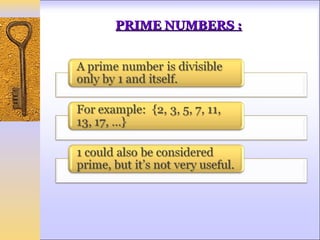
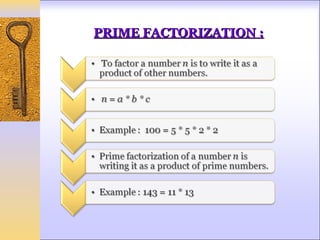
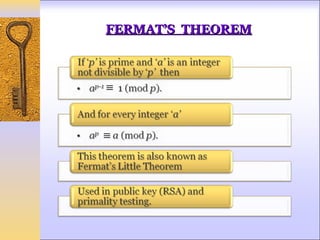
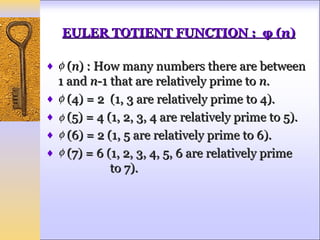
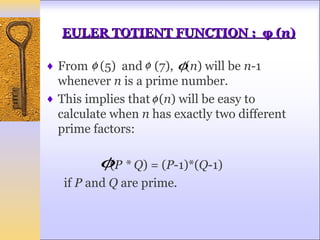
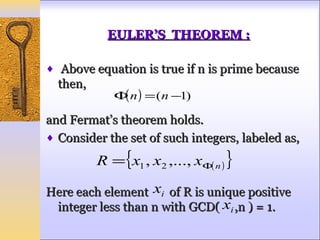
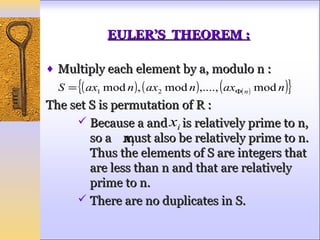
This document discusses Fermat's and Euler's theorems regarding prime numbers and their applications in cryptography. It begins by defining prime numbers, prime factorization, and greatest common divisors. It then explains Fermat's theorem that any integer to the power of a prime number minus one is congruent to one modulo that prime number. Next, it defines Euler's totient function and proves Euler's theorem, which generalizes Fermat's theorem. It concludes by providing an example of how these theorems can be applied to encrypt and decrypt messages in a public-key cryptography system.




![FERMAT’S THEOREM PROOF :
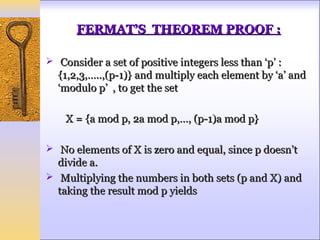
a * 2a *…* (p-1)a ≡ [1 * 2 * 3 *…* (p-1)] (mod p)
a p −1 ( p −1)! ≡ ( p −1)!(mod p )
Thus on equating (p-1)! term from both the sides,
since it is relatively prime to p, result becomes,
a p −1 ≡1(mod p )
An alternative form of Fermat’s Theorem is given as
a p ≡ a (mod p )](https://image.slidesharecdn.com/ankita-121101014040-phpapp01/85/EULER-AND-FERMAT-THEOREM-9-320.jpg)



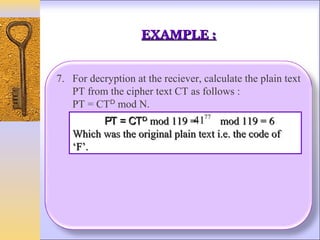
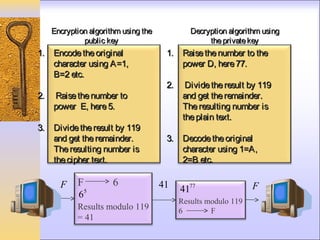

![REFERENCES :
[1] Cryptography and Network Security Principles
and Practice, Fifth Edition, By: William Stallings.
[2] Cryptography and Network Security, Chapter 9
Mathematics of Cryptography, Part III: Primes and
Related Congruence Equations, By: Behrouz
Forouzan.
[3]L. Levine, Fermat's Little Theorem: A Proof by
Function Iteration," Math. Mag. 72 (1999), 308-
309.
[4] C. Smyth, A Coloring Proof of a Generalisation
of Fermat's Little Theorem," Amer. Math. Monthly
93 (1986), 469-471.](https://image.slidesharecdn.com/ankita-121101014040-phpapp01/85/EULER-AND-FERMAT-THEOREM-24-320.jpg)
