Four Network Security Challenges for the Cloud Generation
•
1 like•404 views
Users are accessing cloud applications from anywhere at any time, which has expanded the attack surface and made network defenses more difficult. Traditional network protections are overwhelmed by modern threats like encrypted web traffic and 700+ new browser vulnerabilities each year. Half of malware in 2019 will use encryption for delivery, command and control, or data exfiltration, hiding threats from security tools. Symantec Web Security Services provides cloud-based network security that balances security, performance, complexity and cost to address these challenges.
Report
Share
Report
Share
Download to read offline
Recommended
Your Data Is Under Siege: Fortify Your Endpoints

1 in 5 businesses suffered a security breach in 2016. See the trends and learn how you can stop malware in its tracks.
2017 Cybersecurity Predictions

Read our cybersecurity predictions for 2017: http://researchcenter.paloaltonetworks.com/tag/2017-predictions/
These predictions are part of an ongoing blog series examining “Sure Things” (predictions that are almost guaranteed to happen) and “Long Shots” (predictions that are less likely to happen) in cybersecurity in 2017.
The Top Three 2021 Cyber Threats

Globally recognized cybersecurity expert and best-selling author, Sai Huda, says the top three cyber threats that all organizations need to be on heightened alert for in 2021 are ransomware, cloud misconfigurations exploit and supply chain compromise.
Sai Huda advises businesses on cyber risk management and is a frequent keynote speaker at major industry conferences. He is also the author of the best-selling book “Next Level Cybersecurity: Detect the Signals, Stop the Hack.” In this ground-breaking book, Sai Huda reveals 15 signals that provide early tip-offs to cyberattacks and a seven step method to implement an early warning and detection system to stop a cyber attack in time and prevent loss or damage.
Sai Huda is warning businesses worldwide to be on heightened alert for ransomware, especially new variants that are programmed to scan for keywords that indicate mission critical or highly sensitive data so that critical data can be found quickly. Then the ransomware will exfiltrate a copy, then it will encrypt and lock down access to the data and demand a ransom payment. The attacker will then release a portion of the data publicly to extort the victim to pay the ransom. Phishing and unpatched vulnerabilities are the two main ways the attacker is able to insert ransomware.
He is also warning that cloud misconfigurations are another major threat as businesses move to the cloud but fail to configure properly all of the systems and services the cloud provider makes available. The cloud provider is responsible for security of the cloud, while the business itself is responsible for security in the cloud. Cloud configurations require specific know-how to prevent and detect a cyber attack. Otherwise, there will be many doors and windows open for an attacker to exploit and break in.
Supplier compromise is also another major threat, especially software providers, as evident with the recent SolarWinds supply chain compromise, where the attackers inserted a backdoor malware into the software update process at the supplier and with one fell swoop, as thousands downloaded the software update, the attacker gained entry undetected into thousands or organizations worldwide. So a compromise at a supplier can be the backdoor into the organization.
Regardless, there will be signals of the attackers and in his book Sai Huda reveals the signals that organizations must be on the look out for to prevent becoming victim to ransomware, cloud misconfigurations exploit or supply chain compromise.
The Cost of Inactivity: Malware Infographic

As the cost and likelihood of a breach grows you can't afford "good enough" protection before, during, AND after an attack. Protect your brand and data with Cisco email and web security.
Learn more: http://cs.co/9003hKu3, http://cs.co/9003hKu9
2017 Cyber Risk Grades by Industry: Normshield Executive Presentation

We analyzed more than 200 organizations and aggregated their cyber security vulnerabilities into easy-to-understand letter grades. This presentation outlines the biggest threats and the most at-risk industries. For the full analysis visit https://info.normshield.com/risk-brief
Reduciendo su riesgo cibernético midiendo su Cyber Exposure 

En la economía digital, la transformación digital ya no se trata de interrupciones. Es supervivencia. Cyber Exposure es una disciplina emergente para administrar y medir su superficie de ataque moderna para comprender con precisión y reducir su riesgo cibernético. Si estás volando a ciegas ante una creciente brecha de exposición cibernética, eso es insostenible
Recommended
Your Data Is Under Siege: Fortify Your Endpoints

