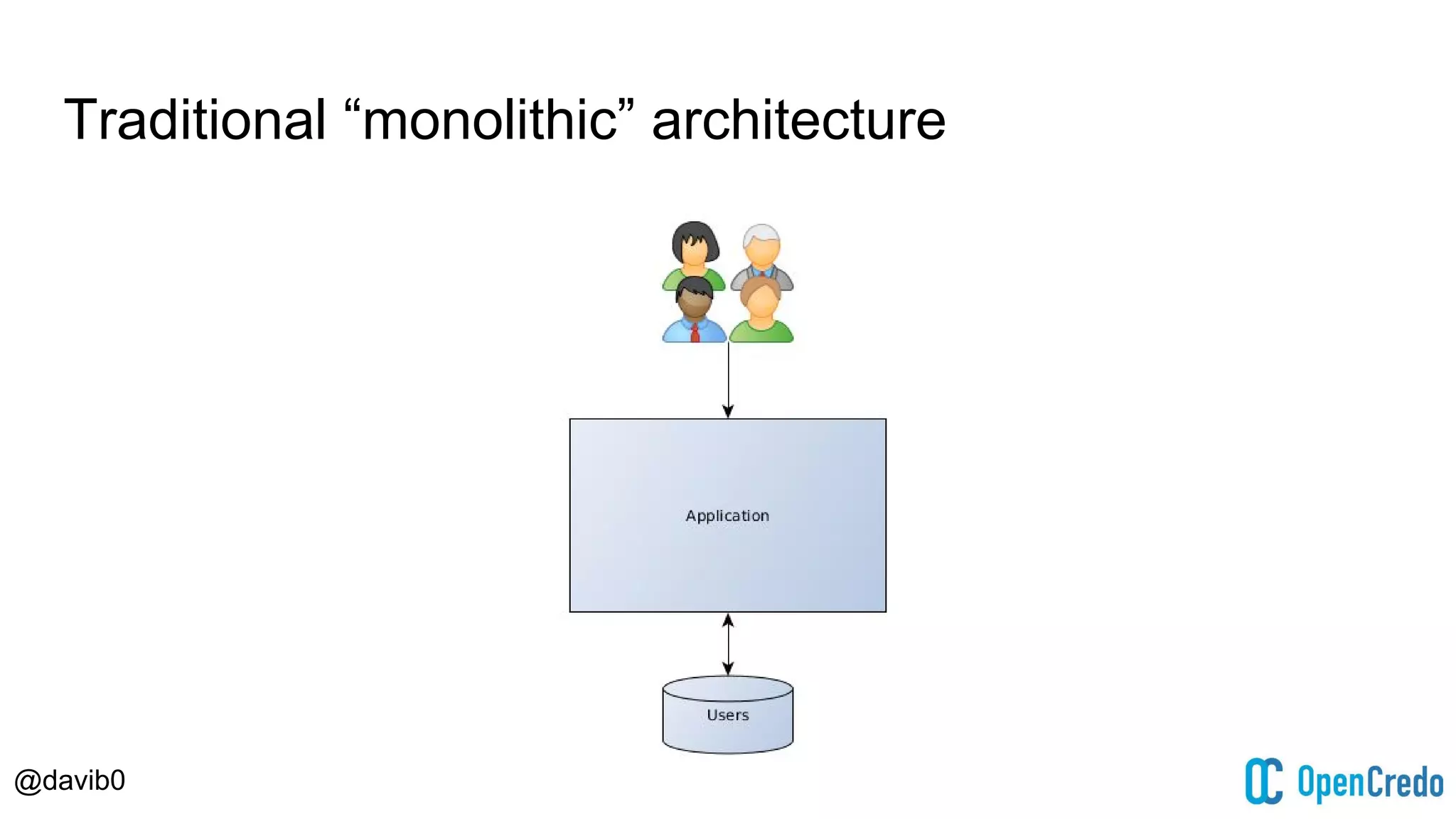
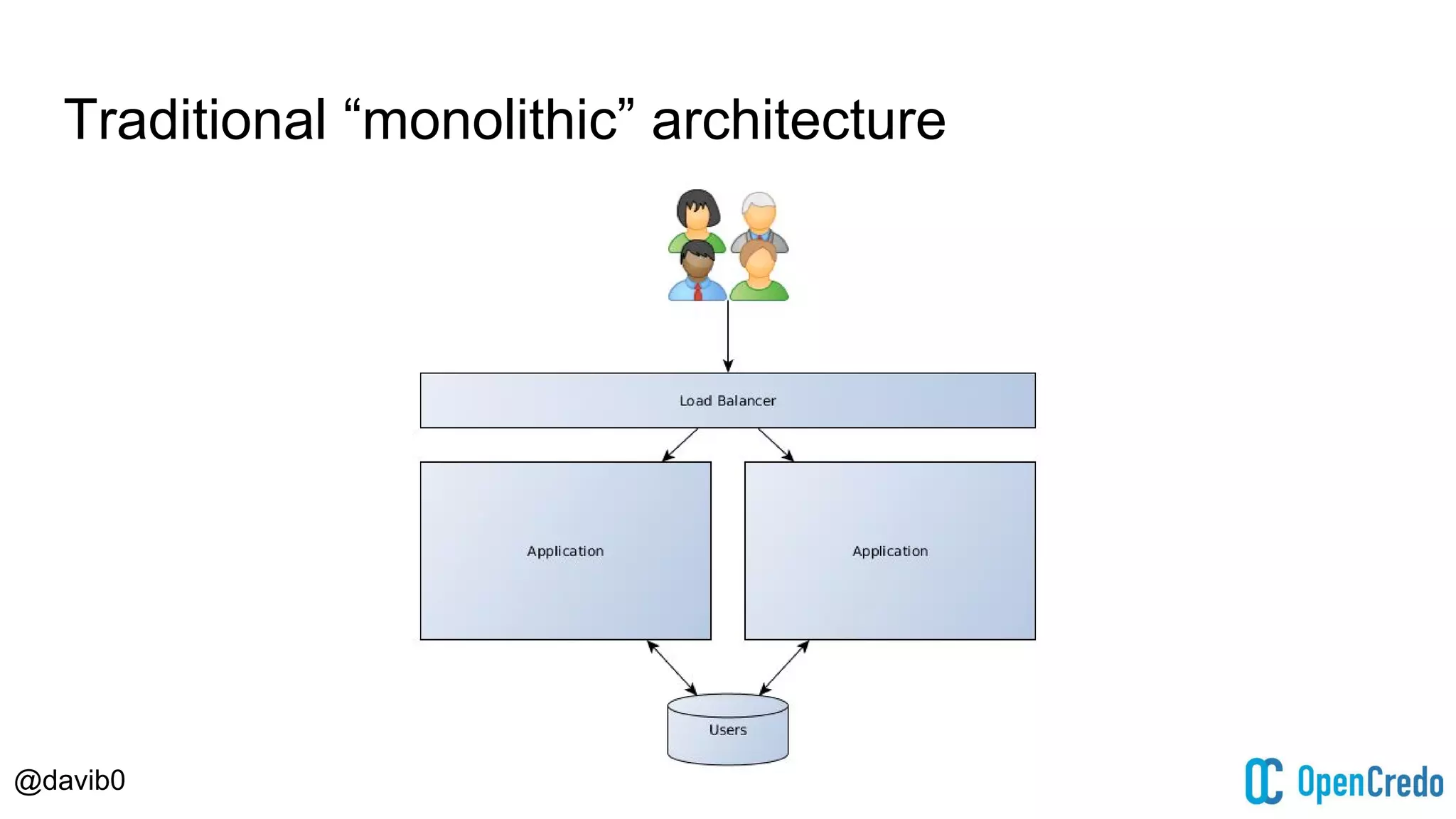
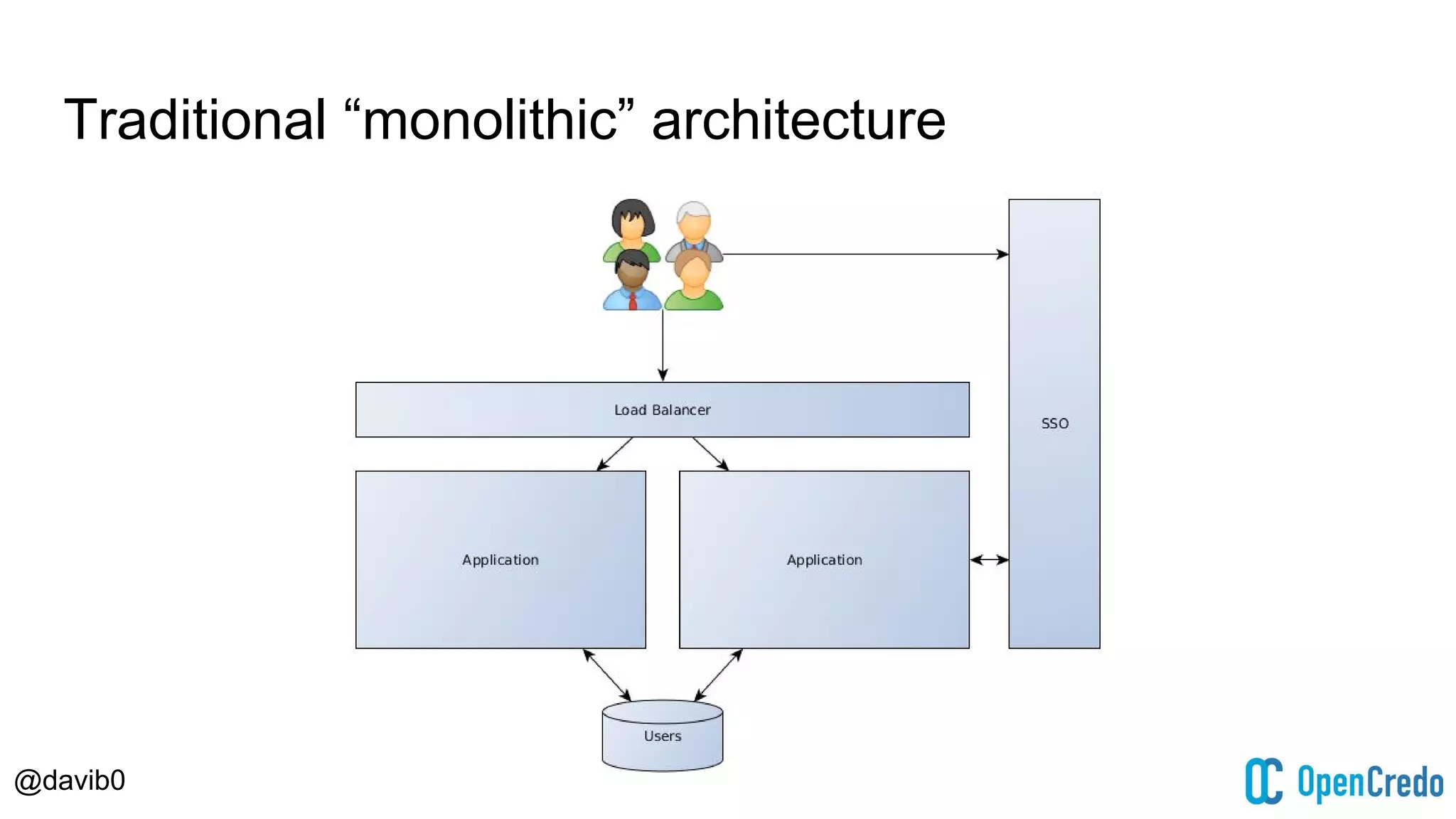
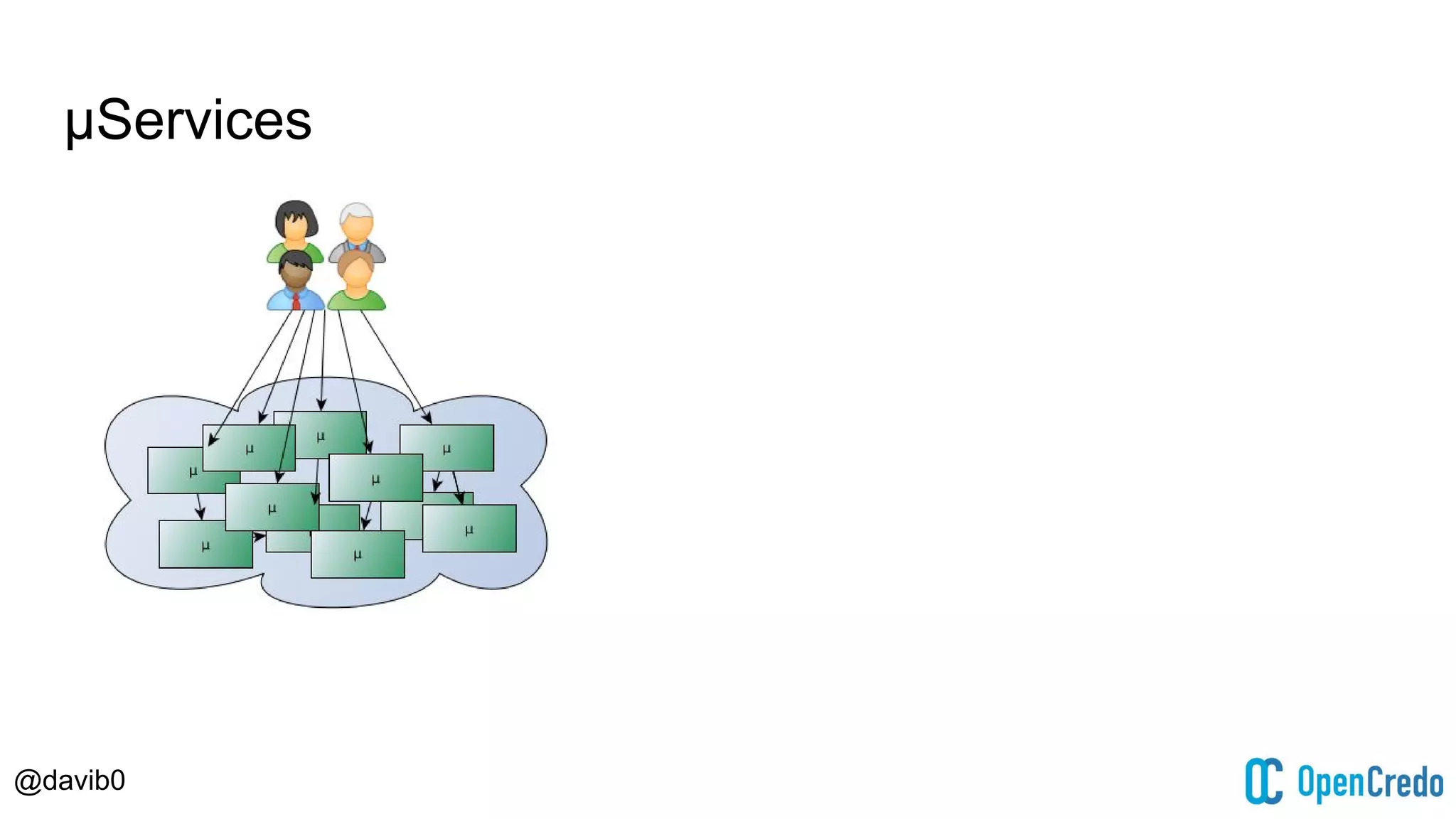
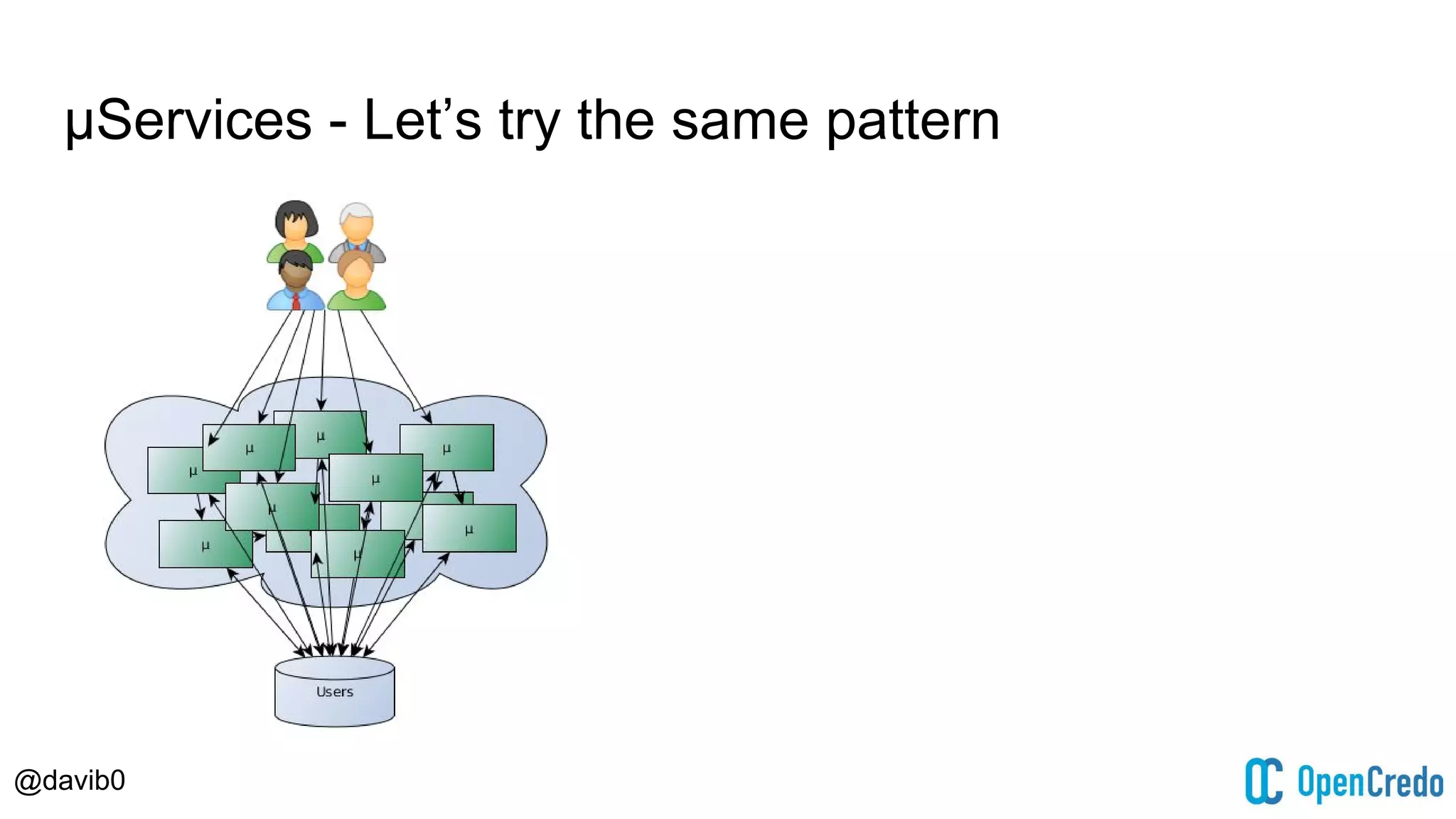
