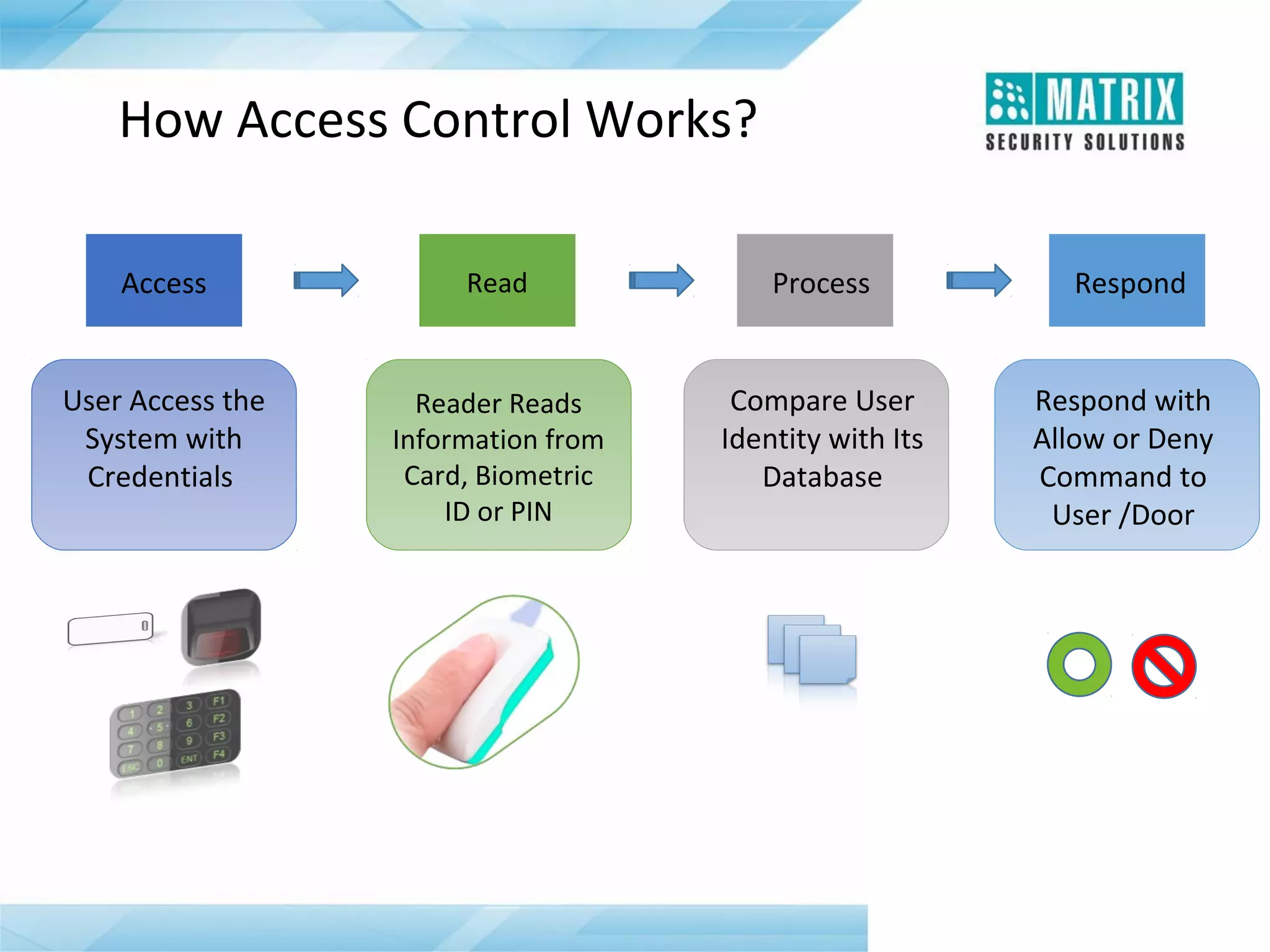
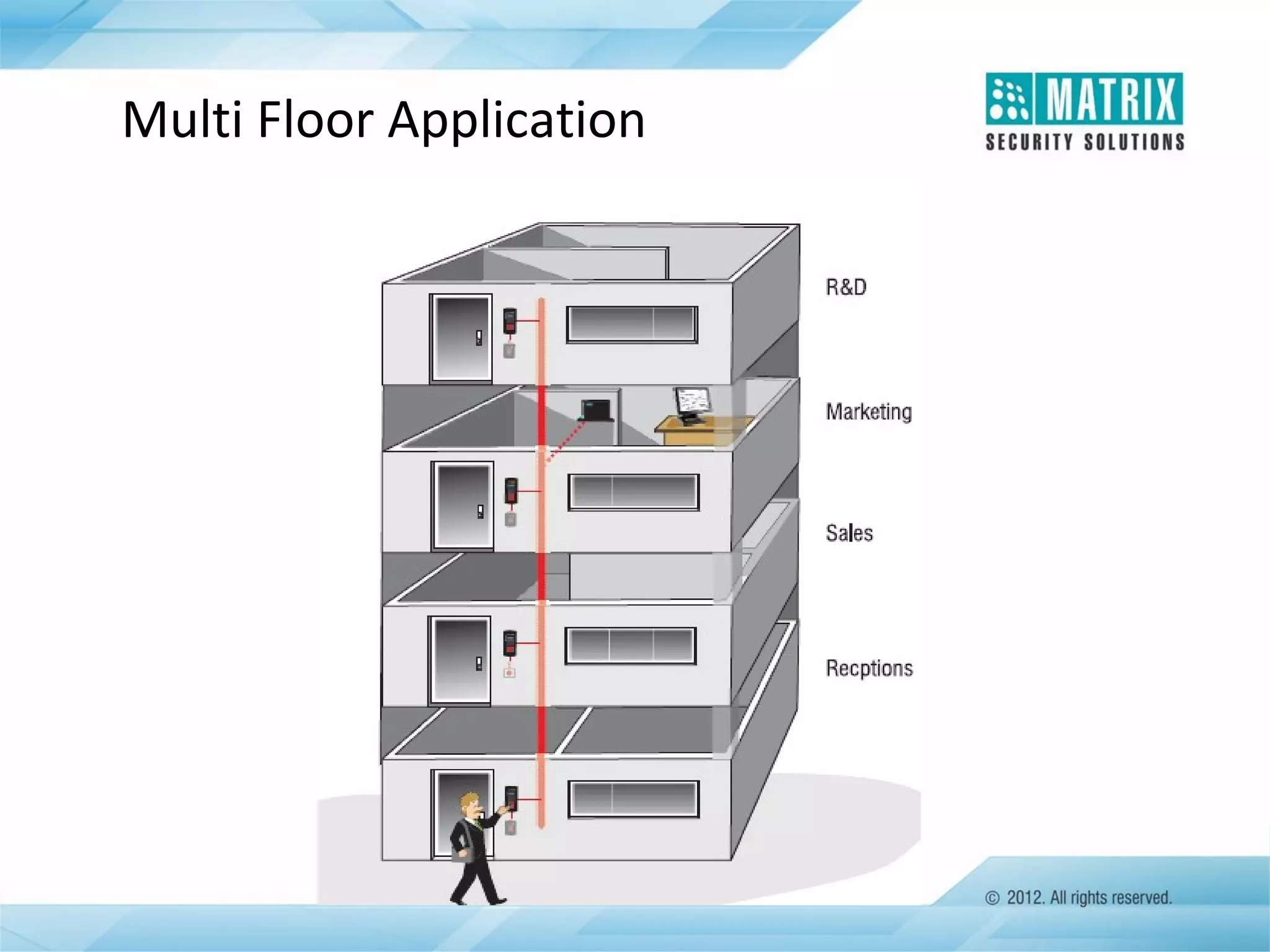
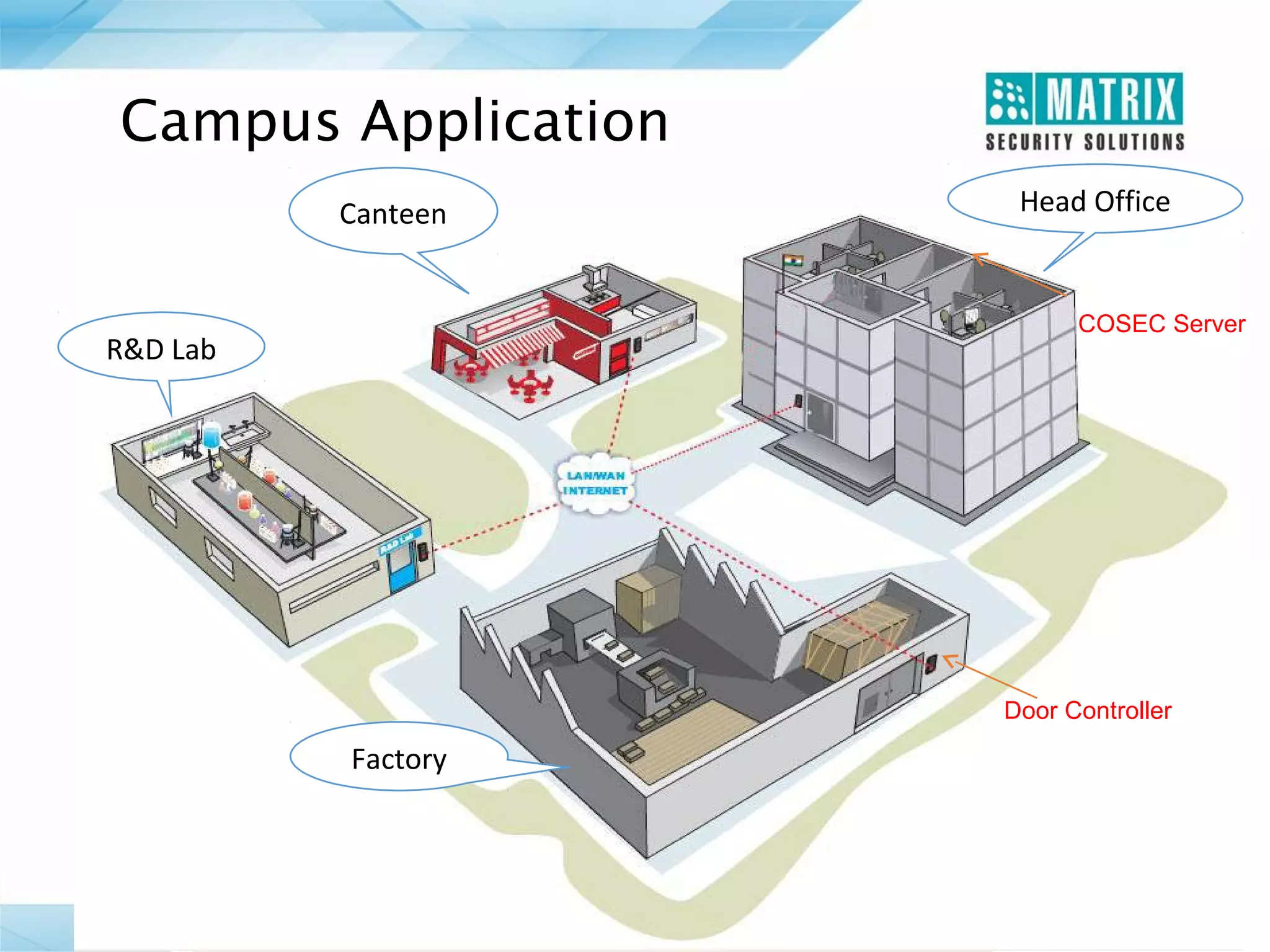
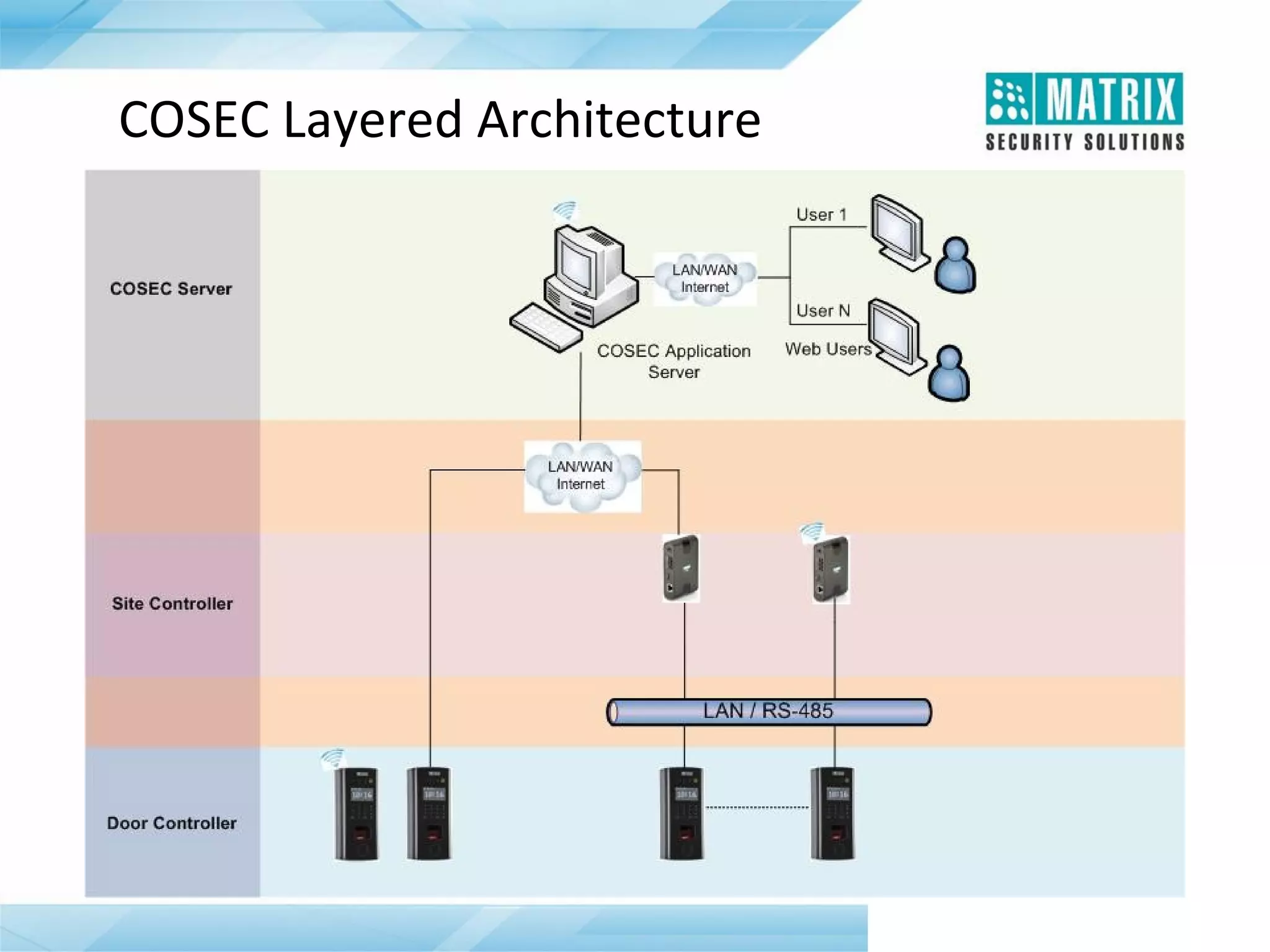
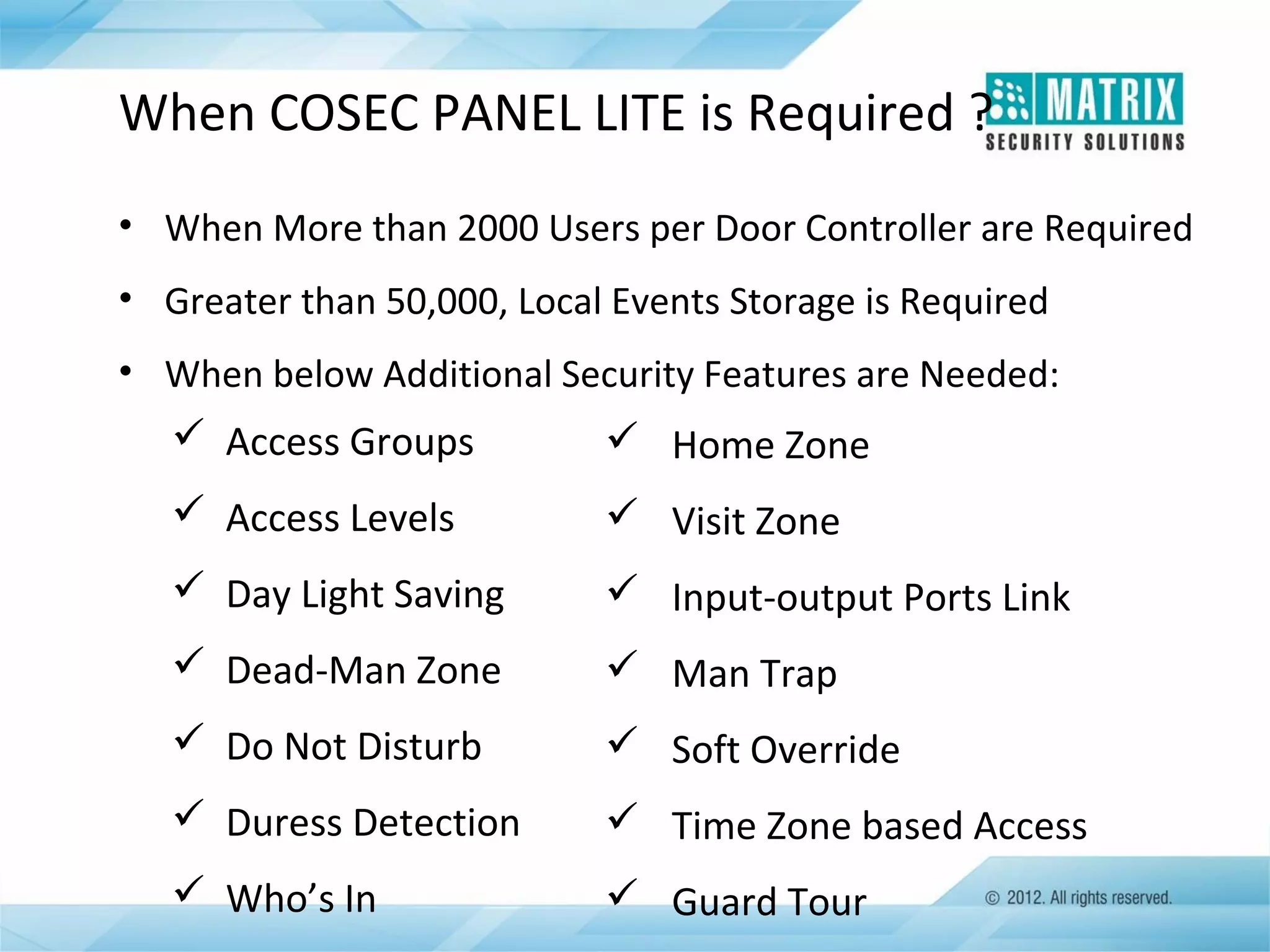