1 in 5 businesses suffered a security breach in 2016. See the trends and learn how you can stop malware in its tracks.
2017 Cybersecurity Predictions

Read our cybersecurity predictions for 2017: http://researchcenter.paloaltonetworks.com/tag/2017-predictions/
These predictions are part of an ongoing blog series examining “Sure Things” (predictions that are almost guaranteed to happen) and “Long Shots” (predictions that are less likely to happen) in cybersecurity in 2017.
The Top Three 2021 Cyber Threats

Globally recognized cybersecurity expert and best-selling author, Sai Huda, says the top three cyber threats that all organizations need to be on heightened alert for in 2021 are ransomware, cloud misconfigurations exploit and supply chain compromise.
Sai Huda advises businesses on cyber risk management and is a frequent keynote speaker at major industry conferences. He is also the author of the best-selling book “Next Level Cybersecurity: Detect the Signals, Stop the Hack.” In this ground-breaking book, Sai Huda reveals 15 signals that provide early tip-offs to cyberattacks and a seven step method to implement an early warning and detection system to stop a cyber attack in time and prevent loss or damage.
Sai Huda is warning businesses worldwide to be on heightened alert for ransomware, especially new variants that are programmed to scan for keywords that indicate mission critical or highly sensitive data so that critical data can be found quickly. Then the ransomware will exfiltrate a copy, then it will encrypt and lock down access to the data and demand a ransom payment. The attacker will then release a portion of the data publicly to extort the victim to pay the ransom. Phishing and unpatched vulnerabilities are the two main ways the attacker is able to insert ransomware.
He is also warning that cloud misconfigurations are another major threat as businesses move to the cloud but fail to configure properly all of the systems and services the cloud provider makes available. The cloud provider is responsible for security of the cloud, while the business itself is responsible for security in the cloud. Cloud configurations require specific know-how to prevent and detect a cyber attack. Otherwise, there will be many doors and windows open for an attacker to exploit and break in.
Supplier compromise is also another major threat, especially software providers, as evident with the recent SolarWinds supply chain compromise, where the attackers inserted a backdoor malware into the software update process at the supplier and with one fell swoop, as thousands downloaded the software update, the attacker gained entry undetected into thousands or organizations worldwide. So a compromise at a supplier can be the backdoor into the organization.
Regardless, there will be signals of the attackers and in his book Sai Huda reveals the signals that organizations must be on the look out for to prevent becoming victim to ransomware, cloud misconfigurations exploit or supply chain compromise.
The Cost of Inactivity: Malware Infographic

As the cost and likelihood of a breach grows you can't afford "good enough" protection before, during, AND after an attack. Protect your brand and data with Cisco email and web security.
Learn more: http://cs.co/9003hKu3, http://cs.co/9003hKu9
2017 Cyber Risk Grades by Industry: Normshield Executive Presentation

We analyzed more than 200 organizations and aggregated their cyber security vulnerabilities into easy-to-understand letter grades. This presentation outlines the biggest threats and the most at-risk industries. For the full analysis visit https://info.normshield.com/risk-brief
Reduciendo su riesgo cibernético midiendo su Cyber Exposure 

En la economía digital, la transformación digital ya no se trata de interrupciones. Es supervivencia. Cyber Exposure es una disciplina emergente para administrar y medir su superficie de ataque moderna para comprender con precisión y reducir su riesgo cibernético. Si estás volando a ciegas ante una creciente brecha de exposición cibernética, eso es insostenible
How Datacenter Threats are Evolving Infographic

Infographic which visually shows how datacenter threats are evolving
IT security in 2021: Why Ransomware Is Still The Biggest Threat

What’s next for cybersecurity in 2021? Last year, both the public and the private sector experienced a plethora of breaches and attacks. From regular security lapses to more complicated, and often more expensive, ransomware attacks - 2020 has seen a drastic increase in the volume of breaches that led to the widespread loss of data and valuable information around the world.
Re solution - corona virus cyber security infographic

