The document provides a detailed examination of various computer viruses for the Certified Ethical Hacker exam 312-50, including notable examples such as the Chernobyl, ExploreZip, and I Love You viruses. It covers the mechanics of these viruses, their payloads, and the methods they use to spread and infect systems. The module aims to familiarize readers with the impact of these viruses and the importance of antivirus software in combating them.






![Ethical Hacking and Countermeasures Exam 312-50 Certified Ethical Hacker
Viruses
Module XVI Page 7 of 42 Ethical Hacking and Countermeasures Copyright © by EC-Council
All rights reserved. Reproduction is strictly prohibited
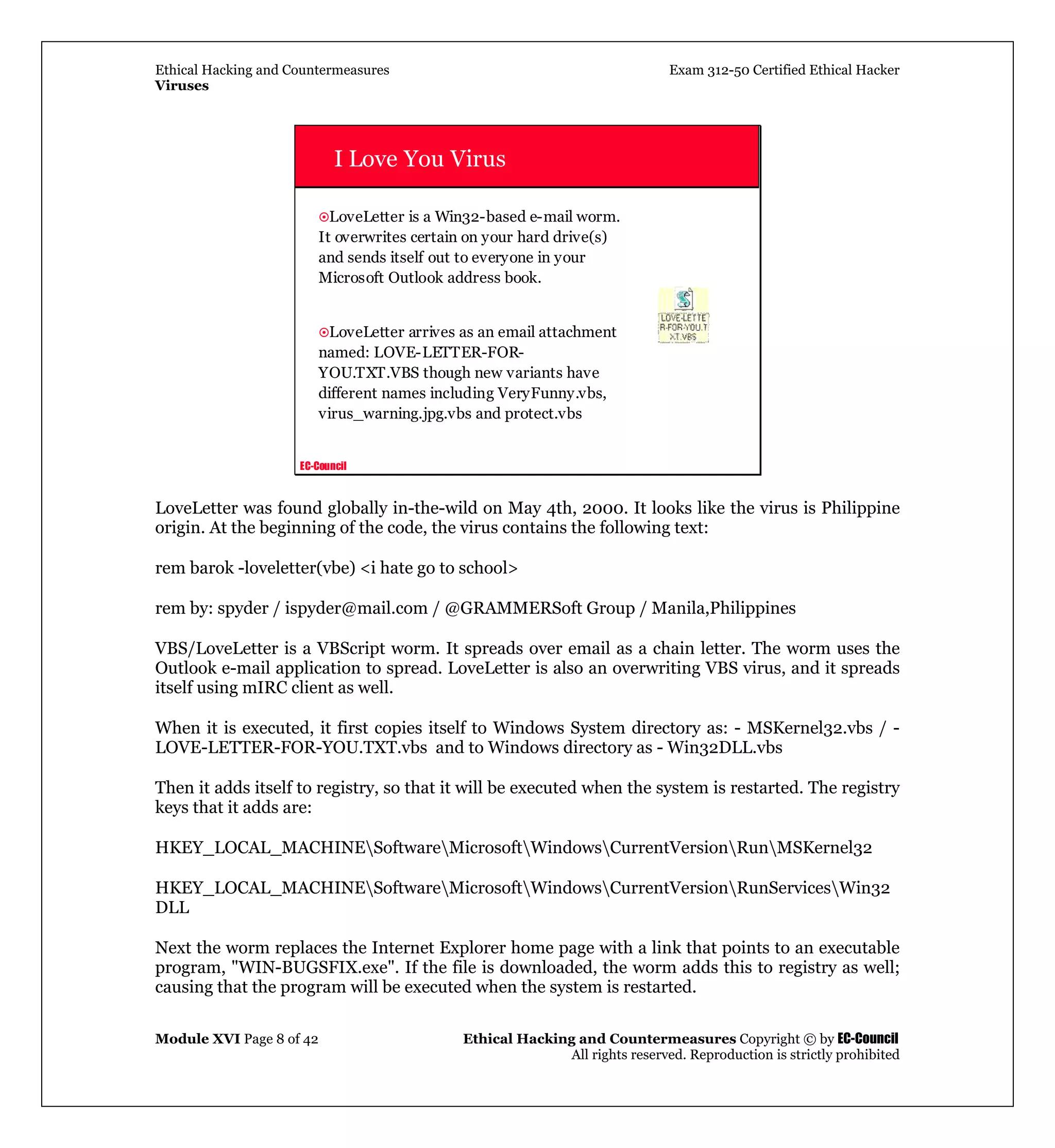
after infection this process is repeated. Files that have been affected by this payload will need to
be restored from backup. Repair is not possible.
