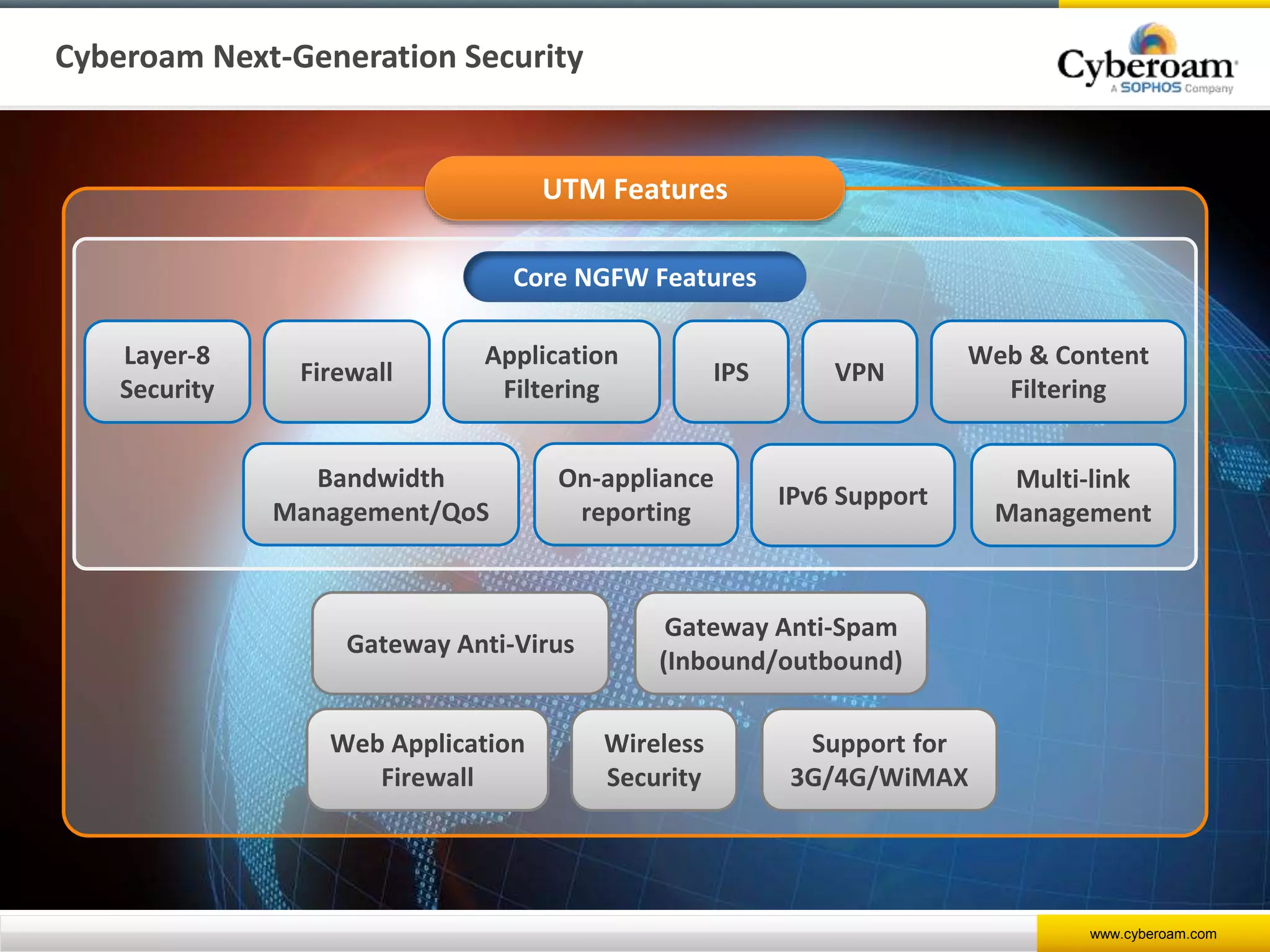
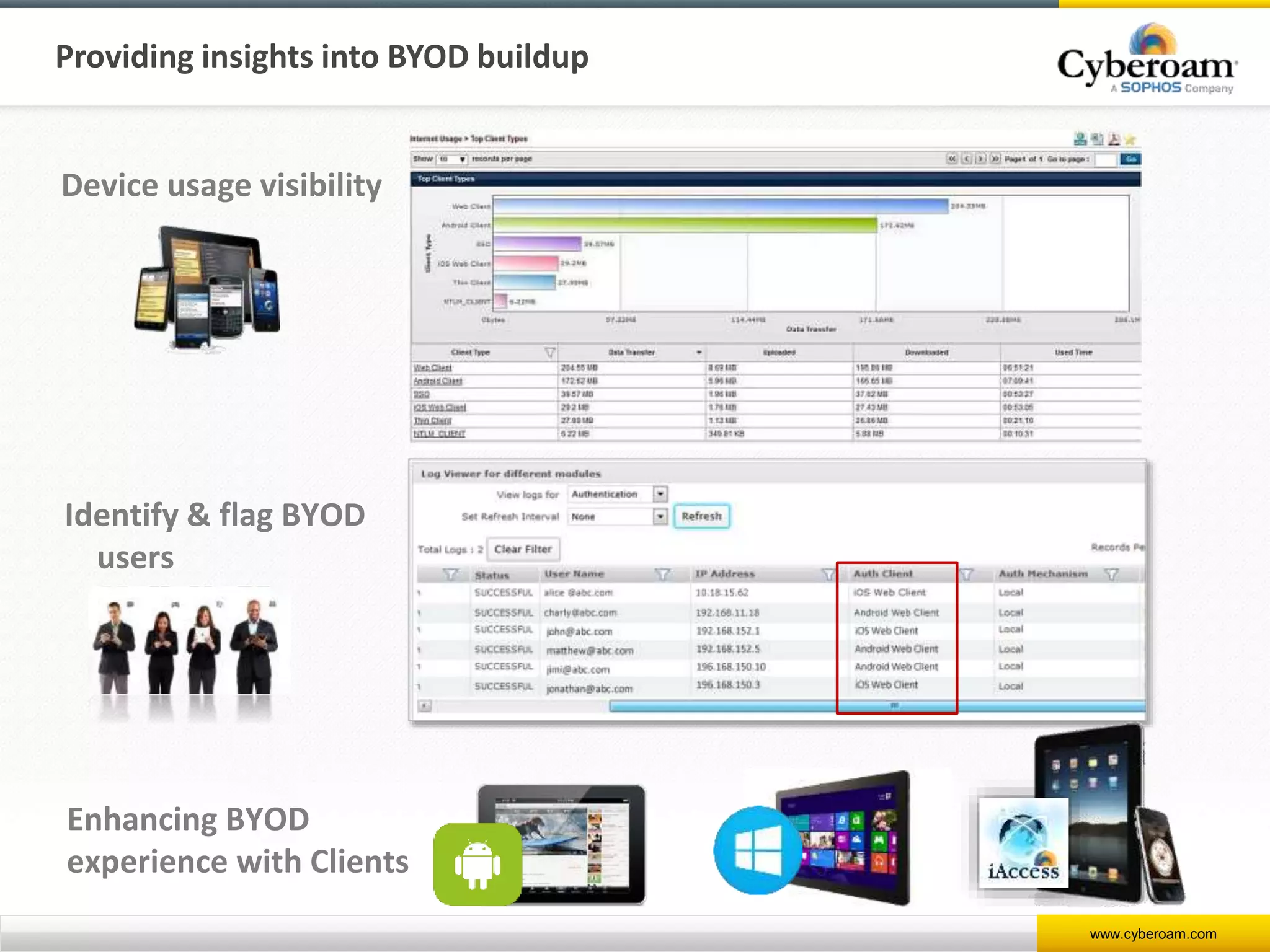
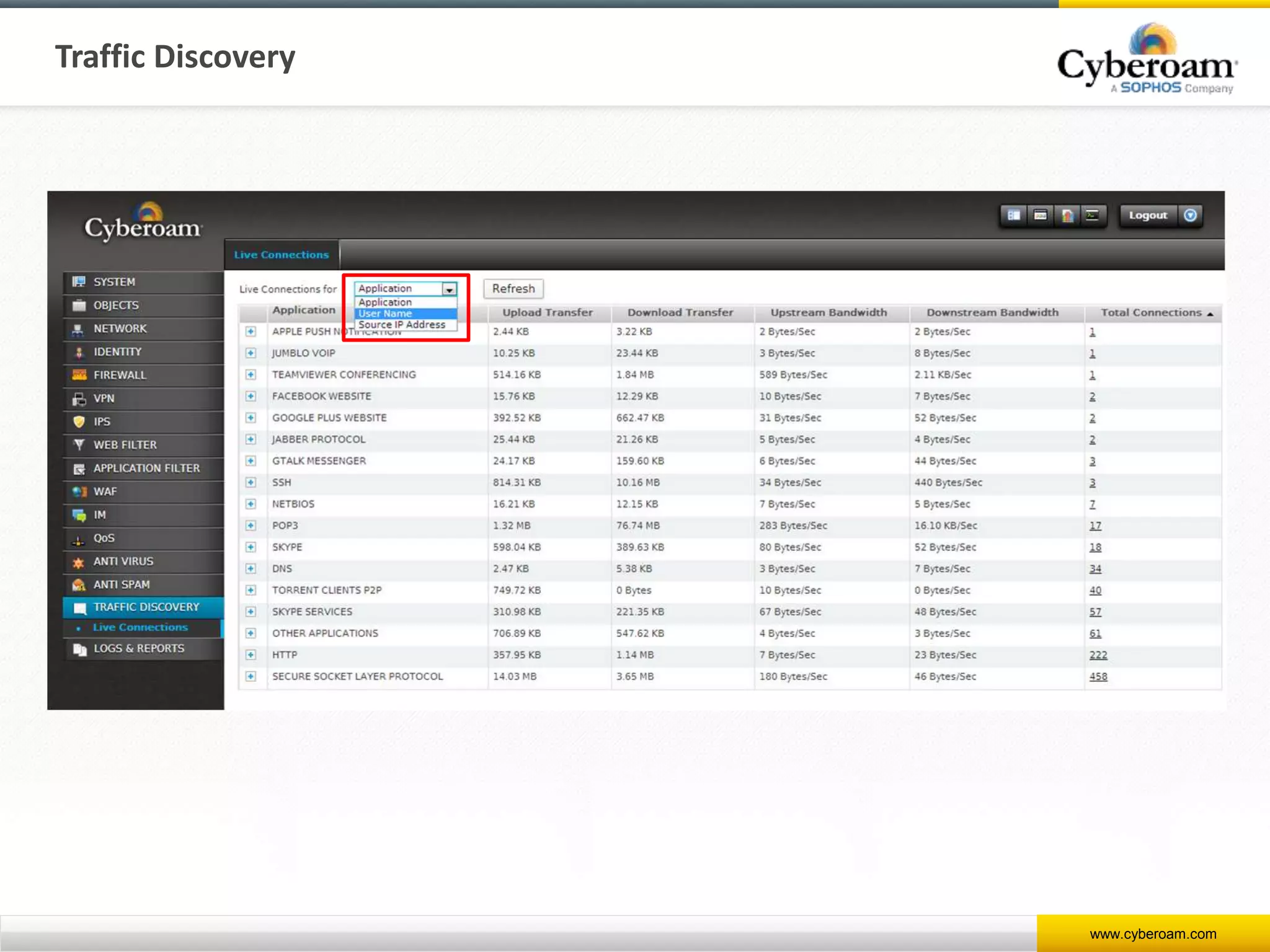
