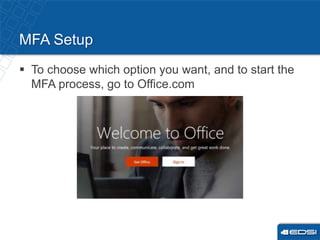
This document discusses multi-factor authentication (MFA) and provides instructions for setting it up. It explains that MFA adds an extra layer of security to protect accounts. The company is enabling MFA on November 8th and all employees must set it up starting that day. Employees will receive a calendar invite with details. There are two main methods for MFA - receiving a text message or using the Microsoft Authenticator app. To set up MFA, employees should go to Office.com and choose their preferred method. After setup, MFA will affect Microsoft Outlook, Skype and mobile email access, potentially requiring reconnection. Managers are asked to prepare their teams and direct them to tutorials for help with the transition.