This worm will locate system drives which are NOT mapped drives using functions from
MPR.DLL and Network Neighborhood. On these systems, the WIN.INI is modified with a run
statement to load a file called _SETUP.EXE from the Windows path, and the file _SETUP.EXE is
copied to the Windows path. These systems will become infected when restarted. This worm will
only try to infect such systems once, whereas systems which are mapped drives are constantly
attempted to be re-infected. Secondly, a machine infected via another share will switch between
_setup and explore per reboot.
Existence of any of the 3 file names mentioned above [note EXPLORER.EXE is a valid name - do
not confuse this name]. Process running as mentioned above, files being corrupted / deleted as
mentioned above.
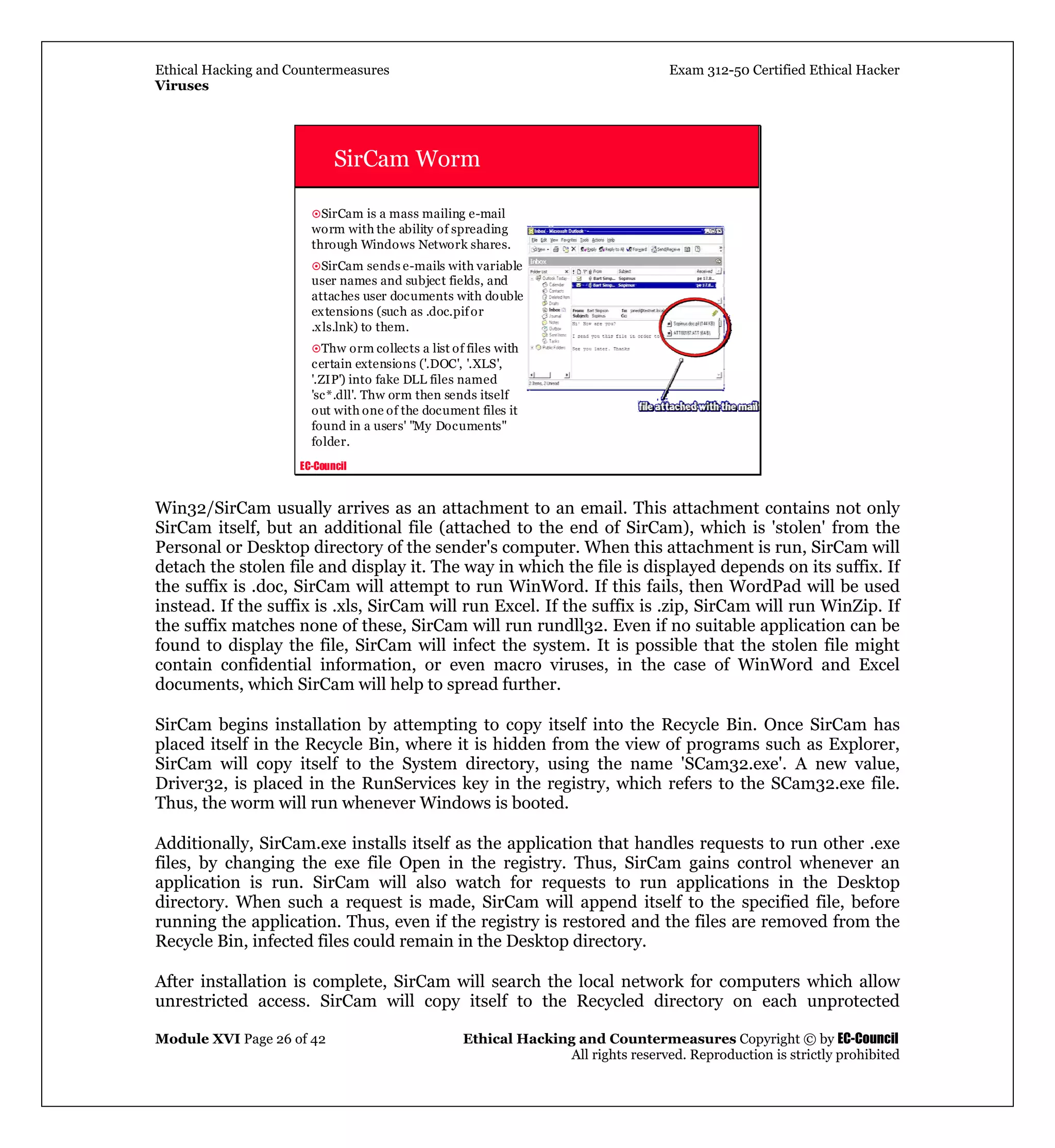
Running the file will directly infect the local system by installing itself and running memory
resident, then it will use browsing of the network to locate available shares. The program searches
local and networked drives (drive letters C through Z) for specific file types and attempts to erase
the contents of the files, leaving a zero byte file. The targets may include Microsoft Office files,
such as .doc, .xls, and .ppt, and various source code files, such as .c, .cpp, .h, and .asm.
