This document covers the enumeration phase of ethical hacking, focusing on techniques and countermeasures for exploiting systems, specifically Windows 2000. It details methods of gathering information such as network resources, users, and groups through attacks like null sessions and SMB enumeration. The importance of understanding these concepts is emphasized for security professionals to implement effective countermeasures against potential intrusions.














![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Enumeration
Module IV Page 16 of 40 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
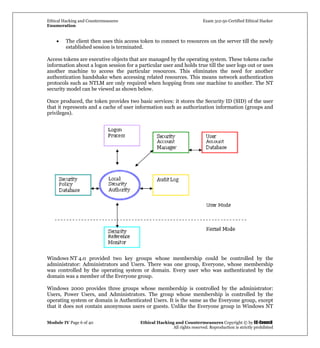
On finding port 139 open, the attacker can first use the nbtstat command
Usage: nbtstat [-a RemoteName] [-A IP_address] [-c] [-n] [-R] [-r] [-S] [-s] [interval]
Note that an attacker will take particular interest in the id <03>. We try to connect to this remote
machine using a null session. Usage: net use IPIPC$ “” /user: “” This command connects to the
machine using a null user and null password as signified by the empty quotes. The IPC$ is the
hidden share on the particular IP that we will try to access in order to list any shared resources.
Two main drawbacks of nbtstat are that it is restricted to operating on a single user and its rather
inscrutable output. The tool NBTScan addresses these issues.
A tool that can be used for such exploits is NBTScan written by Alla Bezroutchko and
available at http://www.inetcat.org/software/nbtscan.html. NBTscan is a program for scanning
IP networks for NetBIOS name information. It sends NetBIOS status query to each address in
supplied range and lists received information in human readable form. For each responded host it
lists IP address, NetBIOS computer name, logged-in user name and MAC address. NBTscan uses
port 137 UDP for sending queries. If the port is closed on destination host destination will reply
with ICMP "Port unreachable" message. See screenshot below.](https://image.slidesharecdn.com/module4enumeration-190219093937/85/Module-4-enumeration-16-320.jpg)
![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Enumeration
Module IV Page 17 of 40 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
EC-Council
Hacking Tool: DumpSec
DumpSec reveals shares over a null session with the target
computer.
DumpSec, presently available as freeware from SomarSoft and downloadable at
http://www.systemtools.com/somarsoft/, is a security auditing program for Windows systems. It
dumps the permissions (DACLs) and audit settings (SACLs) for the file system, registry, printers
and shares in a concise, readable listbox (text) format, so that holes in system security are readily
apparent. DumpSec also dumps user, group and replication information.
DumpSec takes advantage of the NetBIOS API and works by establishing NULL session to the
target box as the Null user via the [net use server "" /user:""] command. It then makes NET*
enumeration application program interface (API) calls like NetServerGetInfo (supported by the
Netapi32 library).
It allows users to remotely connect to any computer and dump permissions, audit settings, and
ownership for the Windows NT/2000 file system into a format that is easily converted to
Microsoft Excel for editing. Hackers can choose to dump either NTFS or share permissions. It can
also dump permissions for printers and the registry.
The highlight is DumpSec’s ability to dump the users and groups in a Windows NT or Active
Directory domain. There are several reporting options and the hacker can choose to dump the
direct and nested group memberships for every user, as well as the logon scripts, account status
such as disabled or locked out, and the ‘true’ last logon time across all domain controllers. The
user can also get password information such as ‘Password Last Set Time’ and ‘Password Expires
Time’. To summarize, Dumpsec can pull a list of users, groups, and the NT system’s policies and
user rights.](https://image.slidesharecdn.com/module4enumeration-190219093937/85/Module-4-enumeration-17-320.jpg)
![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Enumeration
Module IV Page 18 of 40 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
EC-Council
Hacking Tool: NAT
The NetBIOS Auditing Tool (NAT) is designed to explore
the NetBIOS file-sharing services offered by the target
system.
It implements a stepwise approach to gather information
and attempt to obtain file system-level access as though it
were a legitimate local client.
If a NETBIOS session can be established at all via TCP
port 139, the target is declared "vulnerable“.
Once the session is fully set up, transactions are
performed to collect more information about the server
including any file system "shares" it offers.
The NetBIOS Auditing Tool (NAT), written by Andrew Tridgell is designed to explore the
NETBIOS file-sharing services offered by the target system. It implements a stepwise approach to
gather information and attempt to obtain file system-level access as though it were a legitimate
local client.
The auditing tool starts a UDP query to the target, which usually elicits a reply containing the
NetBIOS "computer name". This is needed to establish a session. The reply also can contain other
information such as the workgroup and account names of the machine's users.
Next, TCP connections are made to the target's NetBIOS port [139], and session requests using
the derived computer name are sent across. Various guesses at the computer name are also used,
in case the status query failed or returned incomplete information. If all such attempts to
establish a session fail, the host is assumed invulnerable to NETBIOS attacks even if TCP port 139
was reachable.