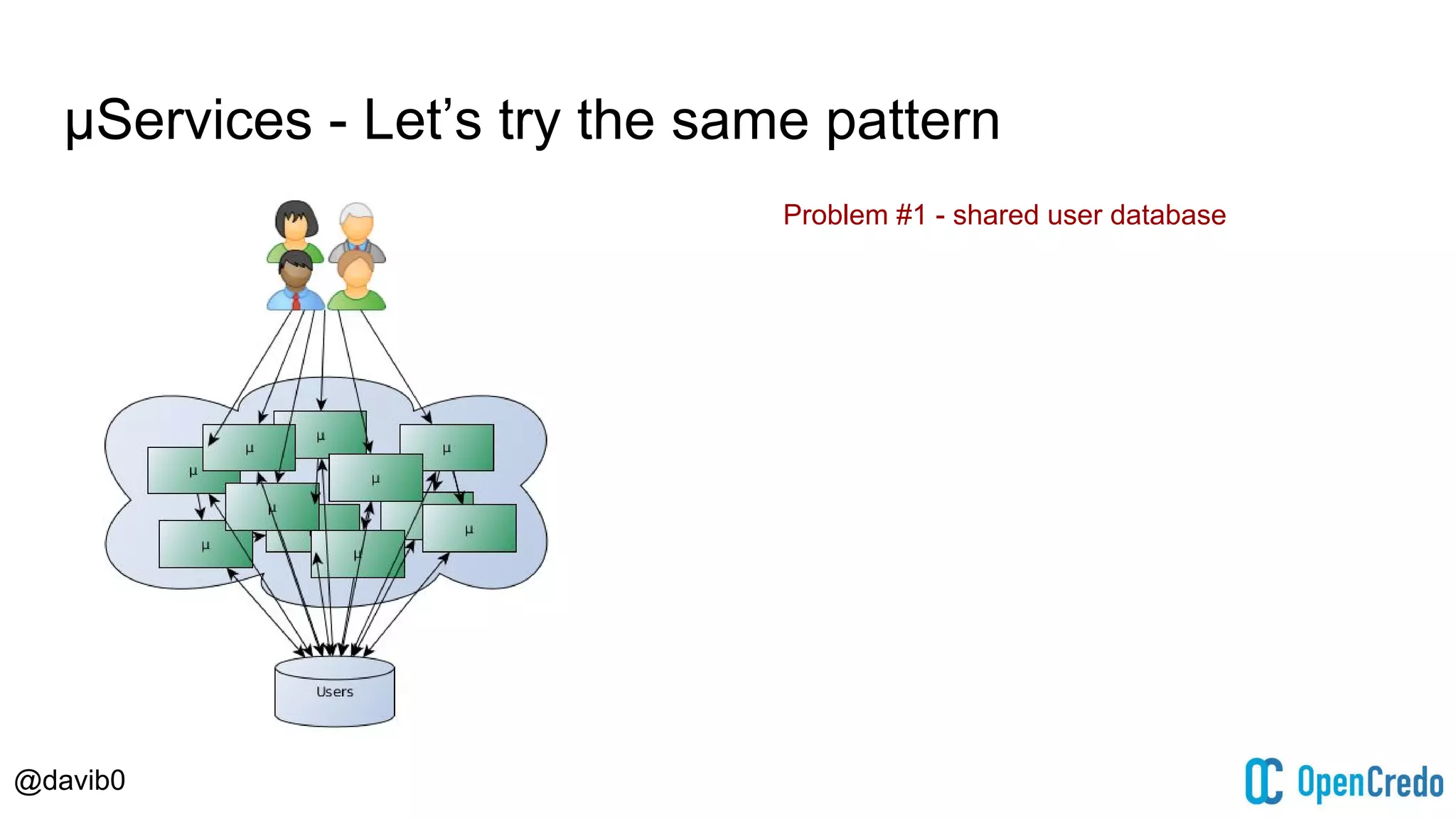
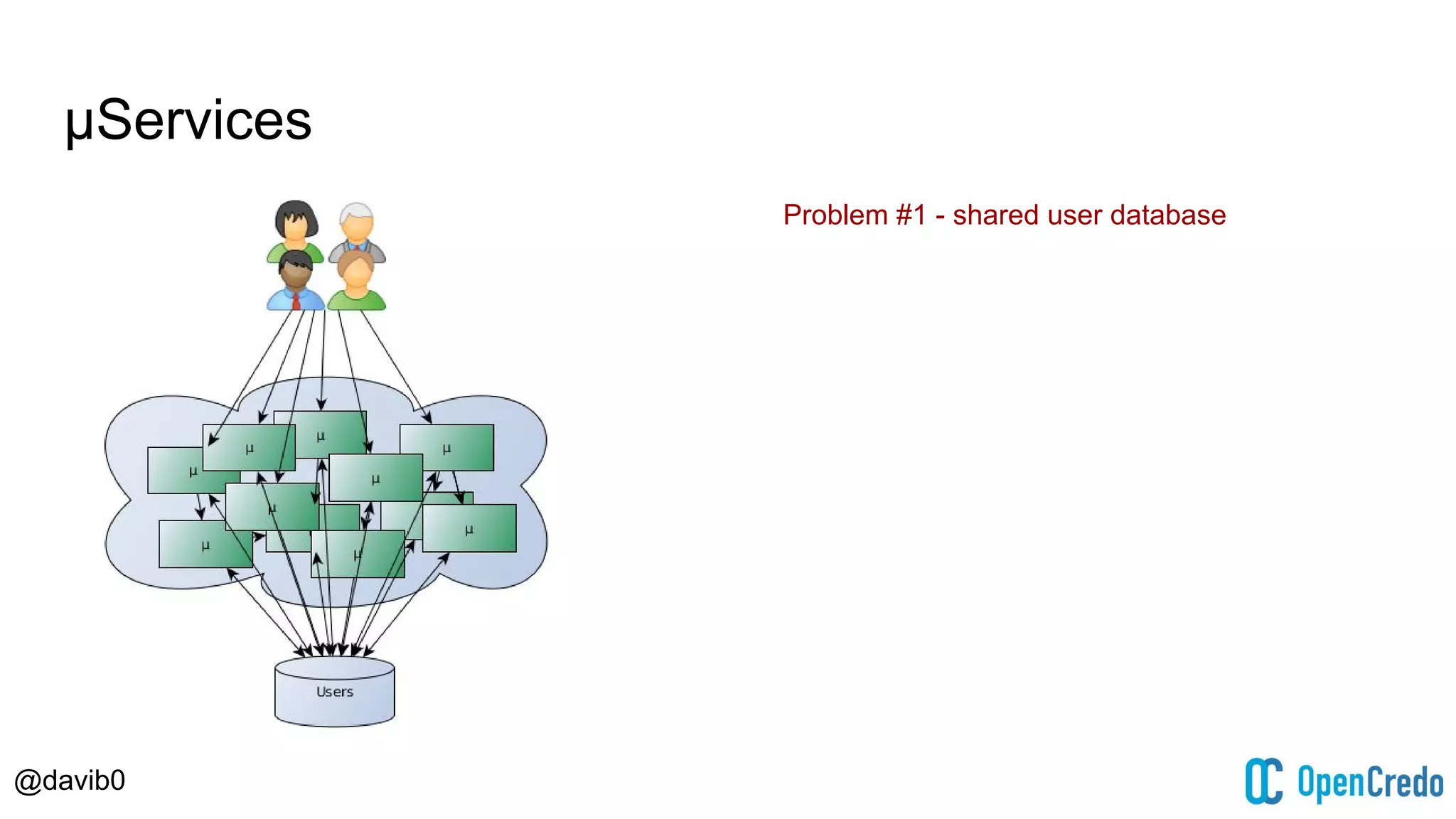
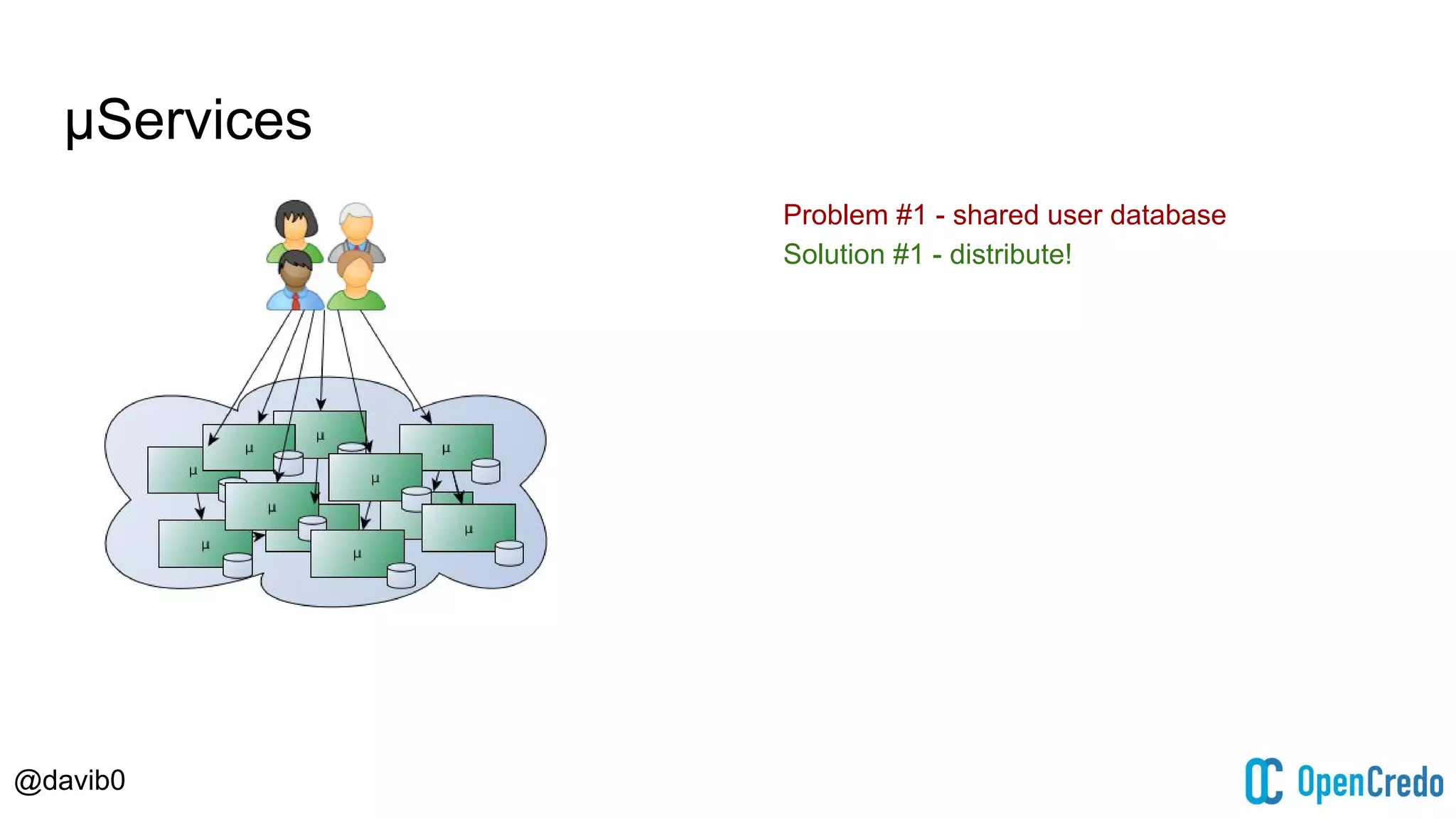
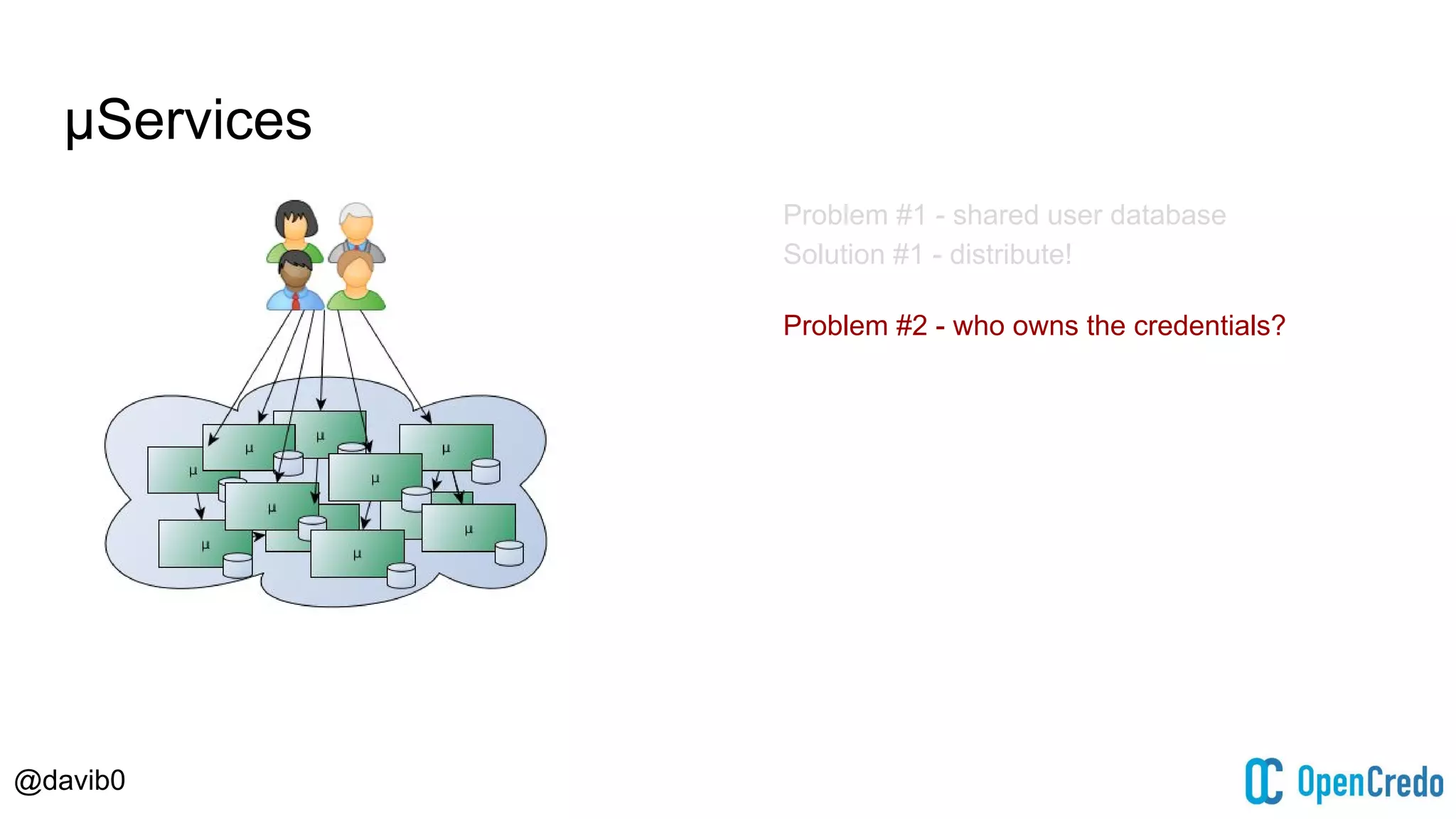
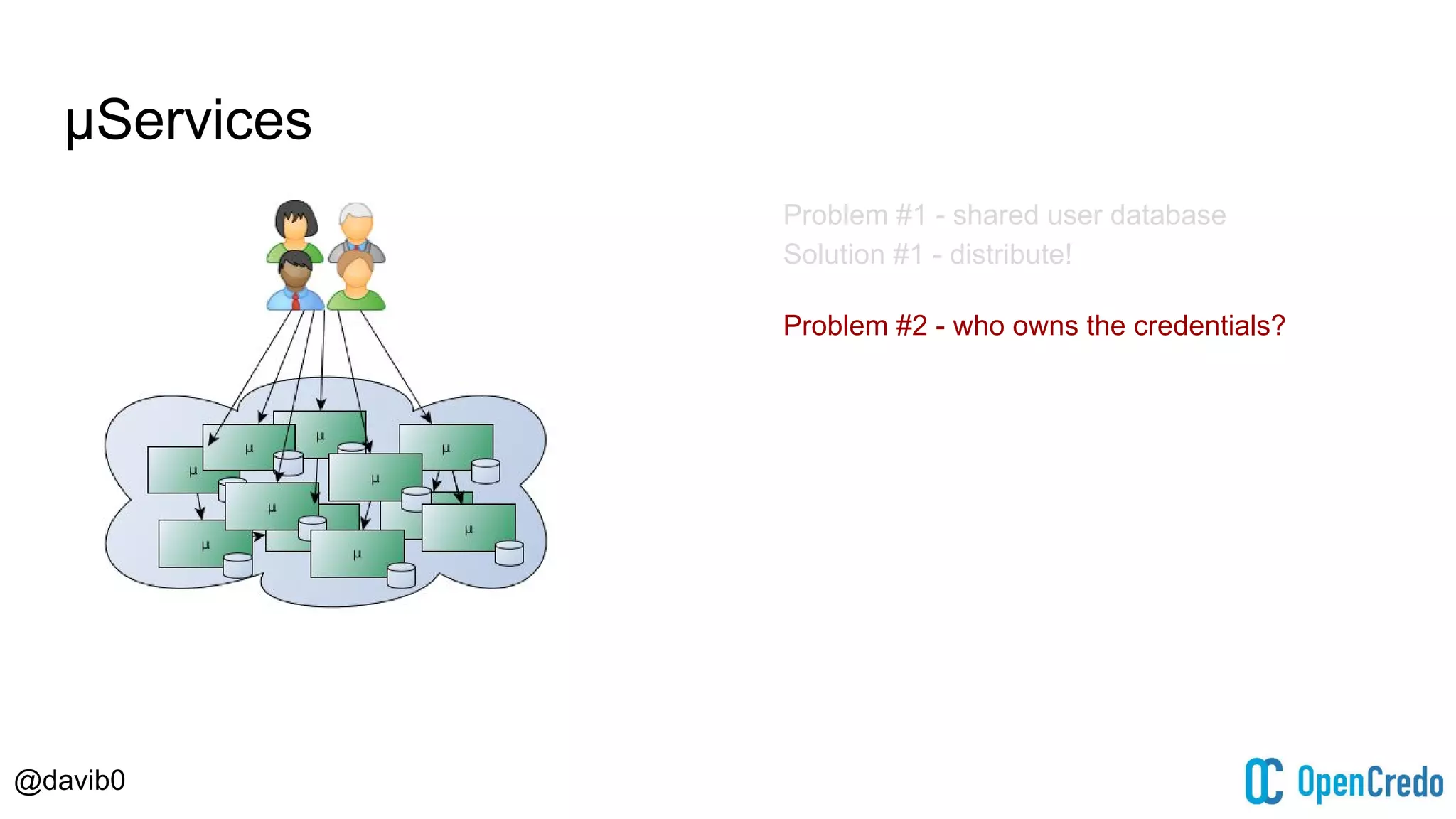
