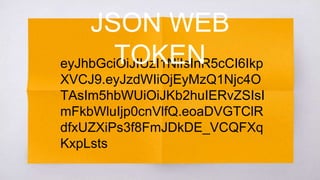
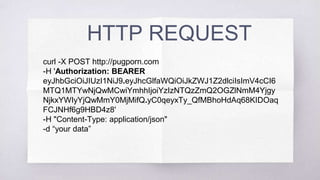
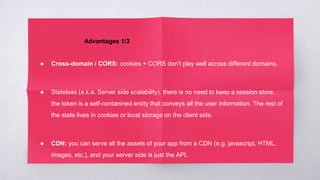
JWT (JSON Web Token) is a standard used to securely transmit information between parties as a JSON object. It allows servers to verify transmitted information without storing state on the server, making it more scalable. JWTs provide authentication and authorization by encoding claims about an entity (such as an user) including an ID, expiration time, and other data inside the token itself.