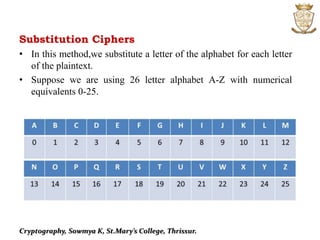
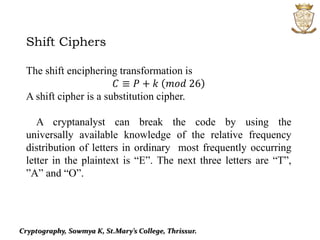
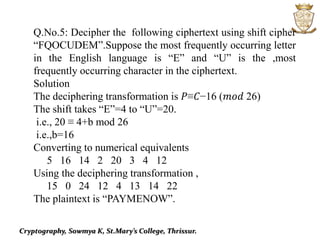
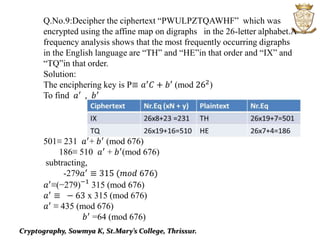
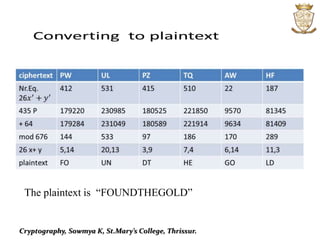
This document discusses cryptography and various encryption techniques. It describes cryptography as the study of methods for sending secret messages. The basic terminology includes plaintext, ciphertext, encryption, and decryption. Several encryption methods are covered, including substitution ciphers, shift ciphers, affine ciphers, and digraph ciphers. Examples are provided to demonstrate how to encrypt and decrypt messages using these different cipher techniques. The document is authored by Sowmya K of St. Mary's College in Thrissur.