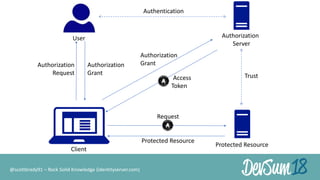
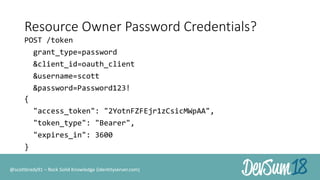
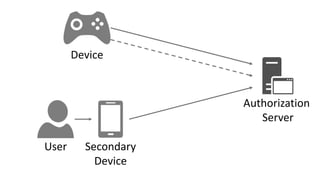
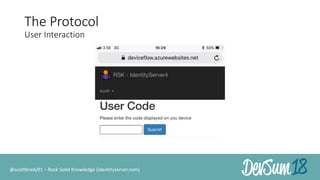
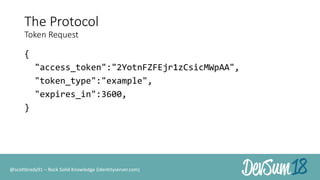
The document discusses secure authorization for devices using the OAuth device flow, addressing problems like delegating application access for browserless and input-constrained devices. It outlines the protocol for device authorization and user interaction, emphasizing the importance of user security and privacy. Additionally, it highlights the implementation of OAuth device flow in IdentityServer and its potential applications in various contexts, such as public printers and smart devices.