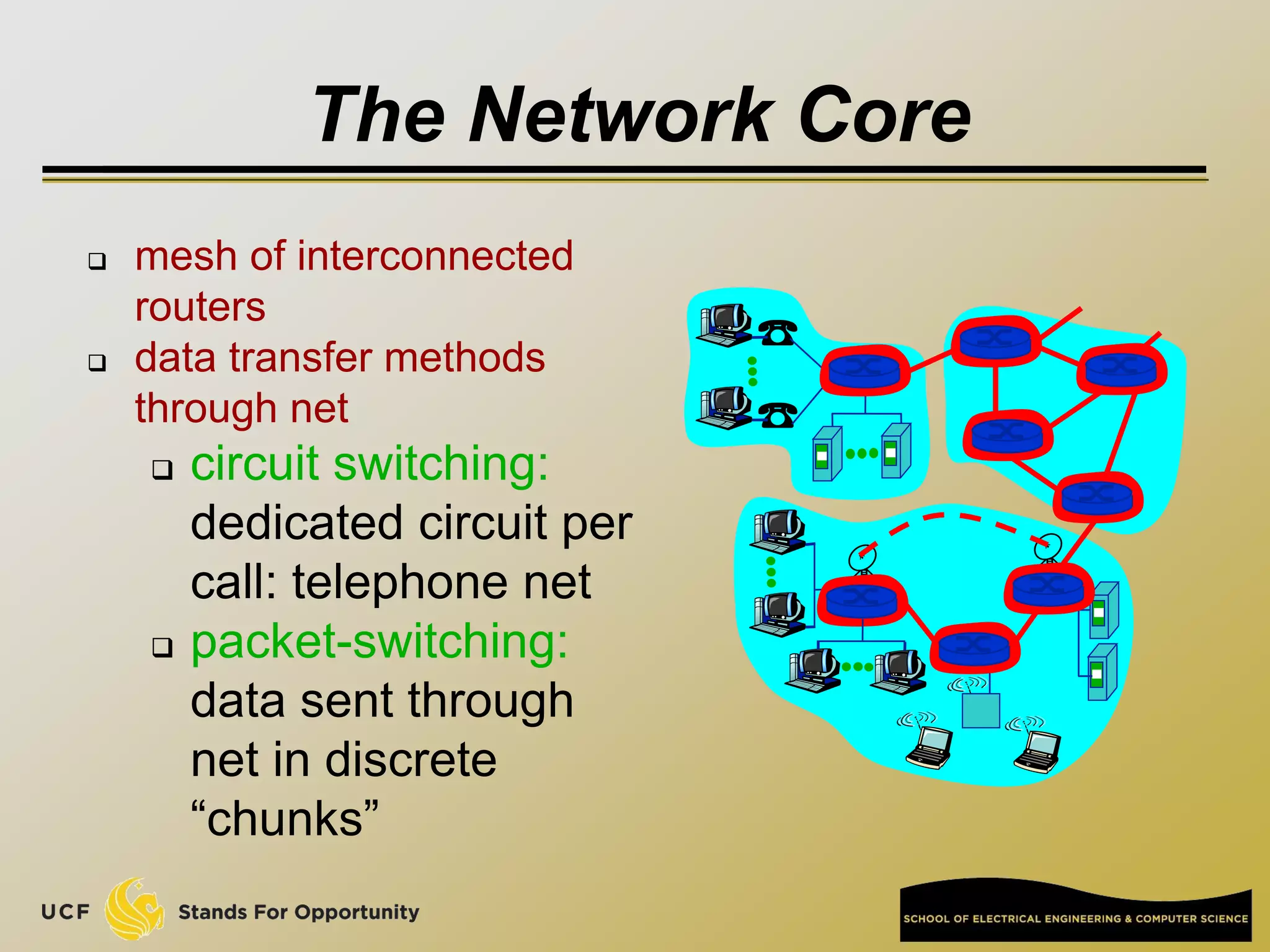
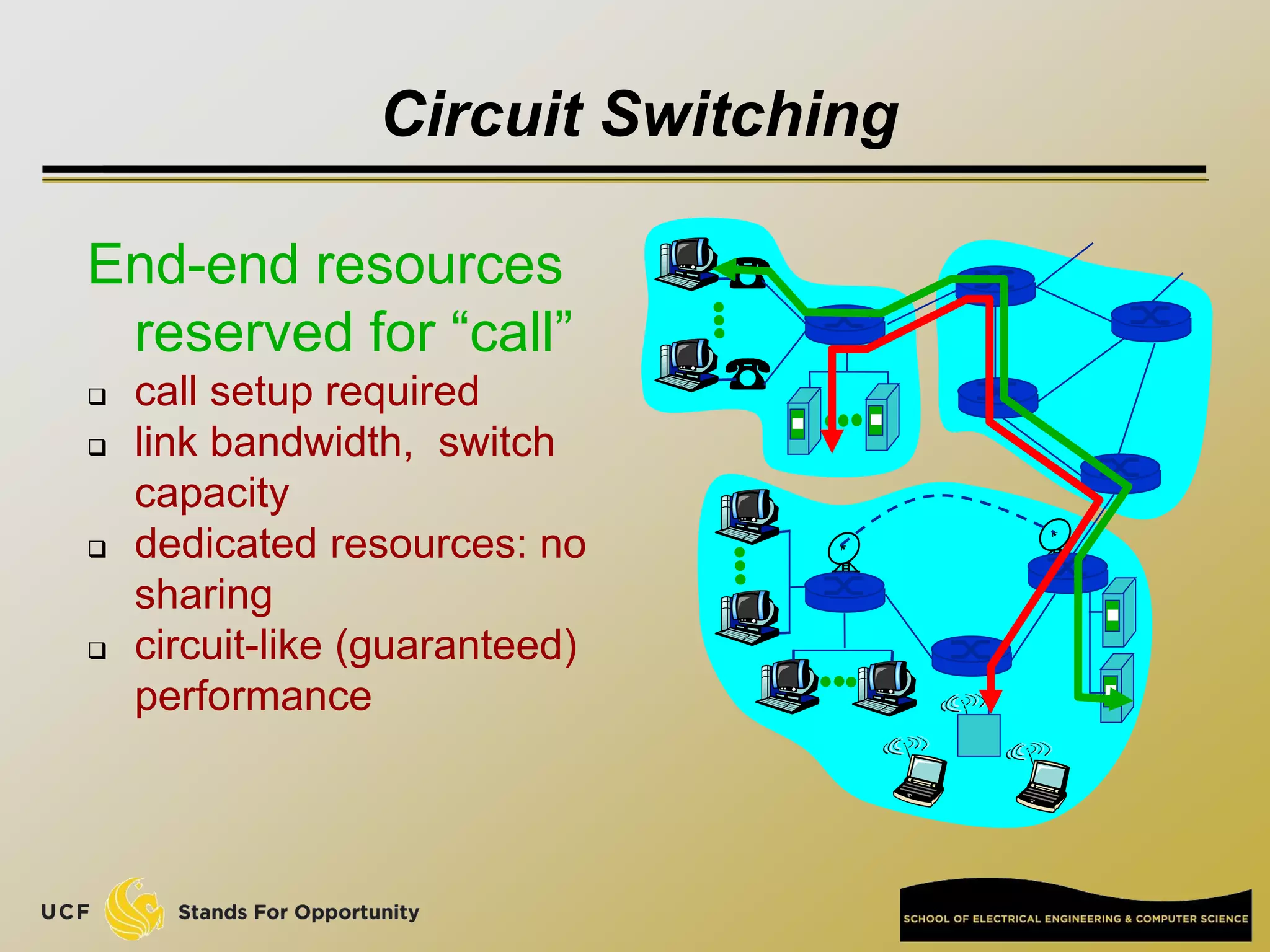
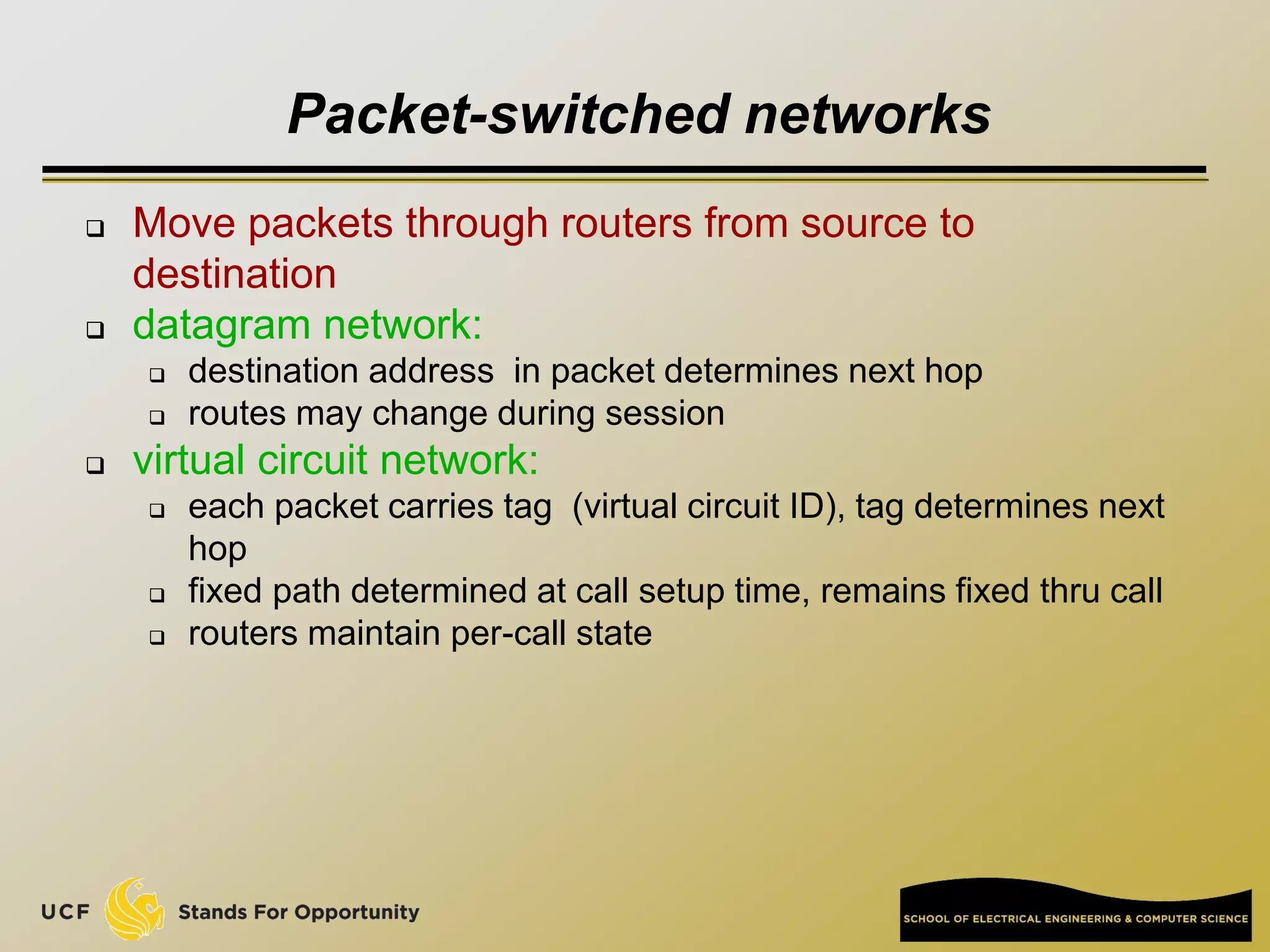
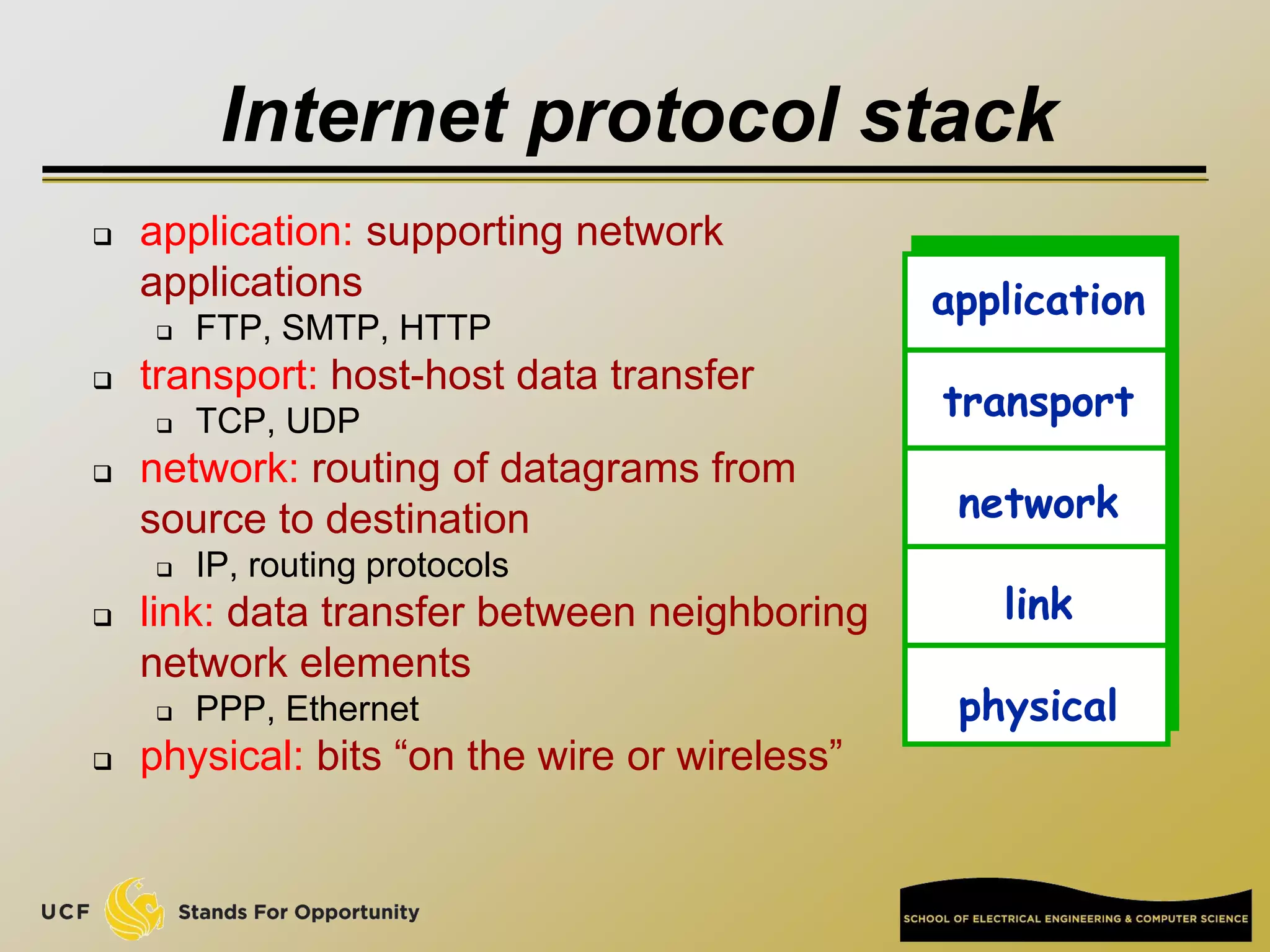
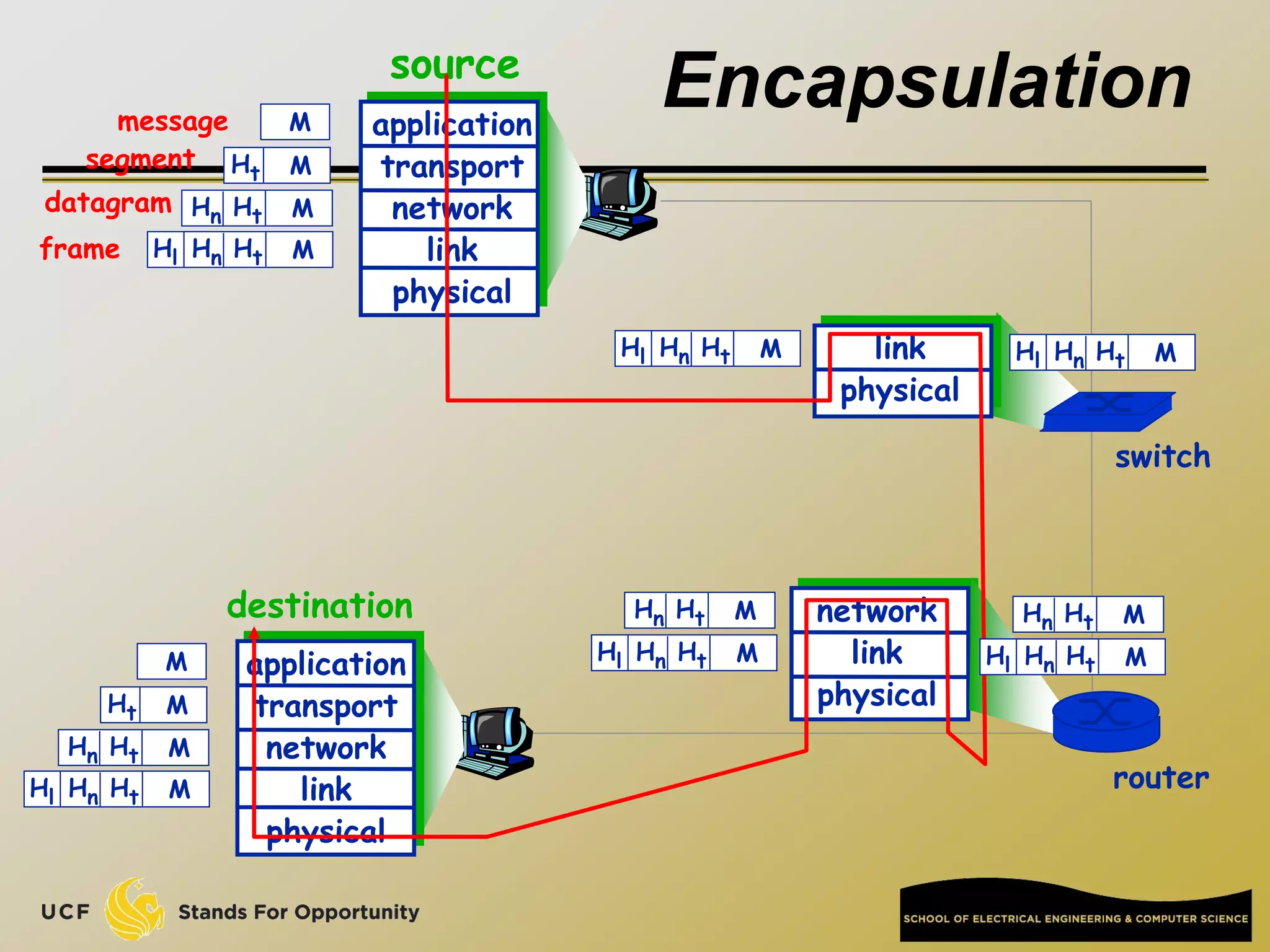
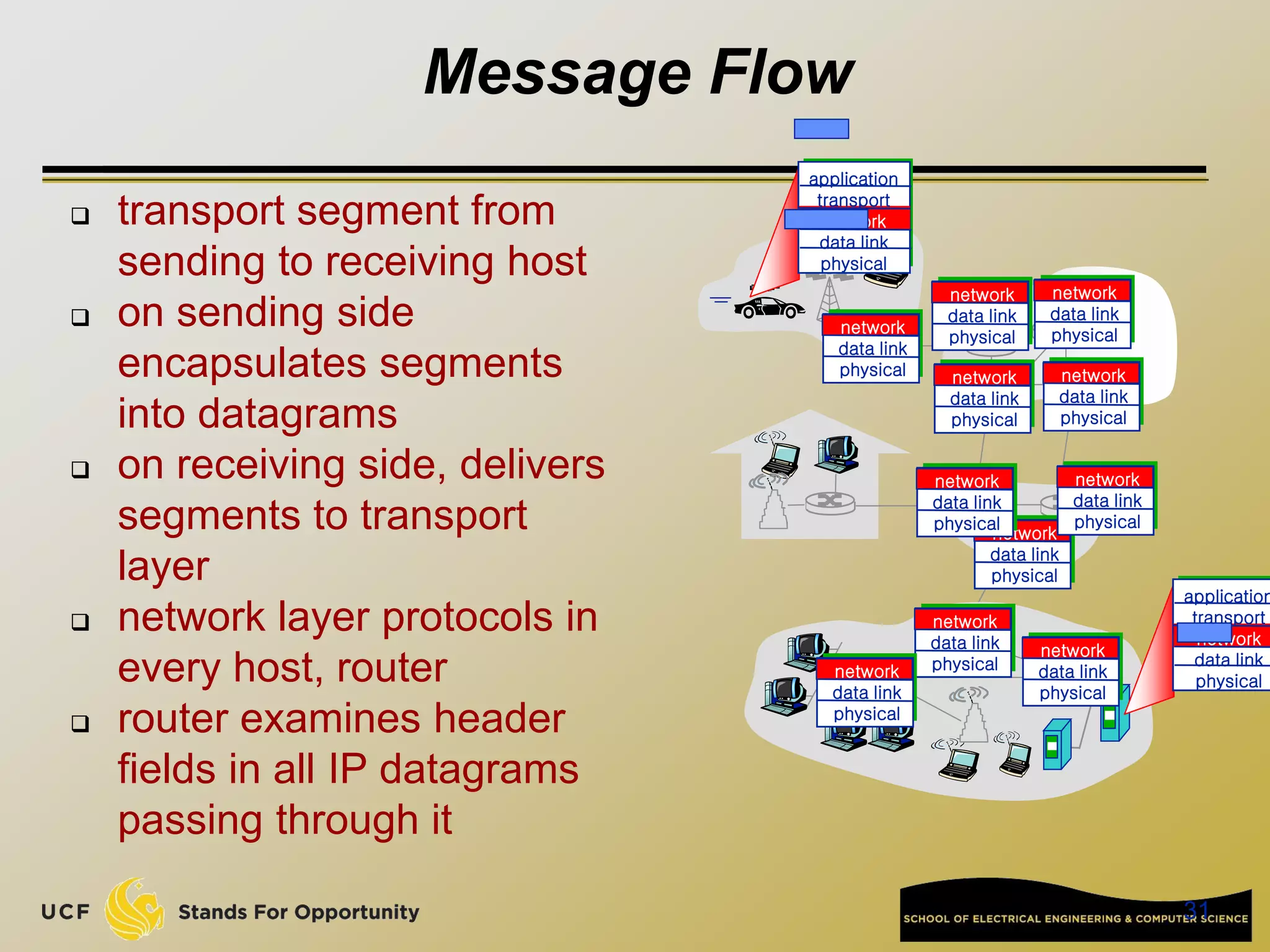
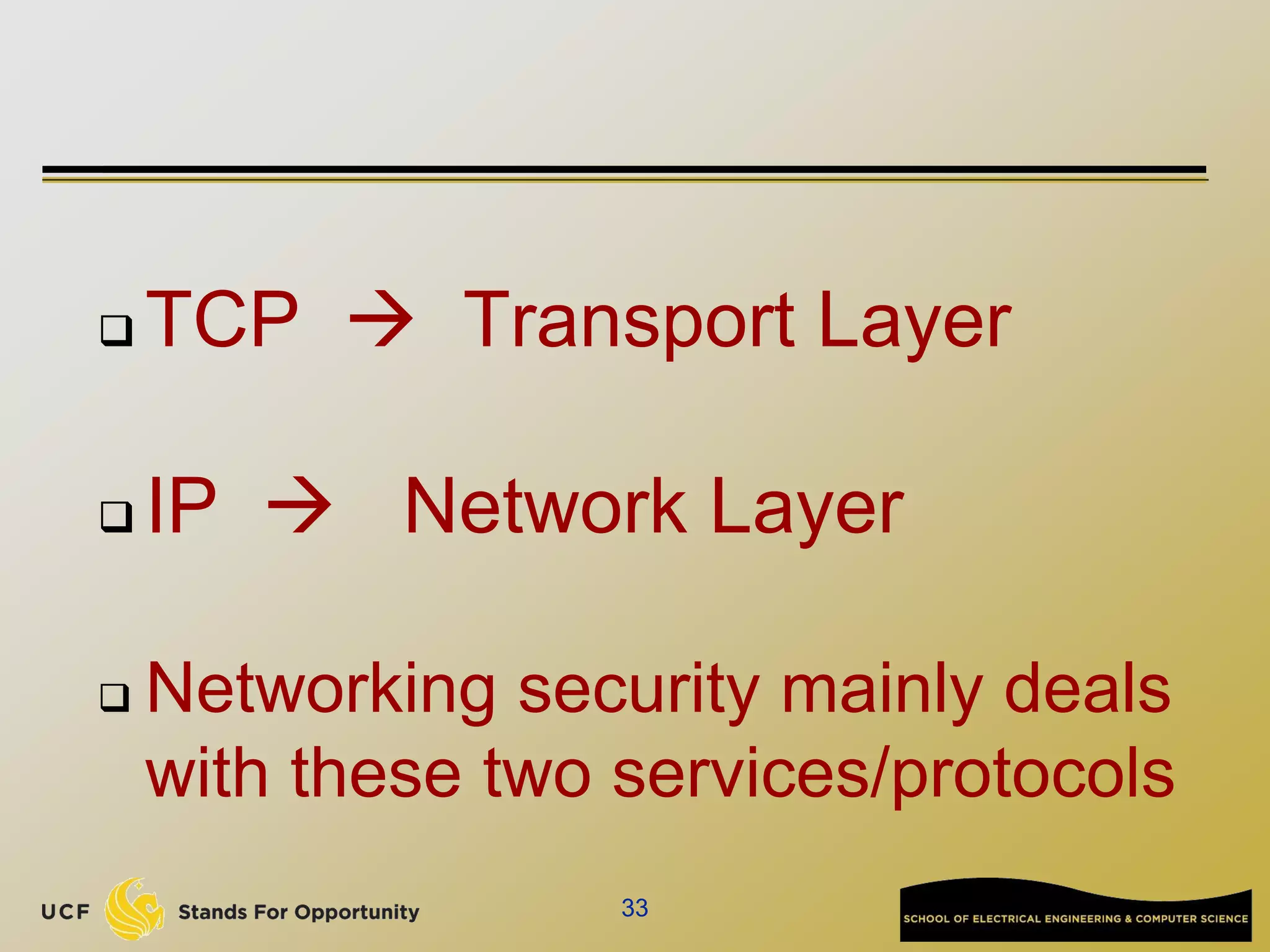
