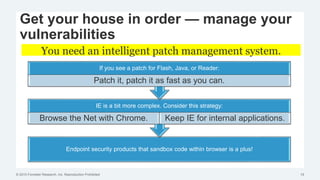
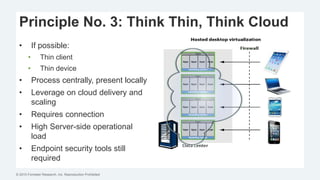
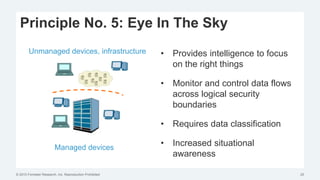
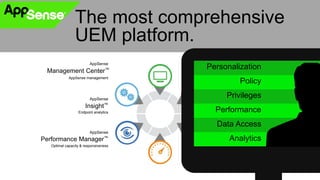
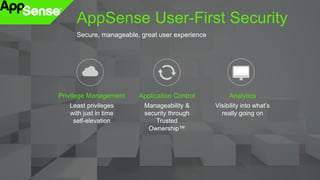
This document discusses strategies for protecting endpoints from targeted attacks. It begins with an overview of the increasing threats facing organizations from malware and cyber attacks. It then outlines five principles for an effective endpoint security strategy: 1) get organizational endpoints in order through vulnerability management and application control, 2) focus on protecting data rather than infrastructure on unmanaged devices, 3) utilize thin clients and cloud-based solutions, 4) implement a zero-trust approach to authentication, and 5) maintain visibility into endpoint activity. The document recommends implementing application control, patching vulnerabilities, deploying recommended security practices, improving authentication, and integrating network and endpoint security controls. It emphasizes continuing to shift focus to securing unmanaged devices by decoupling protection from infrastructure.