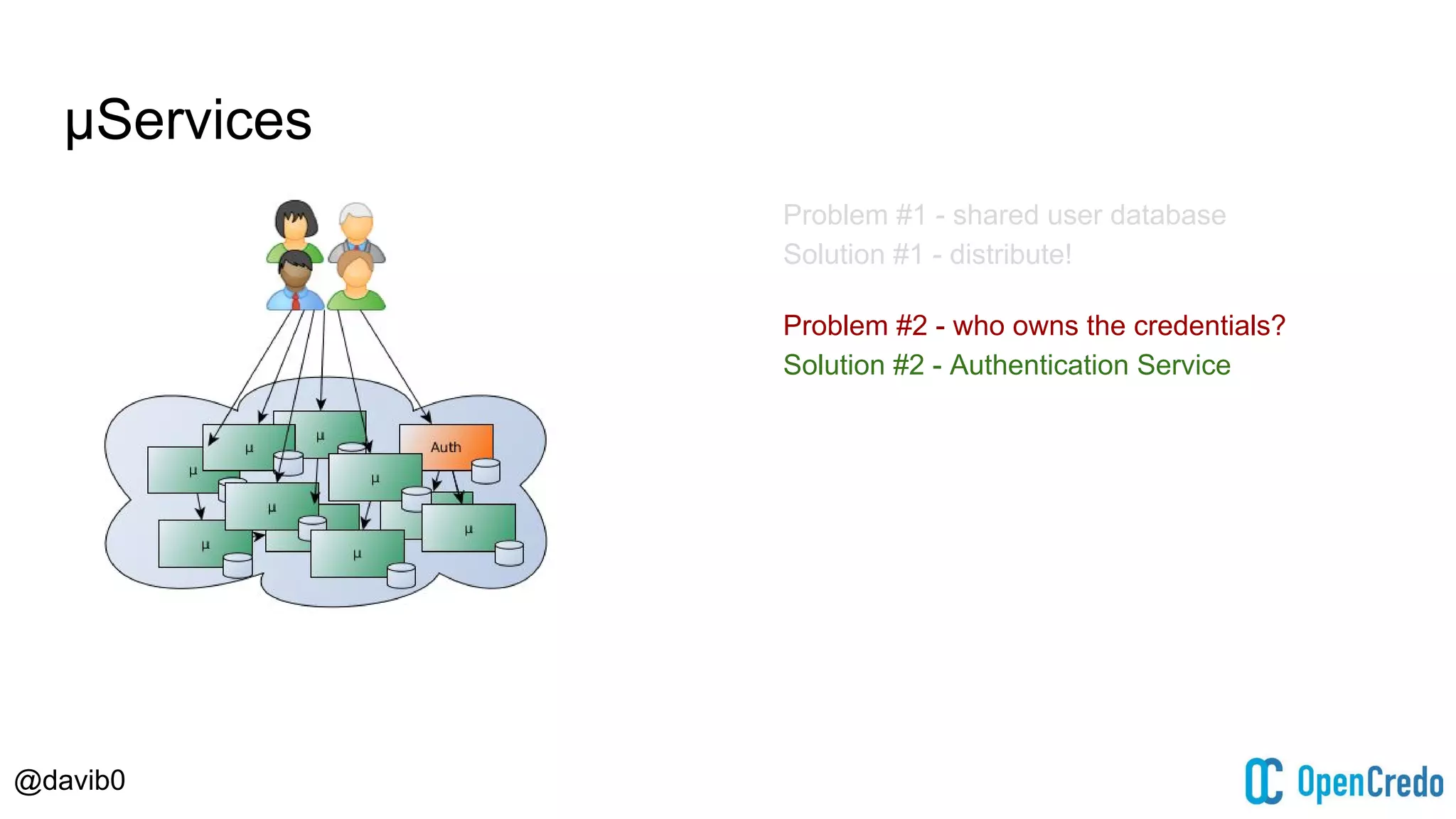
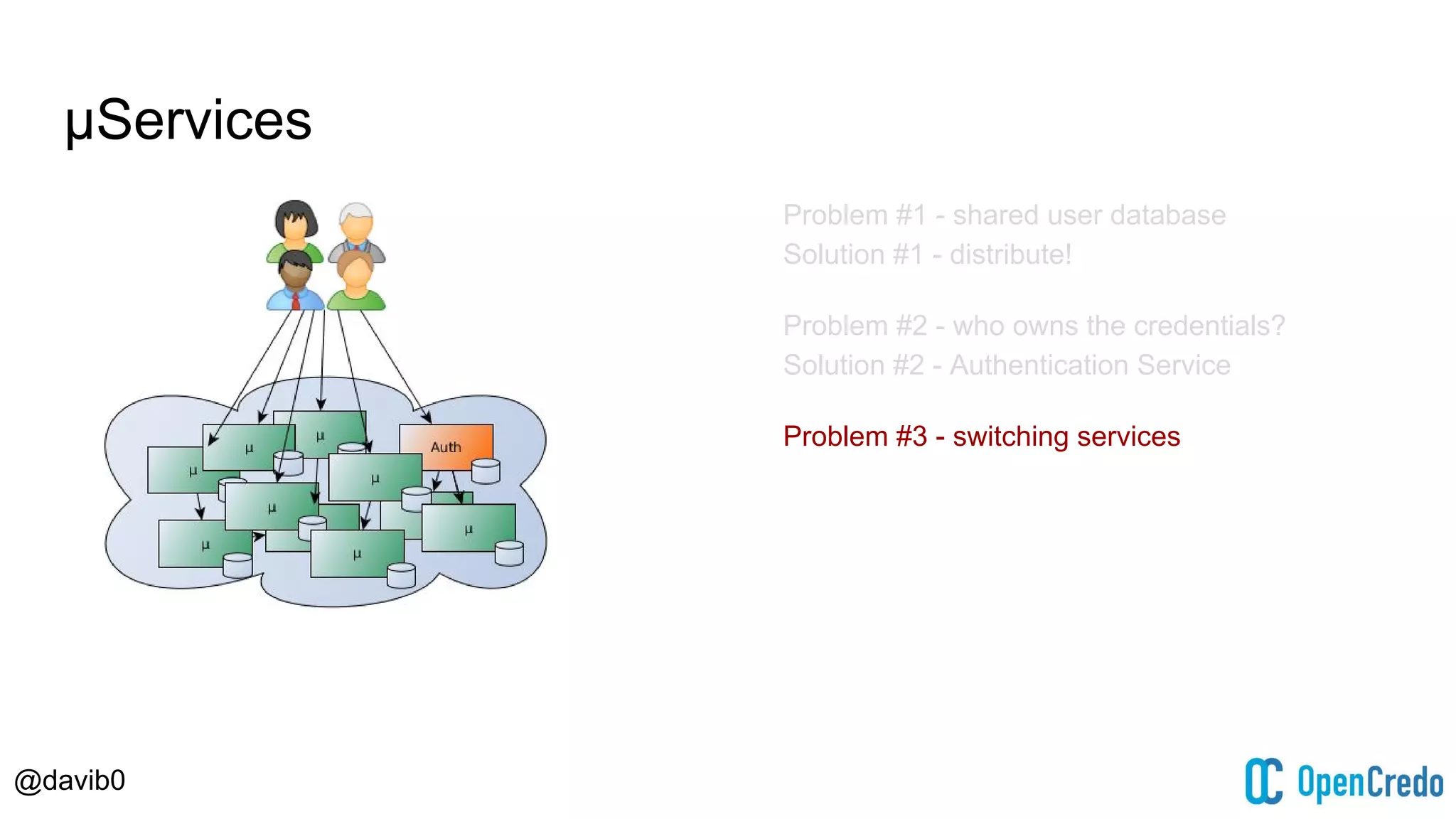
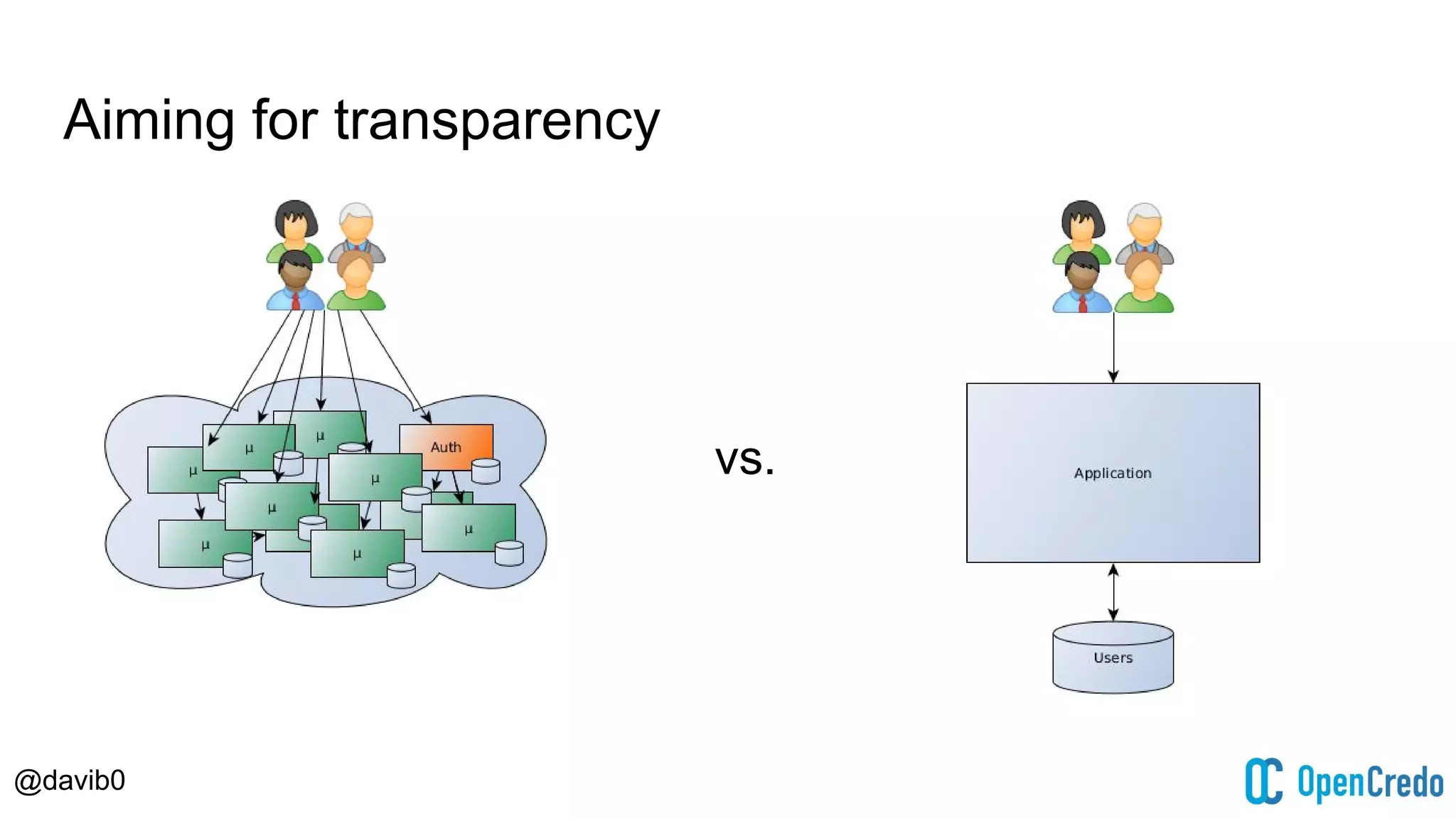
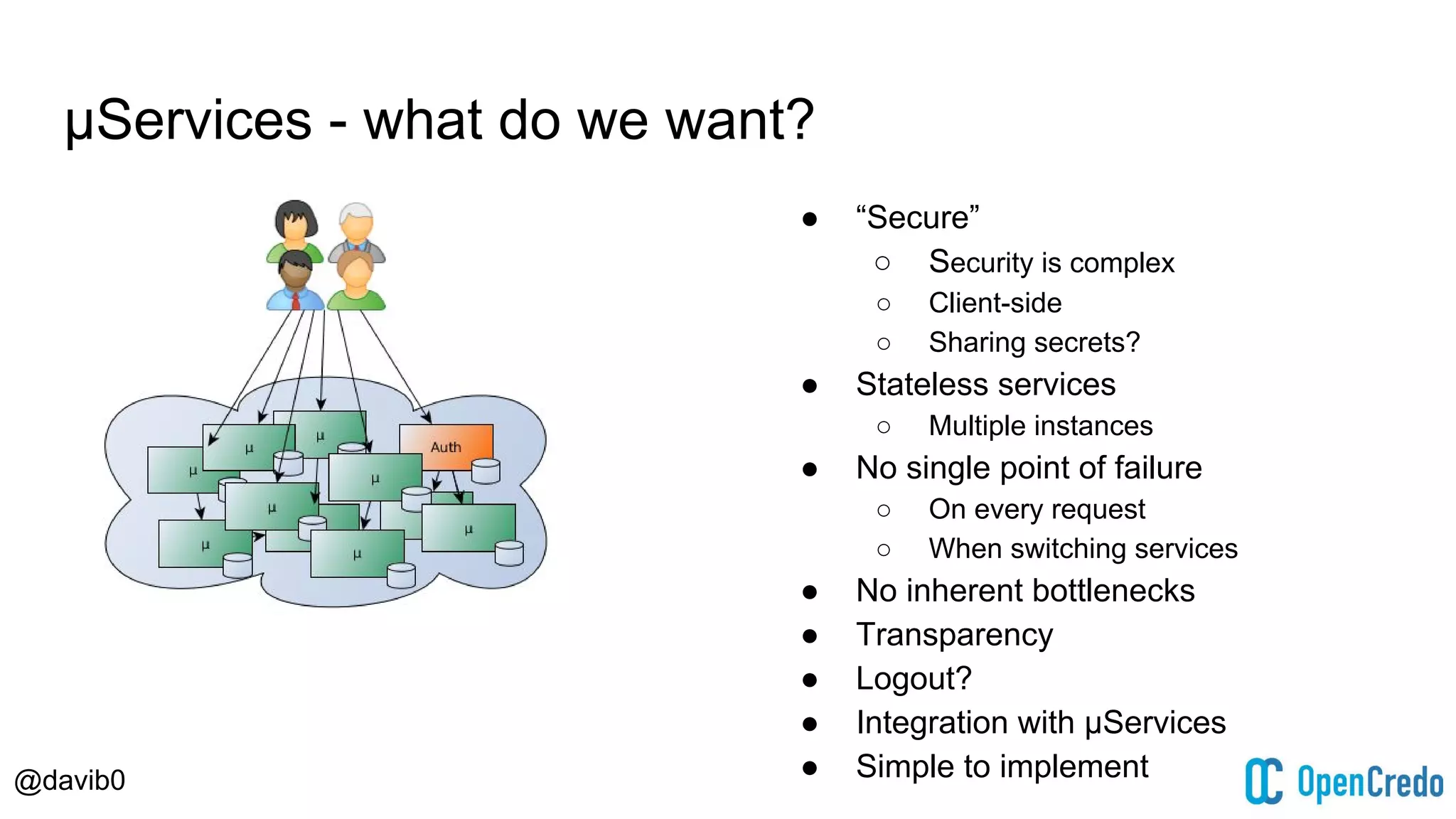
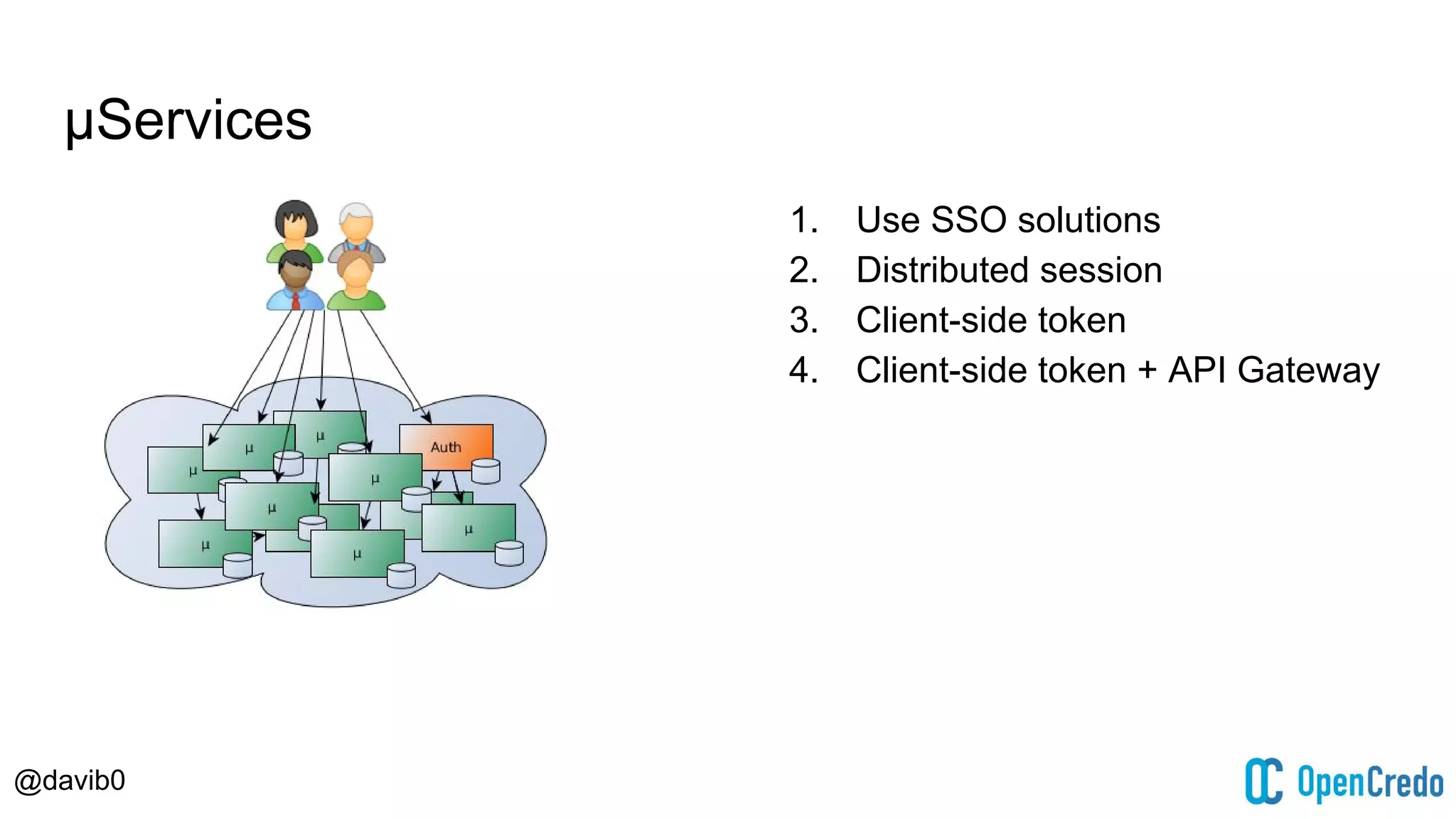