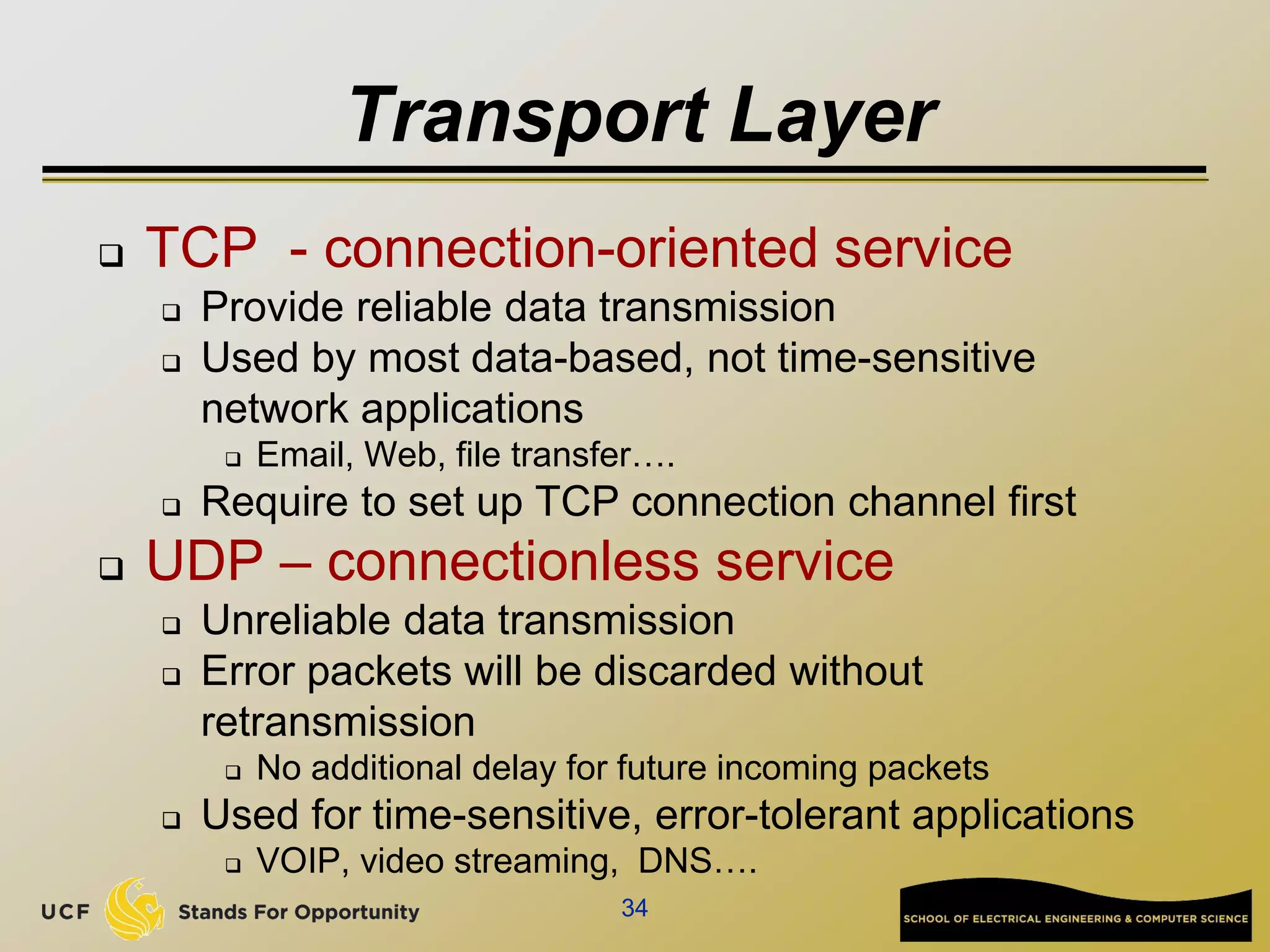
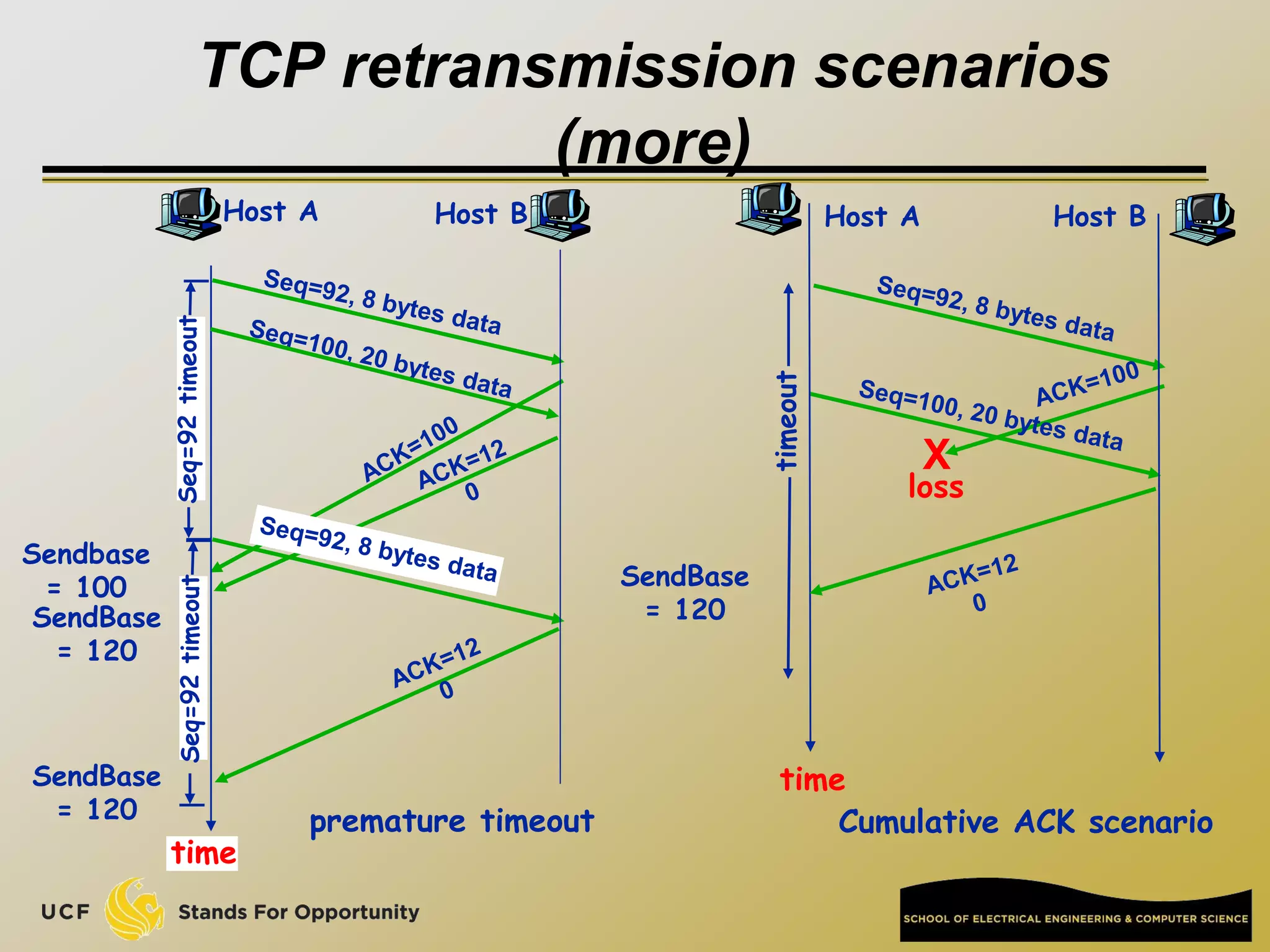
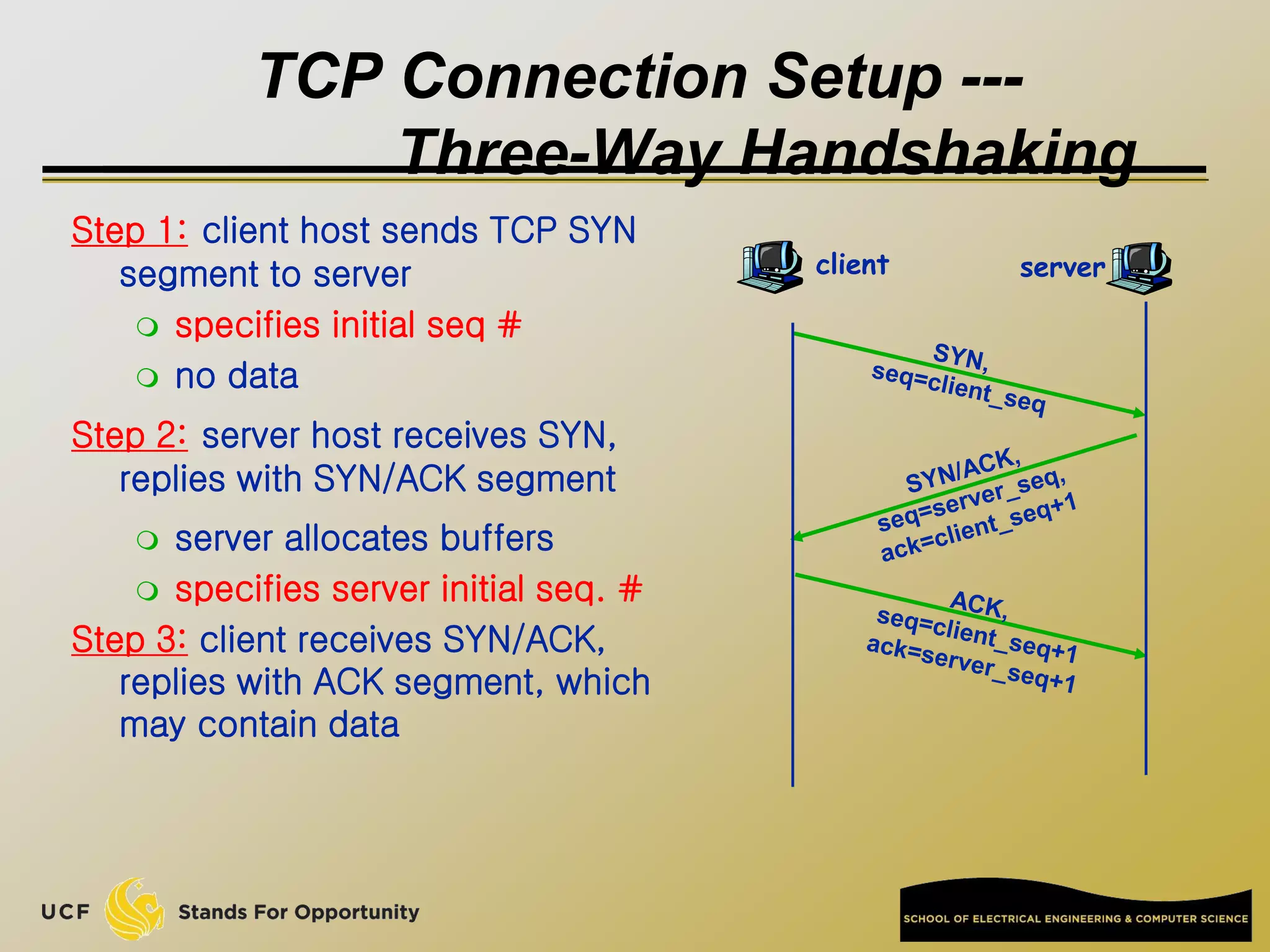
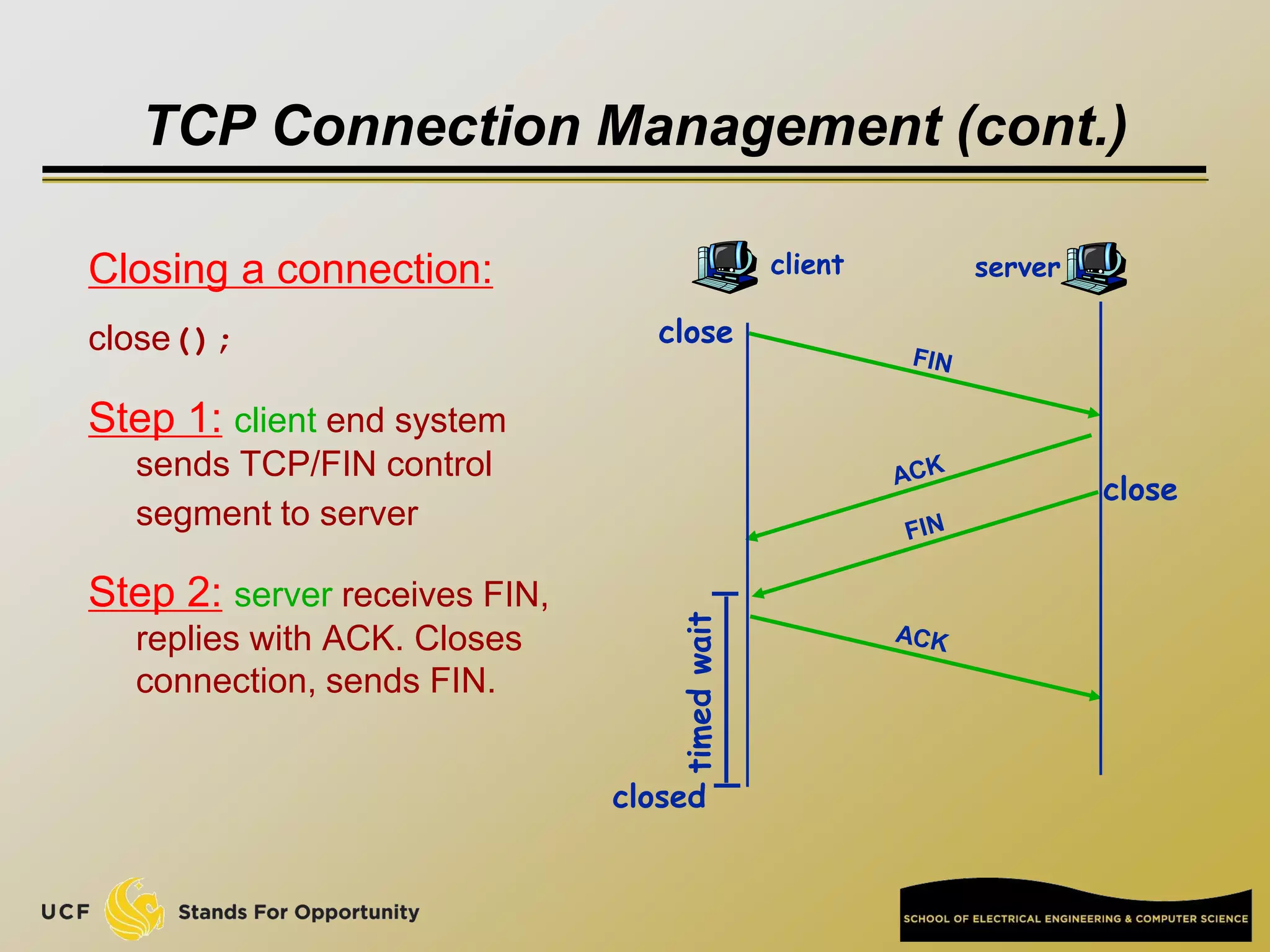
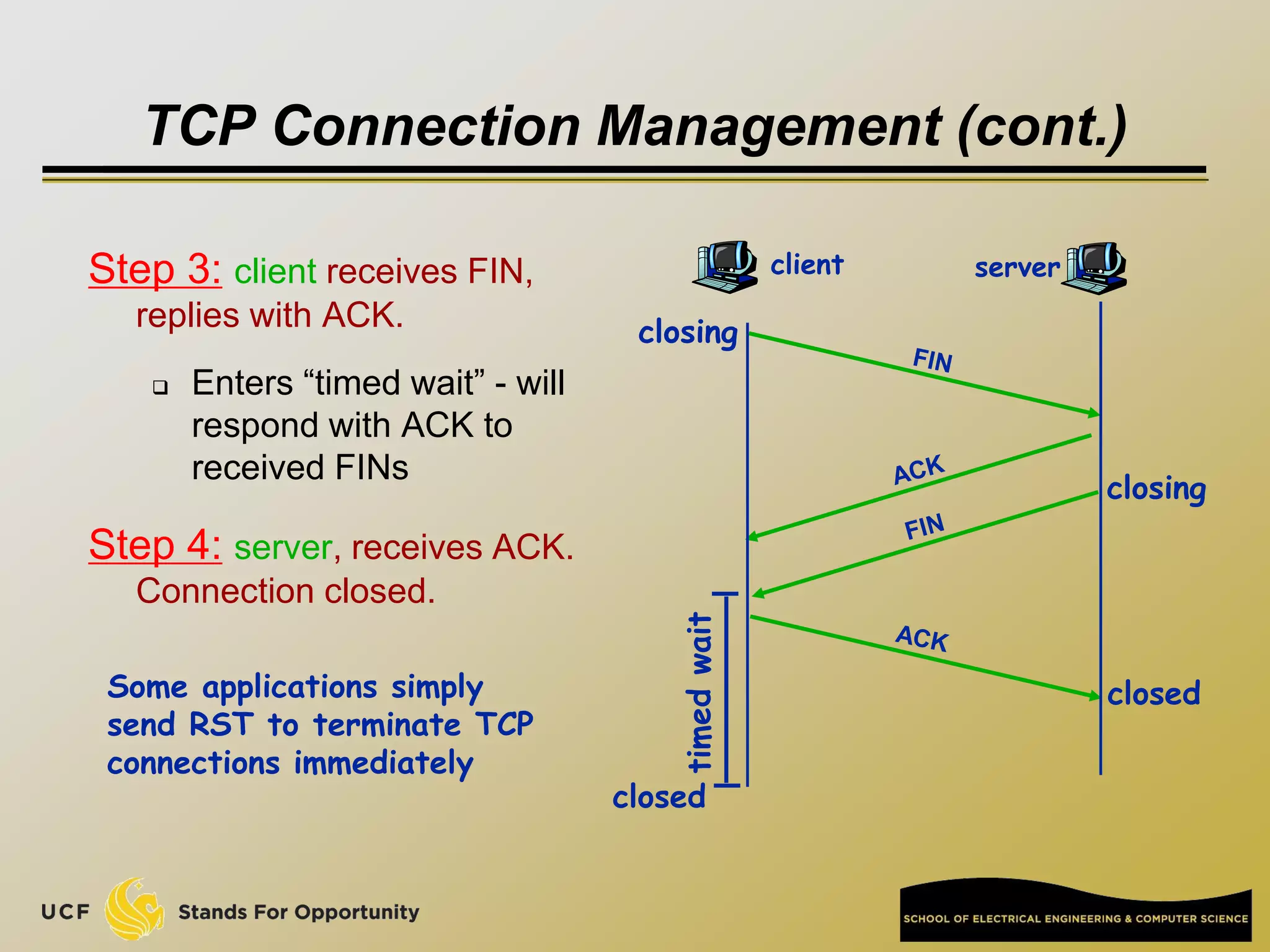
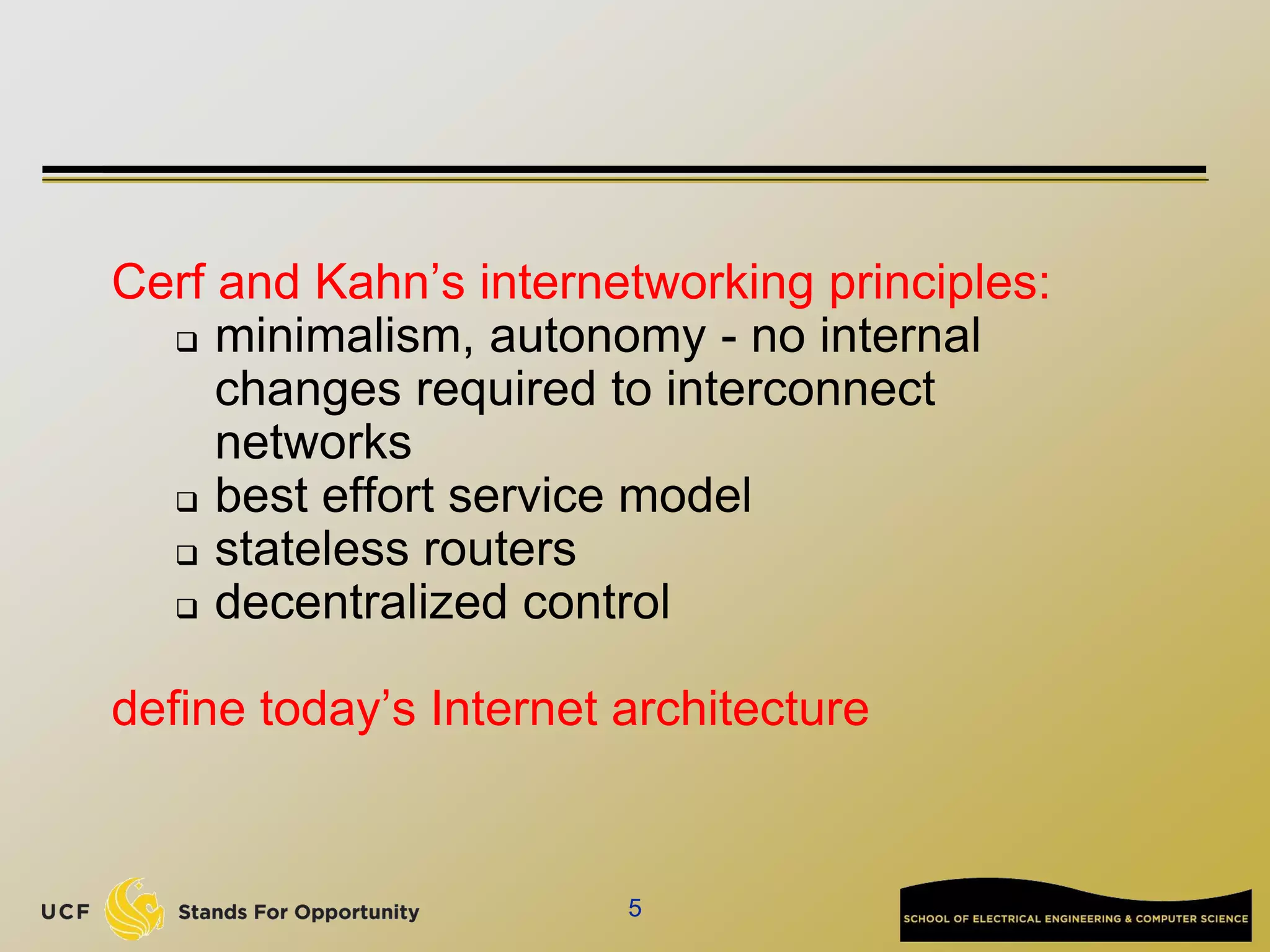
