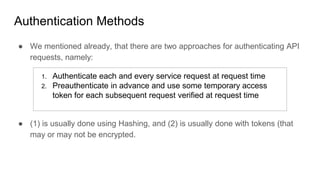
This document discusses identity management and security in cloud computing. It covers key topics such as:
- Centralized identity management provides benefits like a single user identity, consistent security policies, and reduced costs.
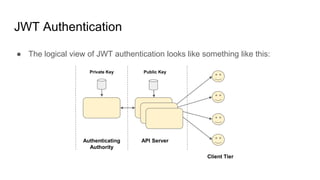
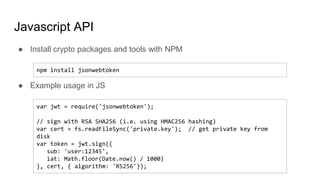
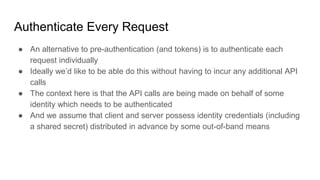
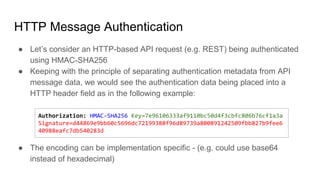
- Authentication establishes a user's identity through credentials. Popular methods include JSON web tokens (JWTs) which use digital signatures to authenticate API requests without authenticating each one individually.
- JWTs work by having a client authenticate once to get a token, then include that token in subsequent requests to prove identity without further authentication. The token contains identity claims and is digitally signed by an authentication authority.