An infographic on the effect that COVID-19 is having on Cyber Security and the measures you can take to protect yourself.
Hacker Tricks: How You Can Protect Yourself

Whenever a form of technology is developed, there’s a new opportunity cybercriminals to use hacker tricks take advantage of their users. Everyday, millions of devious cybercriminals look for different methods for exploiting security vulnerabilities in a business network so they can steal data, extort money from victims, send spam, and promote their view point. Here’s an overview of hacker tricks used to access your network and devices. Learn more here: http://bit.ly/1CeKjHO
180814 cloudsec2018 charles mok1

Understanding and Tackling Emerging Cyber Threats
Aug 14 2018
Trend Micro's CLOUDSEC 2018 "Freedom to Connect"
Patches Arrren't Just for Pirates

The web can be a dangerous place. Software that has code defects, also known as vulnerabilities, pose serious risks to users – from the most casual Internet surfers to business owners.
Mobile Security Research Projects Help

Significant Norms in Mobile Security
Integration of Mobile Security
Supportive Keys for Mobile Security
Pervasive Security Across Your Extended Network

There are many ways attackers can access your network. Keep yours safe before, during, and after an attack with best-in-class Cisco Security designed to protect your business data. Learn more at http://cs.co/9009BJ8o3
Chapter 3, Data Protection vs Ransomware

Virus-ID Discord Discuss Chapter 3, data protection vs ransomware
What is CryptoLocker and How Can I Protect My Business From It?

If your business operates on Windows computers, be on the lookout. Cybercriminals created malicious computer software, called CryptoLocker, which can invade your computer, encrypt your data, and then demand you pay a ransom. Afterwards, you have roughly 72 hours to pay the ransom of at least $200 in bitcoins. If you don’t pay the ransom on time, the price can go up to $2,000. Or don’t pay and lose your data forever, which likely won’t be an option if CryptoLocker encrypted files critical to operating your business, such as legal documents, payroll forms, and customer information.
PhD-Guidance-in-Cyber-Security

KEY PURPOSE OF CYBER SECURITY TOOLS
UPCOMING DEVELOPMENTS IN CYBER SECURITY
FOREMOST RESEARCH AREAS IN CYBER SECURITY
2014 information technology threat predictions

Infographic - 2014 will witness new attack vectors and evasion techniques. Threat innovation will focus on mobile, social and cloud platforms while advanced evasion techniques will plague network security systems...
NormShield Cyber Threat & Vulnerability Orchestration Overview

NormShield is at the forefront of orchestrated cyber security operations and reporting, a transformative new category that Gartner calls SOAR. The NormShield cloud platform automates finding vulnerabilities, prioritizes them and provides actionable intelligence. A key differentiation is the company’s combination of advanced automation and human intelligence for reliability unparalleled in the industry. NormShield CISOs receive letter-grade risk scorecards. Their teams manage risk, not data. The results are measurable: informed decisions and swift action that reduces risk as never before possible and at an affordable price.
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

La seguridad cibernética es claramente un tema de creciente importancia en estos días. La presentación invitará a reflexionar sobre la semántica de las palabras que usamos al hablar sobre seguridad cibernética, y lo guiará a través del mapa de perspectivas y metodologías hacia su propio camino para estar seguros y protegidos en el entorno digital. La charla se ajusta tanto para los líderes empresariales como técnicos.
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
A profile is an extremely sensitive optional configuration file which allows to re-define different system functionality parameters such as mobile carrier settings, Mobile Device Management (MDM) settings and networking settings. Through social engineering techniques such as email phishing or a fake URL, an attacker can convince a user to install a malicious profile and compromise the device settings to silently route network traffic from the device to a remote proxy over SSL using a self-signed certificate.
The impact:
Once the attacker has re-routed all traffic from the mobile device to their own server, they can begin to install other malicious apps and decrypt SSL communications.PhD-Guidance-in-Dependable-and-Secure-Computing