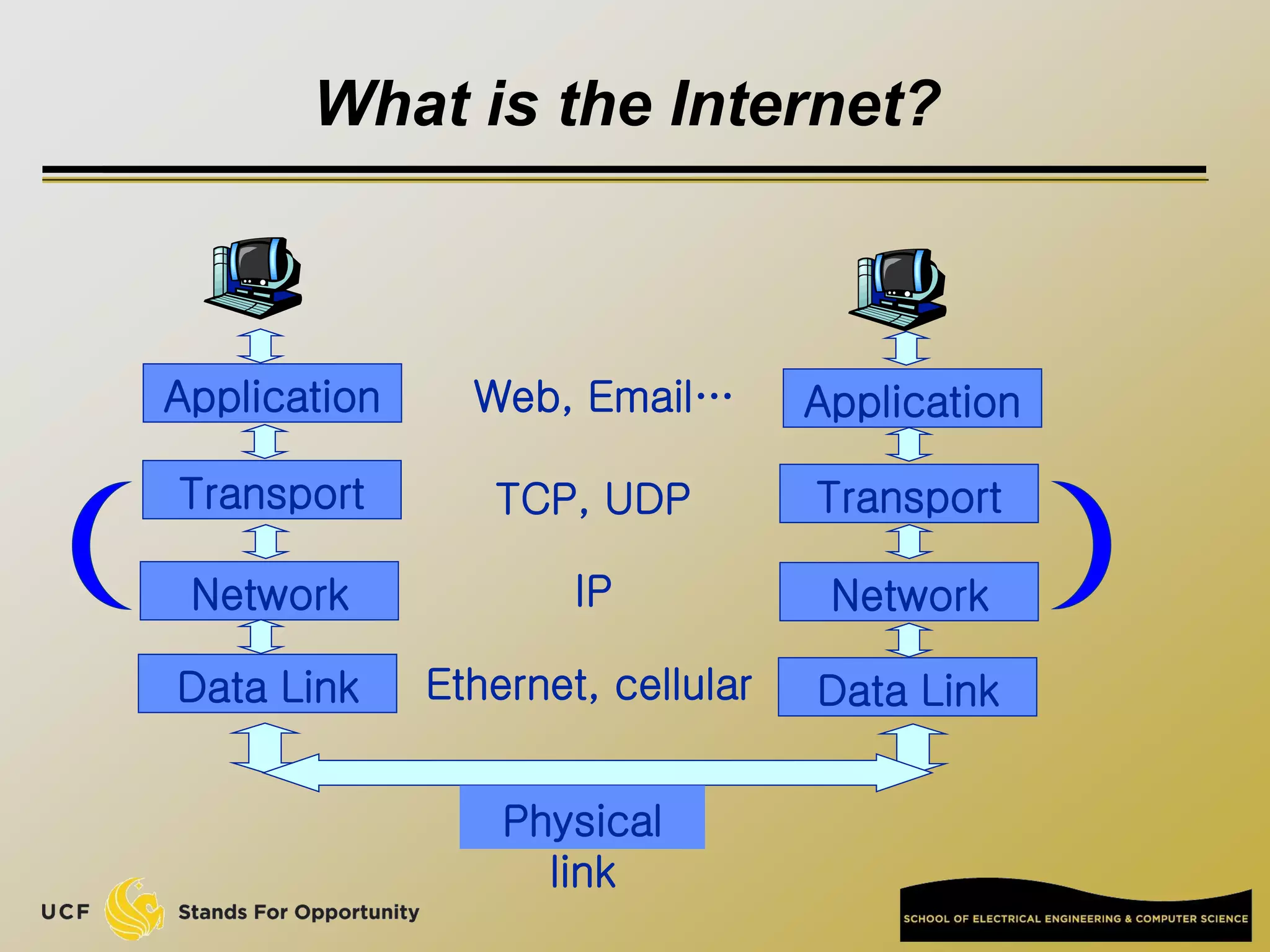
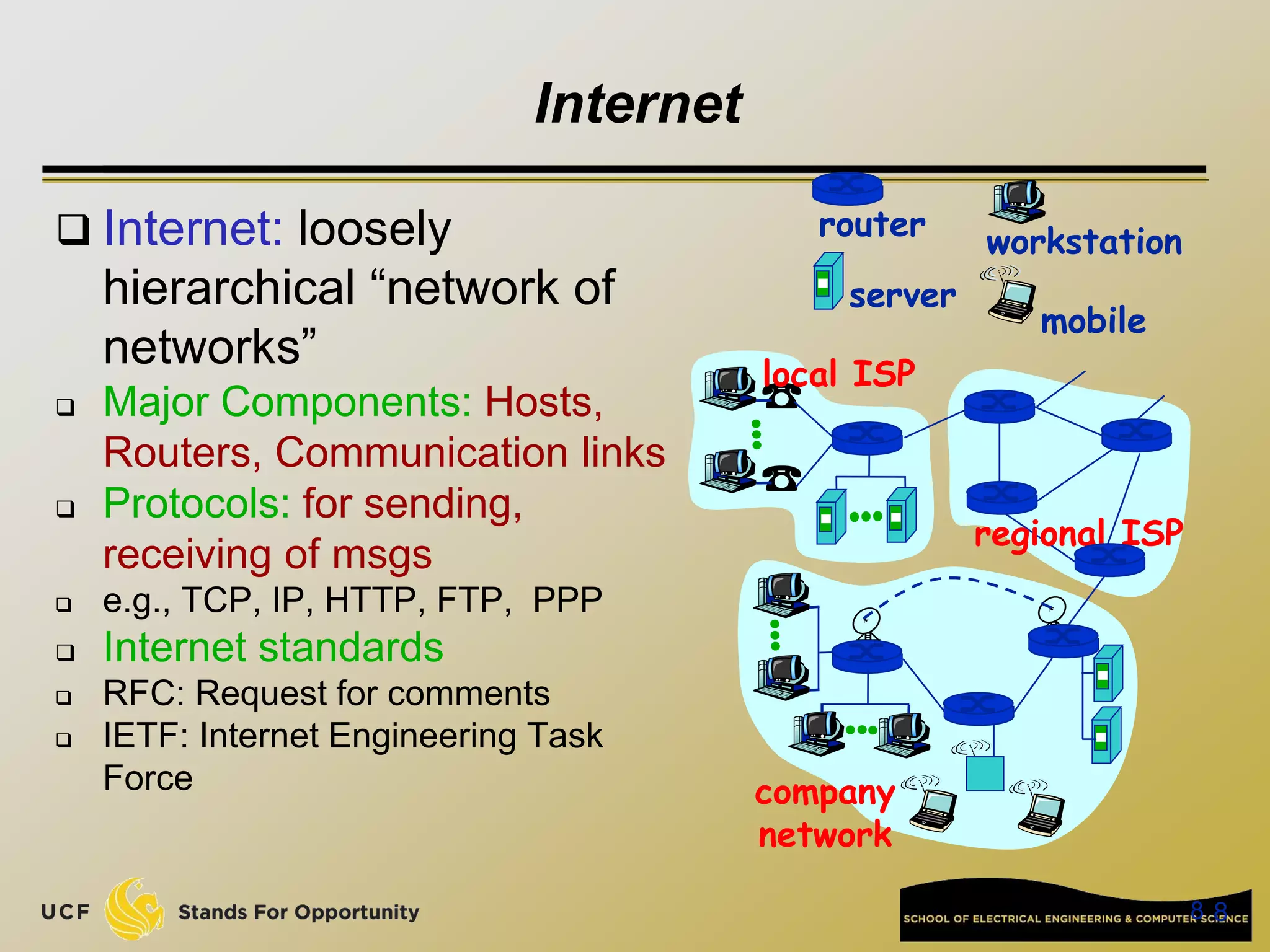
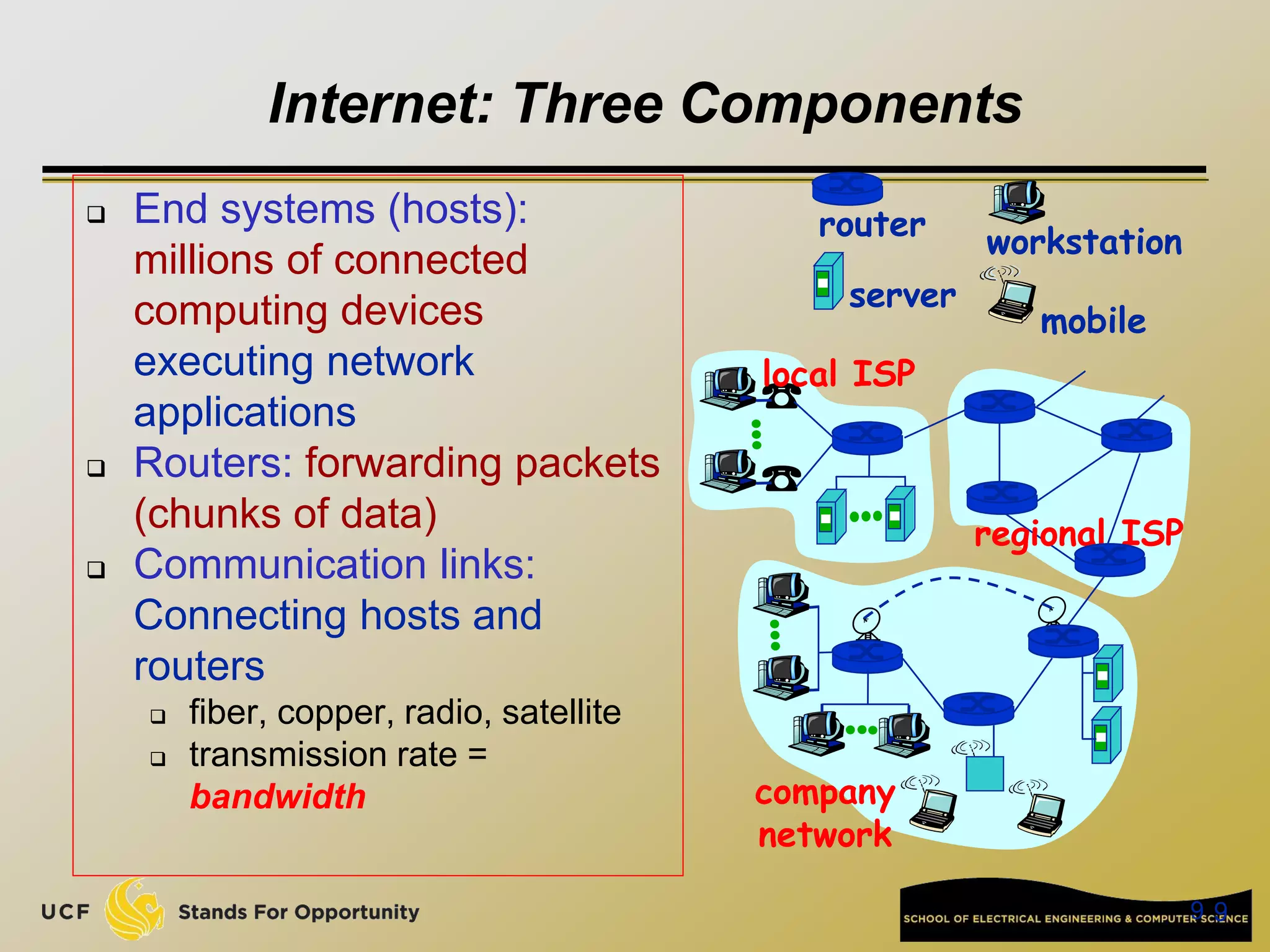
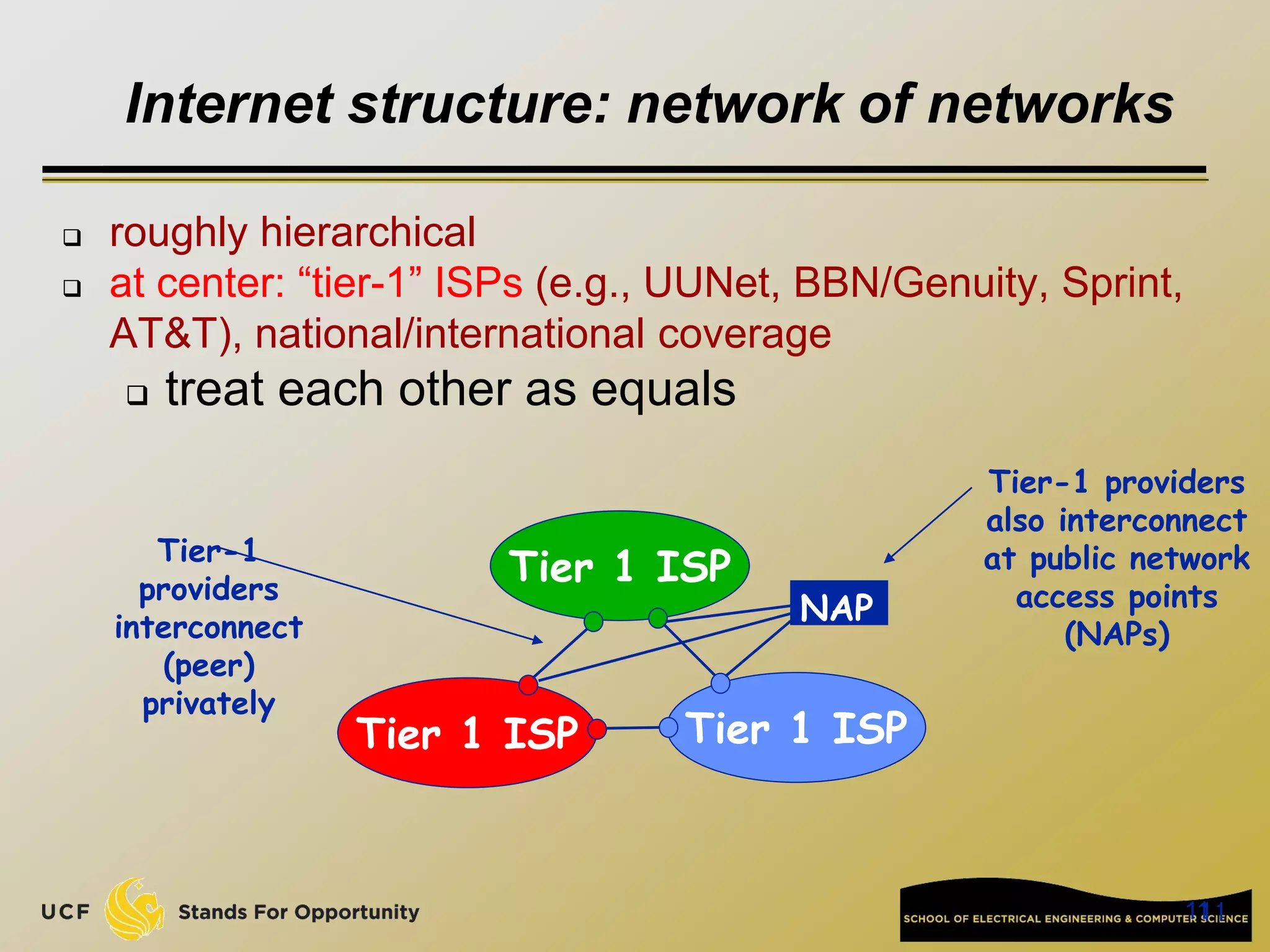
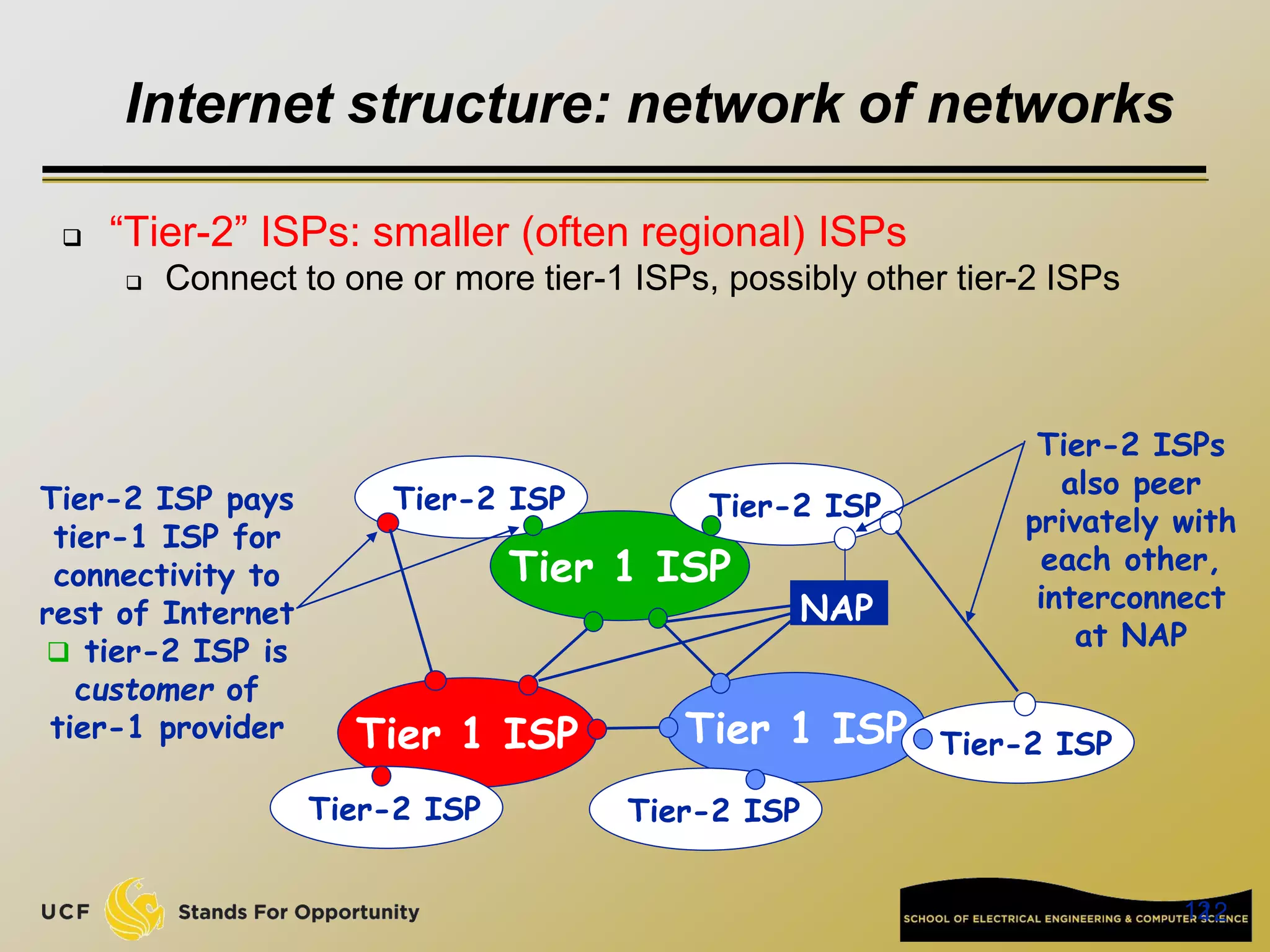
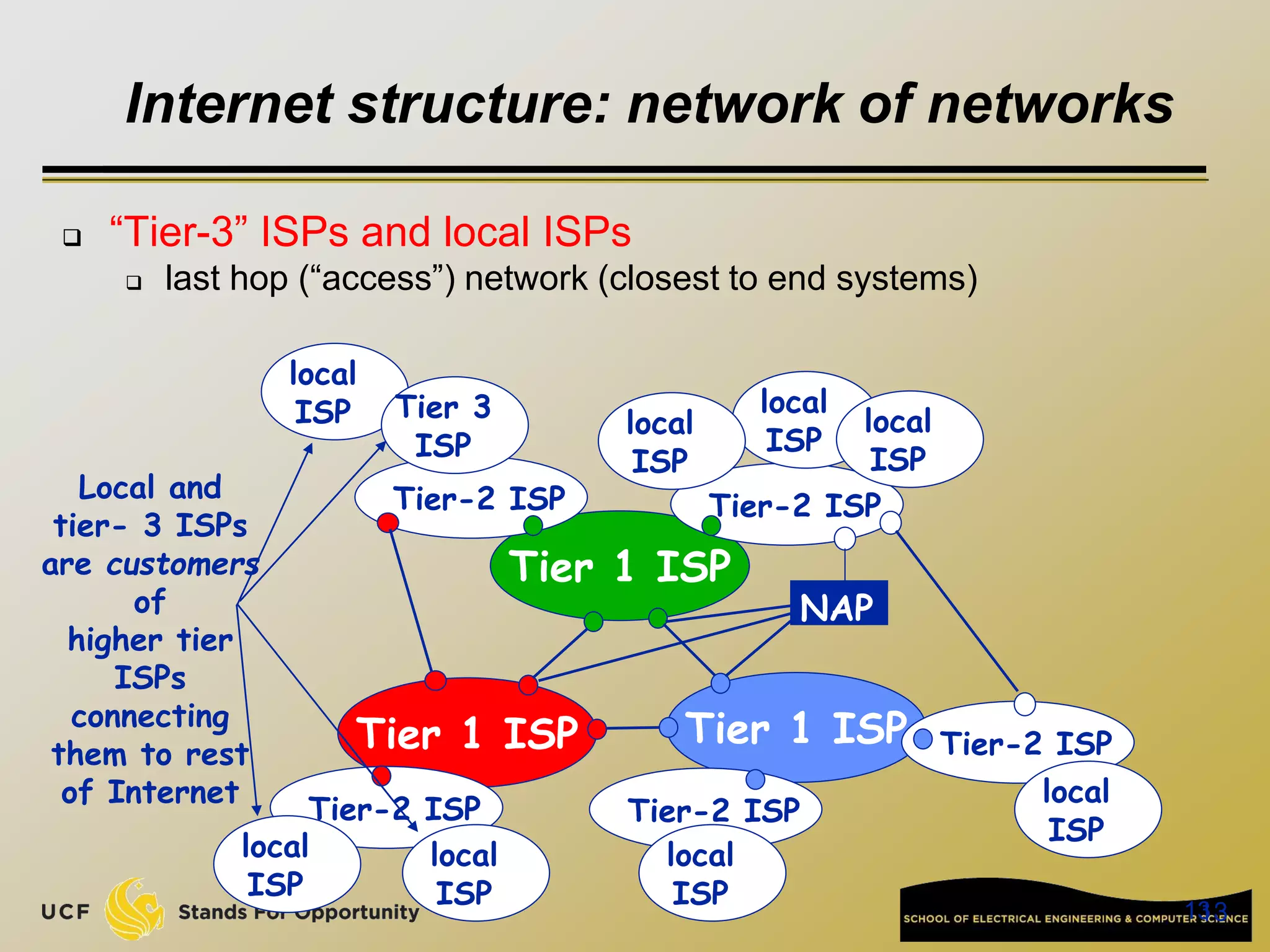
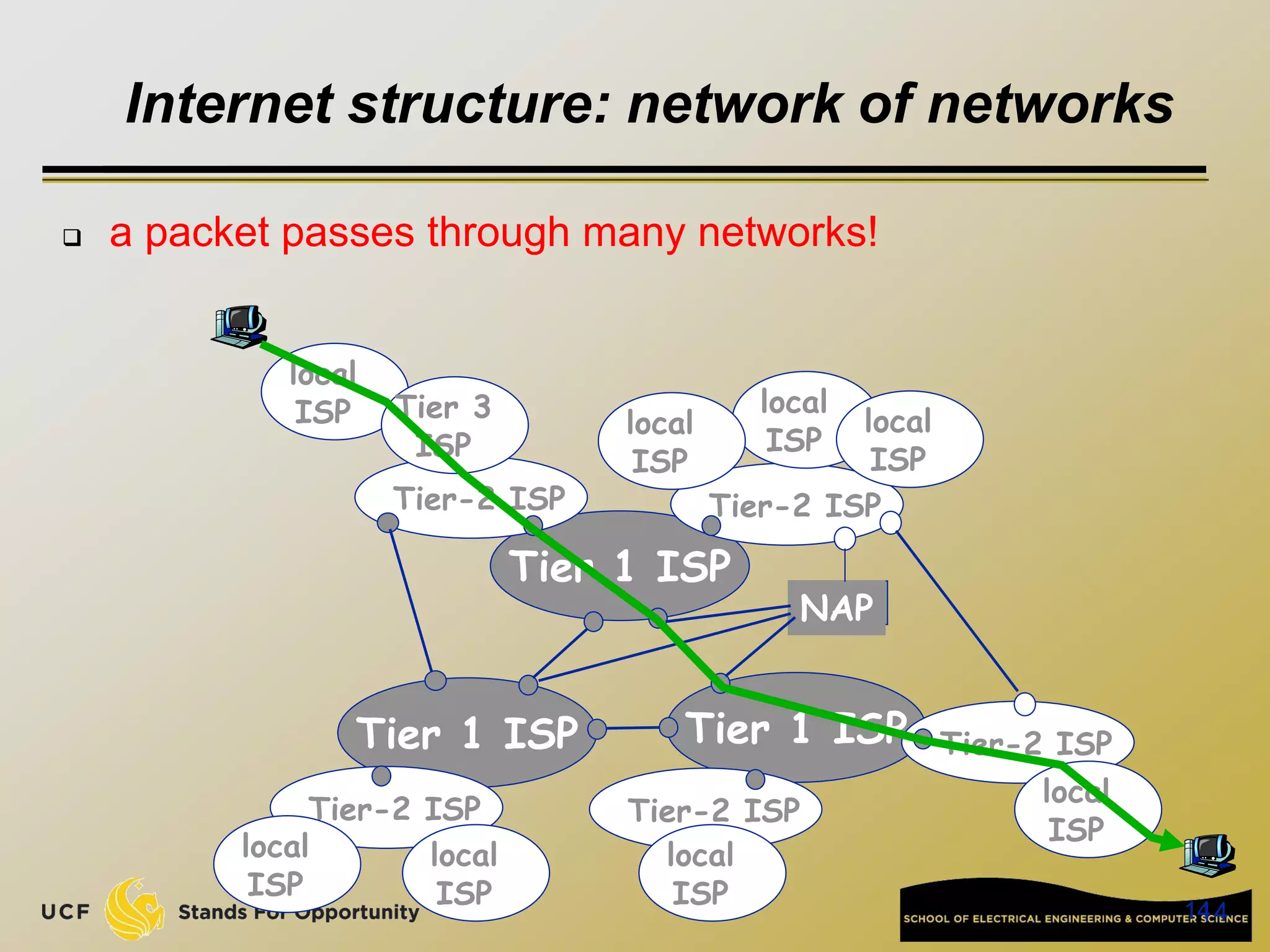
