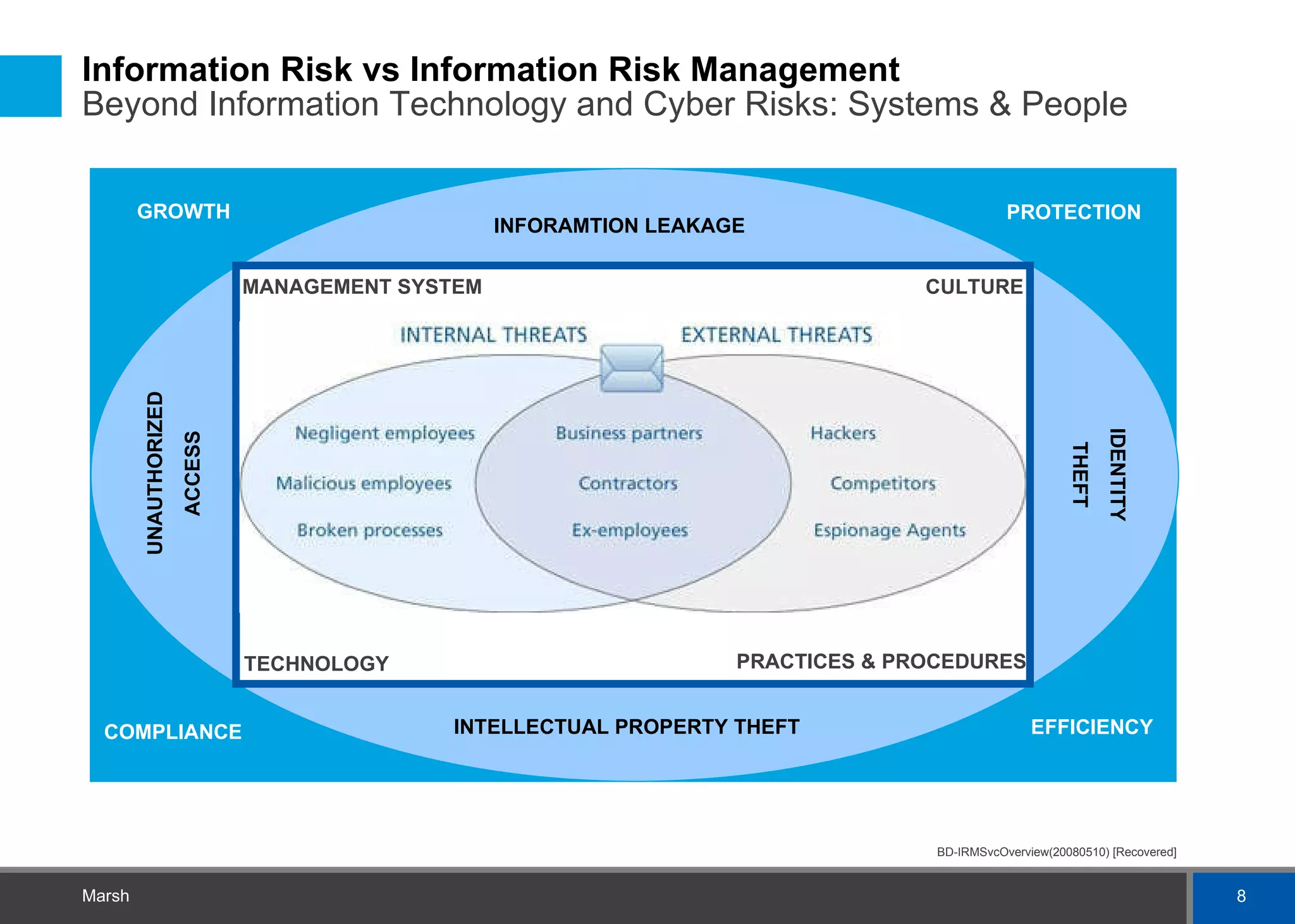
Despite efforts to implement information risk management systems, data breaches still occur frequently, especially internally. This is likely due to issues at both the systems and people levels. At the systems level, there are often too many different management systems that are not integrated, resulting in overlapping controls. At the people level, under-awareness of risks and demotivation from inefficient controls can undermine protection efforts. A successful information risk management approach requires addressing both technical and human aspects through coordinated strategies around governance, culture, procedures and technology.




![Personal Data (Privacy) Ordinance Implications of some judgments Obiter dictum about definition of ‘personal data’ Shi Tao v Privacy Commissioner for Personal Data [2008] 1 HKC 287 “… Neither the email address nor the IP address ex facie revealed the identity of the appellant . The information provided only disclosed that the email was sent from a computer located at the address of a business entity, and the date and time of the transaction. It was not reasonably practicable from such information to ascertain that it was actually the appellant who used the computer identified by the IP address to send out the relevant email at the relevant time…” Eastweek Publisher Ltd & Anor v Privacy Commissioner for Personal Data [2000] 1 HKC 692 “… In this case there was no act of personal data collection, as the data user must be compiling information about an identified person or about a person whom the data user intended to identify to engage the data protection principles. Here the data gatherer was indifferent to the identity of the complainant …” Obiter dictum about ‘data access request’ Wu Kit Ping v Administrative Appeals Board [2007] 5 HKC 450 “… if in the course of complying with a request by a data subject for the disclosure of that data subject’s personal data, the personal data of some other individual must be disclosed , then, unless that other individual has consented to the disclosure of his personal data, the request must be refused …”](https://image.slidesharecdn.com/irmoverview20080801elvin-12826545394453-phpapp02/75/Information-Risk-Management-Overview-7-2048.jpg)