INNOVATIVE TECHNOLOGIES IN DEPENDABLE SECURE COMPUTING
KEY USES OF DEPENDABLE AND SECURE COMPUTING TOOLS
UTMOST TOPICS IN DEPENDABLE SECURE COMPUTING
Watch Guard Reputation Enabled Defense (White Paper)Dna

Watchguard & DNA IT Solutions White Paper on Reputation Enabled Defence
More Related Content
What's hot
How Datacenter Threats are Evolving Infographic

Infographic which visually shows how datacenter threats are evolving
IT security in 2021: Why Ransomware Is Still The Biggest Threat

What’s next for cybersecurity in 2021? Last year, both the public and the private sector experienced a plethora of breaches and attacks. From regular security lapses to more complicated, and often more expensive, ransomware attacks - 2020 has seen a drastic increase in the volume of breaches that led to the widespread loss of data and valuable information around the world.
Re solution - corona virus cyber security infographic

An infographic on the effect that COVID-19 is having on Cyber Security and the measures you can take to protect yourself.
Hacker Tricks: How You Can Protect Yourself

Whenever a form of technology is developed, there’s a new opportunity cybercriminals to use hacker tricks take advantage of their users. Everyday, millions of devious cybercriminals look for different methods for exploiting security vulnerabilities in a business network so they can steal data, extort money from victims, send spam, and promote their view point. Here’s an overview of hacker tricks used to access your network and devices. Learn more here: http://bit.ly/1CeKjHO
180814 cloudsec2018 charles mok1

Understanding and Tackling Emerging Cyber Threats
Aug 14 2018
Trend Micro's CLOUDSEC 2018 "Freedom to Connect"
Patches Arrren't Just for Pirates

The web can be a dangerous place. Software that has code defects, also known as vulnerabilities, pose serious risks to users – from the most casual Internet surfers to business owners.
Mobile Security Research Projects Help

Significant Norms in Mobile Security
Integration of Mobile Security
Supportive Keys for Mobile Security
Pervasive Security Across Your Extended Network

There are many ways attackers can access your network. Keep yours safe before, during, and after an attack with best-in-class Cisco Security designed to protect your business data. Learn more at http://cs.co/9009BJ8o3
Chapter 3, Data Protection vs Ransomware

Virus-ID Discord Discuss Chapter 3, data protection vs ransomware
What is CryptoLocker and How Can I Protect My Business From It?

If your business operates on Windows computers, be on the lookout. Cybercriminals created malicious computer software, called CryptoLocker, which can invade your computer, encrypt your data, and then demand you pay a ransom. Afterwards, you have roughly 72 hours to pay the ransom of at least $200 in bitcoins. If you don’t pay the ransom on time, the price can go up to $2,000. Or don’t pay and lose your data forever, which likely won’t be an option if CryptoLocker encrypted files critical to operating your business, such as legal documents, payroll forms, and customer information.
PhD-Guidance-in-Cyber-Security

KEY PURPOSE OF CYBER SECURITY TOOLS
UPCOMING DEVELOPMENTS IN CYBER SECURITY
FOREMOST RESEARCH AREAS IN CYBER SECURITY
2014 information technology threat predictions

Infographic - 2014 will witness new attack vectors and evasion techniques. Threat innovation will focus on mobile, social and cloud platforms while advanced evasion techniques will plague network security systems...
NormShield Cyber Threat & Vulnerability Orchestration Overview

NormShield is at the forefront of orchestrated cyber security operations and reporting, a transformative new category that Gartner calls SOAR. The NormShield cloud platform automates finding vulnerabilities, prioritizes them and provides actionable intelligence. A key differentiation is the company’s combination of advanced automation and human intelligence for reliability unparalleled in the industry. NormShield CISOs receive letter-grade risk scorecards. Their teams manage risk, not data. The results are measurable: informed decisions and swift action that reduces risk as never before possible and at an affordable price.
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