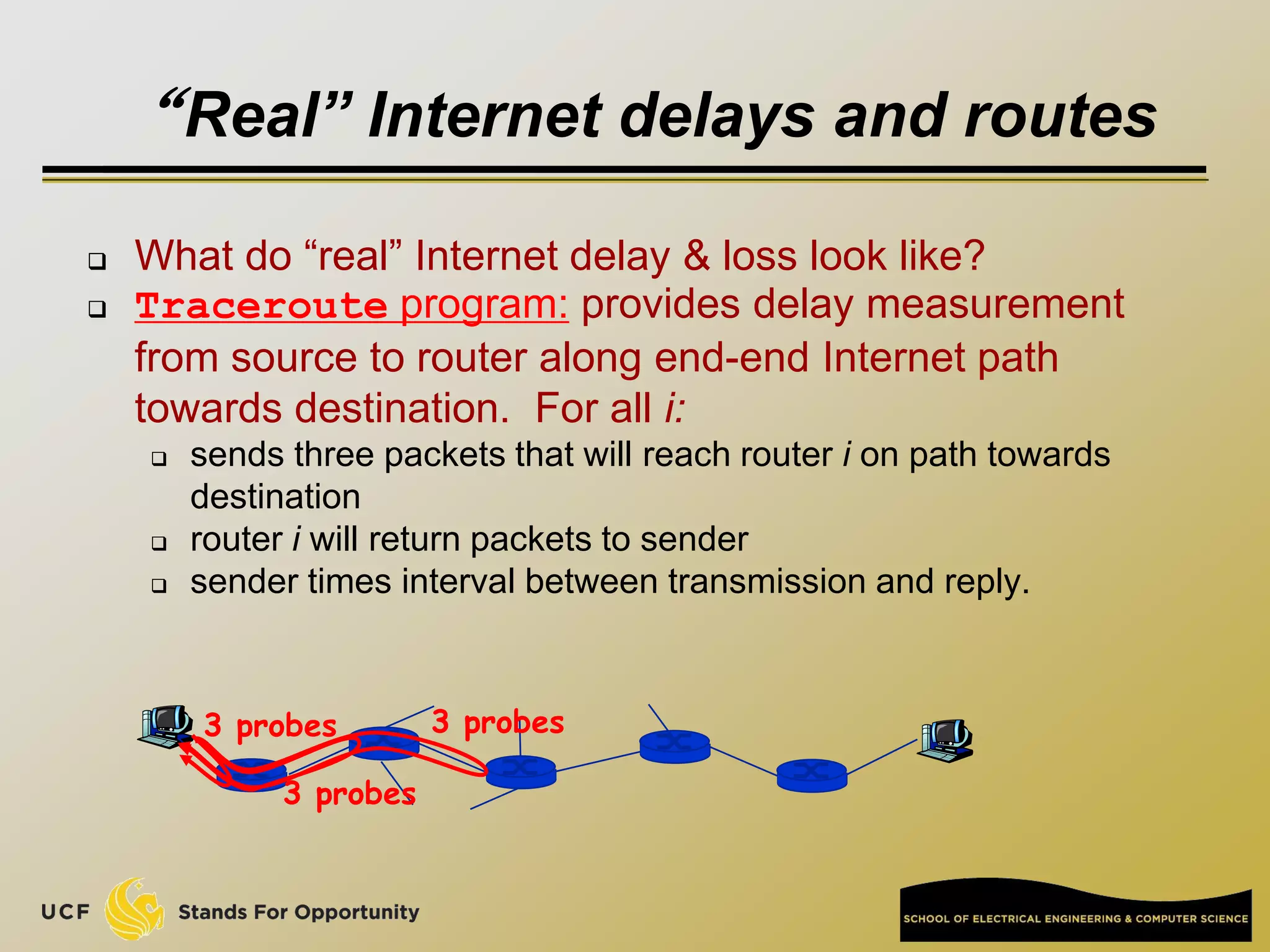
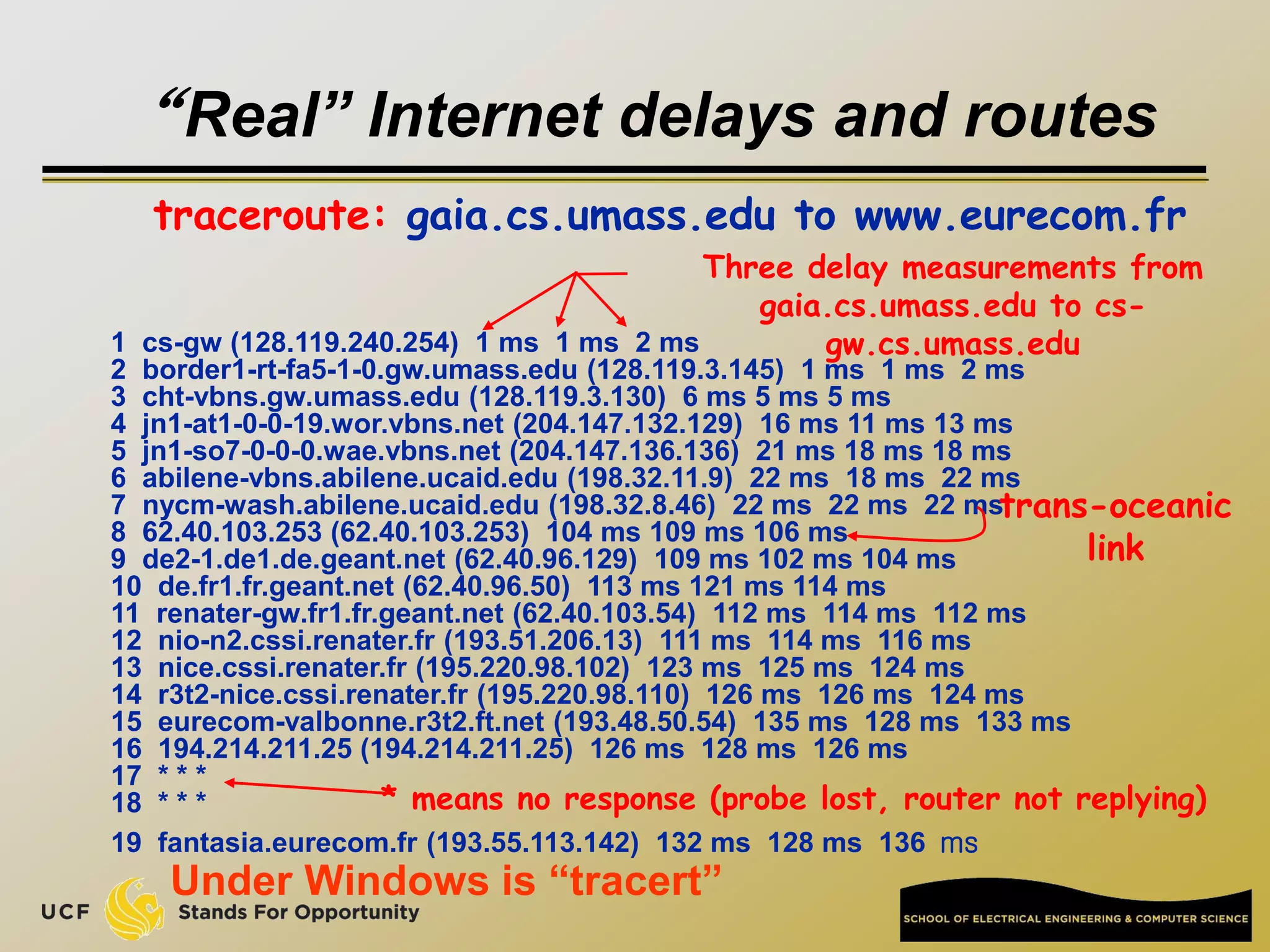
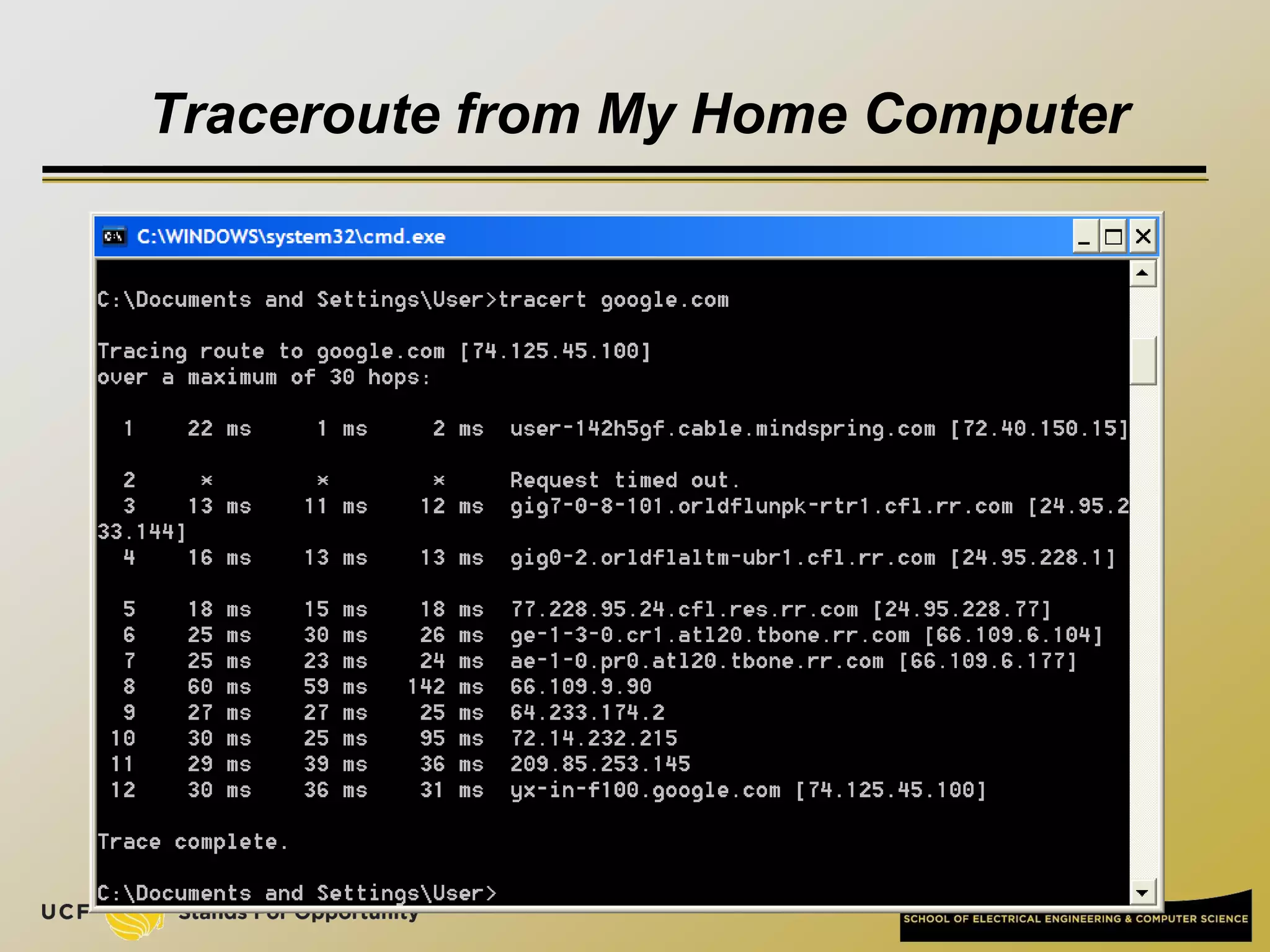
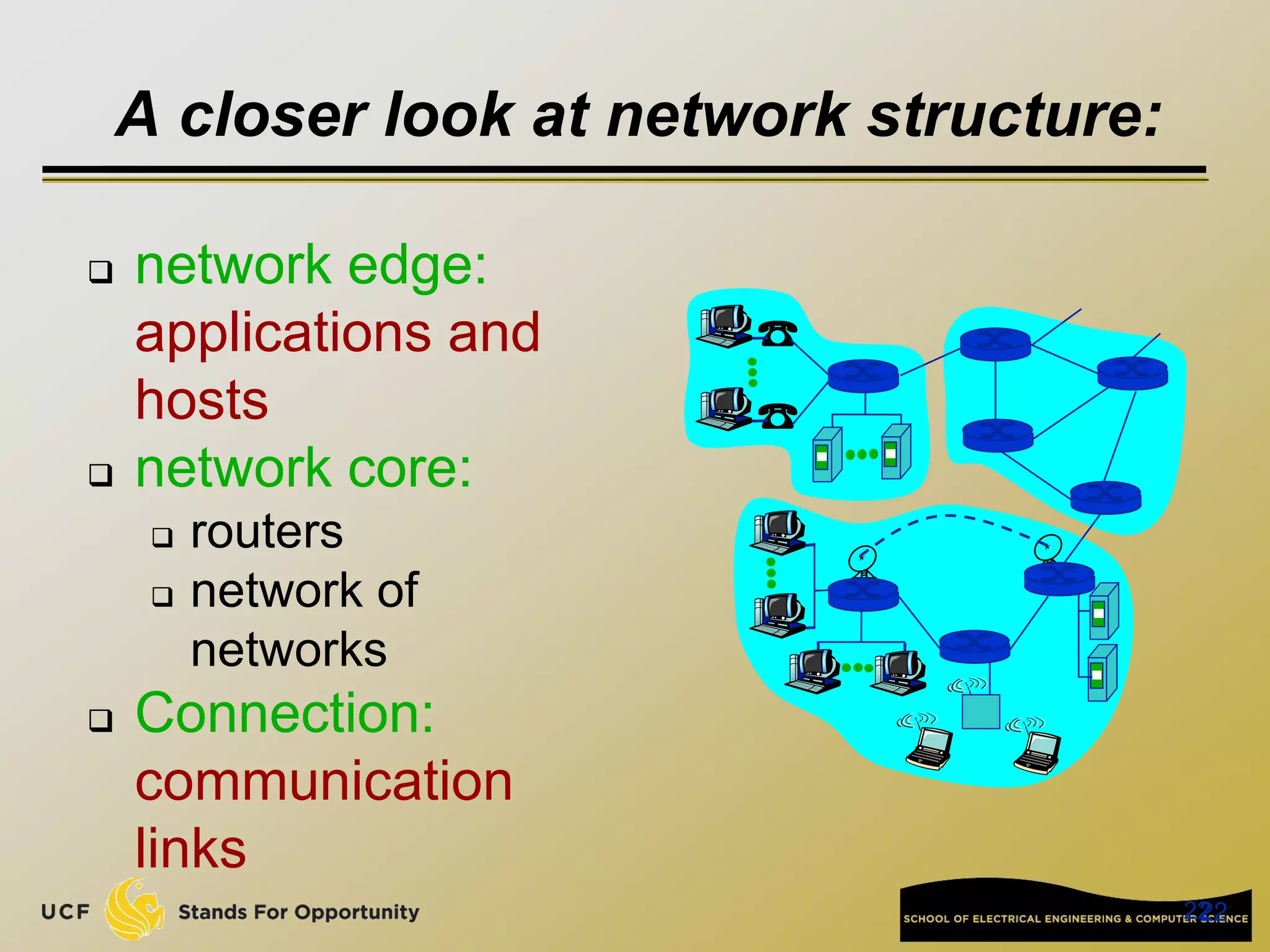
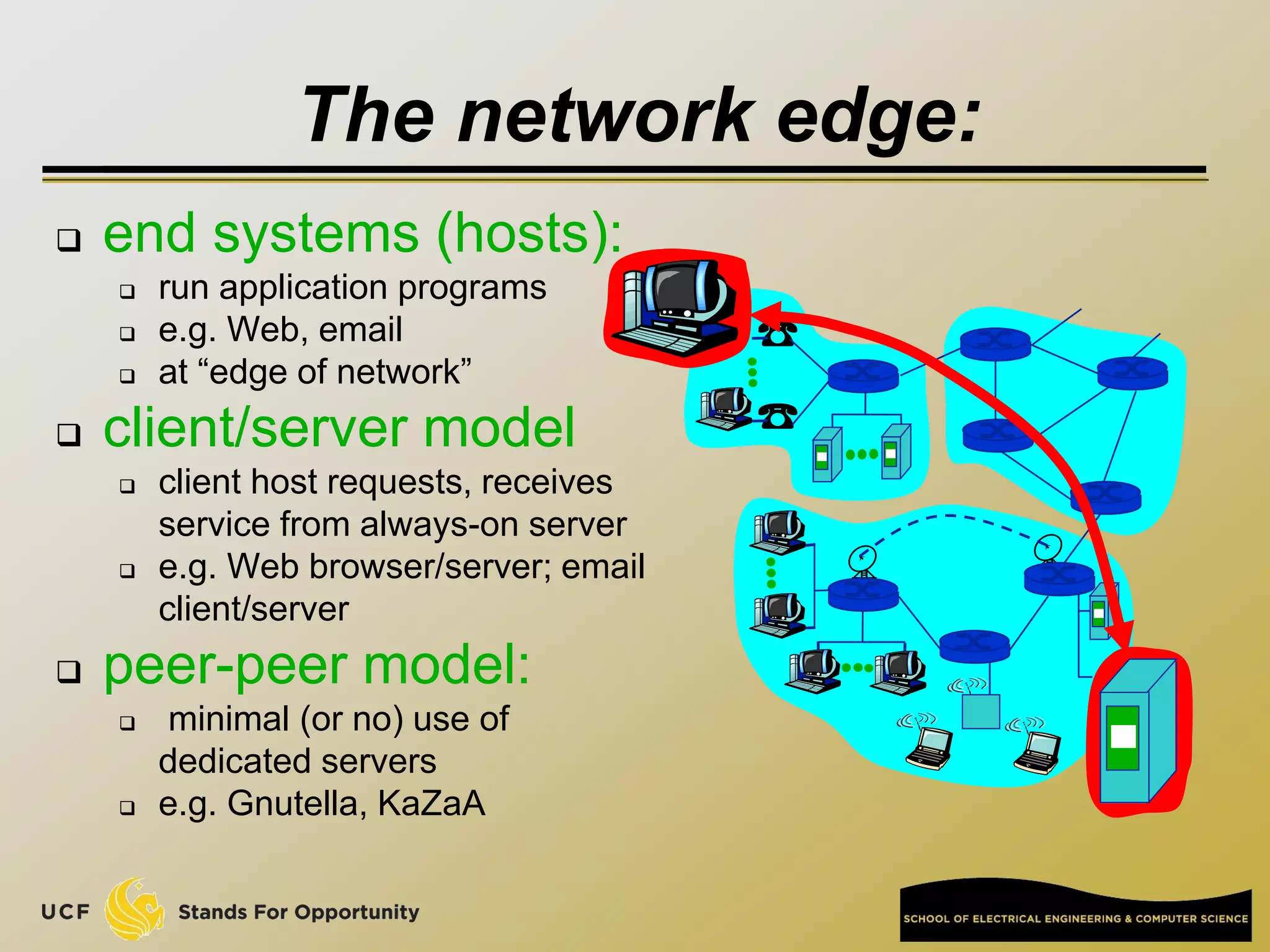
This document provides an overview of the CIS 3360: Security in Computing course being taught by Cliff Zou in Spring 2012. The objectives of the course are to obtain basic knowledge of computer networking, the Internet, network applications and protocols like TCP/IP. It introduces some key concepts like the layered Internet protocol stack, packet switching, and the hierarchical structure of the Internet as a network of networks consisting of end systems, routers, and communication links. Example applications and protocols for each layer are also discussed at a high level.