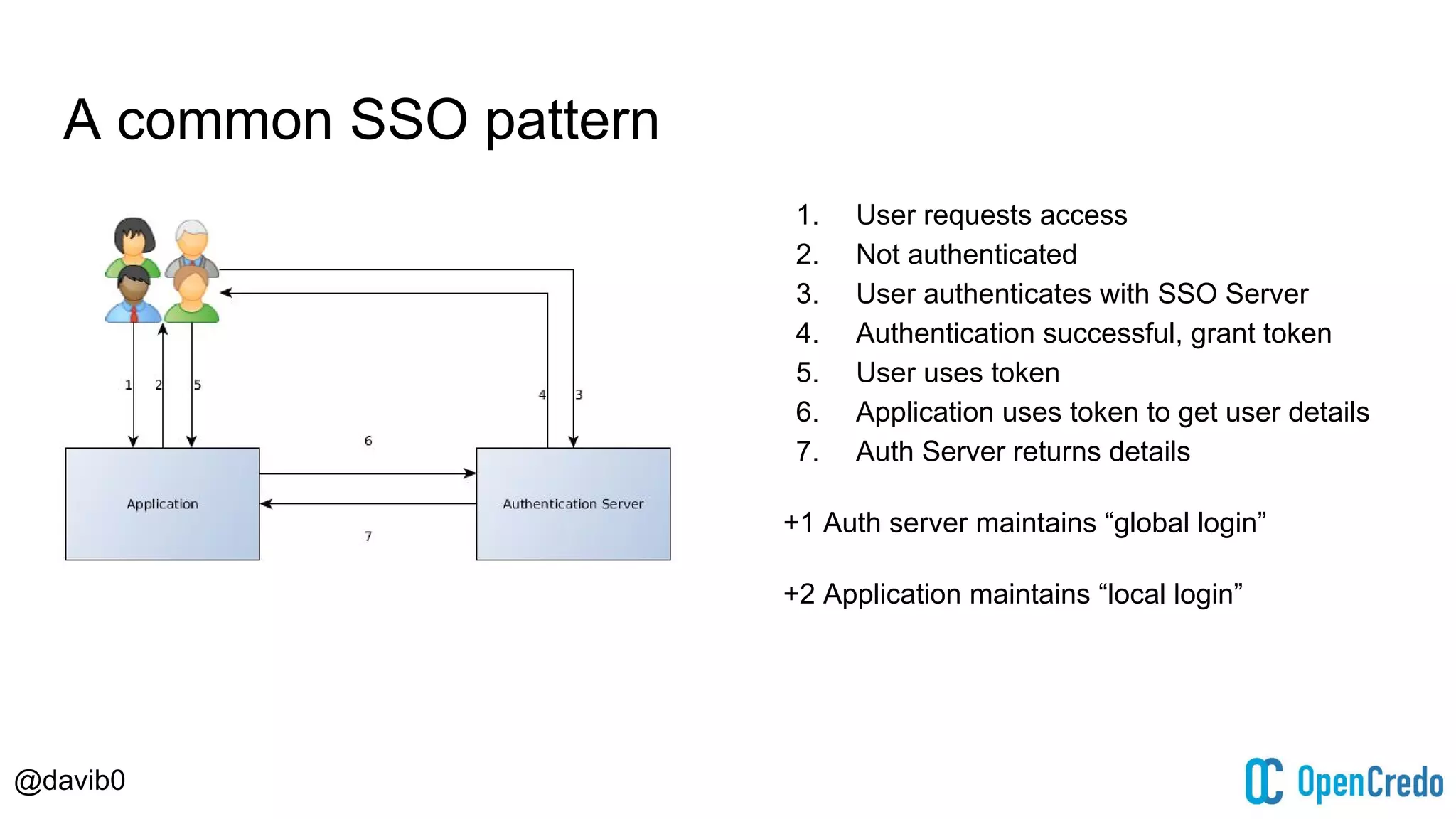
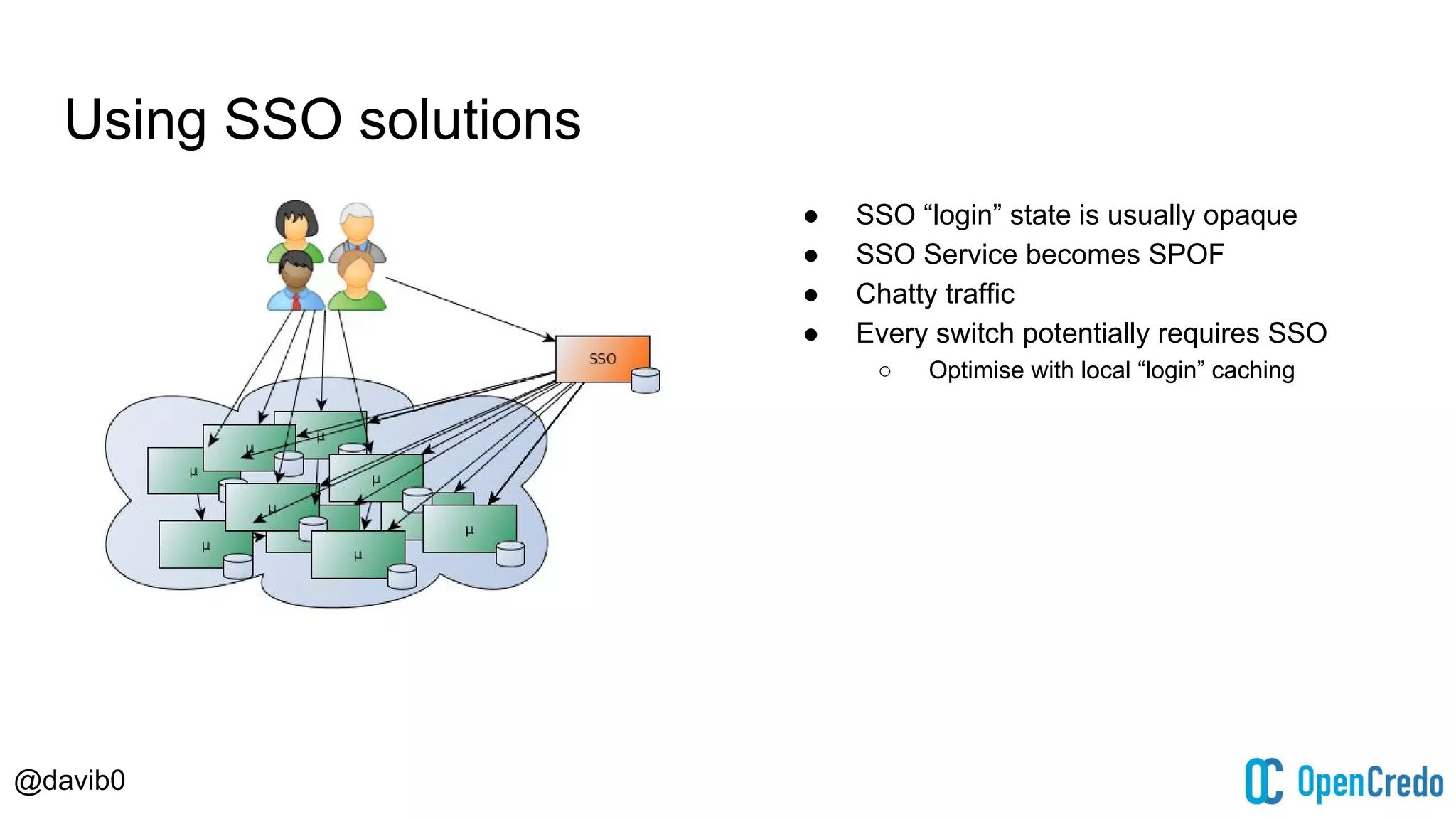
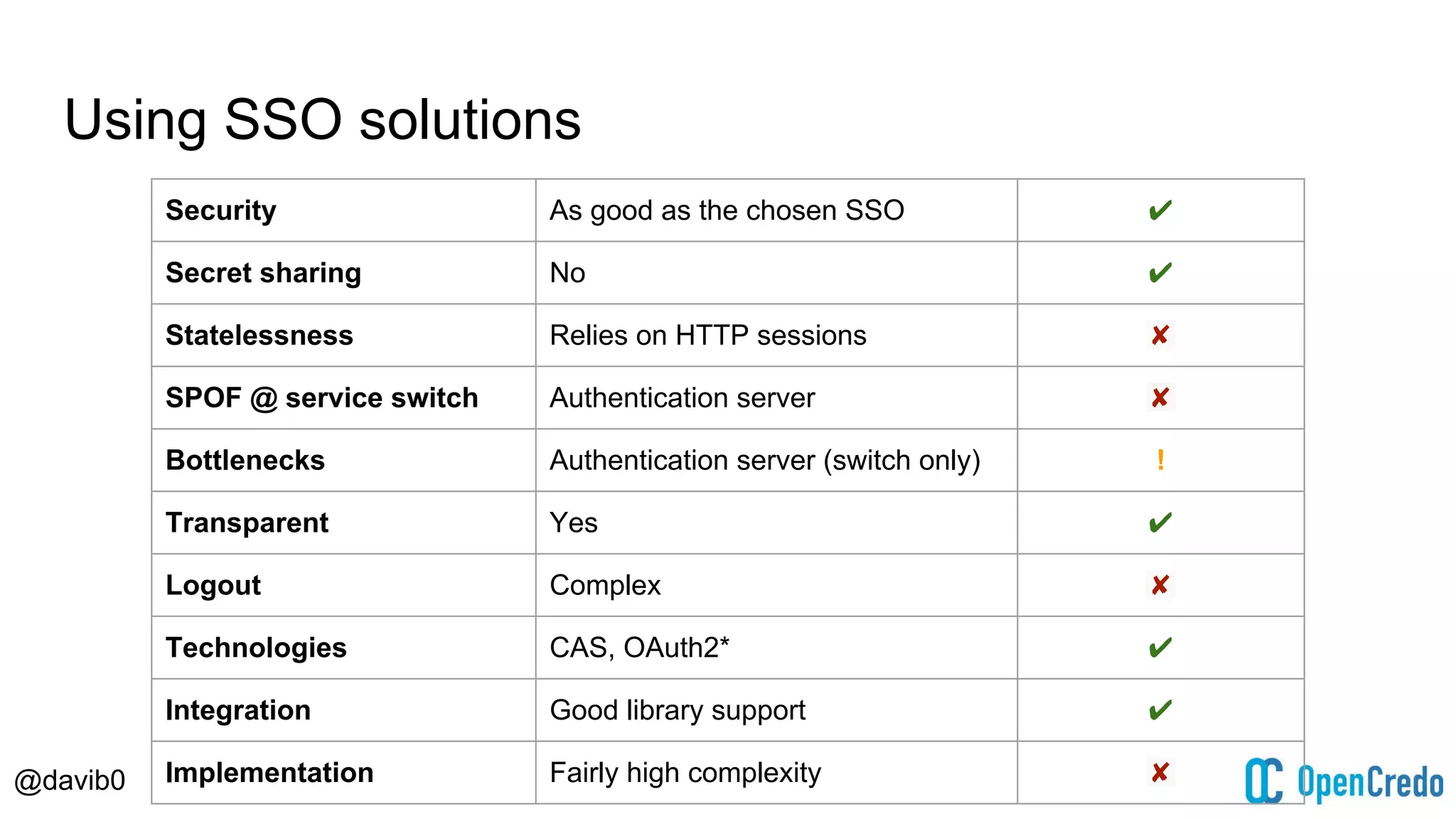
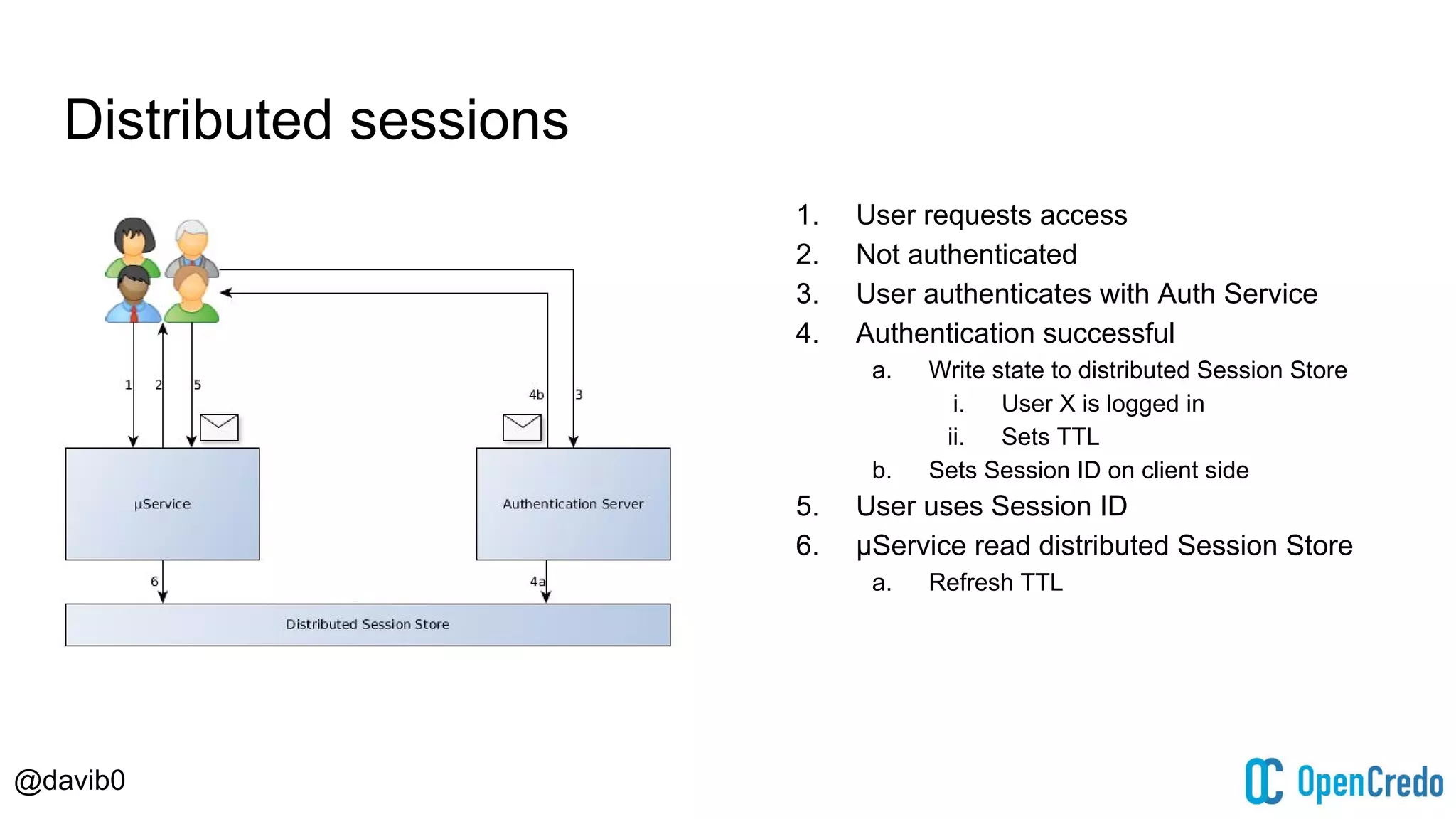
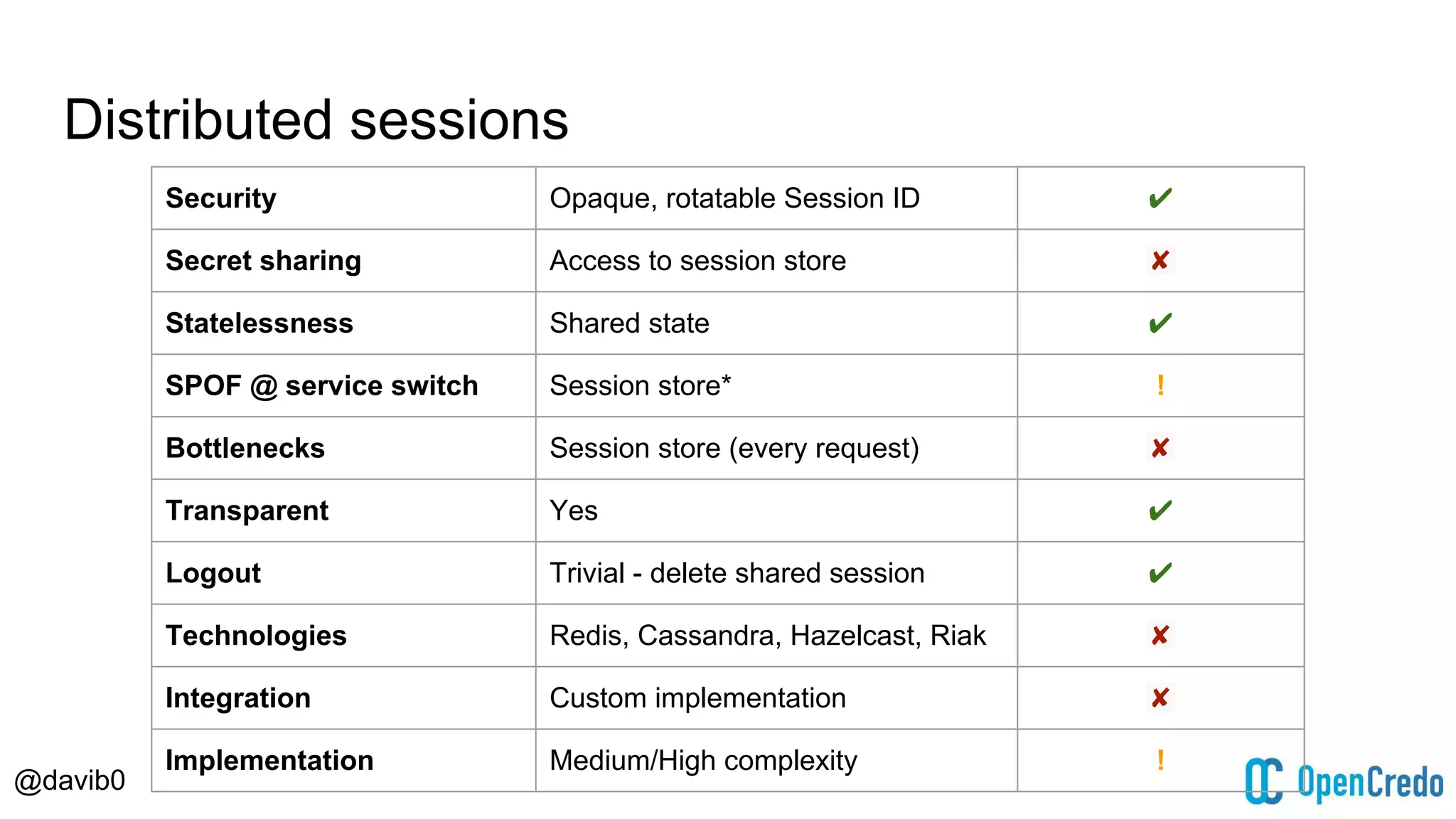
