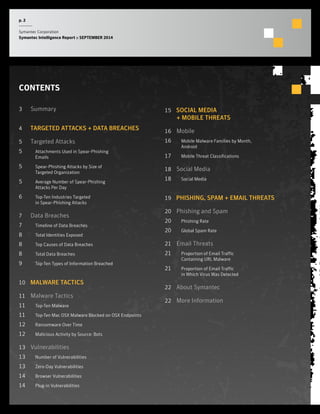
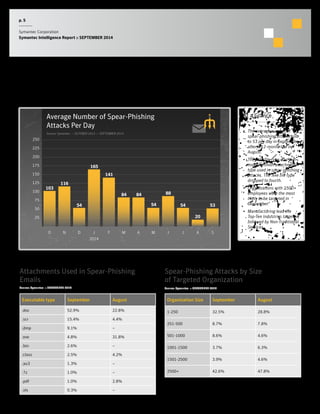
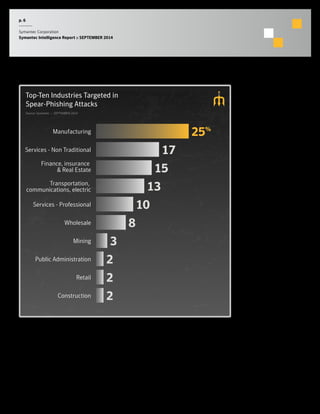
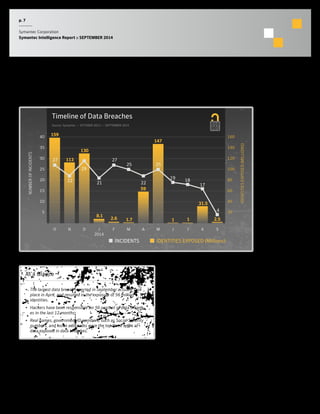
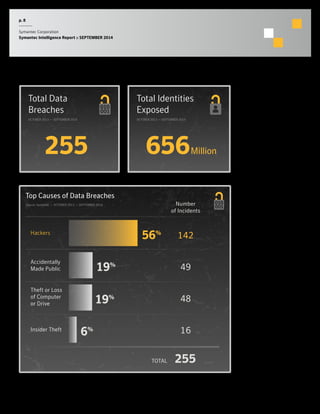
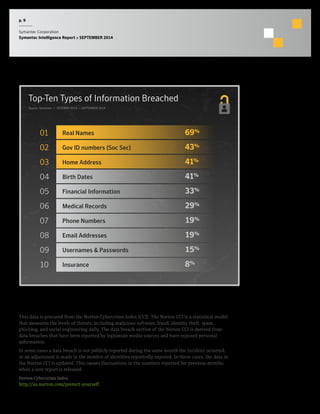
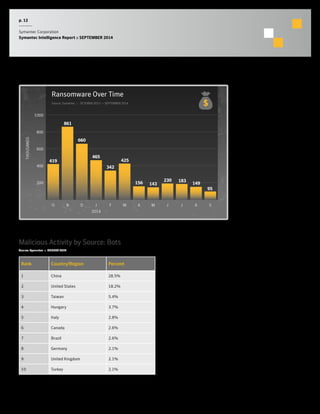
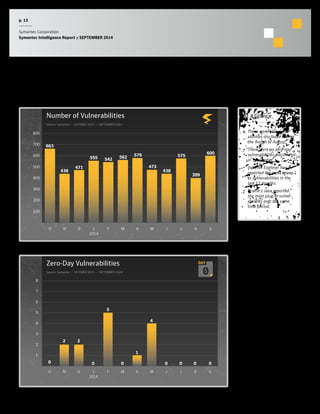
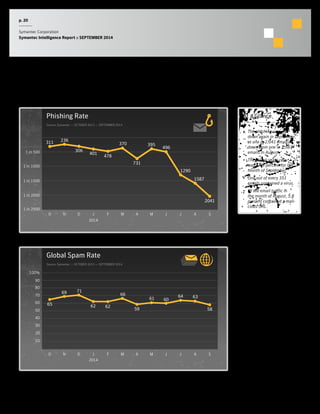
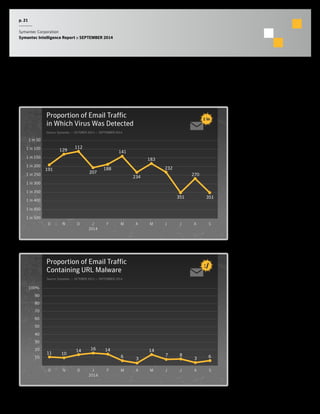
The September 2014 Symantec Intelligence Report highlights an increase in spear-phishing attacks, averaging 53 per day, with .doc files being the most common attachment. There were four public data breaches, exposing 2.5 million identities, with hackers responsible for the majority of breaches in the past year. The report also notes a significant number of vulnerabilities disclosed and a continuing rise of crypto-style ransomware threats.