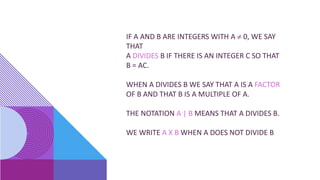
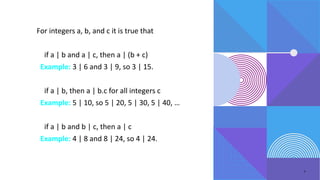
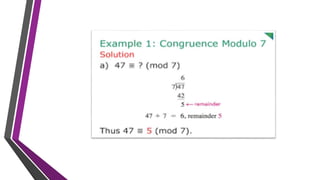
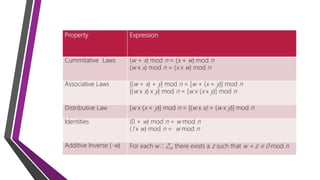
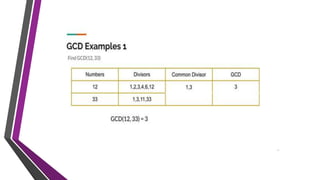
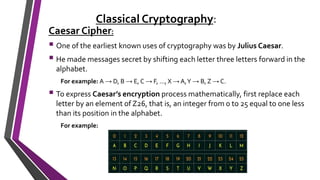
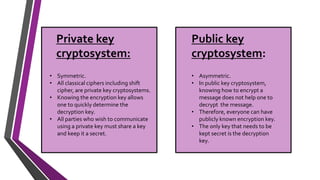
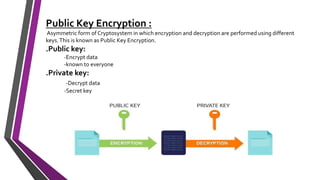
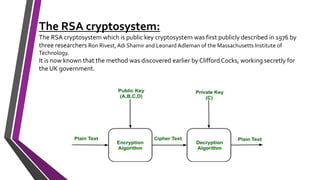
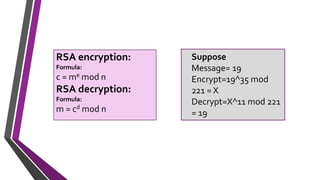
The document covers number theory, including concepts like divisibility, greatest common divisor, and prime numbers, highlighting its application in cryptography. It details encryption methods, such as Caesar and shift ciphers, alongside public and private key cryptosystems like RSA. Additionally, it discusses cryptographic protocols for key exchange and the importance of digital signatures for authentication and integrity.