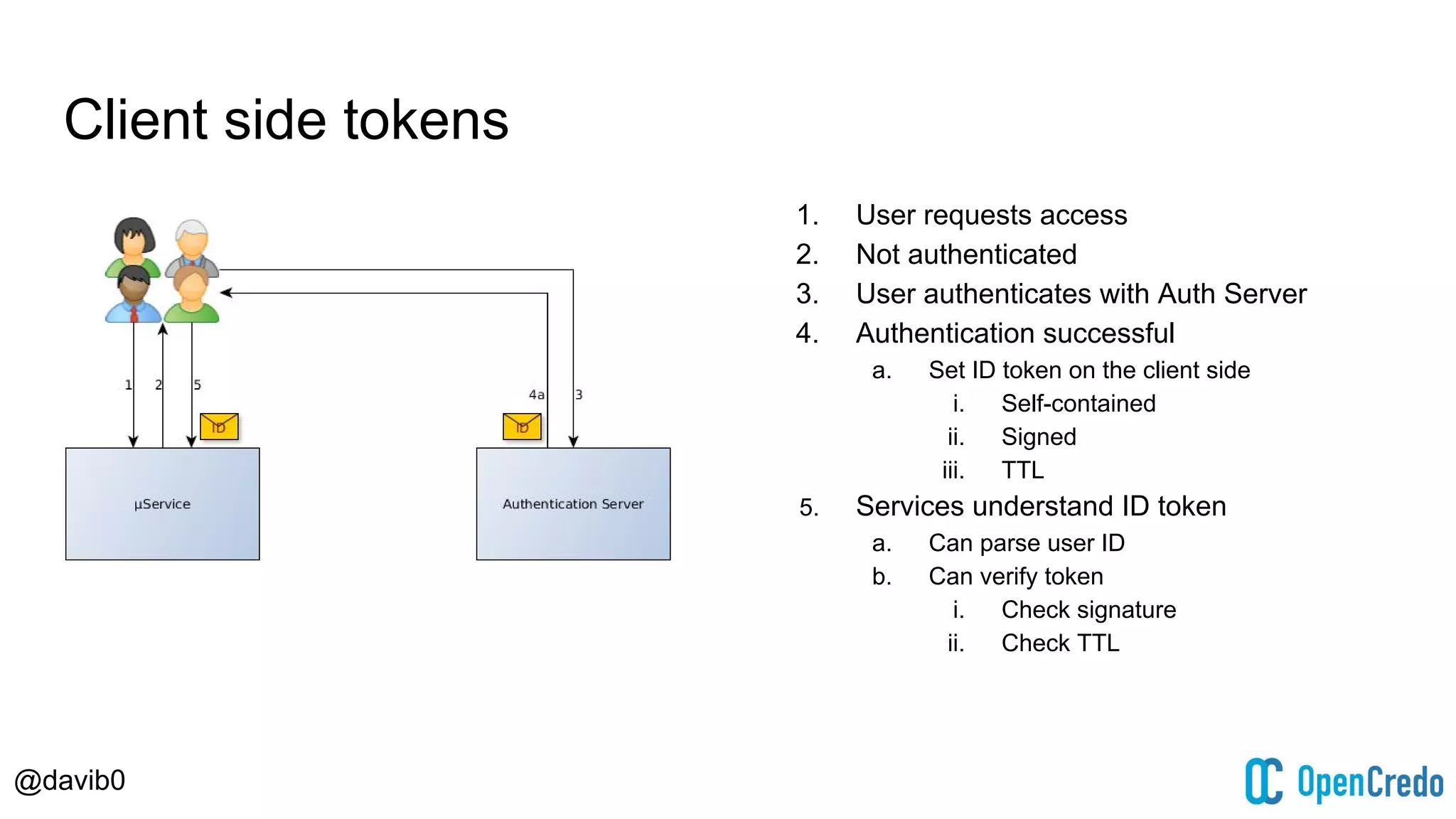
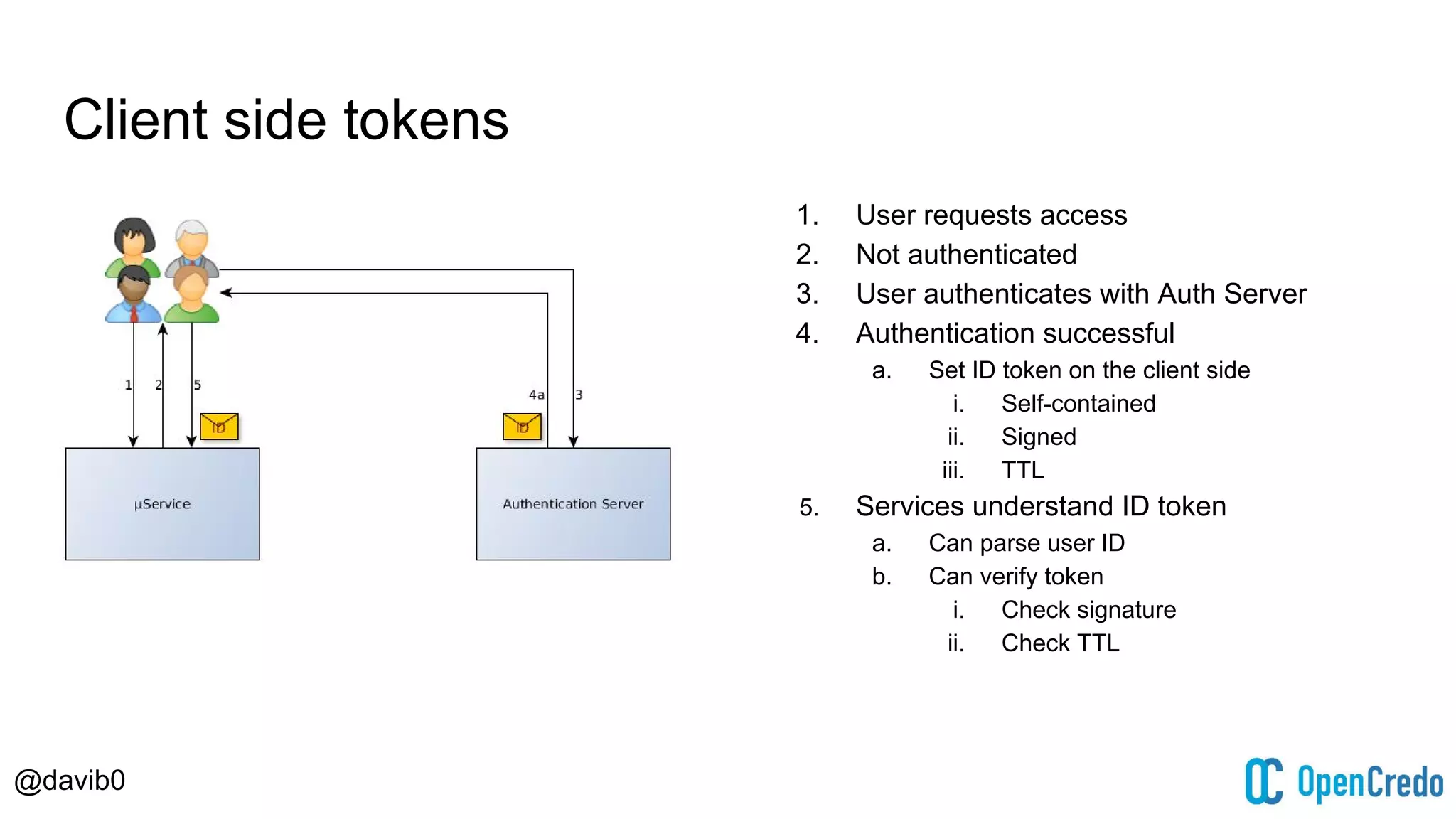
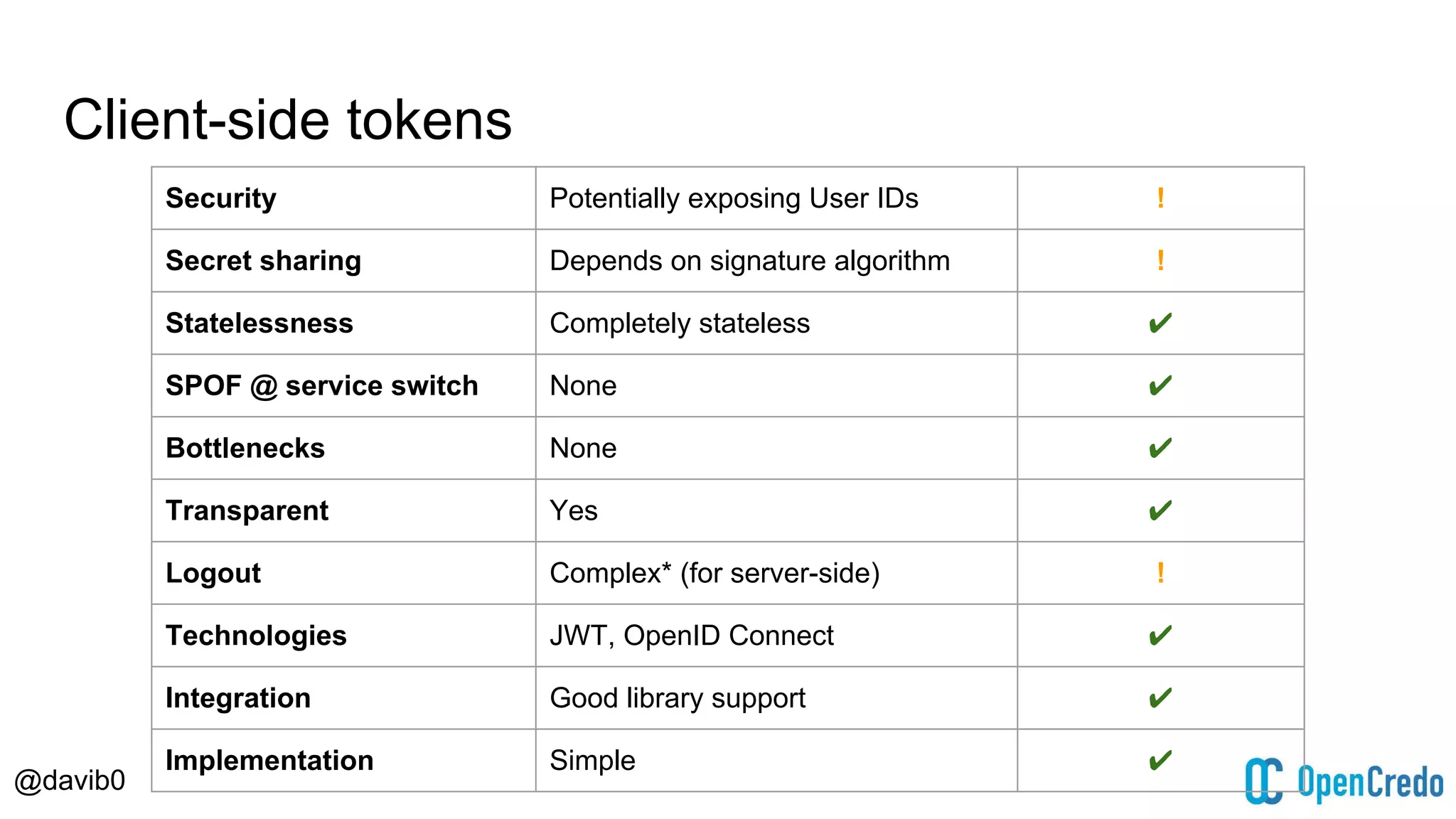
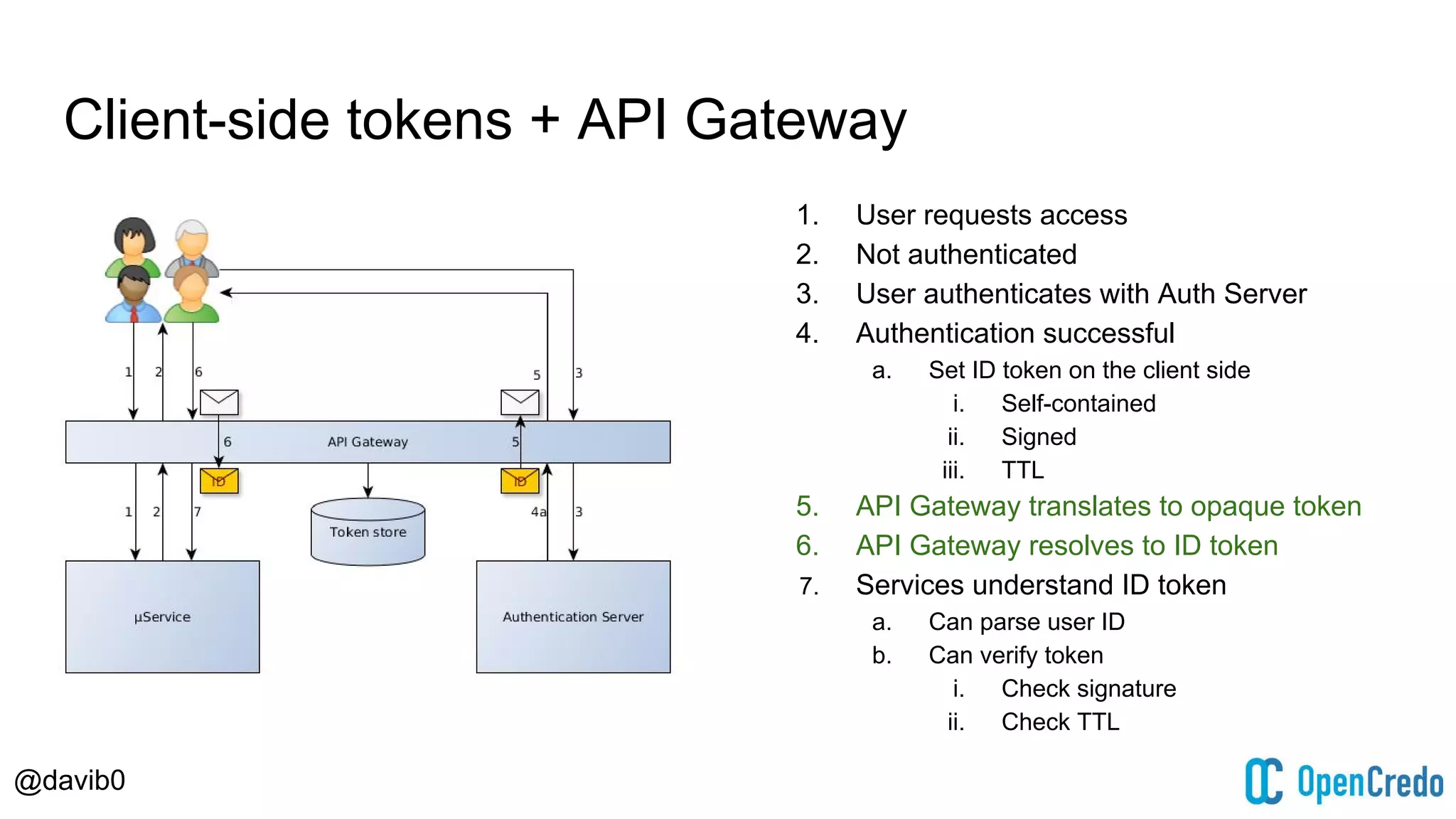