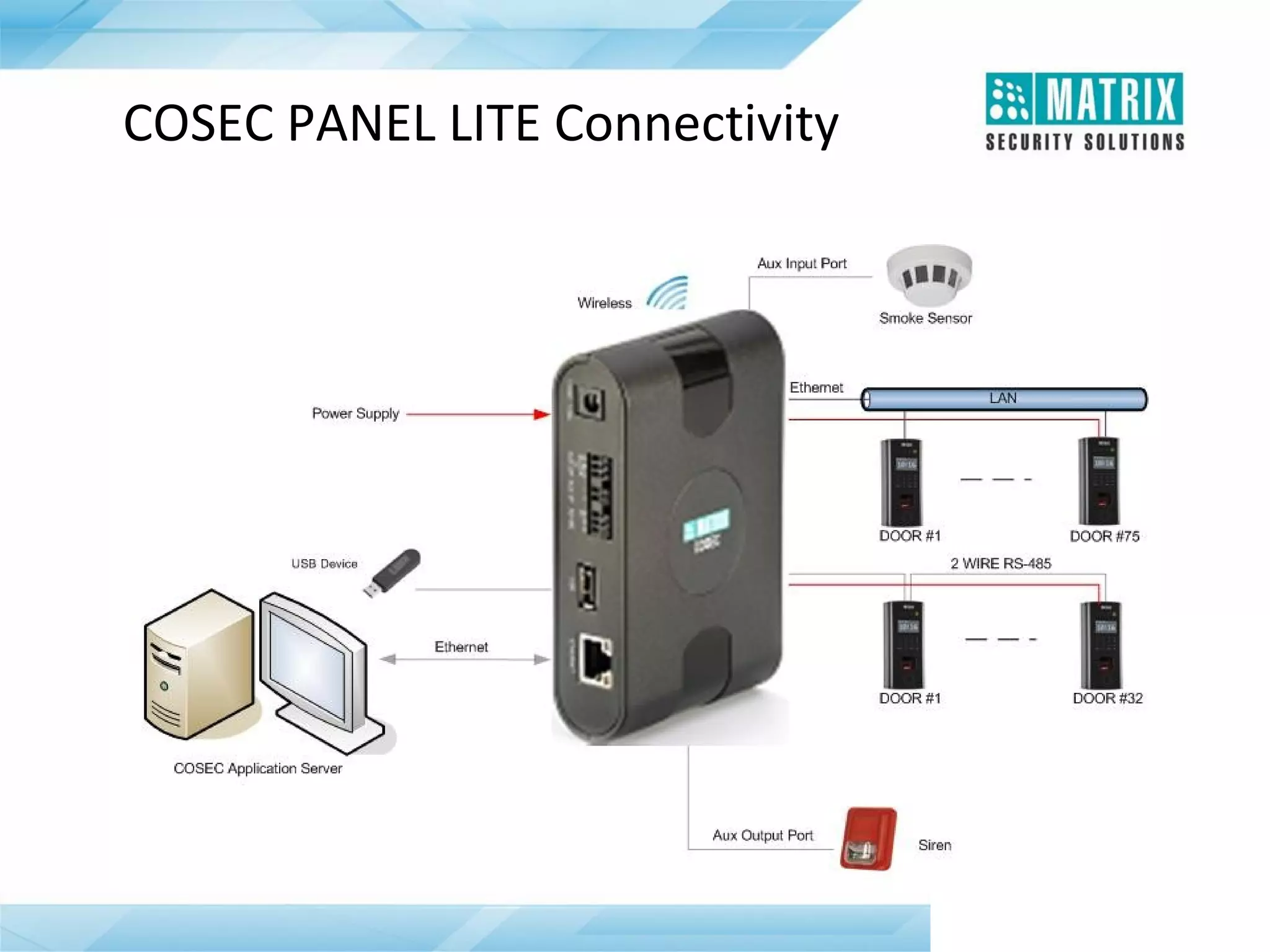
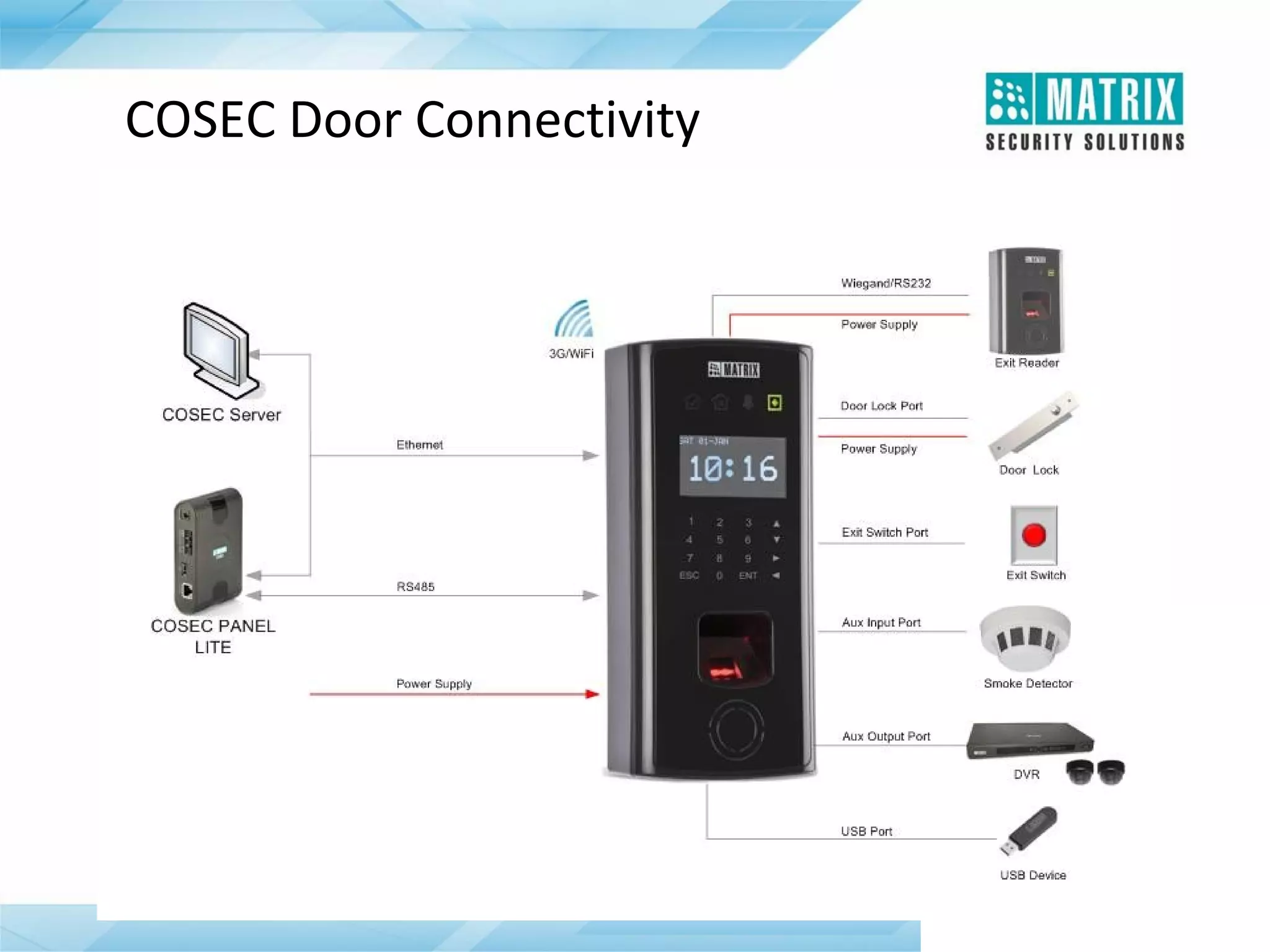
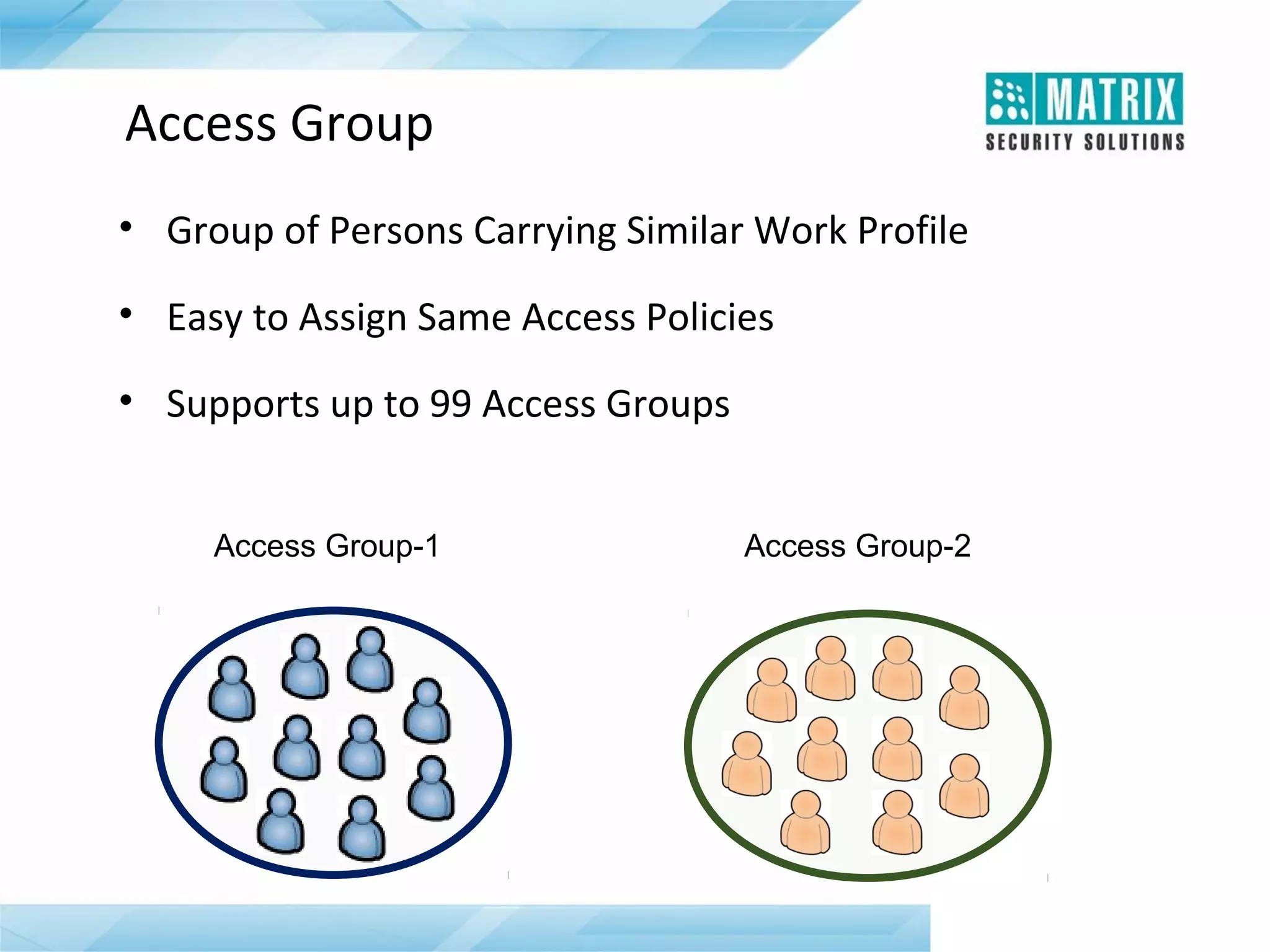
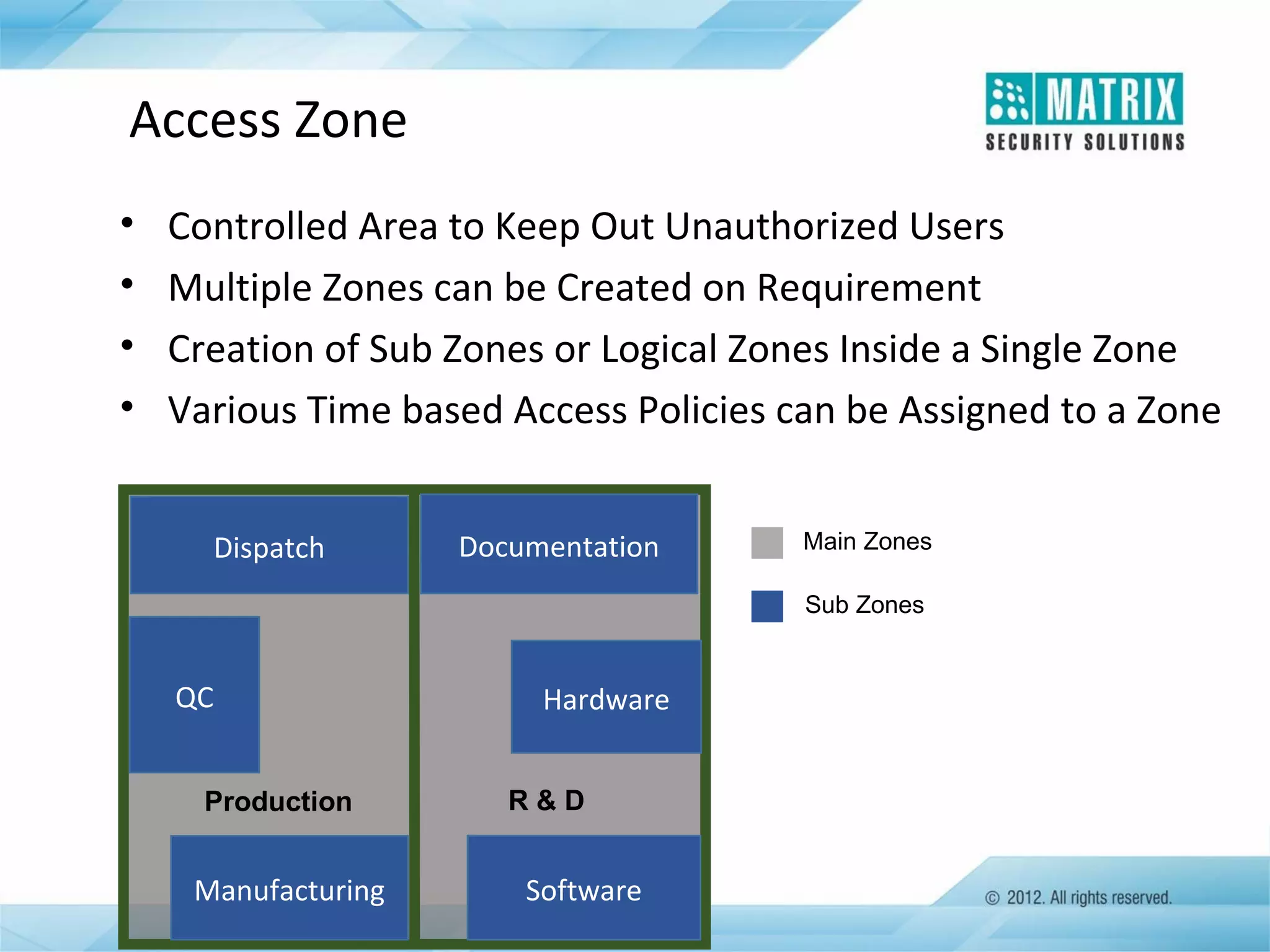
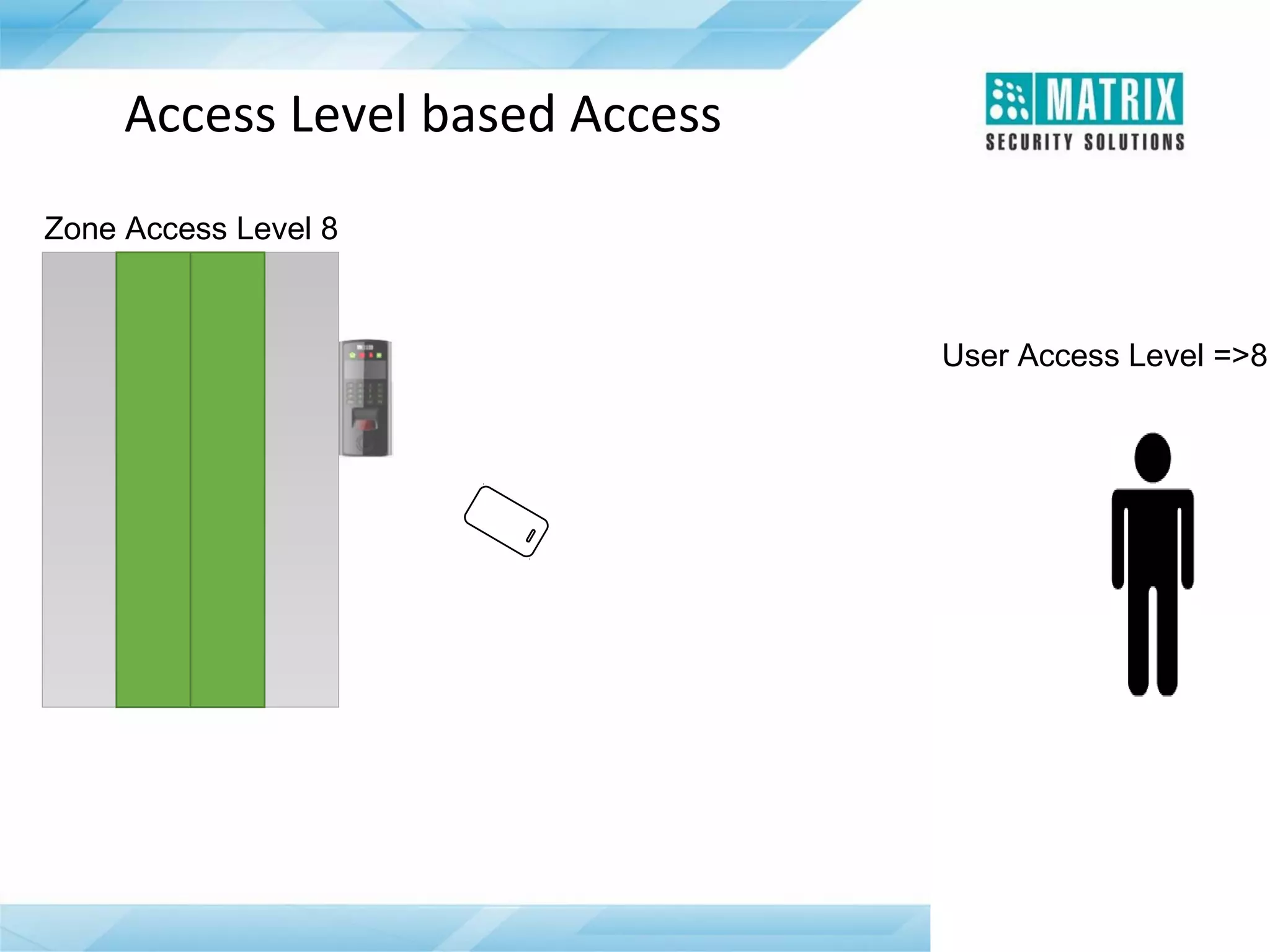