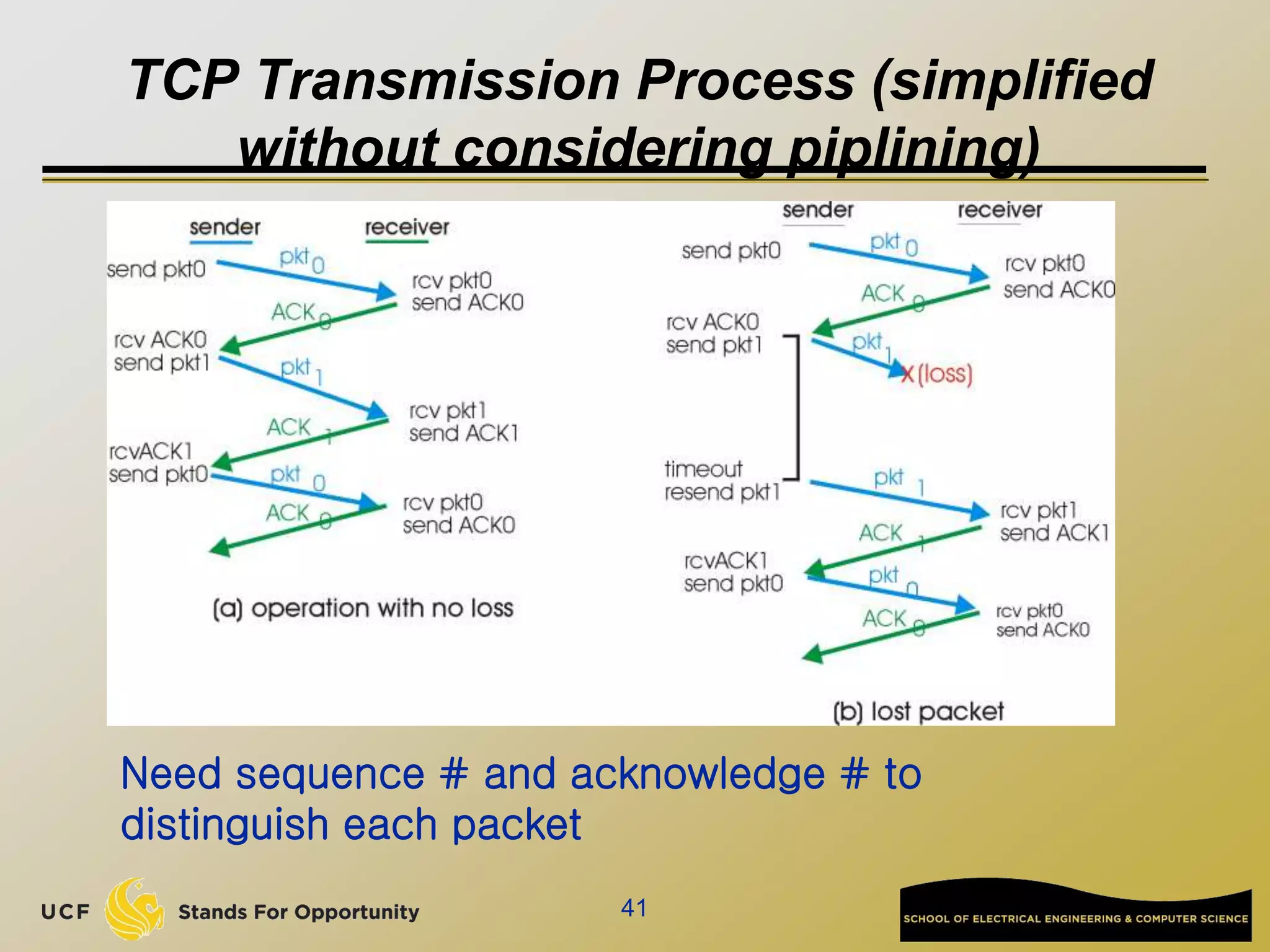
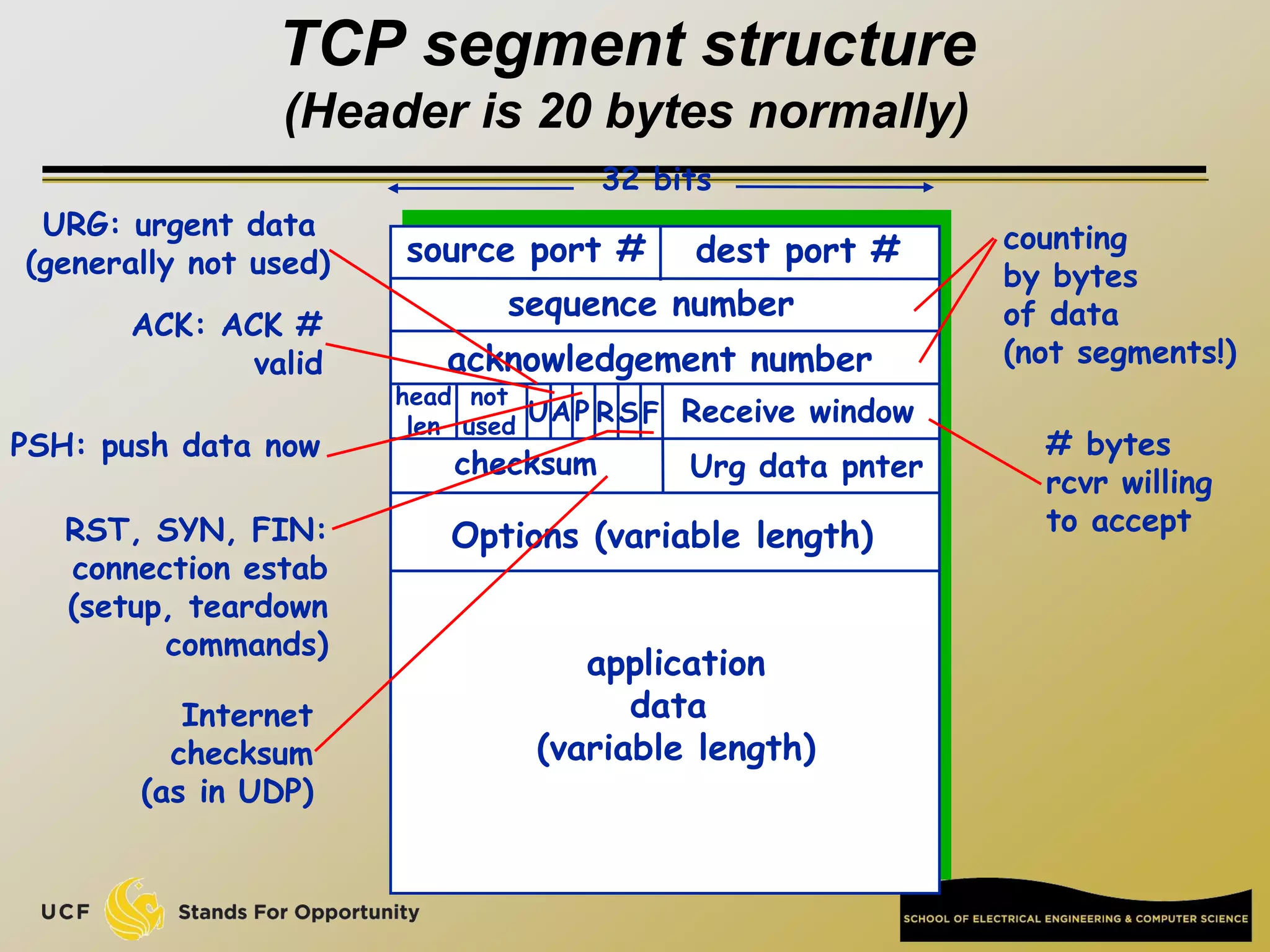
![Network edge: connection-oriented
service
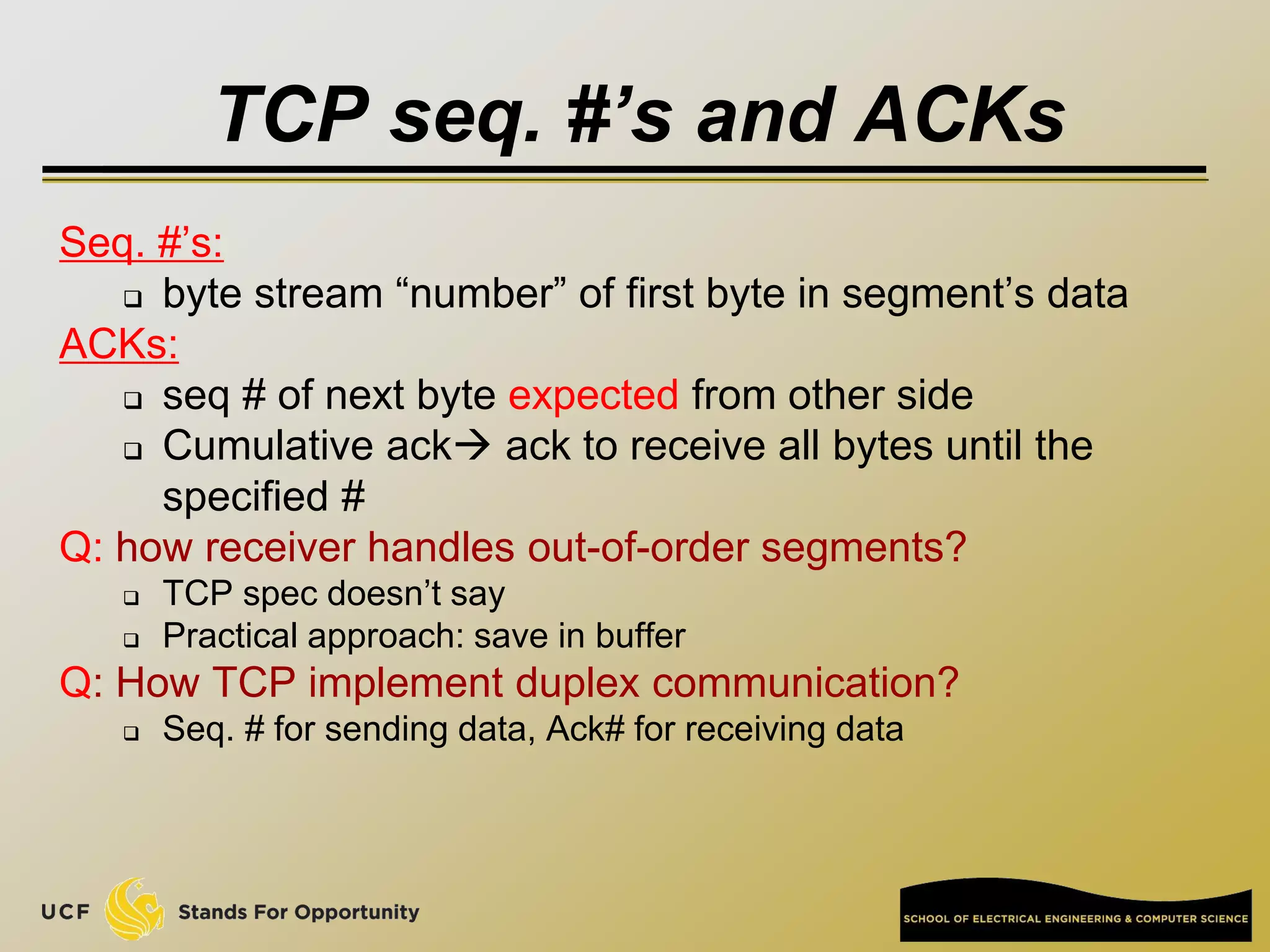
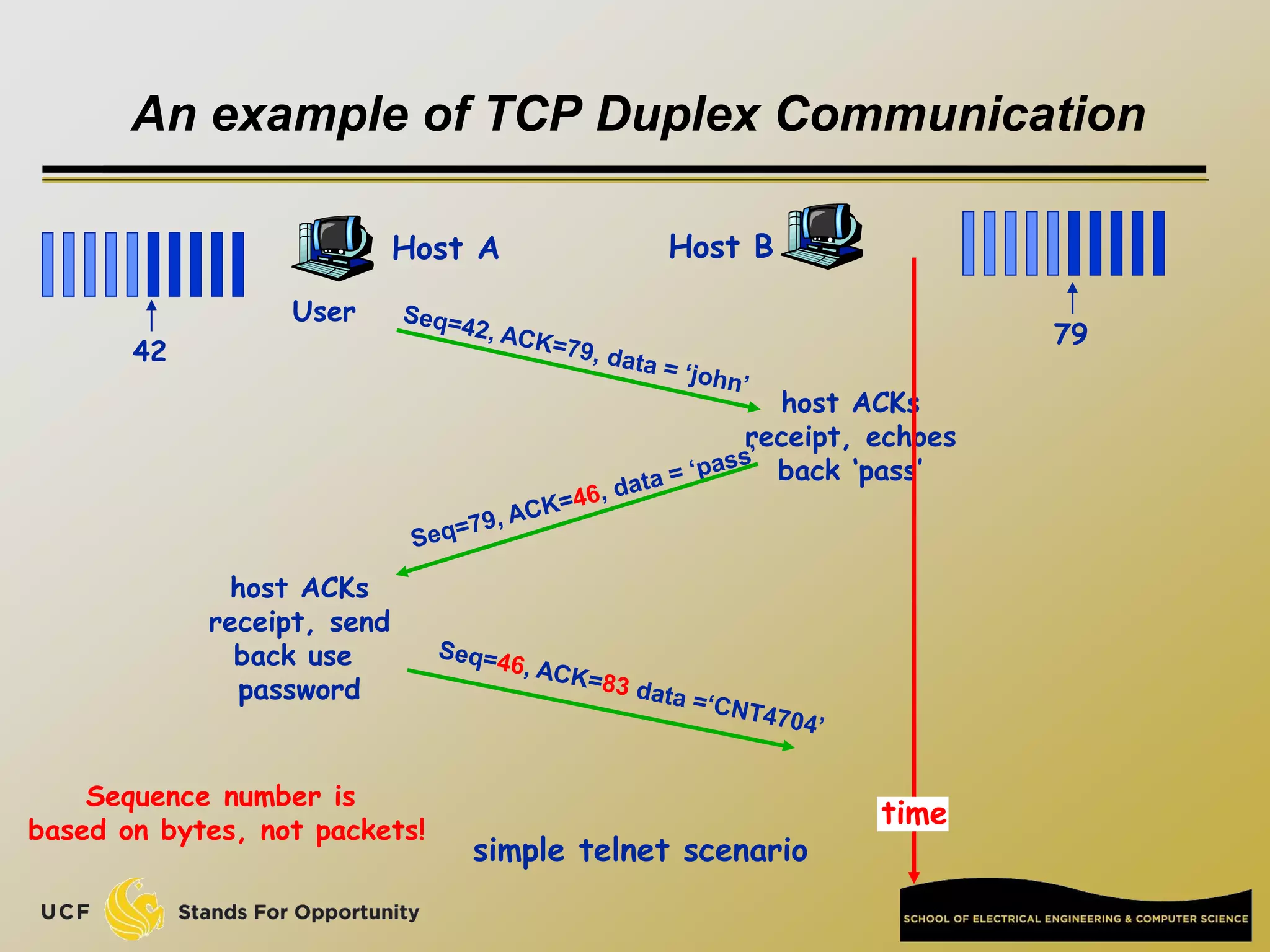
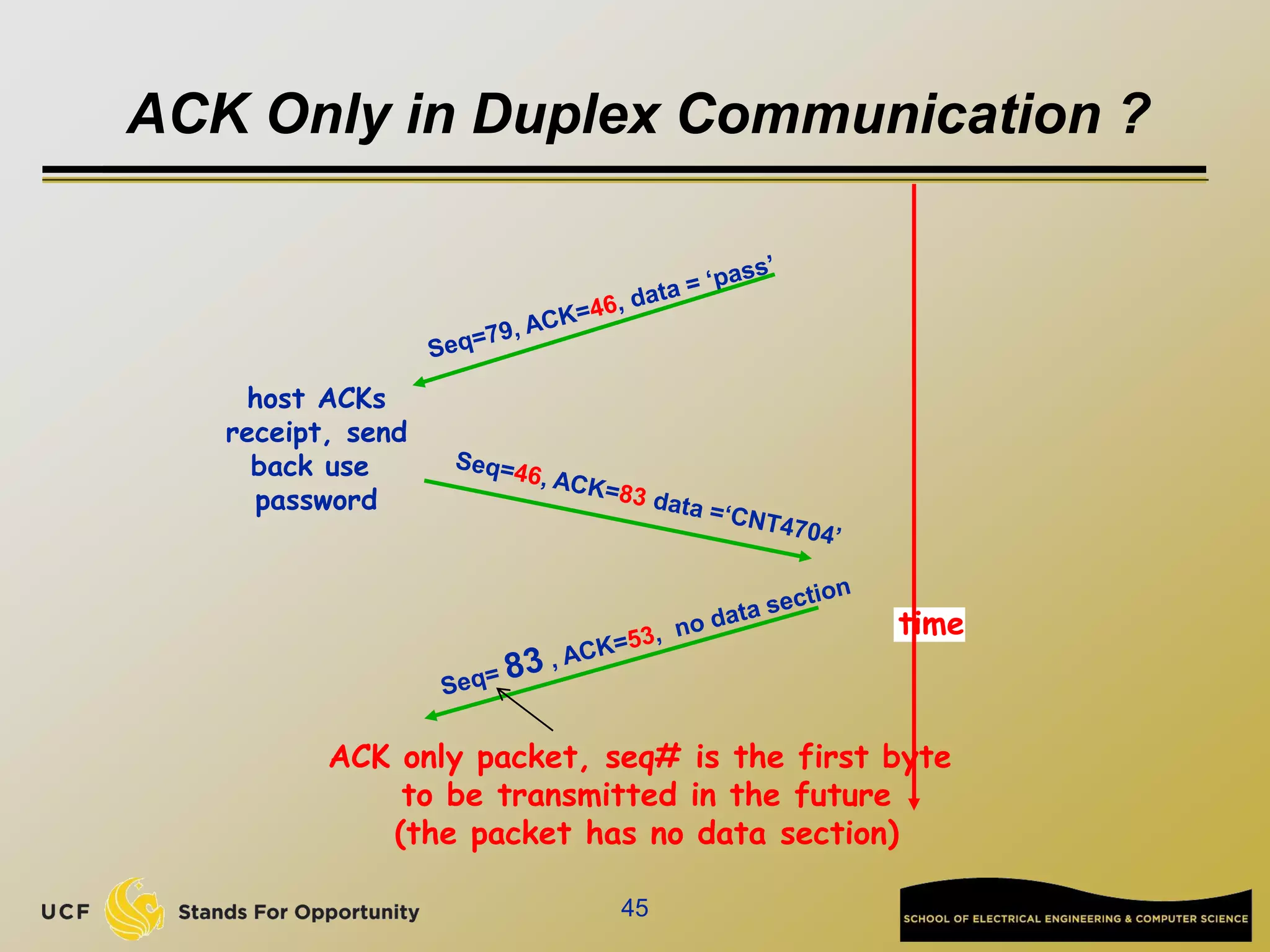
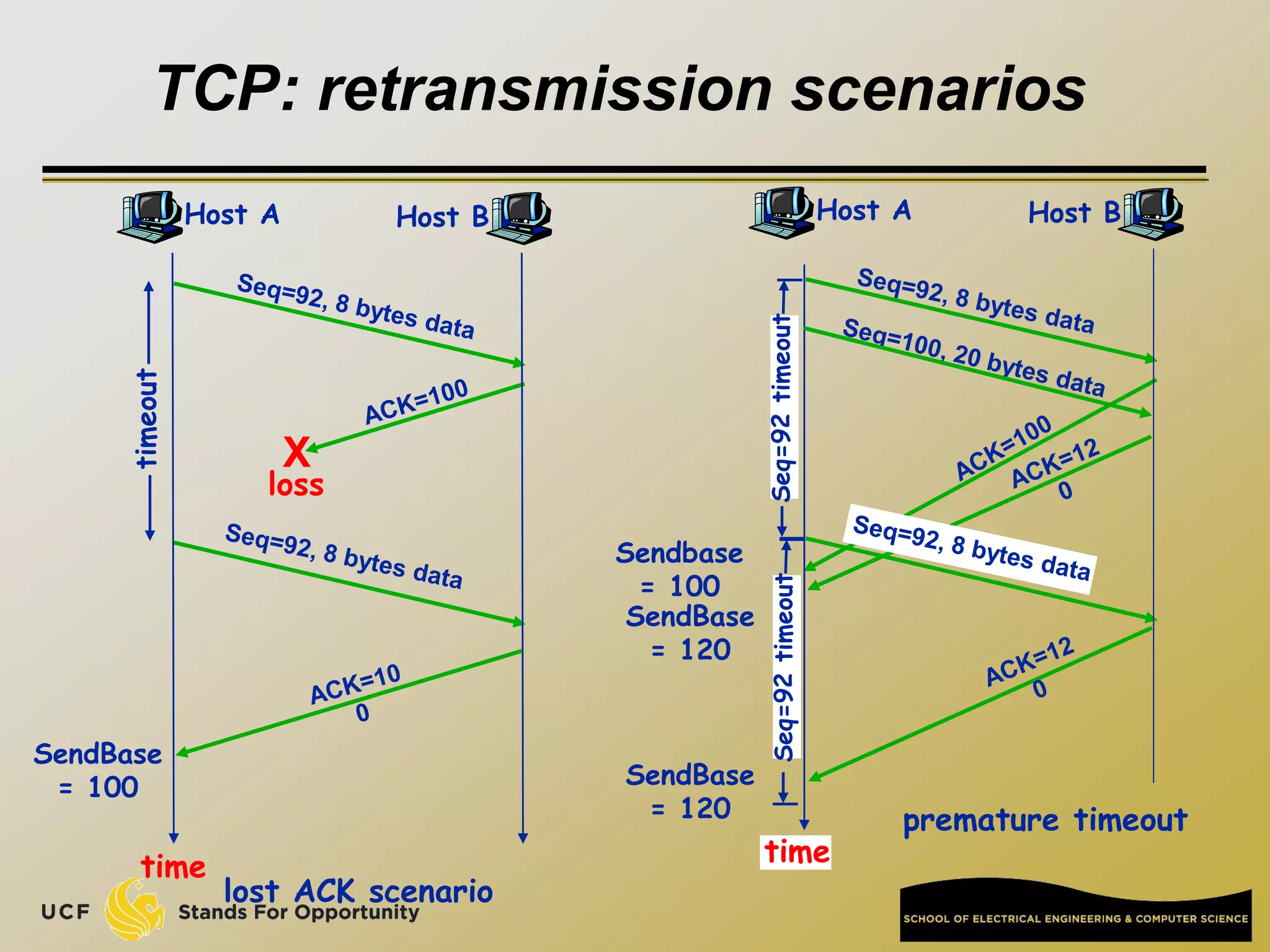
TCP [ Transmission Control Protocol ]
reliable, in-order : byte-stream data transfer
loss: acknowledgements and retransmissions
flow control:
sender won’t overwhelm receiver
congestion control:
senders “slow down sending rate” when network congested
Examples of applications using TCP:
HTTP (Web), FTP (file transfer), SSH