La seguridad cibernética es claramente un tema de creciente importancia en estos días. La presentación invitará a reflexionar sobre la semántica de las palabras que usamos al hablar sobre seguridad cibernética, y lo guiará a través del mapa de perspectivas y metodologías hacia su propio camino para estar seguros y protegidos en el entorno digital. La charla se ajusta tanto para los líderes empresariales como técnicos.
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & MitigationLacoon Mobile Security
A profile is an extremely sensitive optional configuration file which allows to re-define different system functionality parameters such as mobile carrier settings, Mobile Device Management (MDM) settings and networking settings. Through social engineering techniques such as email phishing or a fake URL, an attacker can convince a user to install a malicious profile and compromise the device settings to silently route network traffic from the device to a remote proxy over SSL using a self-signed certificate.
The impact:
Once the attacker has re-routed all traffic from the mobile device to their own server, they can begin to install other malicious apps and decrypt SSL communications.PhD-Guidance-in-Dependable-and-Secure-Computing

INNOVATIVE TECHNOLOGIES IN DEPENDABLE SECURE COMPUTING
KEY USES OF DEPENDABLE AND SECURE COMPUTING TOOLS
UTMOST TOPICS IN DEPENDABLE SECURE COMPUTING
What's hot (20)
IT security in 2021: Why Ransomware Is Still The Biggest Threat

IT security in 2021: Why Ransomware Is Still The Biggest Threat
Re solution - corona virus cyber security infographic

Re solution - corona virus cyber security infographic
What is CryptoLocker and How Can I Protect My Business From It?

What is CryptoLocker and How Can I Protect My Business From It?
NormShield Cyber Threat & Vulnerability Orchestration Overview

NormShield Cyber Threat & Vulnerability Orchestration Overview
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)
iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation

iOS Threats - Malicious Configuration Profiles, Threat, Detection & Mitigation
Similar to Four Network Security Challenges for the Cloud Generation
Watch Guard Reputation Enabled Defense (White Paper)Dna

Watchguard & DNA IT Solutions White Paper on Reputation Enabled Defence
Cloud Application Security Best Practices To follow.pdf

Cloud application security is the practice of protecting cloud-based applications and data from unauthorized access, theft, or loss. It involves implementing various security measures such as encryption, access controls, firewalls, and monitoring to ensure that cloud applications are secure from threats.
Cloud Application Security Best Practices To follow.pdf

Around 75% of modern workloads are now in the cloud. Millions of workers use cloud computing daily to communicate, code, and manage customer relations. Cloud computing is cost-effective, flexible, and convenient. However, cloud computing can pose security risks.
Enhancing Cybersecurity in Remote Work-3.pdf

Turing is a data-science-driven deep jobs platform helping companies spin up their engineering teams in the cloud at the push of a button. Based in Palo Alto, California, it is a fully remote company of 500 800+ people who help connect world-class remote software engineers with world-class companies.
Turing makes the remote hiring journey easy and rewarding for both companies and developers. With Turing, companies can hire pre-vetted, Silicon Valley-caliber remote software talent across 100+ skills in 3-5 days. Also, Turing democratizes opportunities for remote developers from around the world by offering them high-quality software jobs with top US firms.
Turing's Intelligent Talent Cloud uses AI to source, vet, match, and manage over a 1.5 million developers worldwide. This, in turn, helps organizations save valuable time and resources as they build their dream engineering team in a matter of days.
For more info, head over to: http://turing.com/s/yB8zZu
MIST Effective Masquerade Attack Detection in the Cloud

Abstract: Cloud computing promises to significantly change the way we use computers and access and store our personal and business information. With these new computing and communications paradigms arise new data security challenges. Existing data protection mechanisms such as encryption have failed in preventing data theft attacks, especially those perpetrated by an insider to the cloud provider. We propose a different approach for securing data in the cloud using offensive decoy technology. We monitor data access in the cloud and detect abnormal data access patterns. When unauthorized access is suspected and then verified using challenge questions, we launch a disinformation attack by returning large amounts of decoy information to the attacker. This protects against the misuse of the user’s real data. Experiments conducted in a local file setting provide evidence that this approach may provide unprecedented levels of user data security in a Cloud environment.
Keywords: Mist, Insider data stealing, Bait information, Lure Files, Validating user
The Top 5 Risks of Cloud Migration 