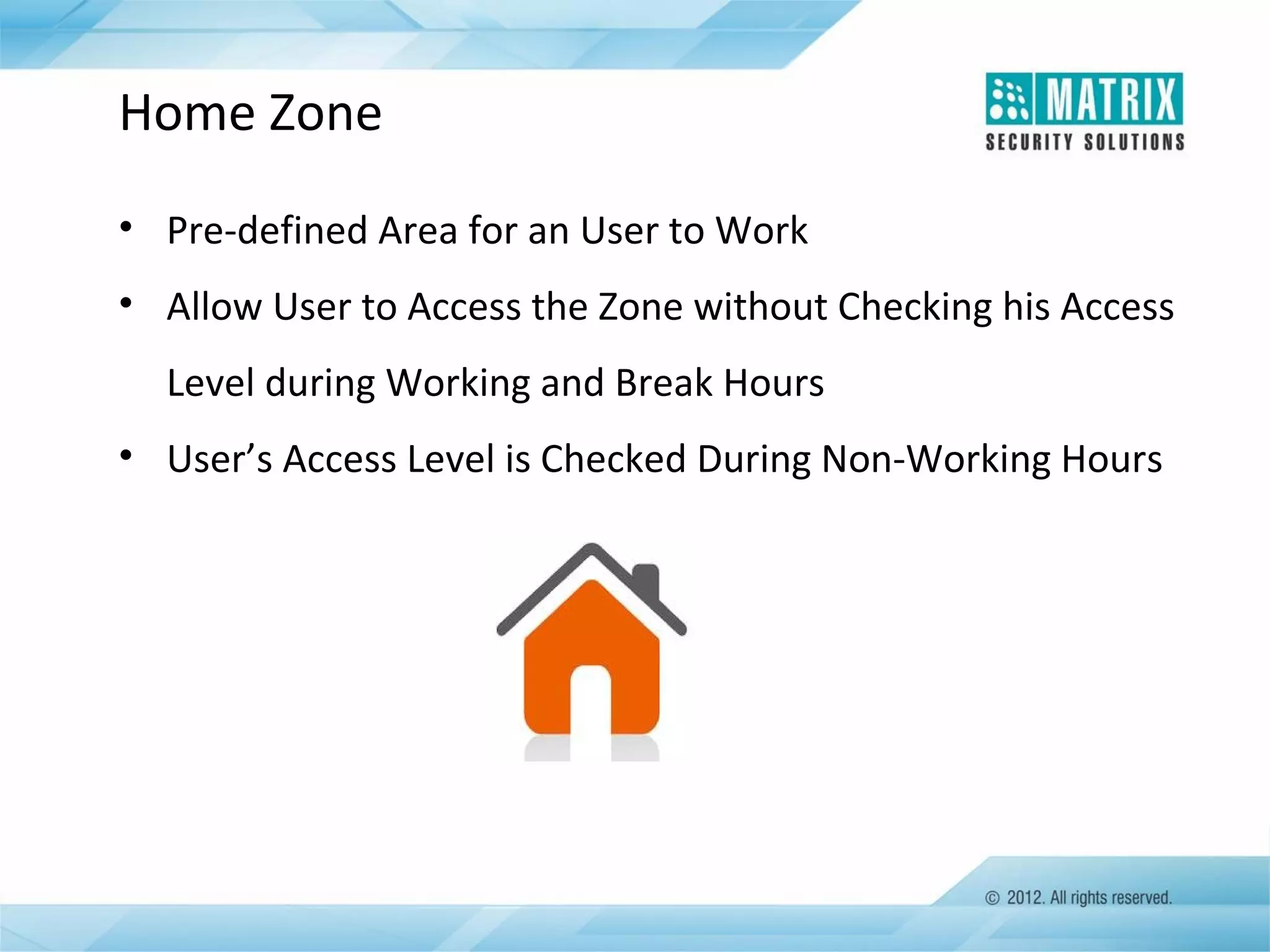
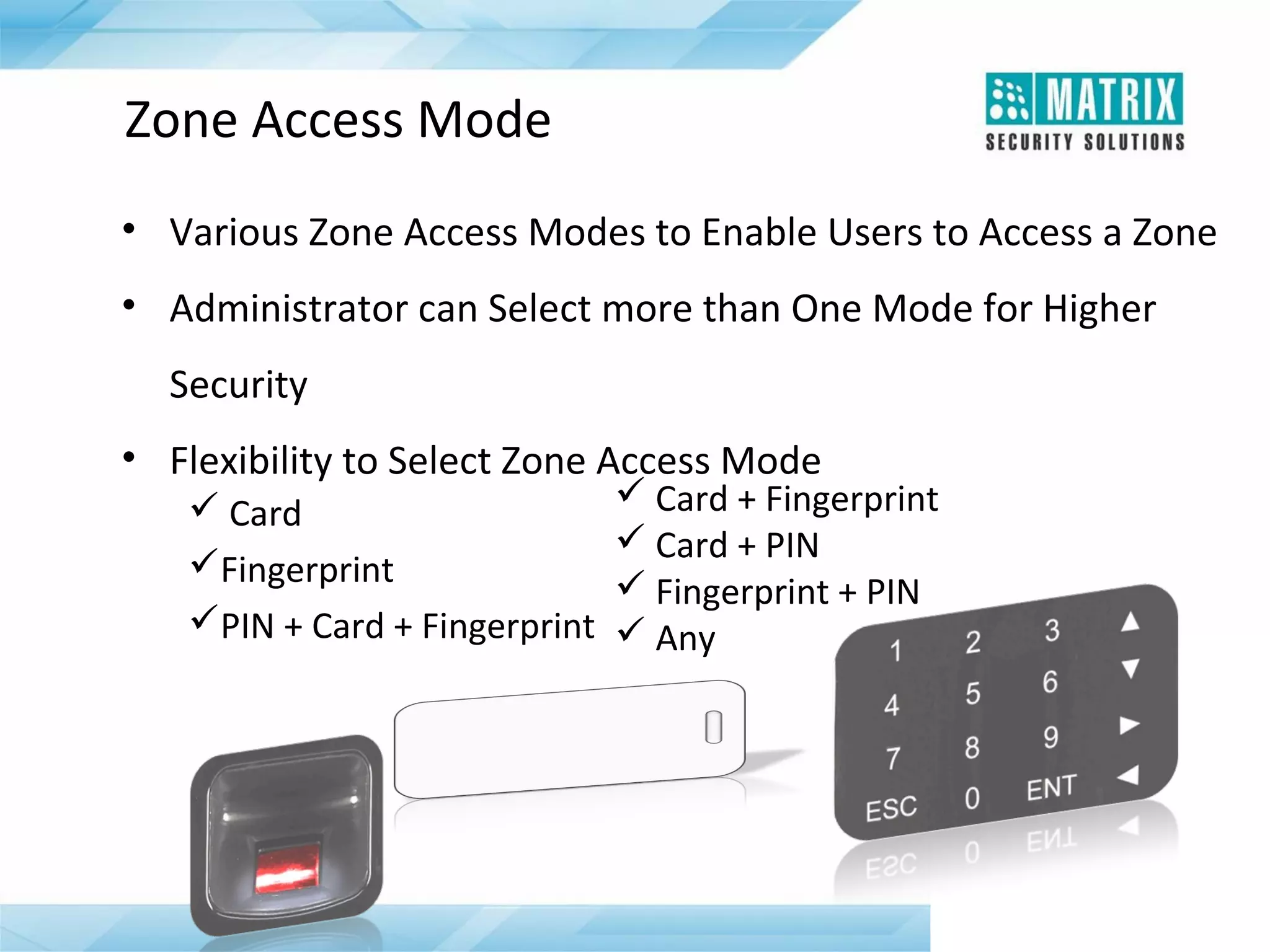
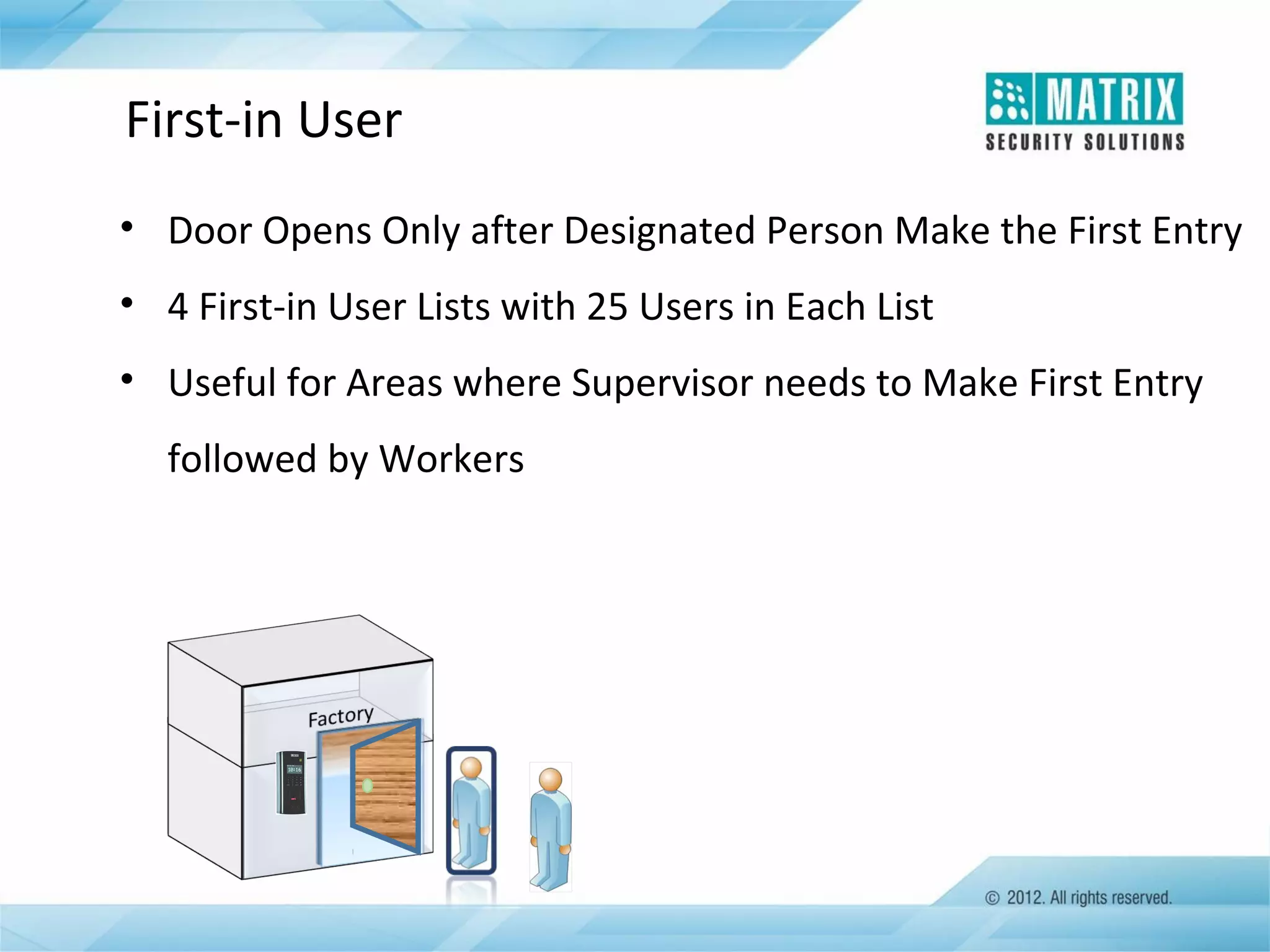
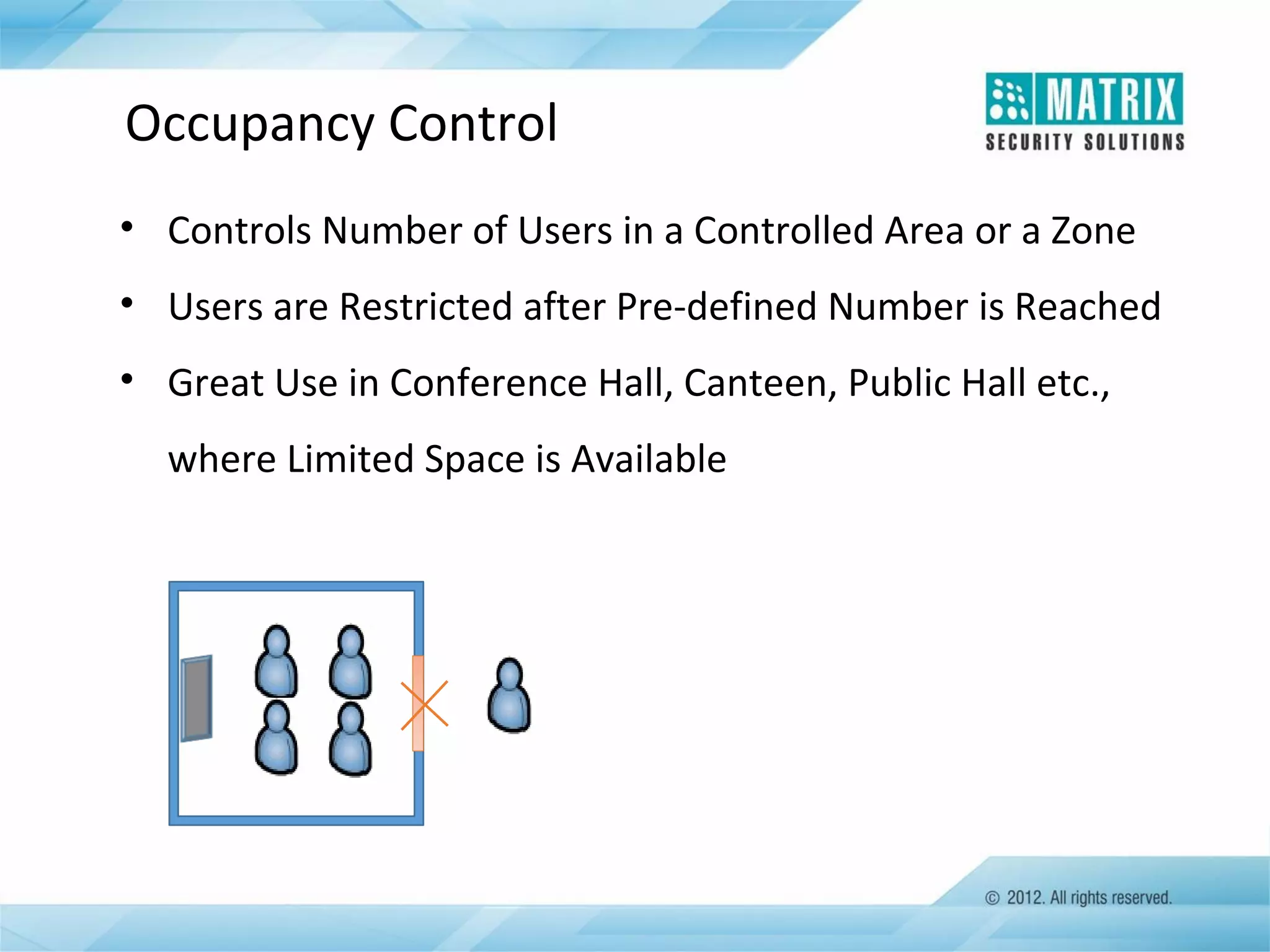
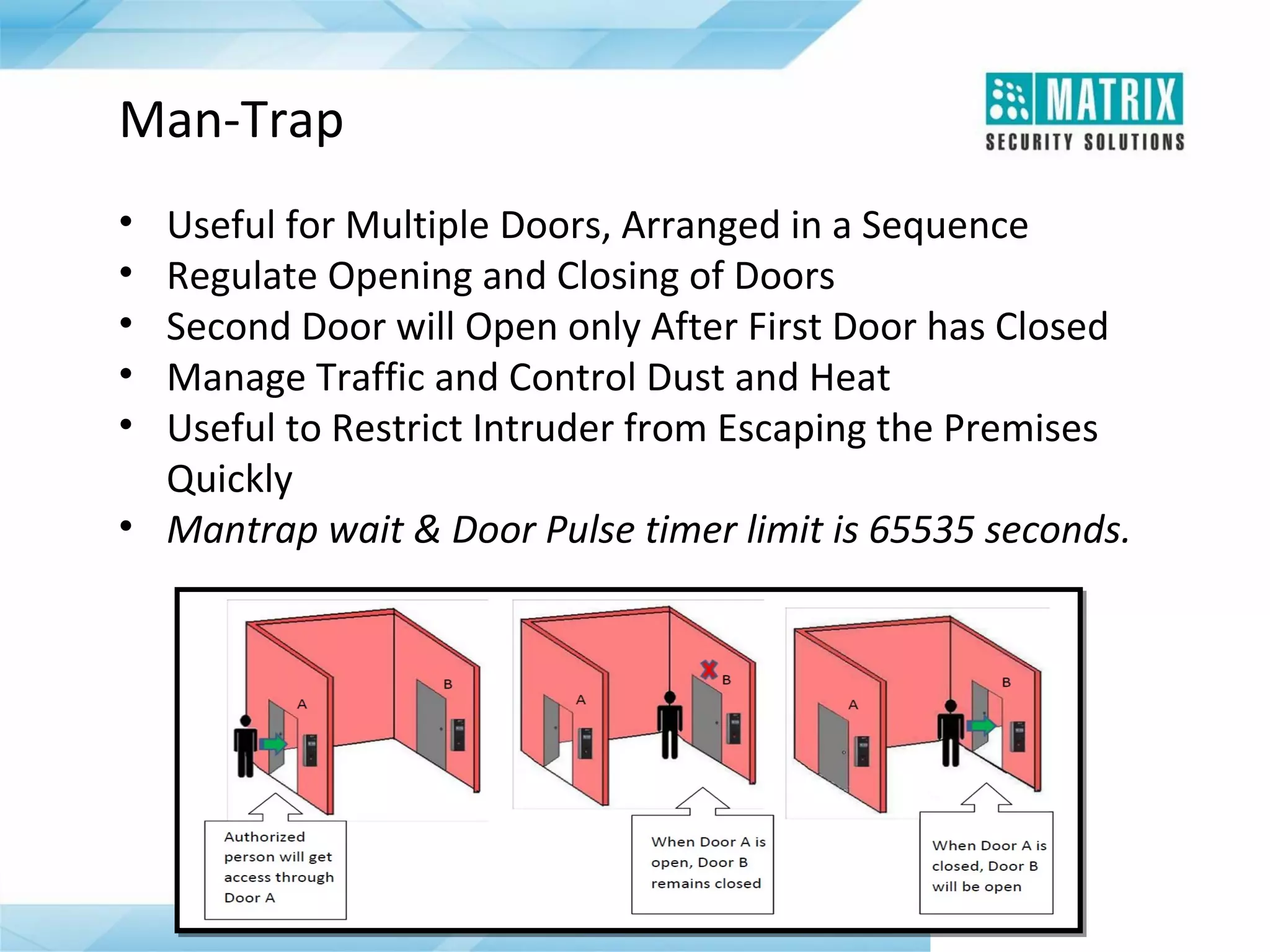