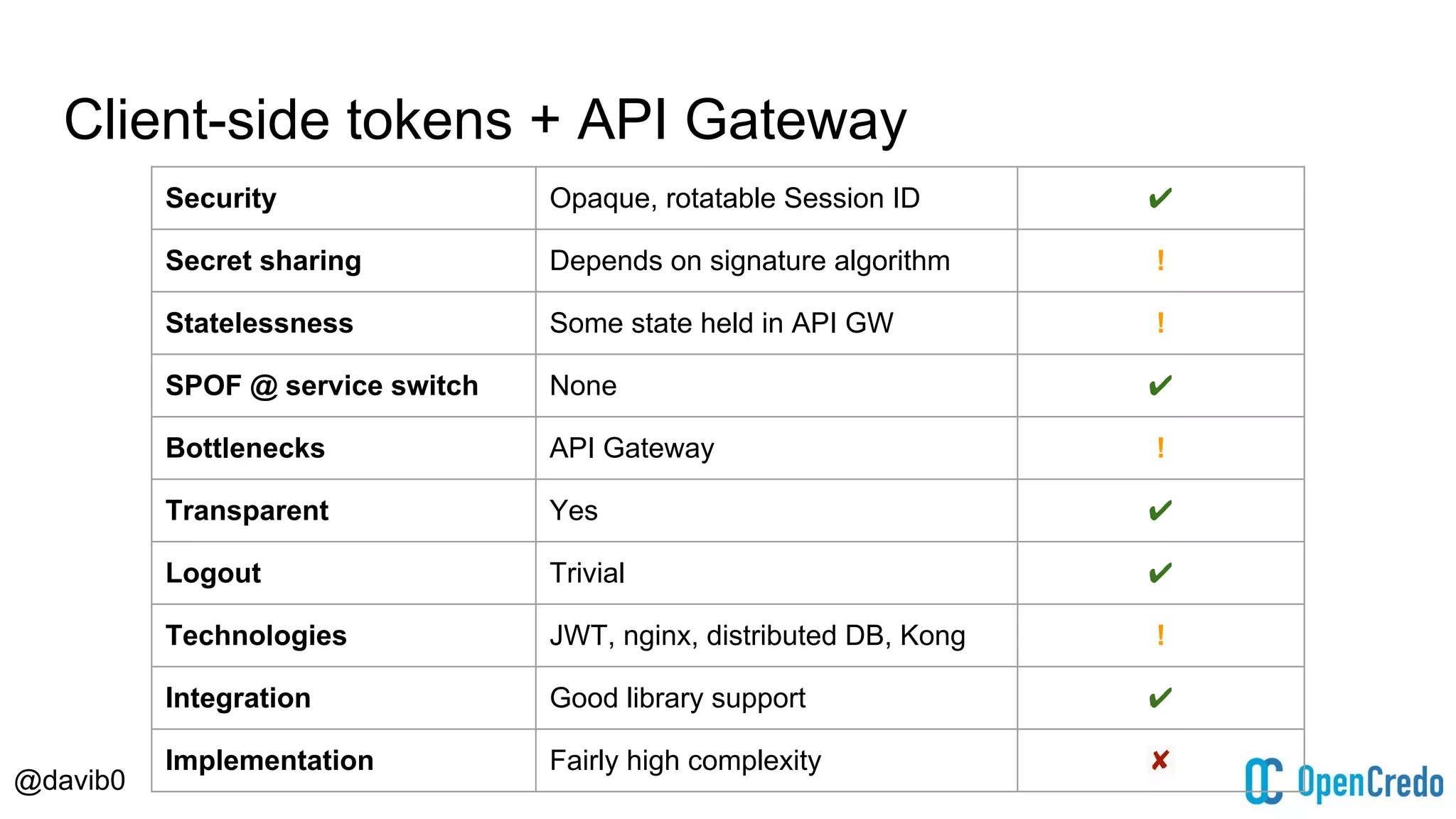
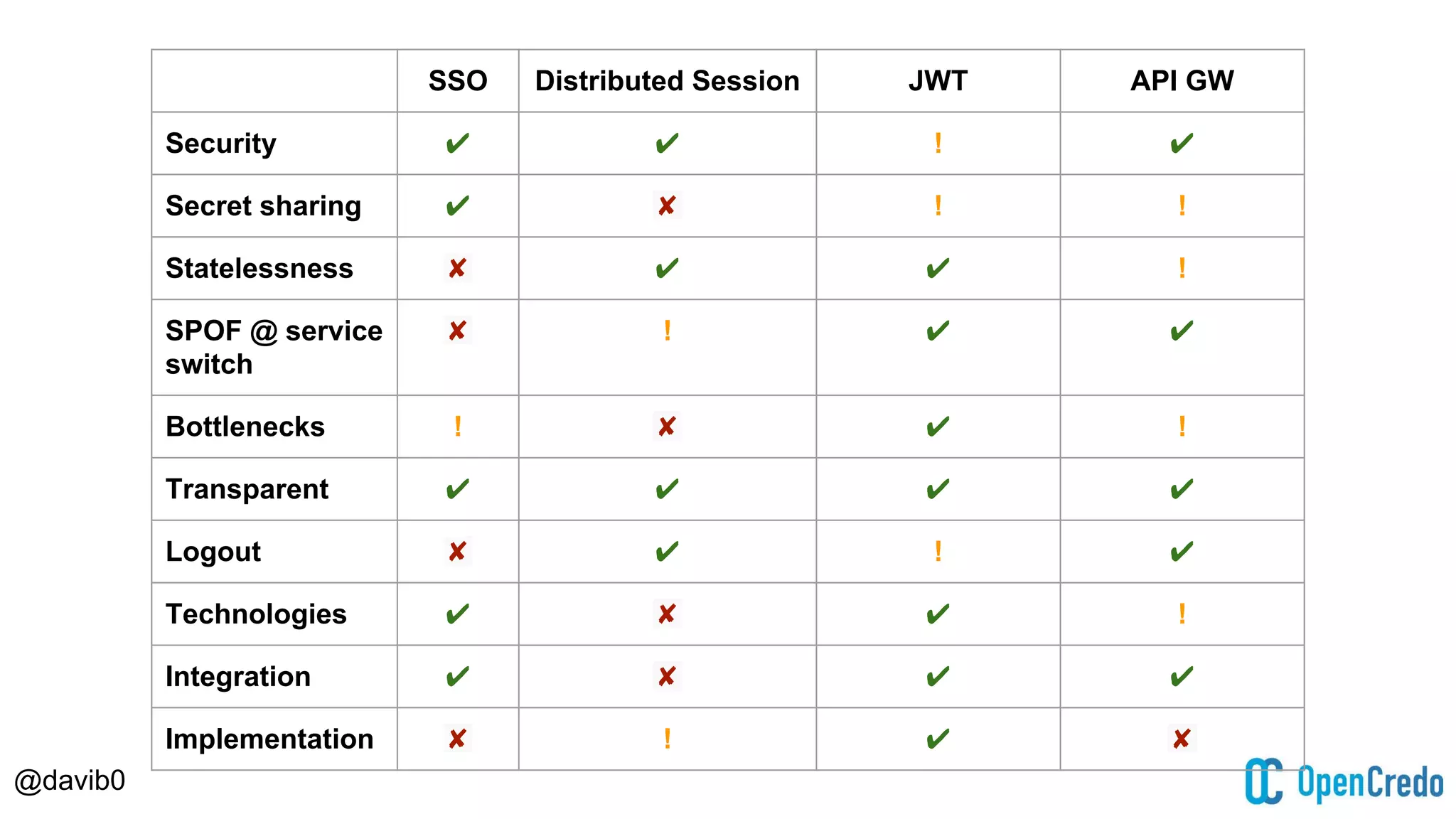
The document discusses authentication and authorization challenges in microservice architectures, highlighting issues such as shared user databases and ownership of credentials. It presents various solutions including Single Sign-On (SSO), distributed sessions, client-side tokens, and the use of API gateways, evaluating their security, statelessness, and integration complexity. The document emphasizes the need for robust authentication mechanisms to ensure security without compromising the microservices' independence and scalability.