(remote secure login), SMTP (email)](https://image.slidesharecdn.com/preknowledge-internetnetworking-230531091354-2eaddd65/75/preKnowledge-InternetNetworking-ppt-24-2048.jpg)
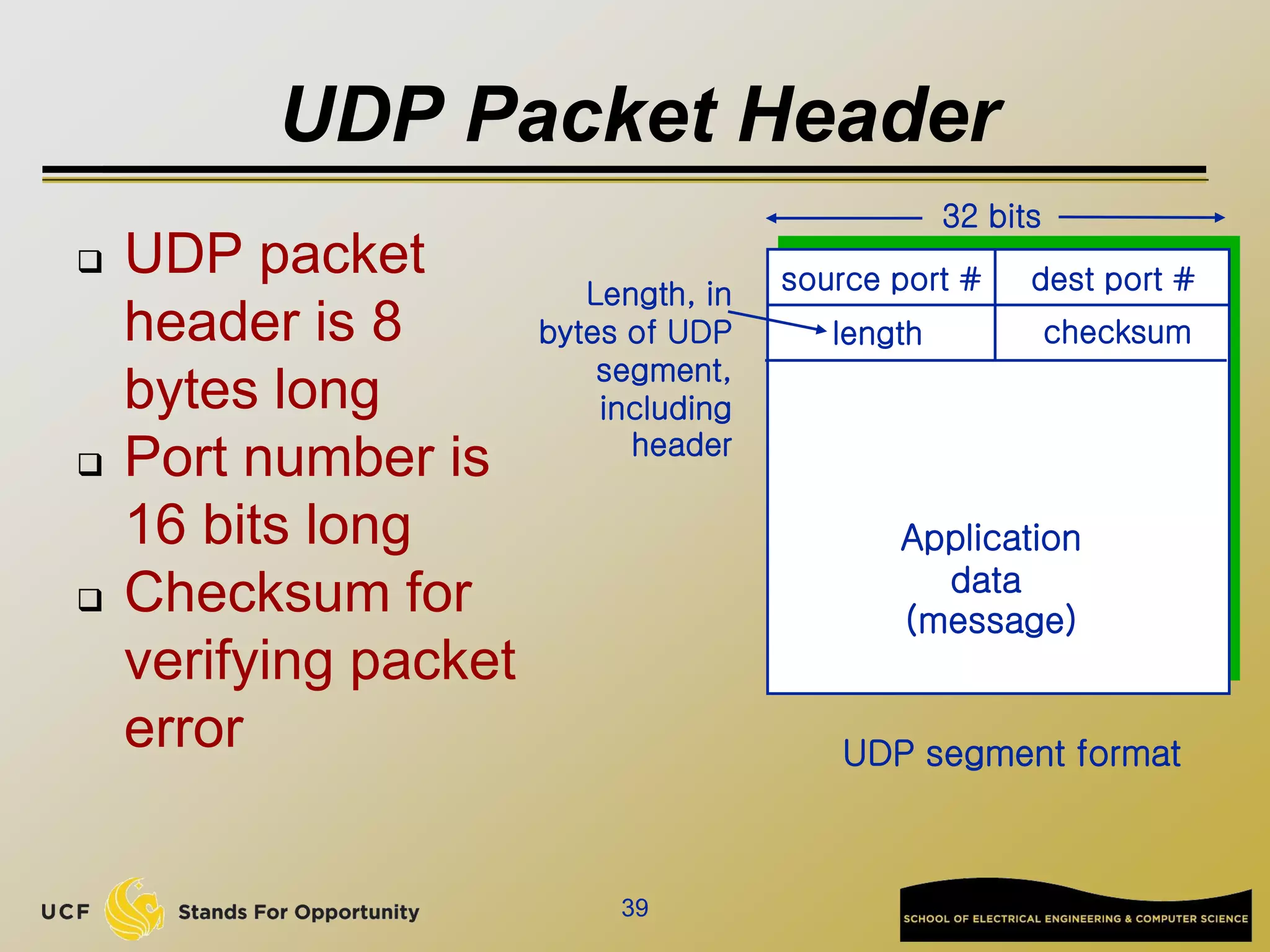
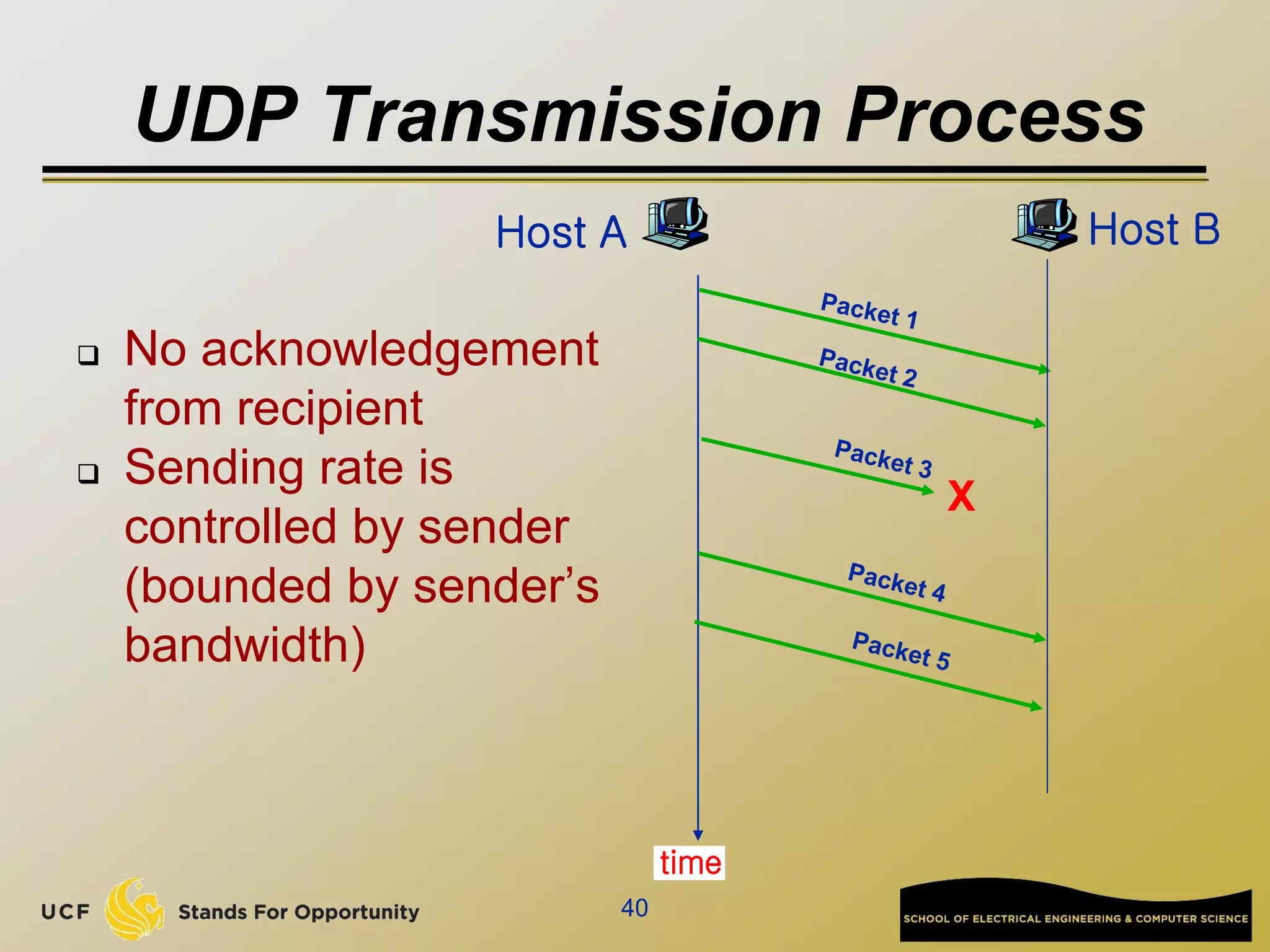
![Network edge: connectionless service
UDP [User Datagram Protocol]
connectionless
unreliable data transfer
no flow control
no congestion control
Examples of applications using UDP:
streaming media, teleconferencing, DNS, Internet
telephony](https://image.slidesharecdn.com/preknowledge-internetnetworking-230531091354-2eaddd65/75/preKnowledge-InternetNetworking-ppt-25-2048.jpg)