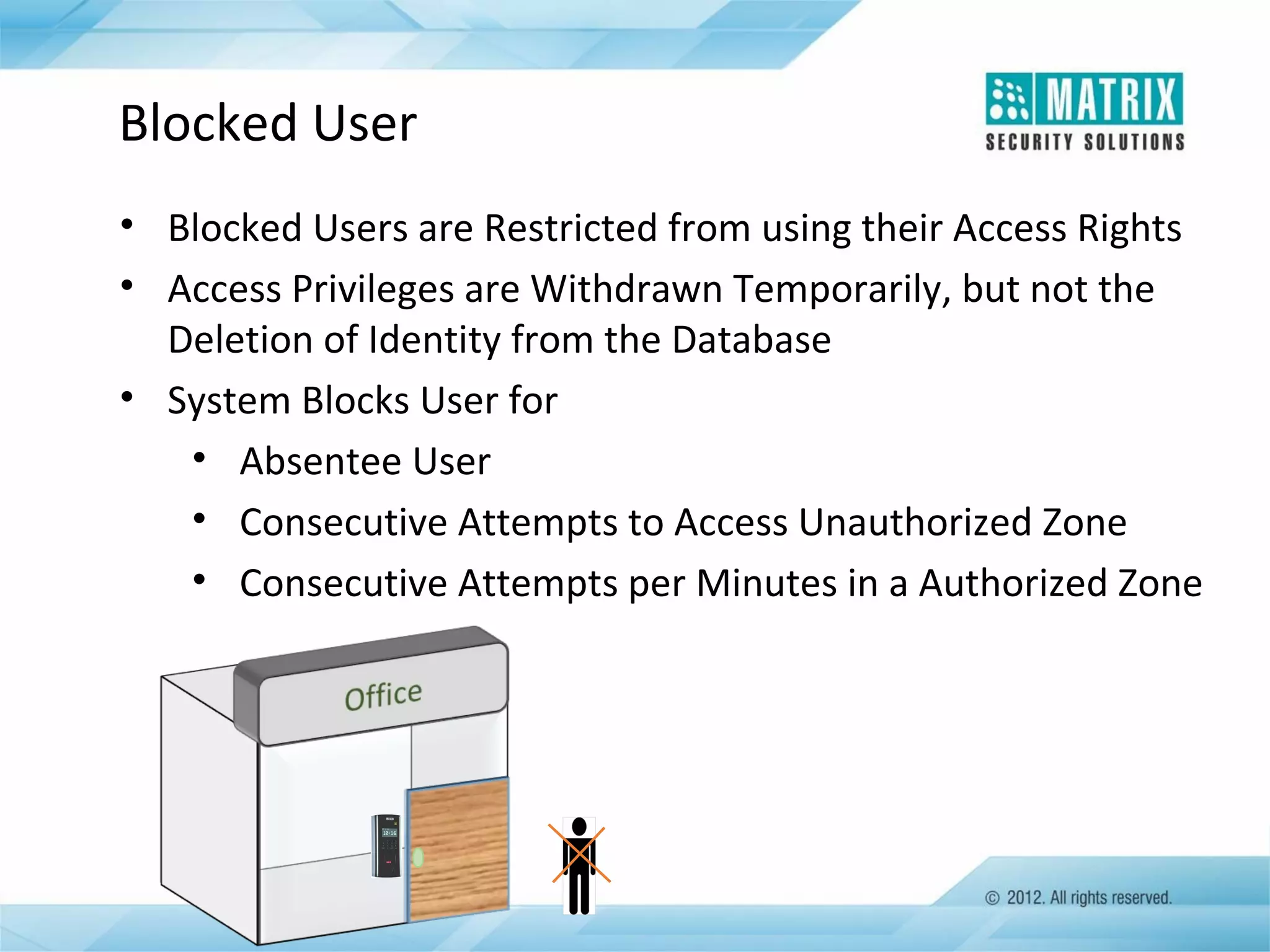
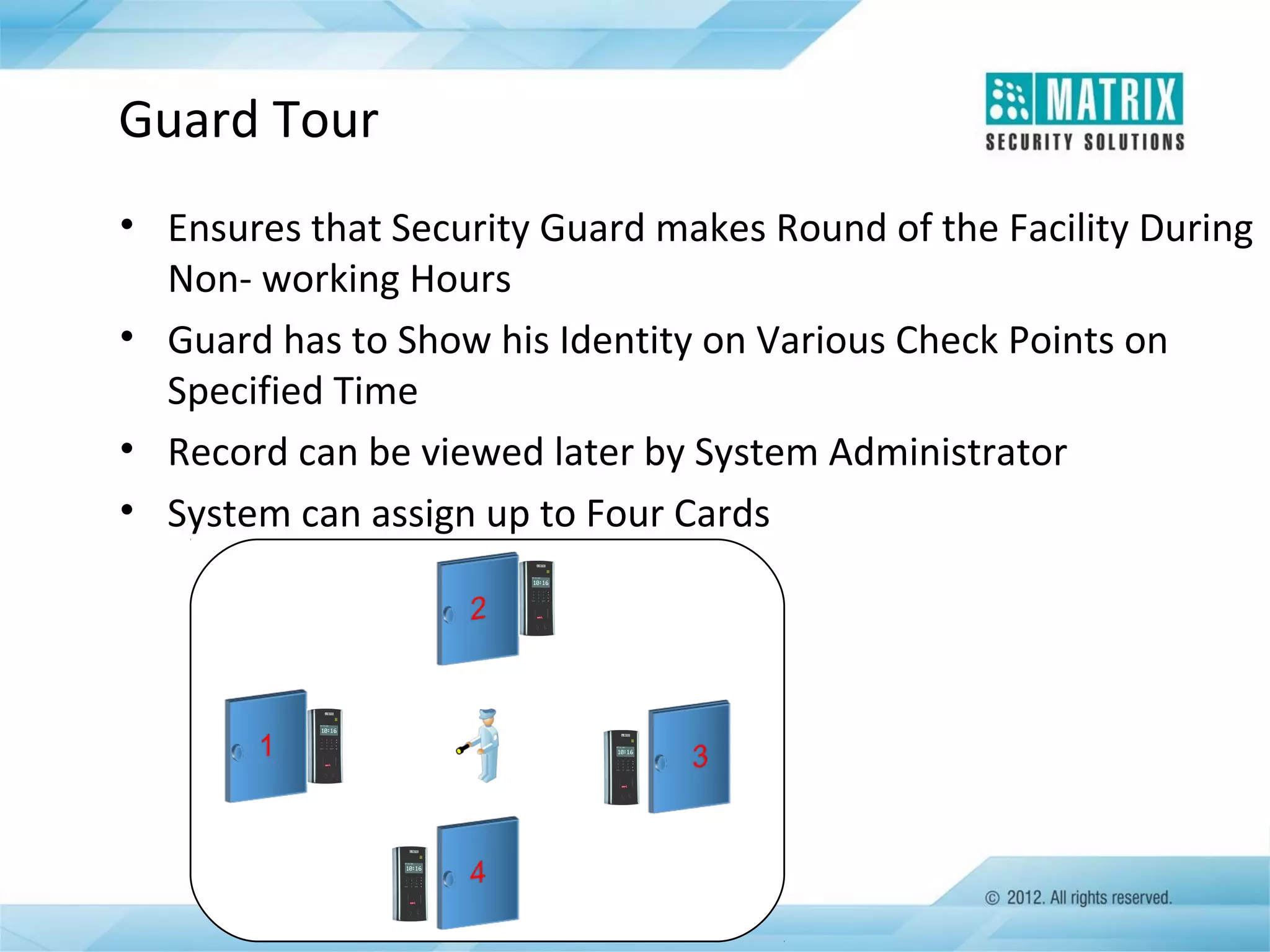
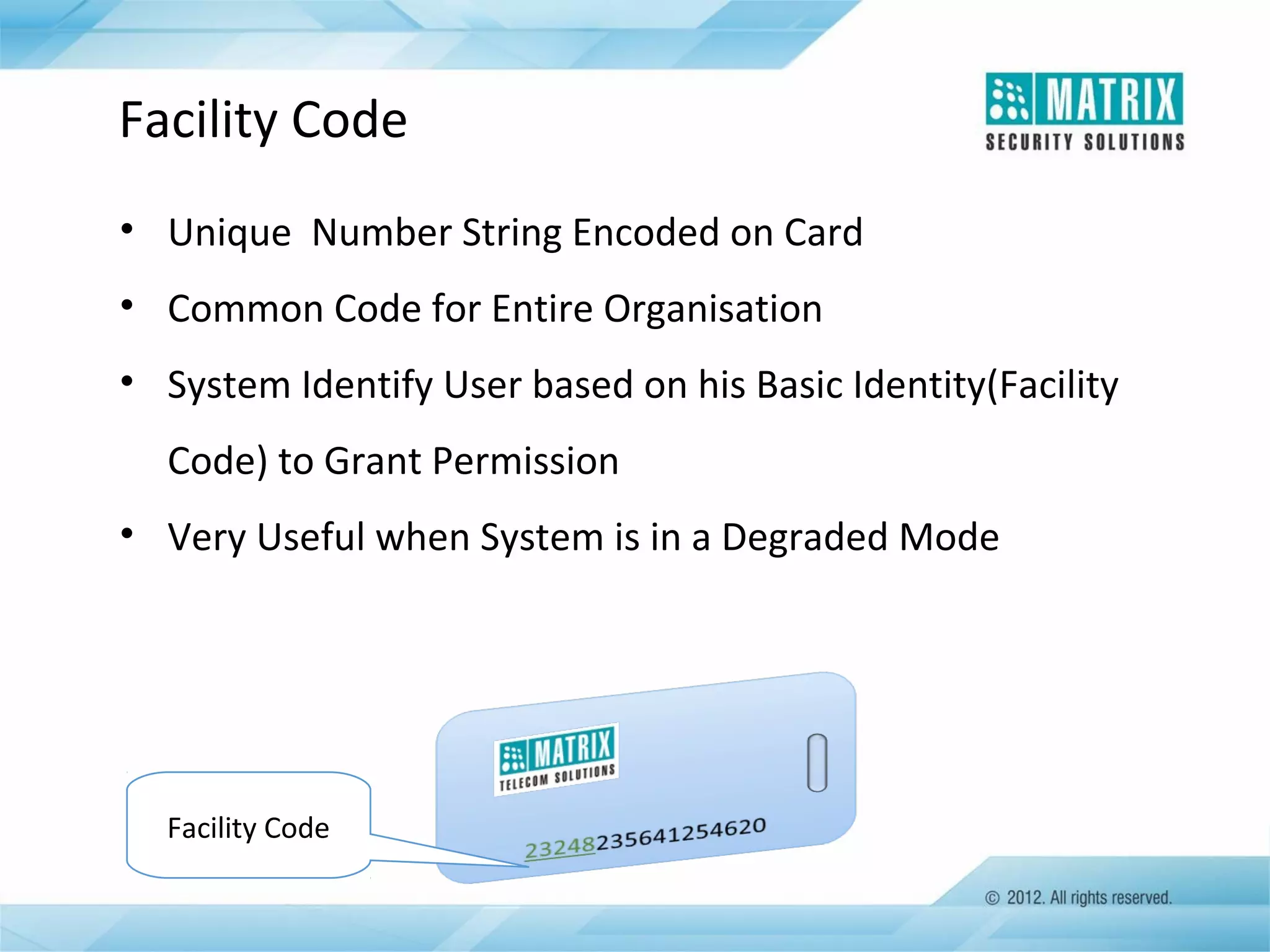
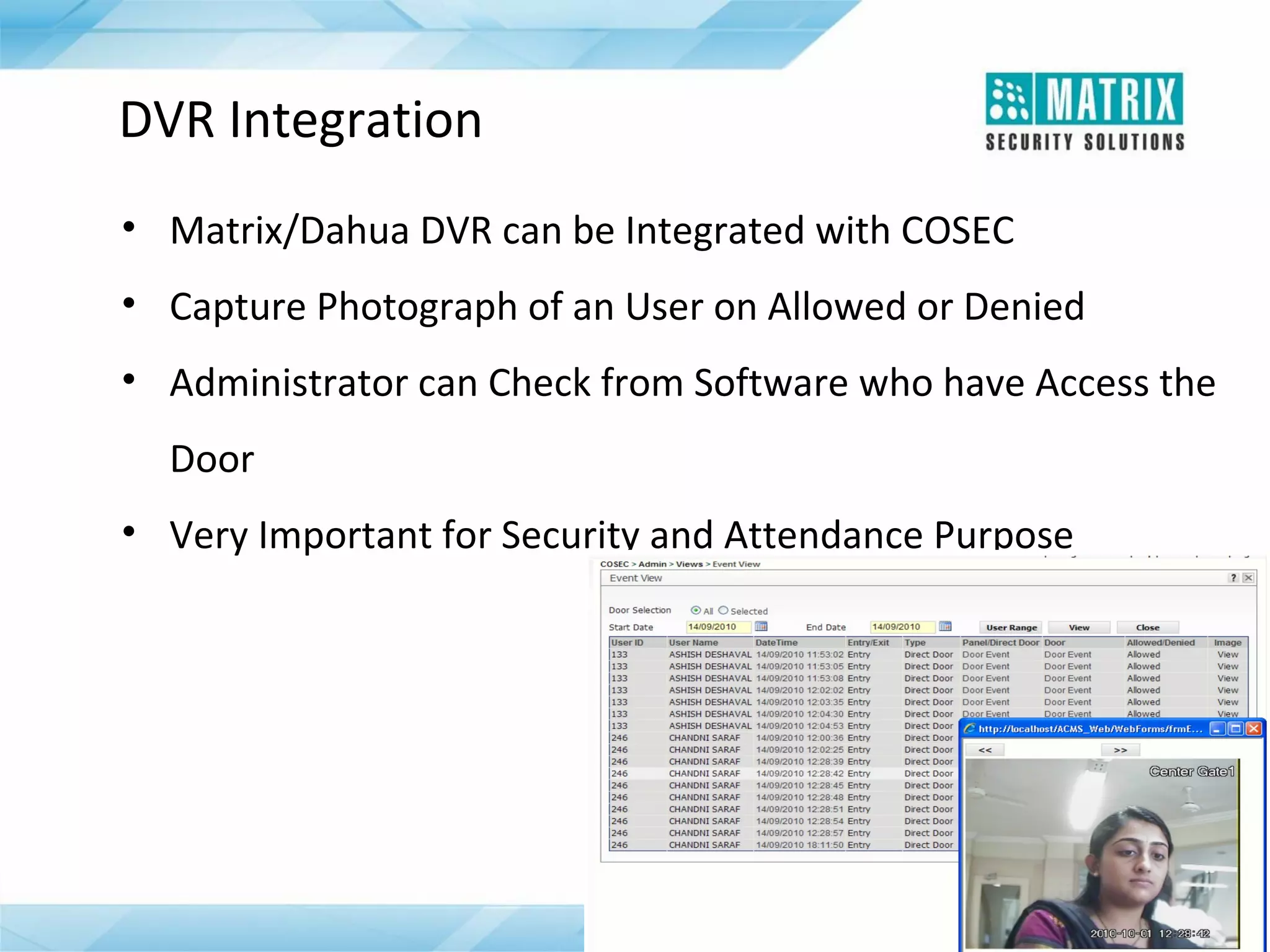
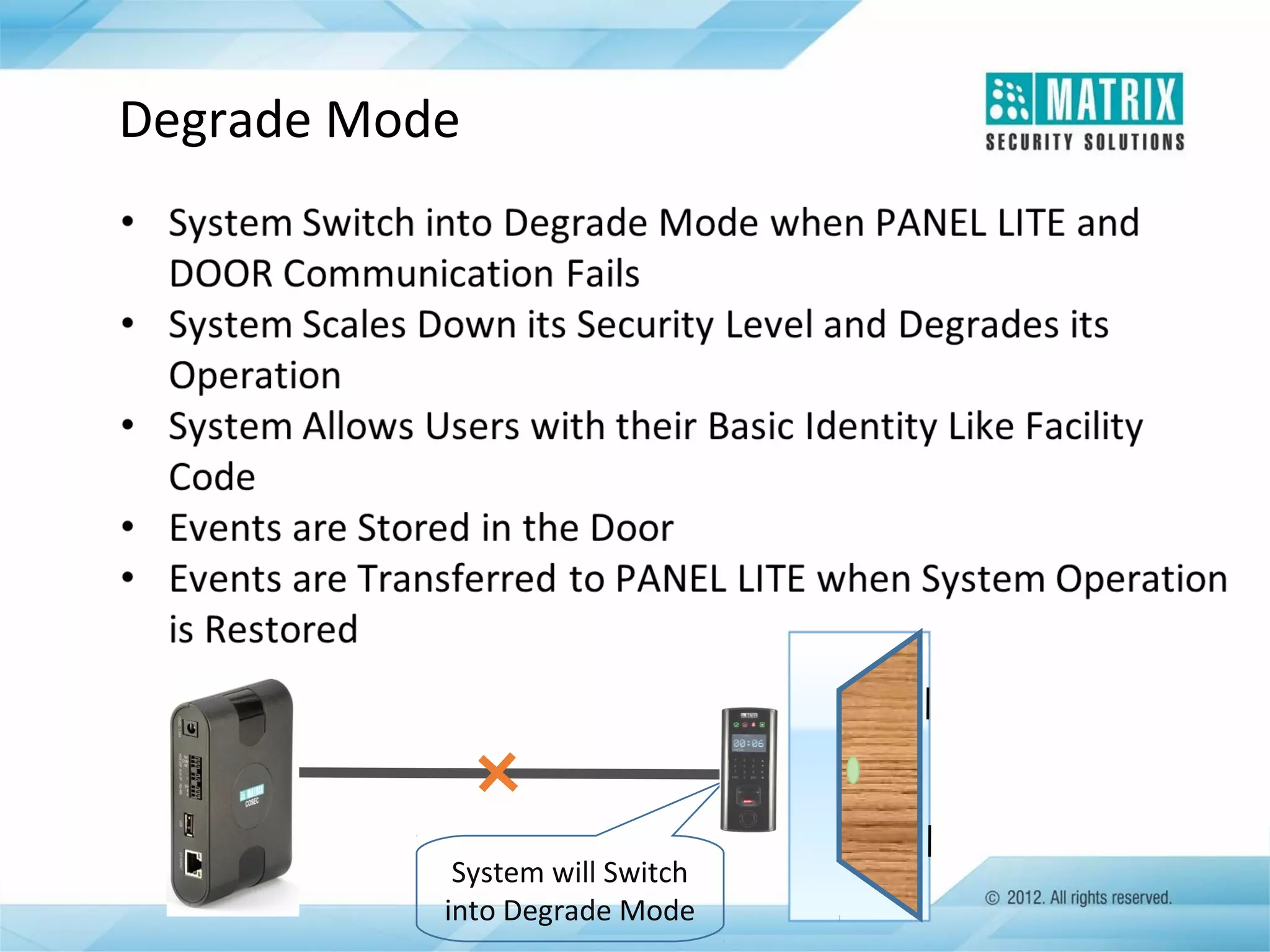