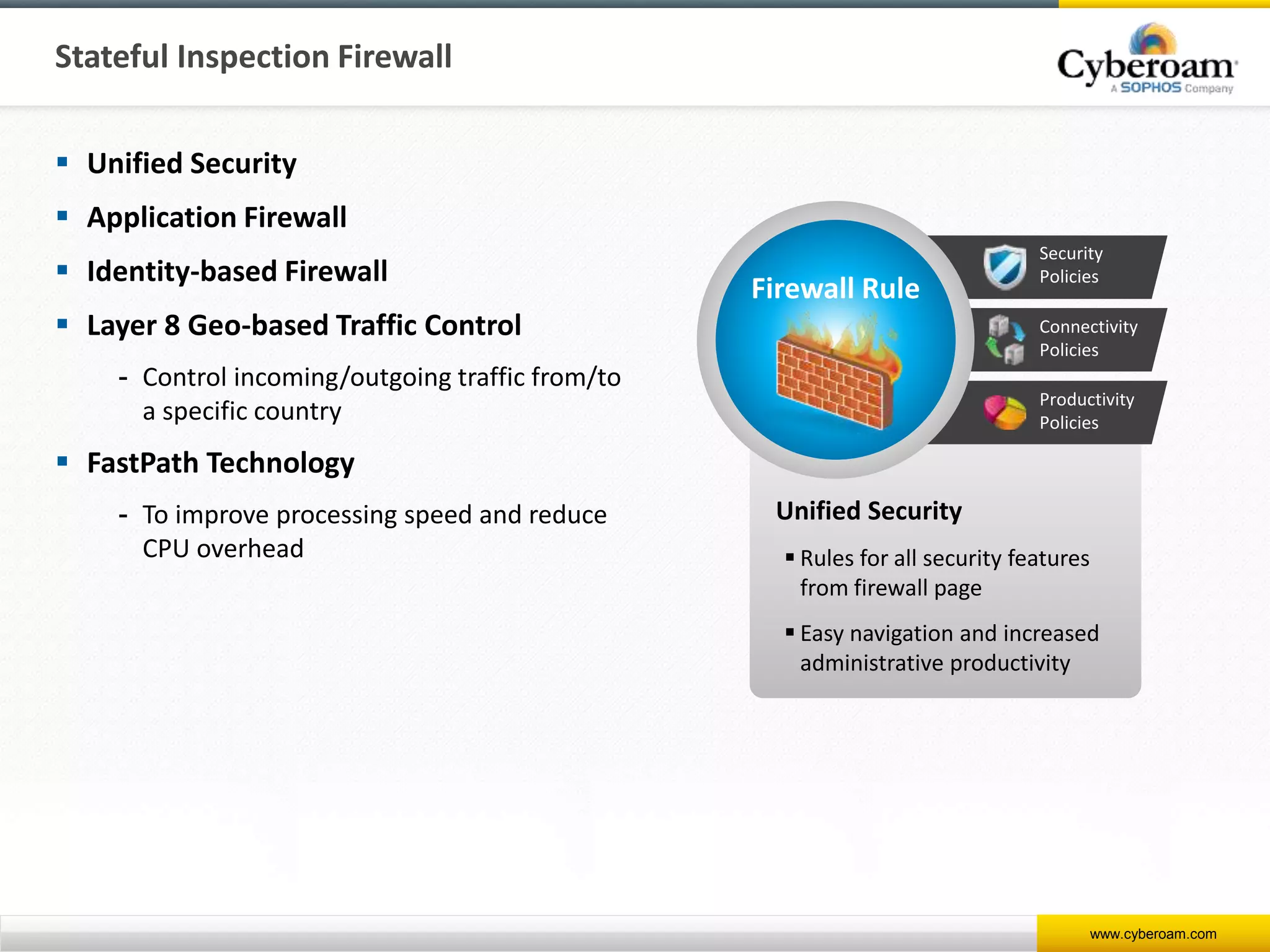
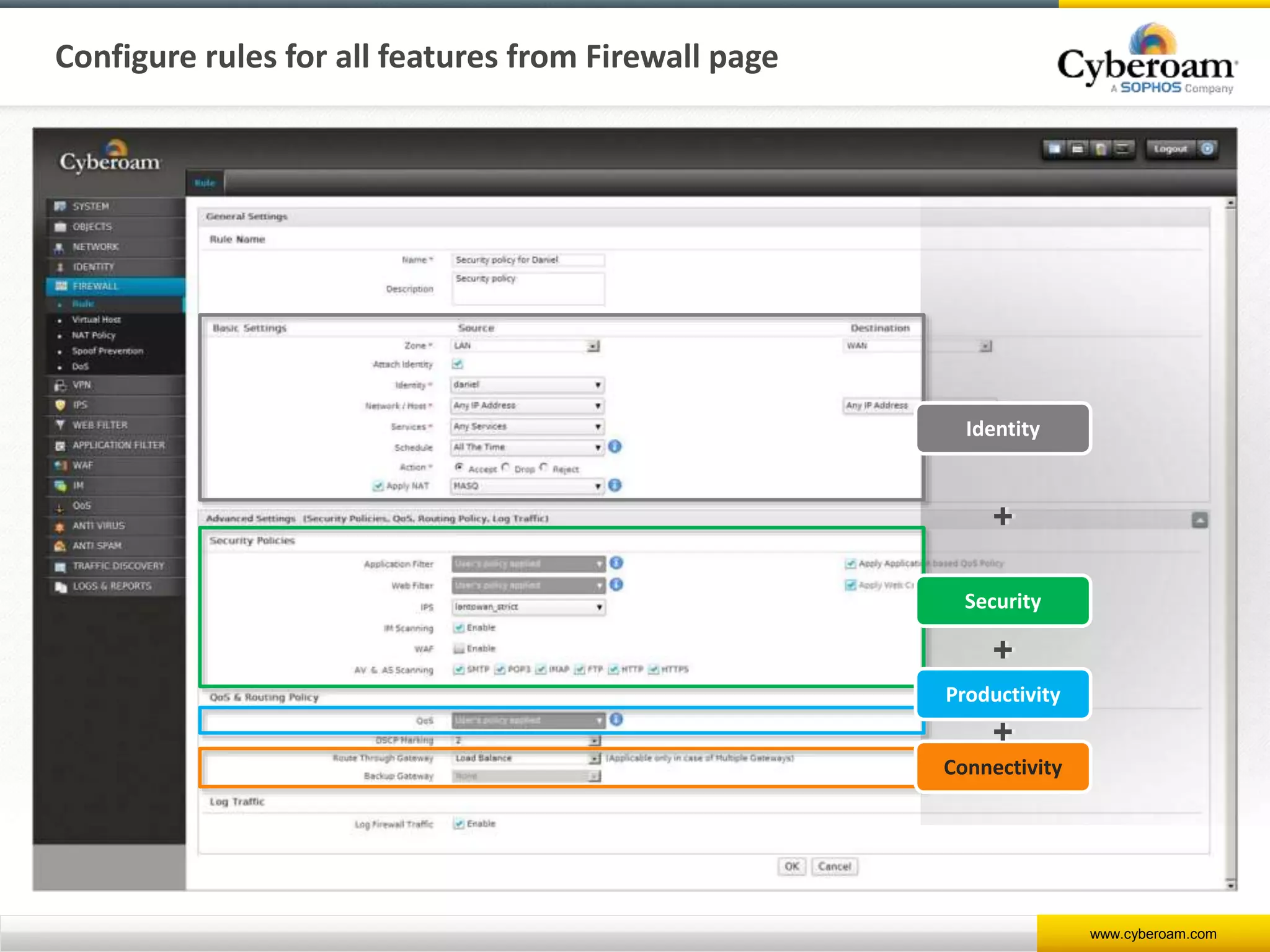
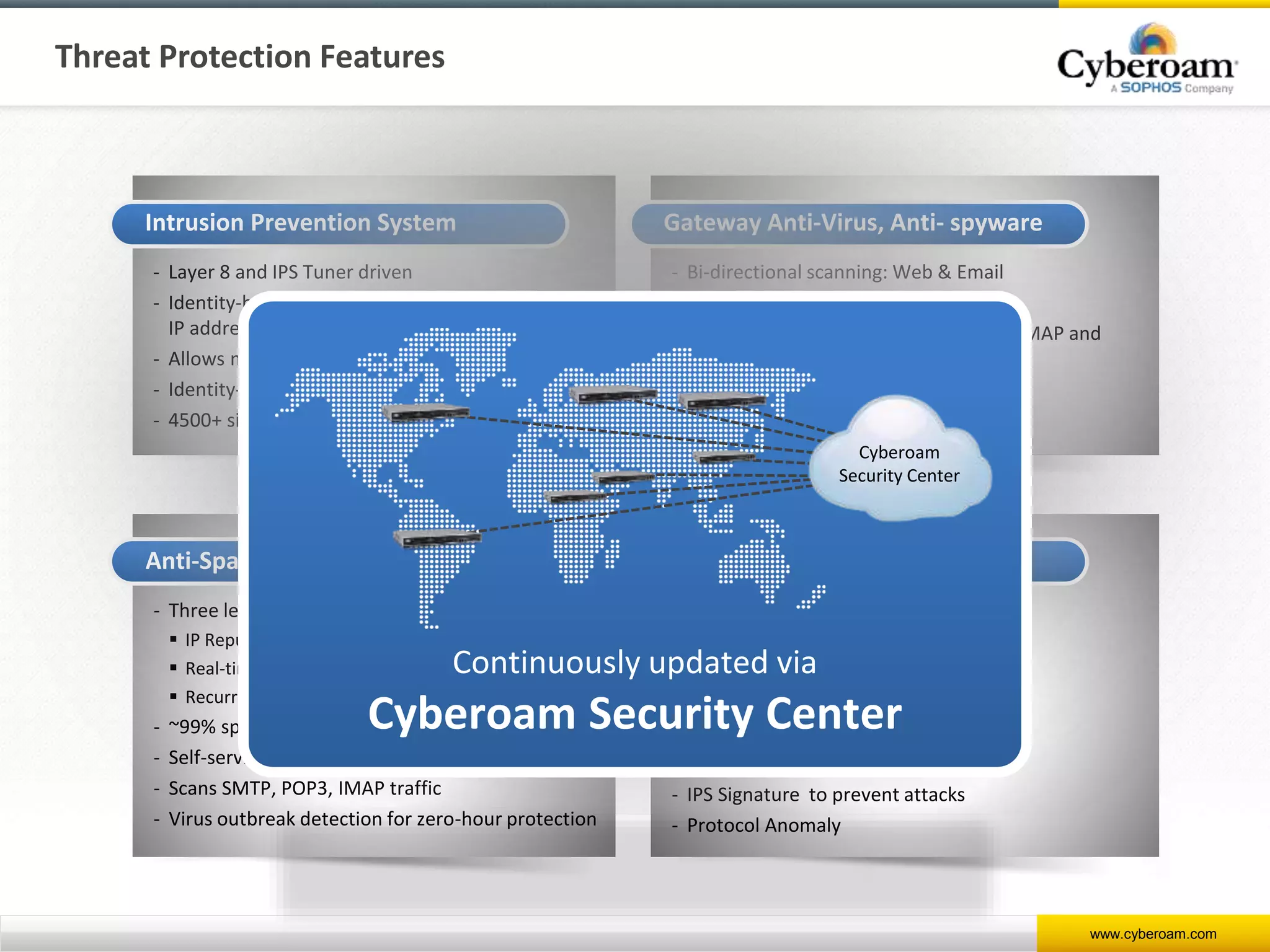
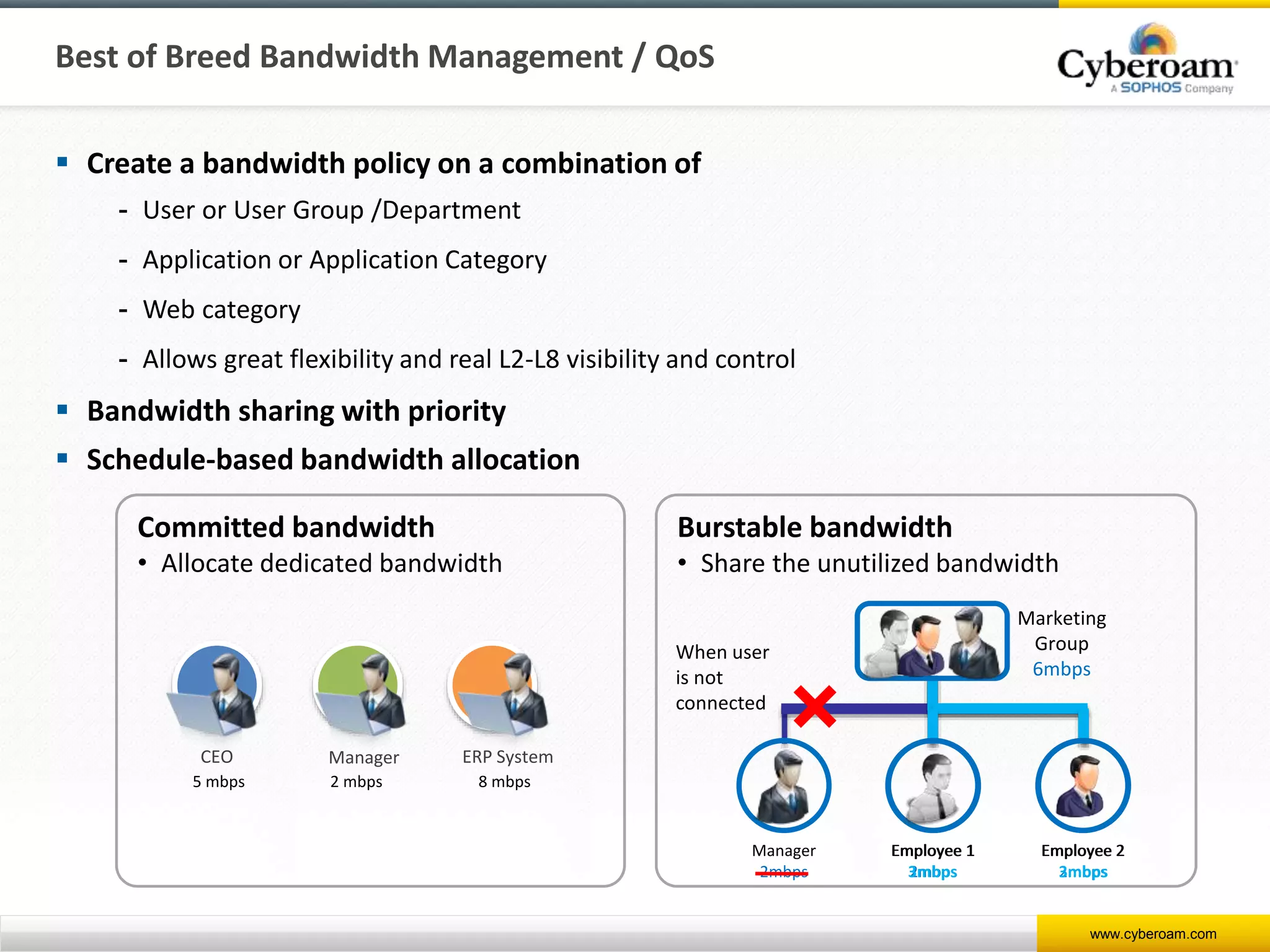