Many organizations fear migrating their applications to the cloud because it can
be an extremely challenging and complex task. This process will require proper
planning, effort, and time in order for it to be successful.
The security measures as well as practices that organizations have built for their
on-premise infrastructure do not coincide with what they require in the cloud,
where everything is deeply integrated.
Before streamlining your workflow with cloud computing, you must be aware of
the most challenging security risks and how to avoid them. Let's explore how
organizations should approach the security aspects of cloud migration, from API
integration to access control and continuous monitoring.
This article will highlight some of the most common fears organizations have
while moving from an on-premise infrastructure to a cloud environment.
The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose

loud computing is evolving fast, and so are the threats and defense tactics. Cloud consumers and providers should always be aware of the latest risks and attack vectors and explore the latest security events to identify new attack vectors. Here, we’ll provide you with a list of the latest threats and discuss their effect on our security posture, and review a recent case study of attacks relevant to those threats.
Cloud_security.pptx

In this presentation, topics discussed are- What is cc?, What are the security risks in the cloud, and how to secure them with different tools?
Top 5 predictions webinar

As security professionals, how can we be sure that we’re ready for 2019? After the last few years, when our practices and conventions have been tested again and again, it’s a little daunting to consider what may face us in the year ahead. Will attackers set their sights on cloud apps? Will hackers join forces with organized crime? Will governments look to the private sector to deal with the skills gap? What will happen to cybersecurity budgets? Join us to get answers to these questions and more.
8 Top Cybersecurity Tools.pdf

Top encryption tools like McAfee are popular among business users. McAfee provides full disk encryption for desktops, laptops, and servers. The algorithm uses Advanced Encryption Standard(AES) with 256-bit keys. McAfee AES is certified by US Federal Information Processing Standard. There is also ready integration of multi-layer authentication.
La sécurité de l'emploi : protégez votre SI

La sécurité n’est plus un add-on au système d’information, mais doit s’intégrer à tous les niveaux, depuis son architecture jusqu’à la résolution d’incidents, en passant par l’exploitation au quotidien des centres de données. Dans un contexte de mobilité accrue et en considérant l’émergence d’un modèle d’informatique à la demande, la sécurité repose autant sur la prévention technique que sur l’éducation comportementale des utilisateurs et sur la capacité des systèmes à résister aux attaques Session présentée par le partenaire : DELL.
Speakers : Florian Malecki (DELL)
Disrupting the Malware Kill Chain - What's New from Palo Alto Networks.

Simon Wong and Chris Cram, Scalar security experts, discuss how Palo Alto Networks technology disrupts the entire malware kill chain. Attendees will also gain insight on flexible deployment options to better serve their mobile users, and how to get the most out of their Palo Alto Networks deployment.
Should we fear the cloud?

When you’re planning to move to the cloud and manage a hybrid environment, security is a top concern. But cloud is not necessarily less secure than a traditional environment. In fact, it may be possible to deliver even greater security in a hybrid cloud environment because it offers new and advanced opportunities.
In this eBook, you’ll discover how hackers are using traditional tactics in new ways to attack the cloud. You’ll also find out how the cloud can help you increase security with innovative approaches designed to detect threats long before they threaten your enterprise.
White Paper: Securing Nomadic Workforce

Top 7 things you need to know to secure your nomadic workforce.
8 Top Cybersecurity Tools.pptx

Cybersecurity threats are also evolving with advances in technology. As technology advances, so do the methods and techniques used by cybercriminals to breach security systems and steal sensitive information.
Similar to Four Network Security Challenges for the Cloud Generation (20)
Cloudflare_Everywhere_Security_Solution_Brief (1).pdf

Cloudflare_Everywhere_Security_Solution_Brief (1).pdf
Watch Guard Reputation Enabled Defense (White Paper)Dna

Watch Guard Reputation Enabled Defense (White Paper)Dna
Cloud Application Security Best Practices To follow.pdf

Cloud Application Security Best Practices To follow.pdf
Cloud Application Security Best Practices To follow.pdf

Cloud Application Security Best Practices To follow.pdf
MIST Effective Masquerade Attack Detection in the Cloud

MIST Effective Masquerade Attack Detection in the Cloud
The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose

The Notorious 9 Cloud Computing Threats - CSA Congress, San Jose
Disrupting the Malware Kill Chain - What's New from Palo Alto Networks.