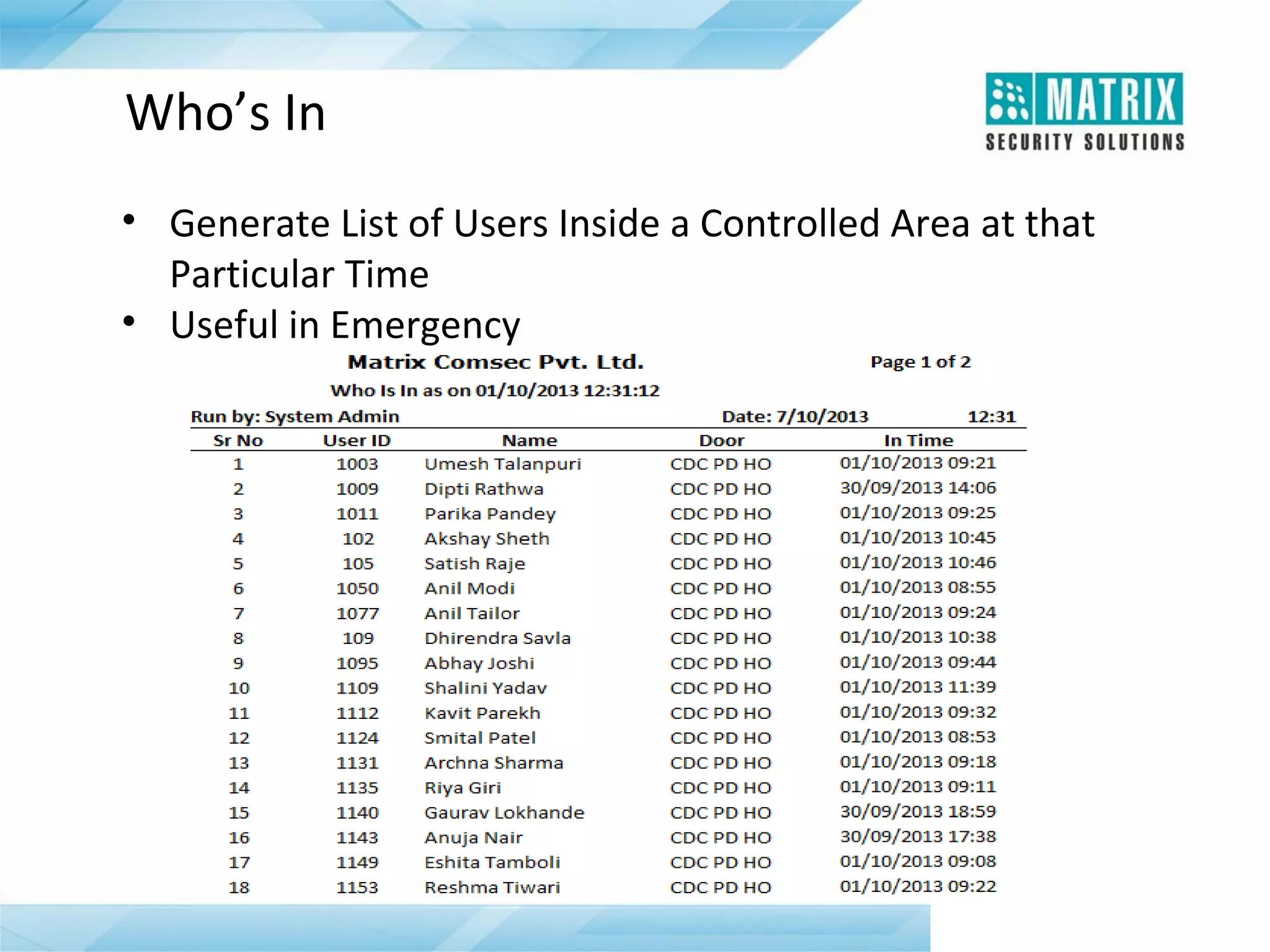
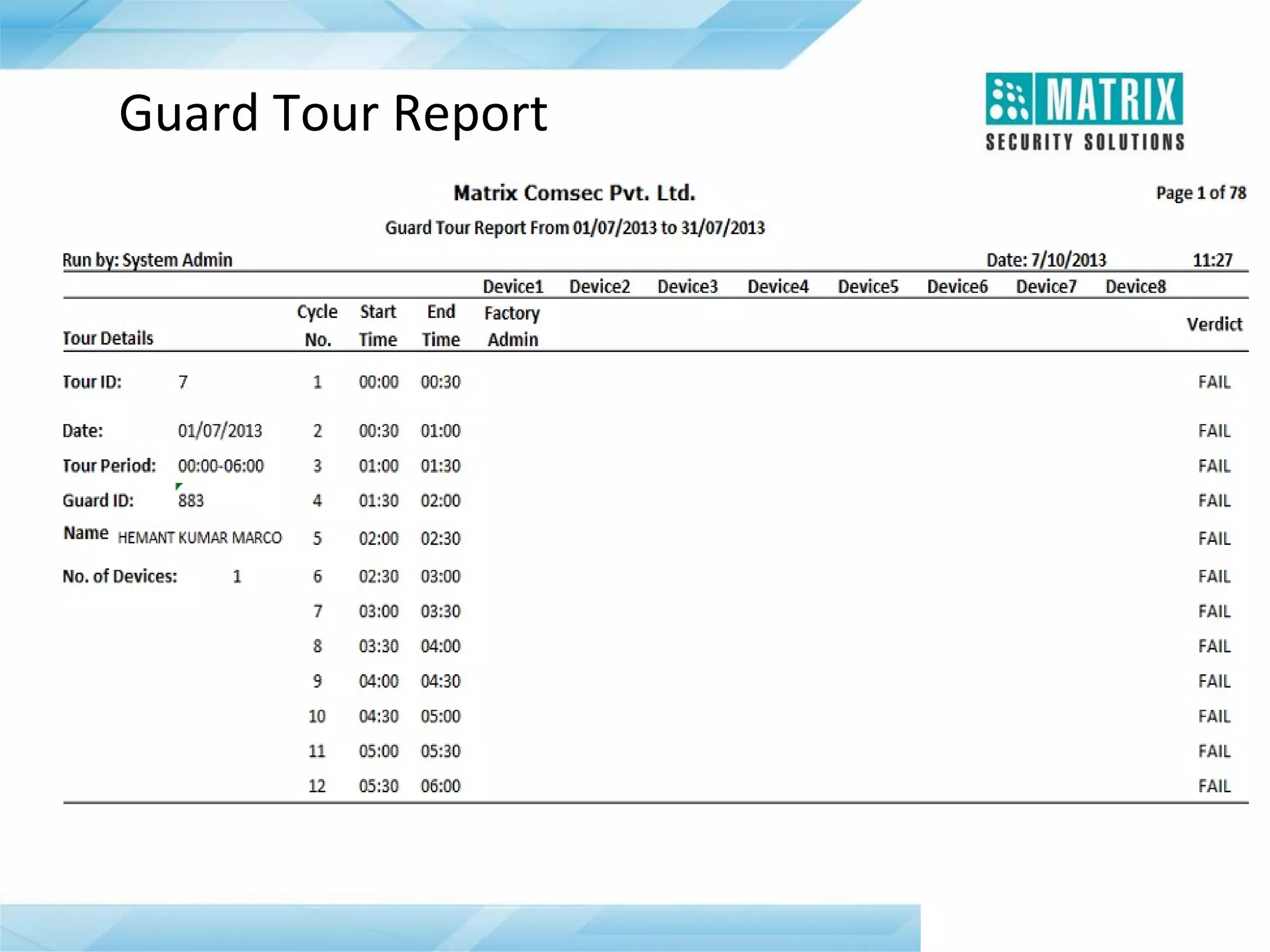
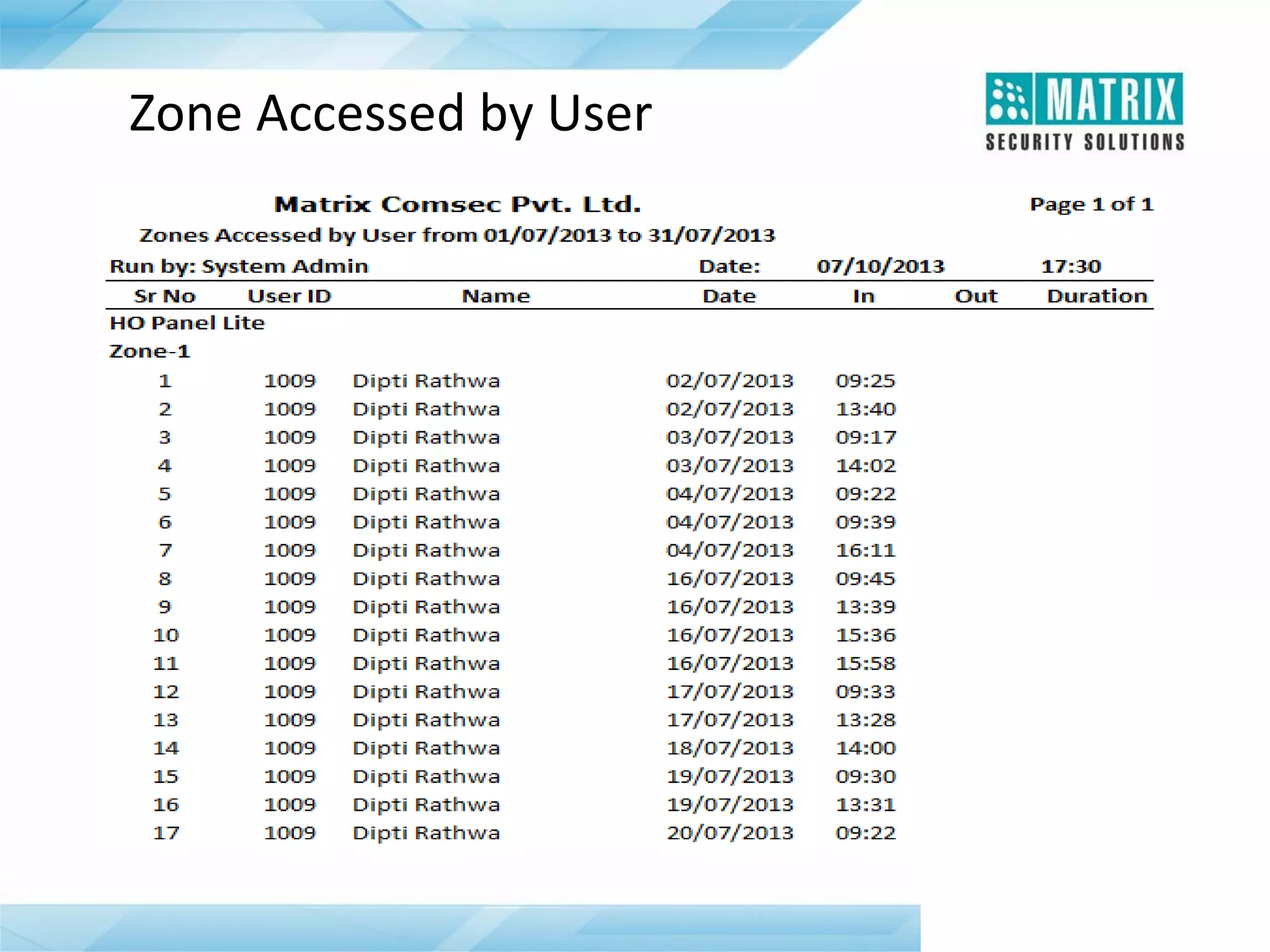
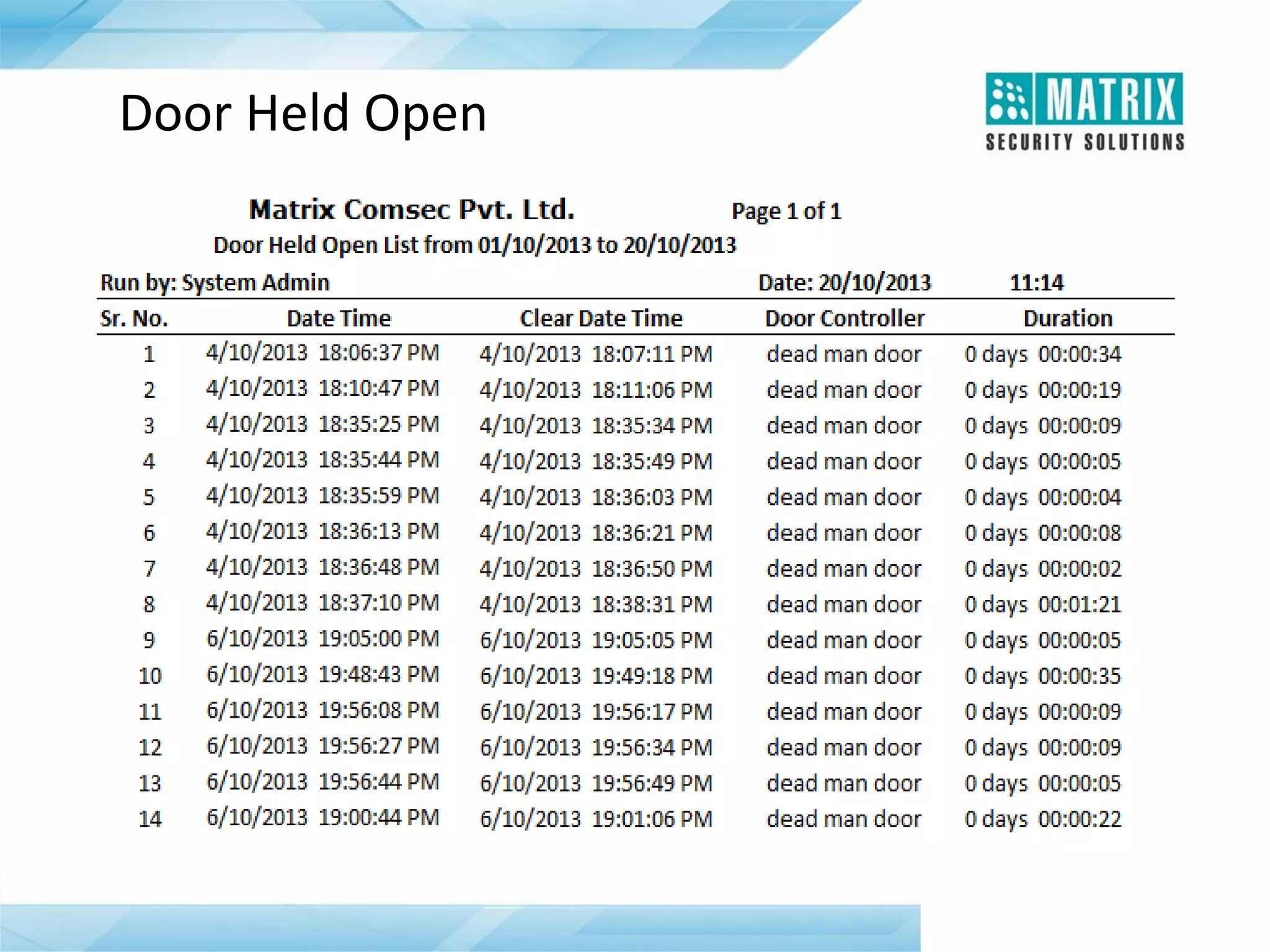
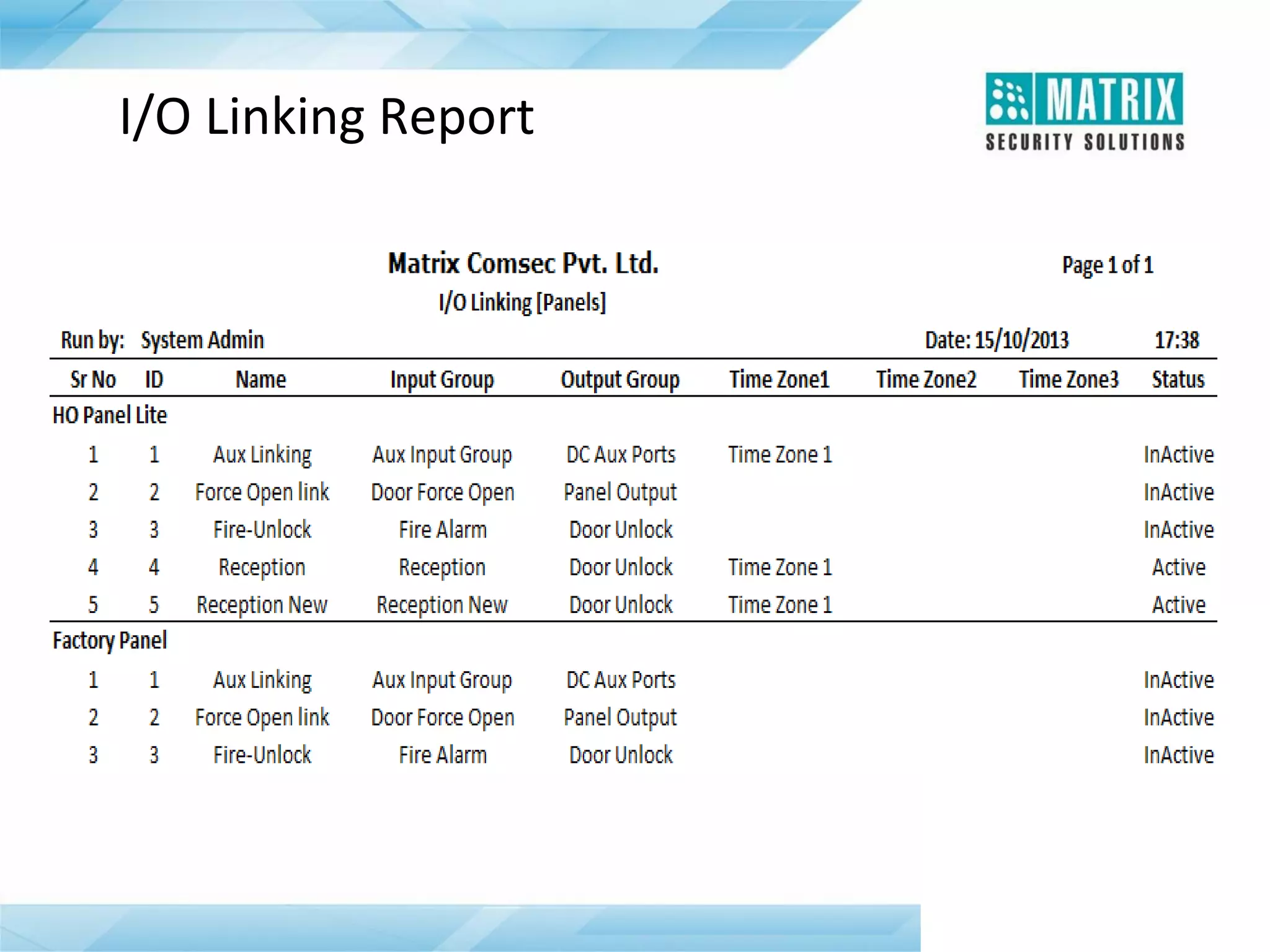