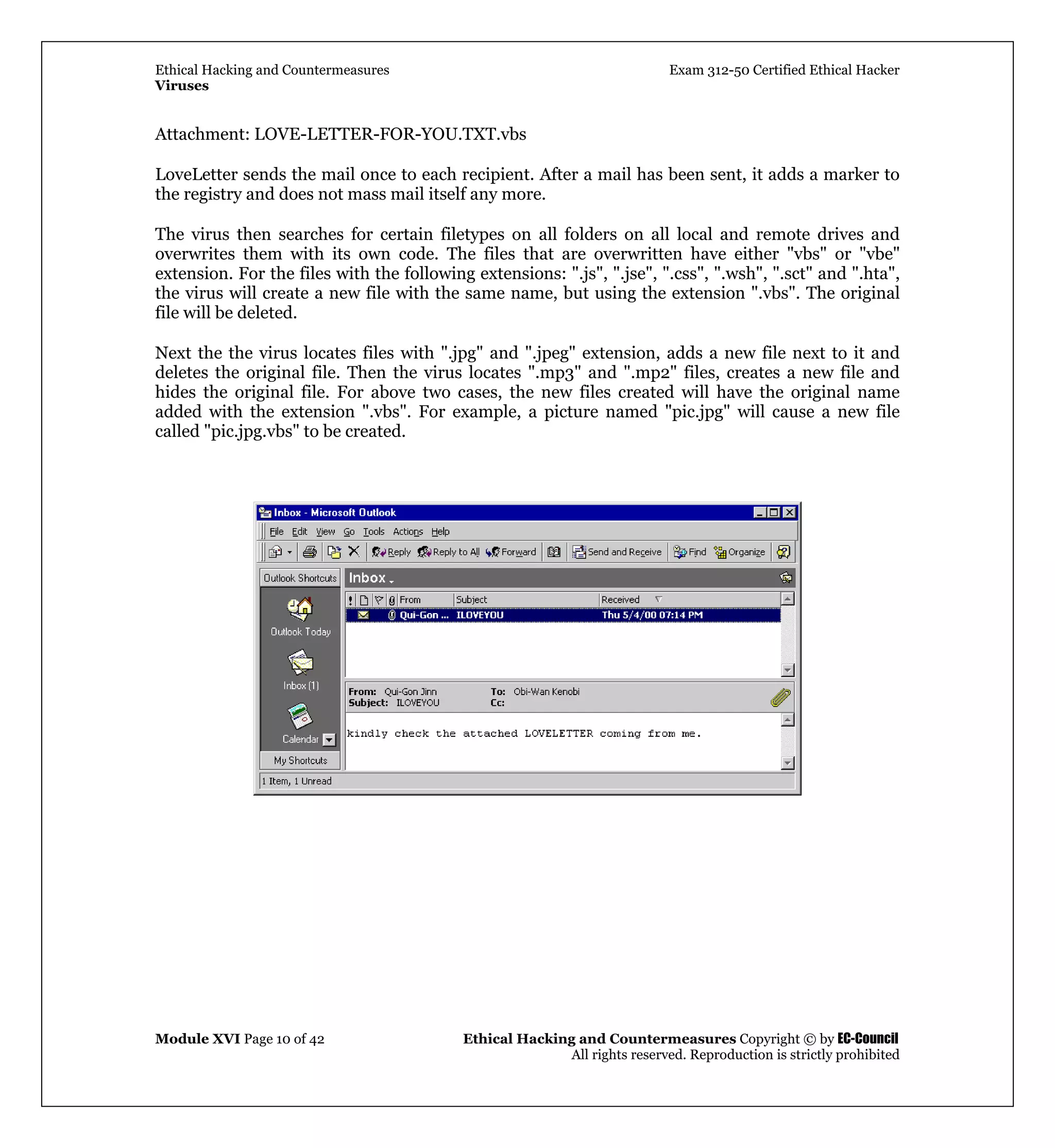
The program propagates by replying to any new email that is received by an infected computer. A
copy of zipped_files.exe is attached to the reply message. The program creates an entry in the
Windows 95/98 WIN.INI file:
run=C:WINDOWSSYSTEMExplore.exe
On Windows NT systems, an entry is made in the system registry:
[HKEY_CURRENT_USERSoftwareMicrosoftWindows
NTCurrentVersionWindows]
run = "c:winntsystem32explore.exe"
The program creates a file called explore.exe in the following locations:
Windows 95/98 - c:windowssystemexplore.exe
Windows NT - c:winntsystem32explore.exe
This file is a copy of the zipped_files.exe Trojan horse, and the file size is 210432 bytes.
MD5 (Explore.exe) = 0e10993050e5ed199e90f7372259e44b](https://image.slidesharecdn.com/module16virus-190228070020/75/Module-16-virus-7-2048.jpg)