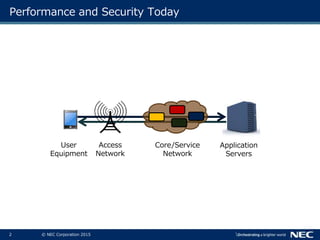
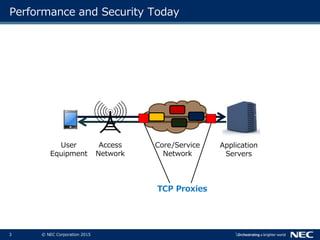
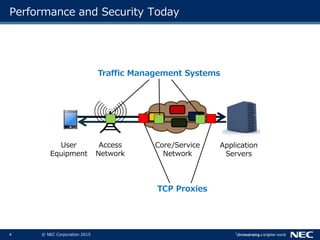
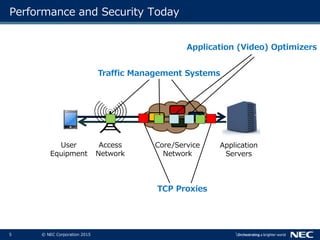
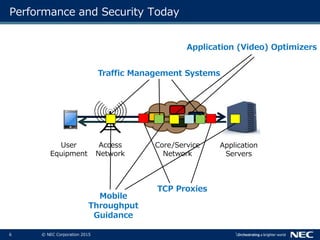
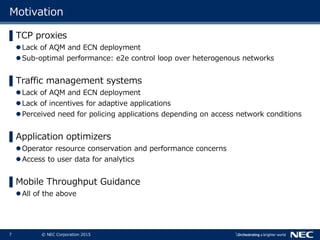
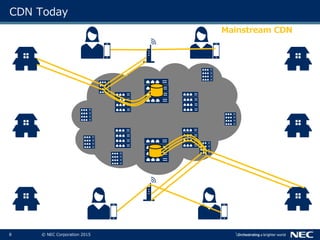
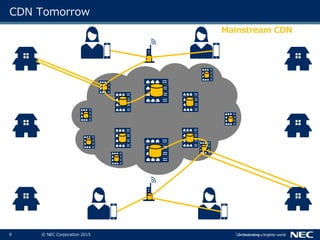
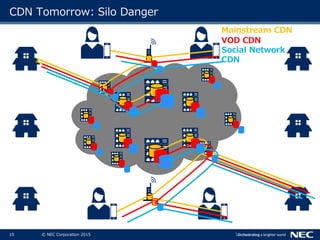
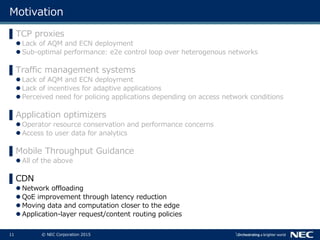
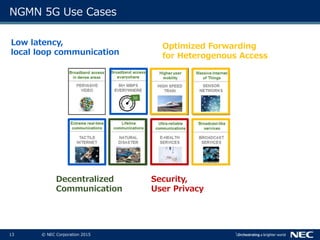
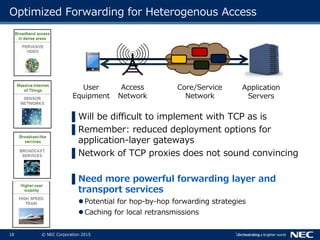
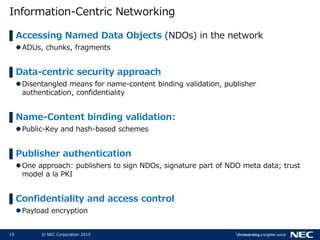
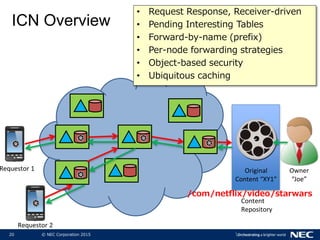
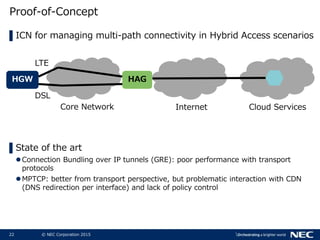
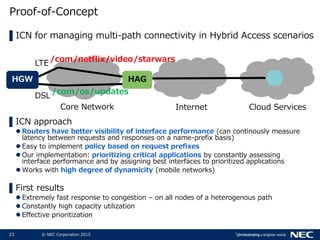
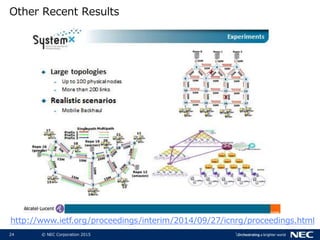
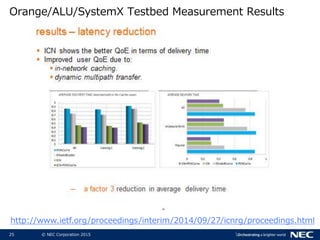
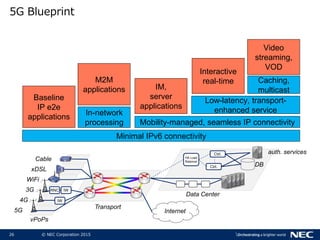
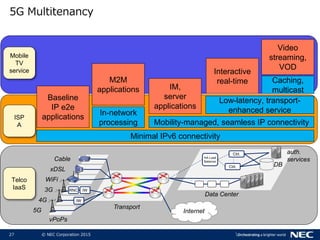
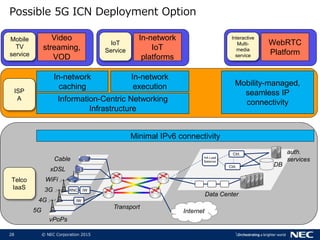
The document discusses performance and security challenges in 5G networks. It describes current approaches like TCP proxies, traffic management systems, and application optimizers that are used but have limitations. It proposes that information-centric networking (ICN) could help address issues with heterogeneous access networks, ubiquitous caching, mobility, and security in 5G. The document summarizes results from ICN testbeds and provides an example of how ICN could be deployed in a 5G network to improve performance for various use cases while allowing for multitenancy. Key challenges for 5G include user privacy with encrypted traffic and supporting diverse performance needs across heterogeneous networks.