If a connection is established NetBIOS "protocol levels" are negotiated across the new connection.
This establishes various modes and capabilities the client and server can use with each other, such
as password encryption and if the server uses user-level or share-level security. If the server
requires further session setup to establish credentials, various defaults are attempted. Completely
blank usernames and passwords are often allowed to set up "guest" connections to a server; if this
fails then guesses are tried using fairly standard account names such as ADMINISTRATOR, and
some of the names returned from the status query. Extensive username/password checking is not
done at this point, since the aim is just to get the session established, but it should be noted that if
this phase is reached at all many more guesses can be attempted and likely without the owner of
the target being immediately aware of it.](https://image.slidesharecdn.com/module4enumeration-190219093937/85/Module-4-enumeration-18-320.jpg)
![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Enumeration
Module IV Page 19 of 40 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
Once the session is fully set up, transactions are performed to collect more information about
the server including any file system "shares" it offers.
Attempts are then made to connect to all listed file system shares and some potentially unlisted
ones. If the server requires passwords for the shares, defaults are attempted as described above
for session setup. Any successful connections are then explored for writeability and some known
file-naming problems.
If a NETBIOS session can be established at all via TCP port 139, the target is declared
"vulnerable" with the remaining question being to what extent.
Information is collected under the appropriate vulnerability at most of these steps, since any point
along the way be blocked by the security configurations of the target. Most Microsoft-OS based
servers and Unix SAMBA will yield computer names and share lists, but not allow actual file-
sharing connections without a valid username and/or password. A remote connection to a share is
therefore a possibly serious security problem, and a connection that allows writing to the share
almost certainly so. Let’s take a look at an output from NAT.exe
C:nat>nat 192.168.2.176
[*]--- Checking host: 192.168.2.176
[*]--- Obtaining list of remote NetBIOS names
[*]--- Remote systems name tables:
JOHN
WORKGROUP
JOHN
JOHN
WORKGROUP
………………………
[*]--- Attempting to connect with name: JOHN
[*]--- CONNECTED with name: JOHN
..……………………..
[*]--- Attempting to establish session
[*]--- Obtained server information:
Server= [JOHN] User= [] Workgroup= [WORKGROUP] Domain= [WORKGROUP]](https://image.slidesharecdn.com/module4enumeration-190219093937/85/Module-4-enumeration-19-320.jpg)
![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Enumeration
Module IV Page 20 of 40 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
[*]--- Obtained listing of shares:
Sharename Type Comment
--------- ---- -------
D Disk:
IPC$ IPC: Remote Inter Process Communication
[*]--- Attempting to access share: JOHND
[*]--- WARNING: Able to access share: JOHND
[*]--- Checking write access in: JOHND
[*]--- WARNING: Directory is writeable: JOHND
[*]--- Attempting to exercise... bug on: JOHND](https://image.slidesharecdn.com/module4enumeration-190219093937/85/Module-4-enumeration-20-320.jpg)



![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Enumeration
Module IV Page 24 of 40 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
• Share Table - If the cracker knows what shares are exported and used by a Windows
machine, it can lead to a serious security compromise.
Here, we will look at an SNMP utility called SNMPutil.exe which is a part of the Windows 2000
resource kit. Let us take a look at what we can discover with it from the command line prompt.
usage: snmputil [get | getnext | walk] target host community OID
In this output, the variable is called 1.3.6.1.2.1.1.2.0, and we ‘get’ its value, which turns out to be
1.The variable name (1.3.6.1.2.1.1.2.0) is called an object identifier or OID. An alternative to this is
found in the second line of the output shown here. The ‘interfaces.ifNumber.0’ is the same OID,
but is more easily readable. The second and third arguments to SNMPUTIL designate the host to
which the SNMP request will be sent (210.212.69.129), and community (authentication string or
password) to use (public). The ‘public’ community is the default when SNMP support is installed
on a Windows 2000 host, and it allows the user to read all variables present. Since even the
number of interfaces in a host is sensitive data, the threat is evident. Let us look at some of the
other variables that might be of interest to an attacker and a security professional.
IpForwarding (1.3.6.1.2.1.4.1.0) - Is the host forwarding? This is not a good sign for a workstation.
IcmpInRedirects (1.3.6.1.2.1.5.7) - Is the host redirecting icmp messages?
TcpOutRsts (1.3.6.1.2.1.6.15) - A counter indicating the number of RSTs send by the box. This
counter will increase rapidly when port-scanned.
UdpNoPorts (1.3.6.1.2.1.7.2) - A counter indicating traffic to ports where no service was present.
Also a possible port-scan signal.
SNMP walk automates the whole process of getting the variables and can be redirected to an
output file. To summarize, Snmputil can reveal details about services that are running, share
names, share paths, any comments on shares, usernames and domain names etc.](https://image.slidesharecdn.com/module4enumeration-190219093937/85/Module-4-enumeration-24-320.jpg)