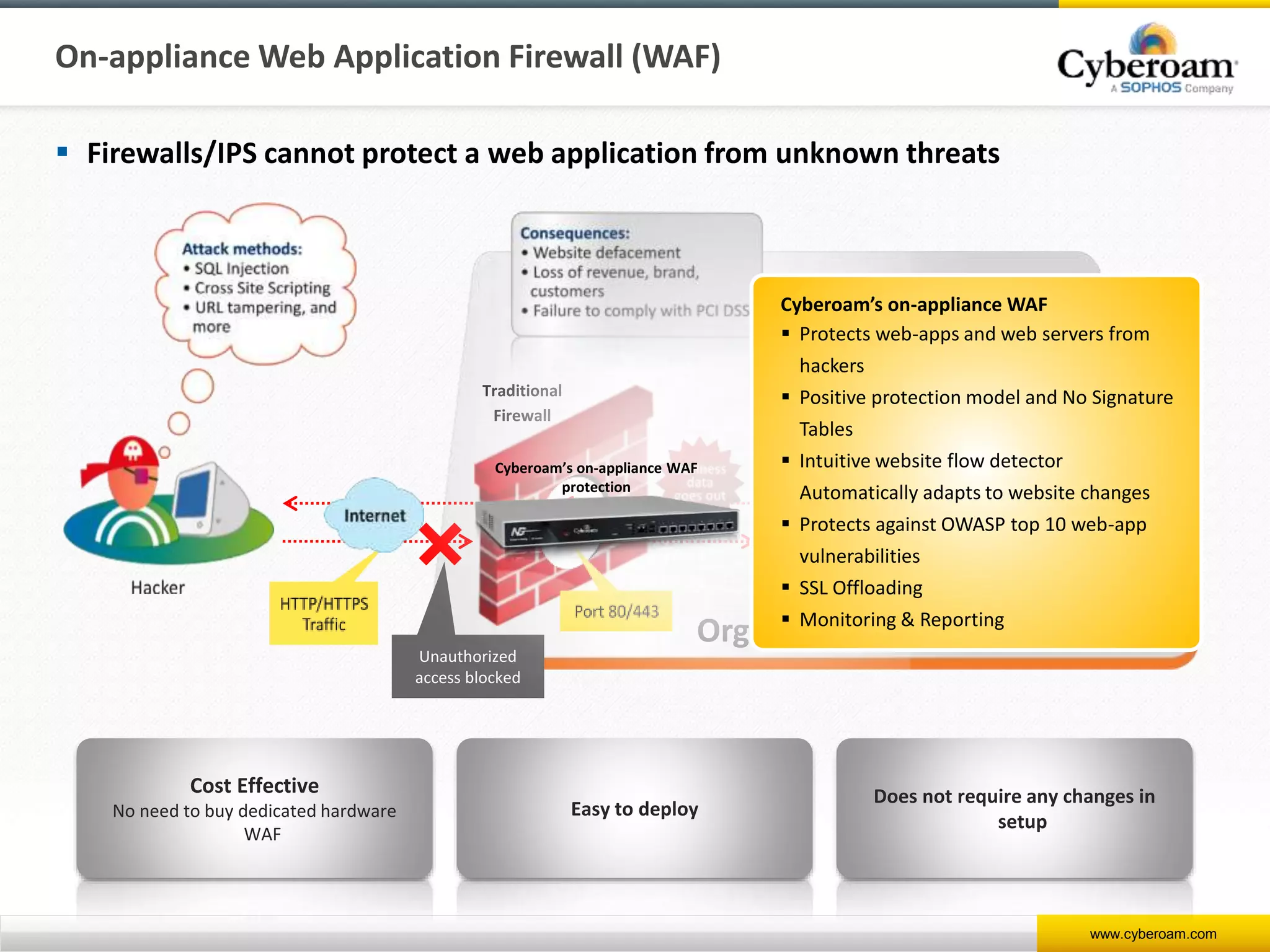
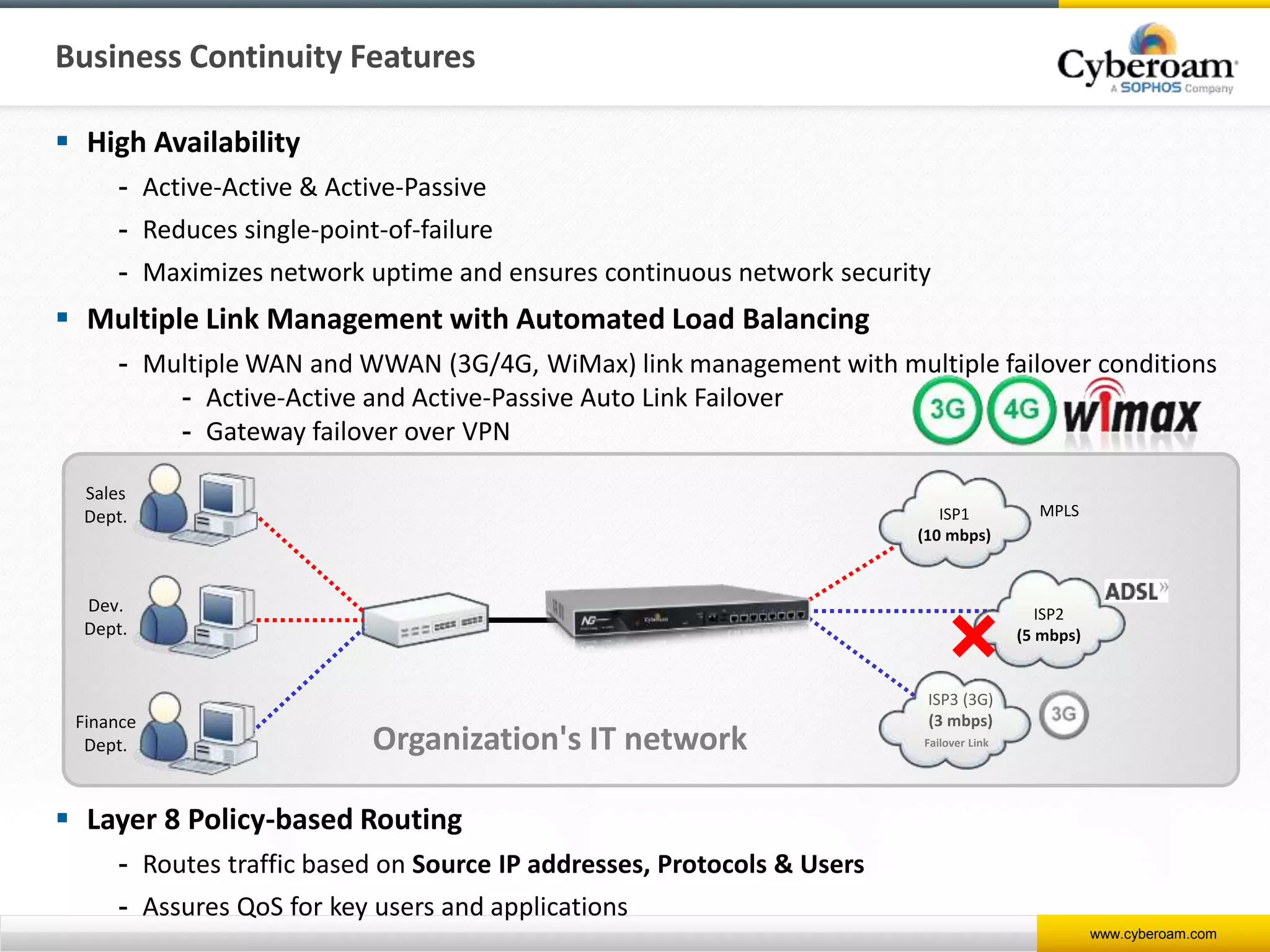
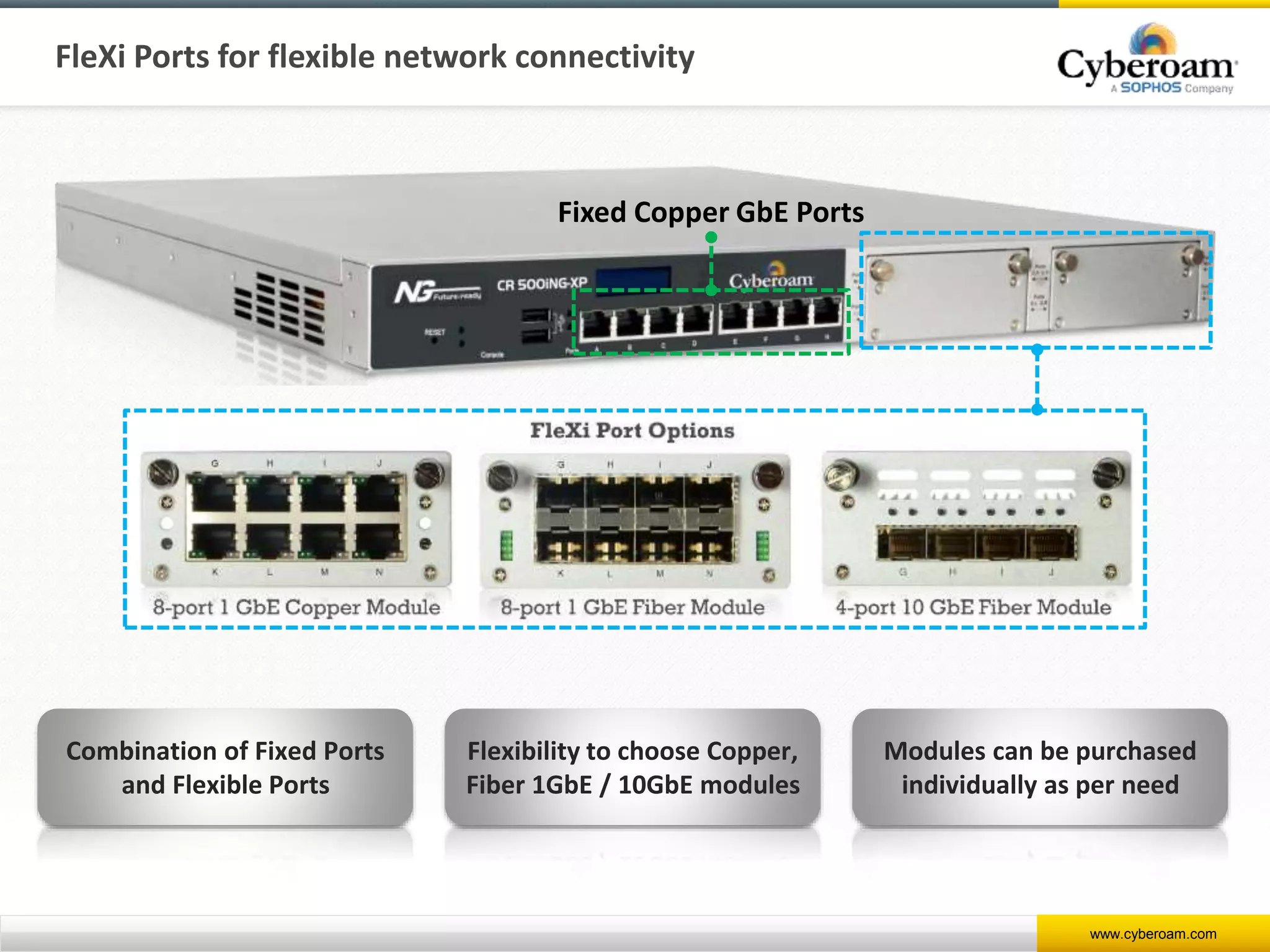
