A Guide to Multi Factor Authentication
•
0 likes•100 views
Check out this infographic to learn all about multi factor authentication or MFA.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Simplify Security And Device Management Final Pres10 23final

Simplify Security And Device Management Final Pres10 23final
Best Practices for Multi-Factor Authentication on IBM i

Best Practices for Multi-Factor Authentication on IBM i
Joomla web application development vulnerabilities

Joomla web application development vulnerabilities
Avoiding Two-factor Authentication? You're Not Alone

Avoiding Two-factor Authentication? You're Not Alone
Combat Passwords on Post-Its with Multi-Factor Authentication for IBM i

Combat Passwords on Post-Its with Multi-Factor Authentication for IBM i
3 reasons your business can't ignore Two-Factor Authentication

3 reasons your business can't ignore Two-Factor Authentication
Similar to A Guide to Multi Factor Authentication
Similar to A Guide to Multi Factor Authentication (20)
What, Exactly, is Multi-Factor Authentication, and How To Use It?

What, Exactly, is Multi-Factor Authentication, and How To Use It?
Multi_Factor_Authentication_against_Data_Theft_PPTDark_Blue_Brown.pdf

Multi_Factor_Authentication_against_Data_Theft_PPTDark_Blue_Brown.pdf
Multi Factor Authentication Whitepaper Arx - Intellect Design

Multi Factor Authentication Whitepaper Arx - Intellect Design
Role Of Two Factor Authentication In Safeguarding Online Transactions

Role Of Two Factor Authentication In Safeguarding Online Transactions
Boosting Customer Engagement with Transactional SMS API: A Complete Guide

Boosting Customer Engagement with Transactional SMS API: A Complete Guide
What All You Need To Know About Multi-Factor Authentication & IVR in Banking!

What All You Need To Know About Multi-Factor Authentication & IVR in Banking!
Android Based Total Security for System Authentication

Android Based Total Security for System Authentication
Three Step Multifactor Authentication Systems for Modern Security

Three Step Multifactor Authentication Systems for Modern Security
More from Jack Forbes
More from Jack Forbes (20)
Authentication and Authorization Defined_ What's the Difference_.pdf

Authentication and Authorization Defined_ What's the Difference_.pdf
Digital identity management for the cmo, ciso, and cio

Digital identity management for the cmo, ciso, and cio
8 effective communication strategies for internal alignment and growth in 2021

8 effective communication strategies for internal alignment and growth in 2021
Recently uploaded
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
A Guide to Multi Factor Authentication
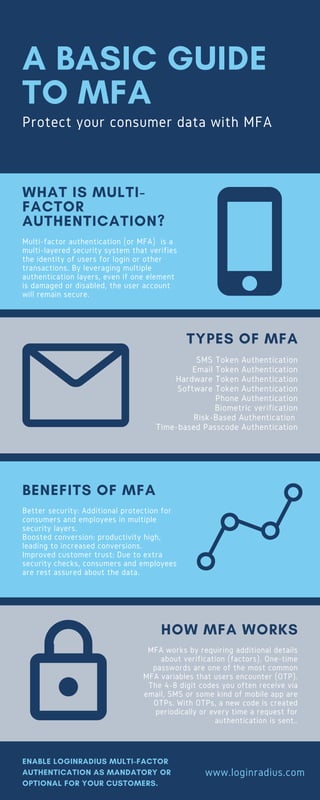
- 1. A BASIC GUIDE TO MFA Protect your consumer data with MFA SMS Token Authentication Email Token Authentication Hardware Token Authentication Software Token Authentication Phone Authentication Biometric verification Risk-Based Authentication Time-based Passcode Authentication TYPES OF MFA Better security: Additional protection for consumers and employees in multiple security layers. Boosted conversion: productivity high, leading to increased conversions. Improved customer trust: Due to extra security checks, consumers and employees are rest assured about the data. BENEFITS OF MFA Multi-factor authentication (or MFA) is a multi-layered security system that verifies the identity of users for login or other transactions. By leveraging multiple authentication layers, even if one element is damaged or disabled, the user account will remain secure. WHAT IS MULTI- FACTOR AUTHENTICATION? MFA works by requiring additional details about verification (factors). One-time passwords are one of the most common MFA variables that users encounter (OTP). The 4-8 digit codes you often receive via email, SMS or some kind of mobile app are OTPs. With OTPs, a new code is created periodically or every time a request for authentication is sent.. HOW MFA WORKS www.loginradius.com ENABLE LOGINRADIUS MULTI-FACTOR AUTHENTICATION AS MANDATORY OR OPTIONAL FOR YOUR CUSTOMERS.