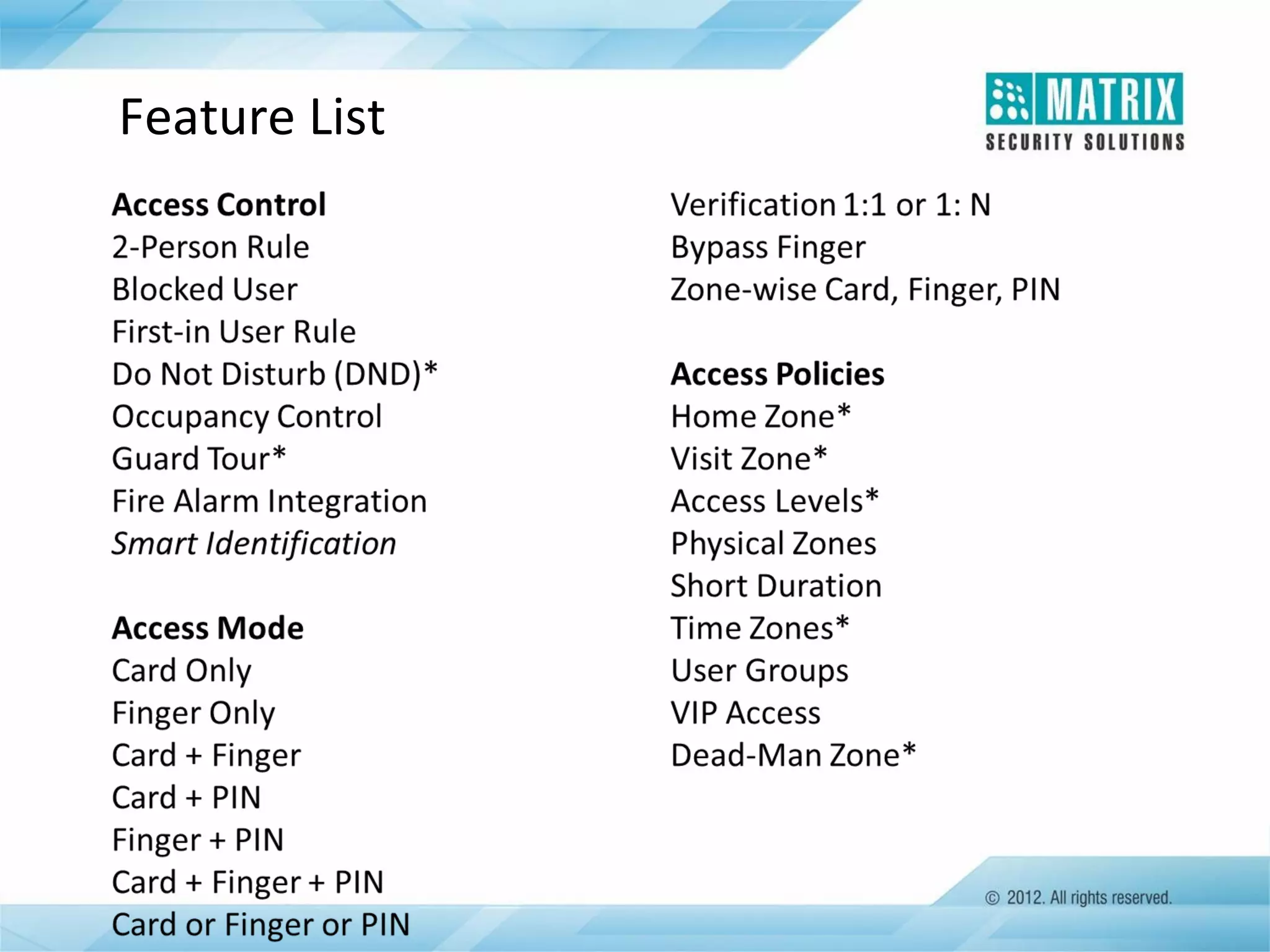
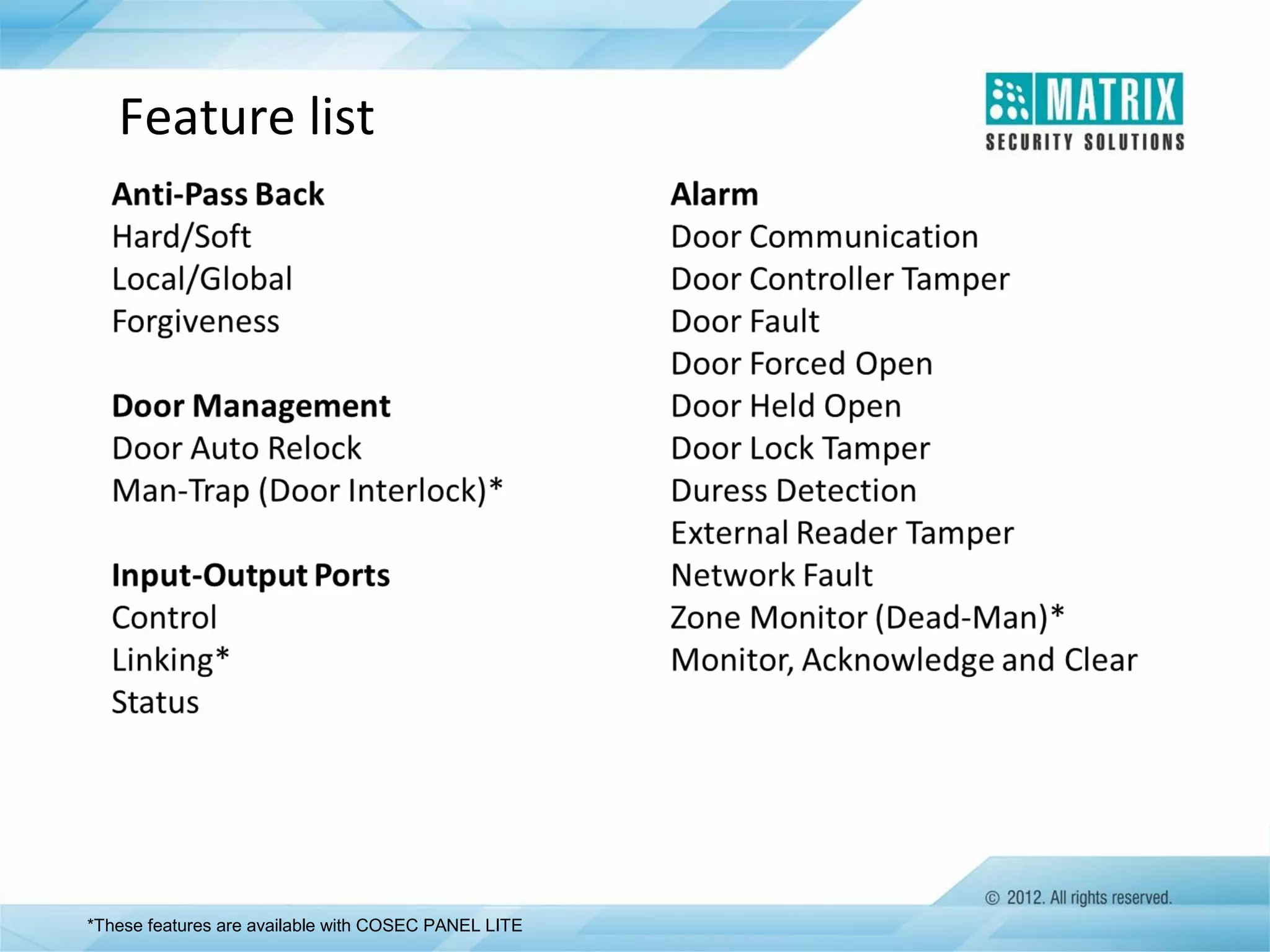
The document outlines the features and functionalities of the COSEC access control system, designed to enhance security by managing user access through various methods such as biometrics, cards, and PINs. It details the system's architecture, target customers, and numerous applications, as well as advanced features like emergency handling, monitoring, and integration with other security systems. Additionally, it covers the benefits of the COSEC system, including enhanced security, reduced personnel costs, and comprehensive reporting capabilities.