Disrupting the Malware Kill Chain - What's New from Palo Alto Networks.
More from AboutSSL
Difference Between Digital Signature vs Digital Certificate

Know what is Digital Signature and Digital Certificate in details and understanding the real difference between them.
How to Install SSL Certificate in Red Hat Linux Apache Web Server

Follow this step by step guide to install SSL Certificate in Red Hat Linux Apache Web Server.
How to Move SSL Certificate from One Windows Server to Another

Step by step guide to move or copy an SSL certificate from one windows server to another windows server.
Installation Instructions for Microsoft Exchange 2010 Server

Follow these step by step instructions to install an SSL certificate in Microsoft Exchange Server 2010.
Wildcard and SAN (Multi-Domain) Certificates – What’s the Difference?

If you unsure between a Wildcard and a SAN (Multi-Domain) SSL certificate. Don’t worry! This presentation will help you understand the differences.
All You Need to Know About EV SSL Security

Understand An Extended Validation or EV SSL certificate, which is known as Green Address Bar Security in SSL security industry.
Top 9 Best Wildcard SSL Certificate Providers

It's a very crucial to find the cheap Wildcard SSL certificate & it's best provider from the globe. We evaluate the Best Wildcard SSL certificate providers in this presentation which can help you to find the cheap one.
Which are the best Organization Validation SSL Certificates? 

Find out the best Organization Validation SSL certificates such as InstantSSL, Elite SSL, True BusinessID, Secure Site, SSL Web Server from the trusted SSL providers Comodo, Thawte, Symantec & GeoTrust.
Top 7 Cheap Multi-Domain SSL Certificate Providers

Know the top 7 cheap Multi-Domain SSL certificate providers, features, technical specifications and examples of multi domain SSL certificate.
2016 Security Predictions Infographic by Symantec

2016 Security Predictions – Looking Ahead Infographic by Symantec.
A List of Affordable SSL Certificate Providers 2016

Know about the list of affordable SSL certificate providers 2016 such as The SSL Store™, Namecheap, Comodo SSL Store, GoDaddy, SSL.com, Network Solutions, GlobalSign, Trustico for website security.
How Does Code Signing Works?

A Code Signing Certificate is a digital signature technology allows authorized software publishers to sign their software code, script and content to authenticate their identification over internet.
More from AboutSSL (12)
Difference Between Digital Signature vs Digital Certificate

Difference Between Digital Signature vs Digital Certificate
How to Install SSL Certificate in Red Hat Linux Apache Web Server

How to Install SSL Certificate in Red Hat Linux Apache Web Server
How to Move SSL Certificate from One Windows Server to Another

How to Move SSL Certificate from One Windows Server to Another
Installation Instructions for Microsoft Exchange 2010 Server

Installation Instructions for Microsoft Exchange 2010 Server
Wildcard and SAN (Multi-Domain) Certificates – What’s the Difference?

Wildcard and SAN (Multi-Domain) Certificates – What’s the Difference?
Which are the best Organization Validation SSL Certificates? 