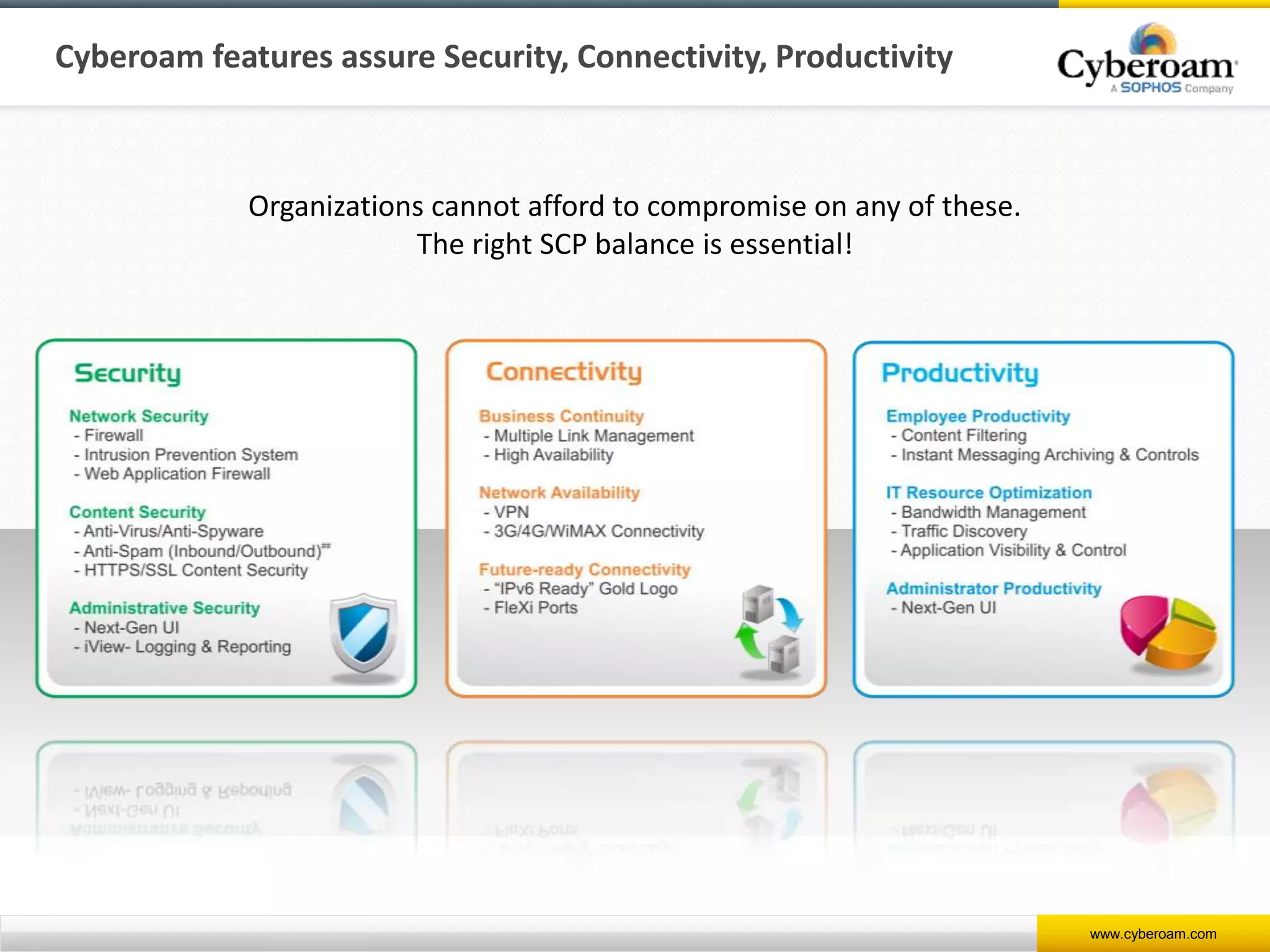
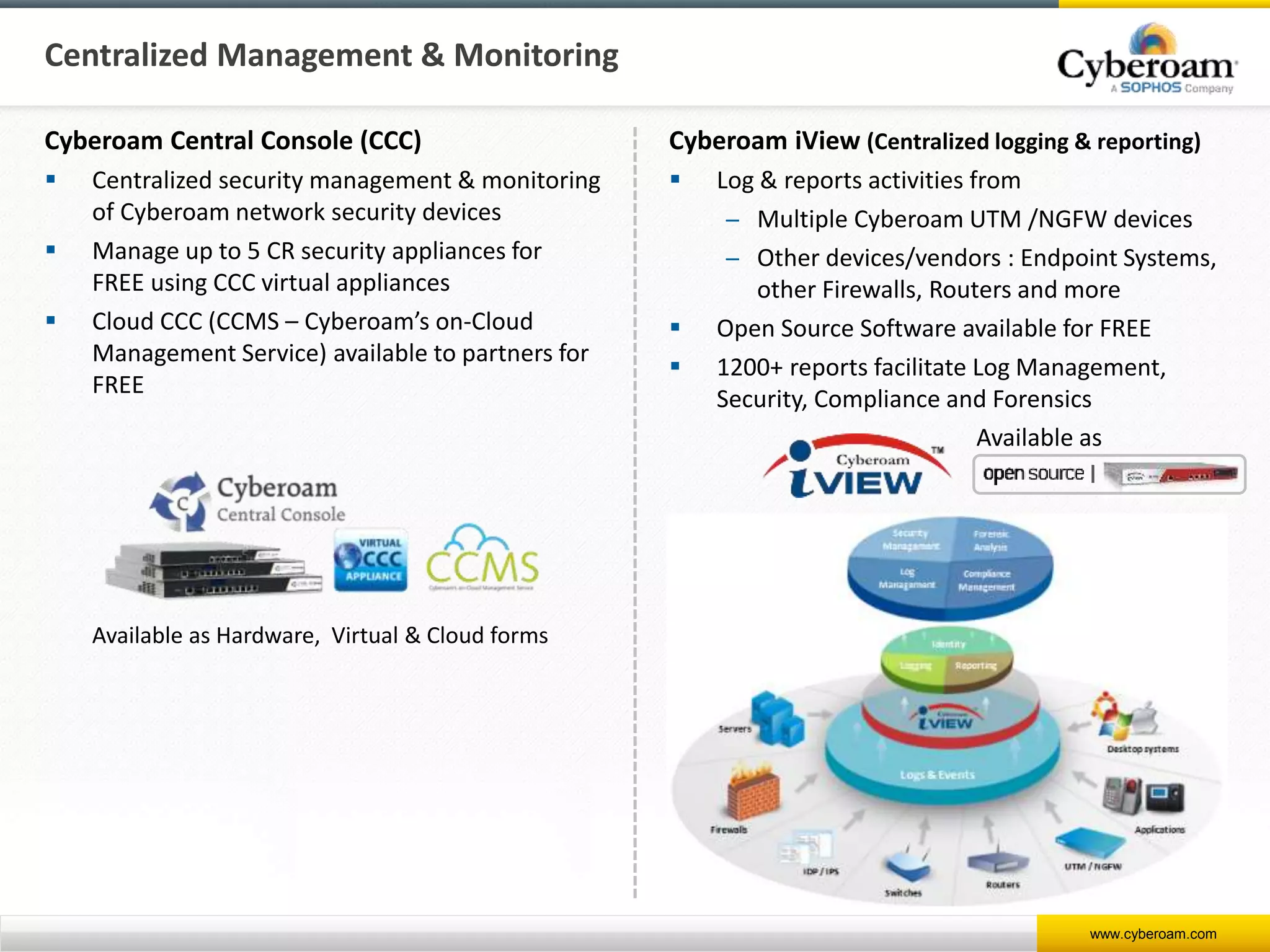
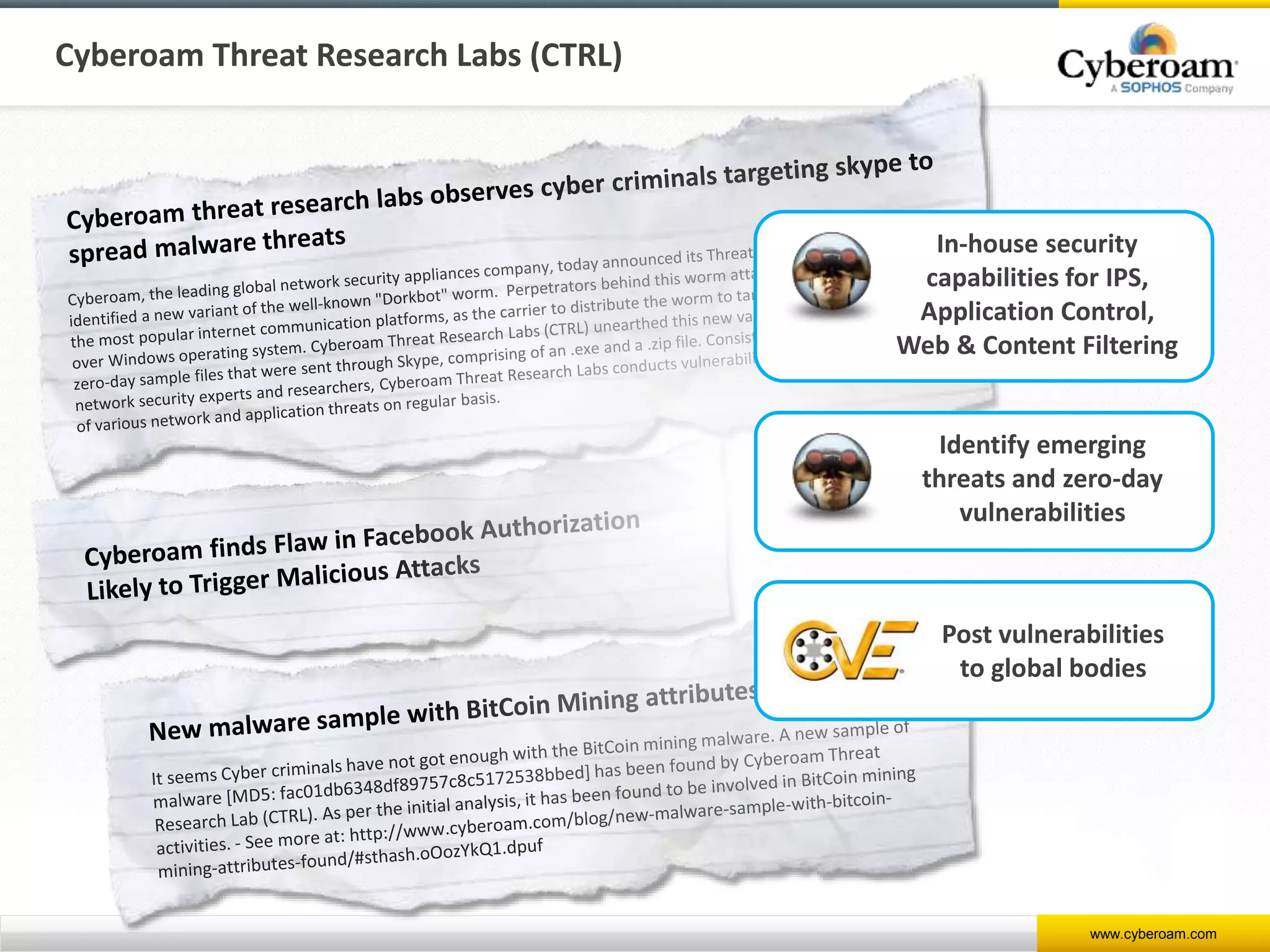
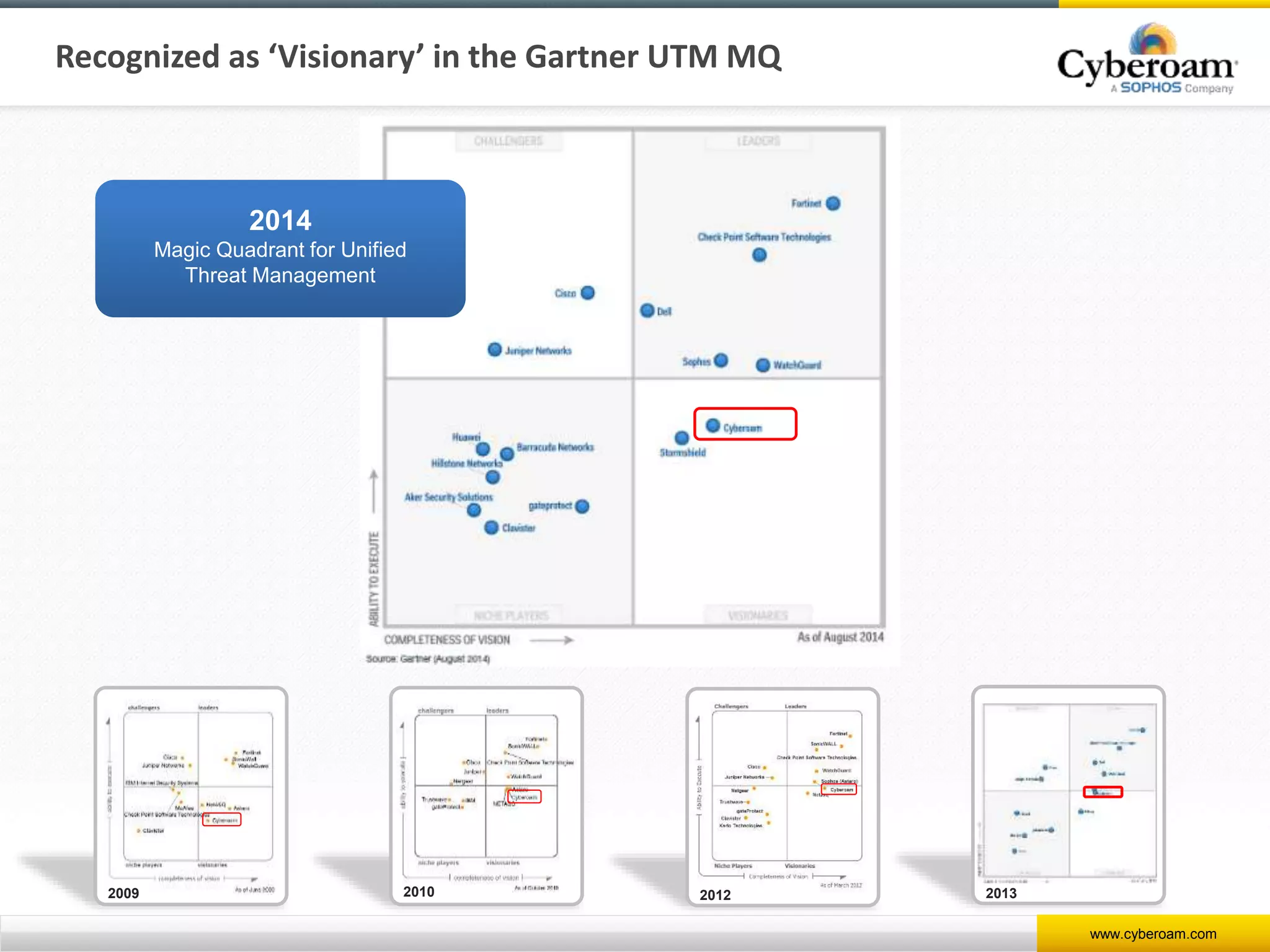
Cyberoam is a leading provider of network security appliances, offering next-generation firewall and unified threat management solutions for businesses globally. Their products feature advanced security capabilities, including identity-based management, web filtering, and multi-layered intrusion prevention, along with centralized management tools for monitoring and analysis. Cyberoam also supports various deployment options including hardware, virtual, and cloud, catering to diverse organizational needs across multiple industries.