Which are the best Organization Validation SSL Certificates?
Top 7 Cheap Multi-Domain SSL Certificate Providers

Top 7 Cheap Multi-Domain SSL Certificate Providers
A List of Affordable SSL Certificate Providers 2016

A List of Affordable SSL Certificate Providers 2016
Recently uploaded
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP of Product, Amplitude
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
"Impact of front-end architecture on development cost", Viktor Turskyi

I have heard many times that architecture is not important for the front-end. Also, many times I have seen how developers implement features on the front-end just following the standard rules for a framework and think that this is enough to successfully launch the project, and then the project fails. How to prevent this and what approach to choose? I have launched dozens of complex projects and during the talk we will analyze which approaches have worked for me and which have not.
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
ODC, Data Fabric and Architecture User Group

Let's dive deeper into the world of ODC! Ricardo Alves (OutSystems) will join us to tell all about the new Data Fabric. After that, Sezen de Bruijn (OutSystems) will get into the details on how to best design a sturdy architecture within ODC.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Recently uploaded (20)
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
"Impact of front-end architecture on development cost", Viktor Turskyi

"Impact of front-end architecture on development cost", Viktor Turskyi
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
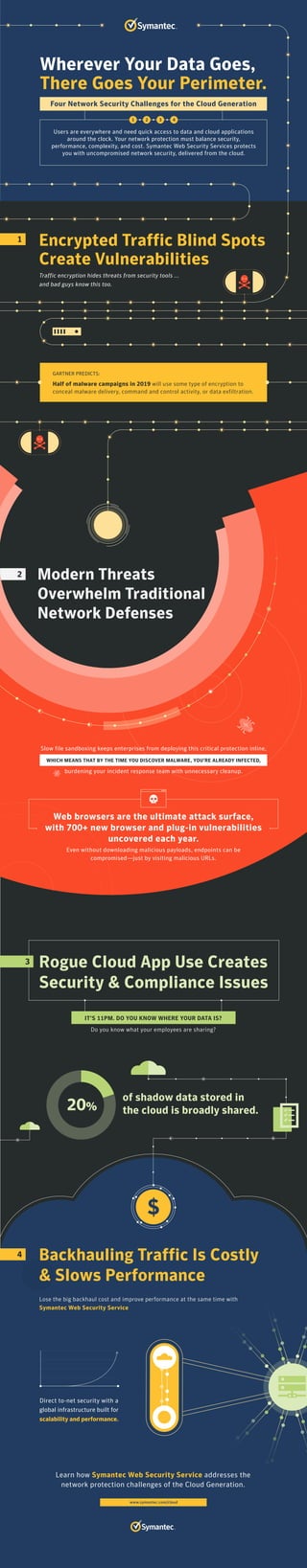
Four Network Security Challenges for the Cloud Generation
- 1. 4 Rogue Cloud App Use Creates Security & Compliance Issues of shadow data stored in the cloud is broadly shared. IT’S 11PM. DO YOU KNOW WHERE YOUR DATA IS? Do you know what your employees are sharing? 3 20% Modern Threats Overwhelm Traditional Network Defenses 2 Web browsers are the ultimate attack surface, with 700+ new browser and plug-in vulnerabilities uncovered each year. Even without downloading malicious payloads, endpoints can be compromised—just by visiting malicious URLs. Wherever Your Data Goes, There Goes Your Perimeter. Users are everywhere and need quick access to data and cloud applications around the clock. Your network protection must balance security, performance, complexity, and cost. Symantec Web Security Services protects you with uncompromised network security, delivered from the cloud. 1 GARTNER PREDICTS: Half of malware campaigns in 2019 will use some type of encryption to conceal malware delivery, command and control activity, or data exfiltration. Four Network Security Challenges for the Cloud Generation 1 2 3 4 Traffic encryption hides threats from security tools ... and bad guys know this too. Encrypted Traffic Blind Spots Create Vulnerabilities Lose the big backhaul cost and improve performance at the same time with Symantec Web Security Service Backhauling Traffic Is Costly & Slows Performance www.symantec.com/cloud Learn how Symantec Web Security Service addresses the network protection challenges of the Cloud Generation. Direct to-net security with a global infrastructure built for scalability and performance. Slow file sandboxing keeps enterprises from deploying this critical protection inline, WHICH MEANS THAT BY THE TIME YOU DISCOVER MALWARE, YOU’RE ALREADY INFECTED, burdening your incident response team with unnecessary cleanup.
