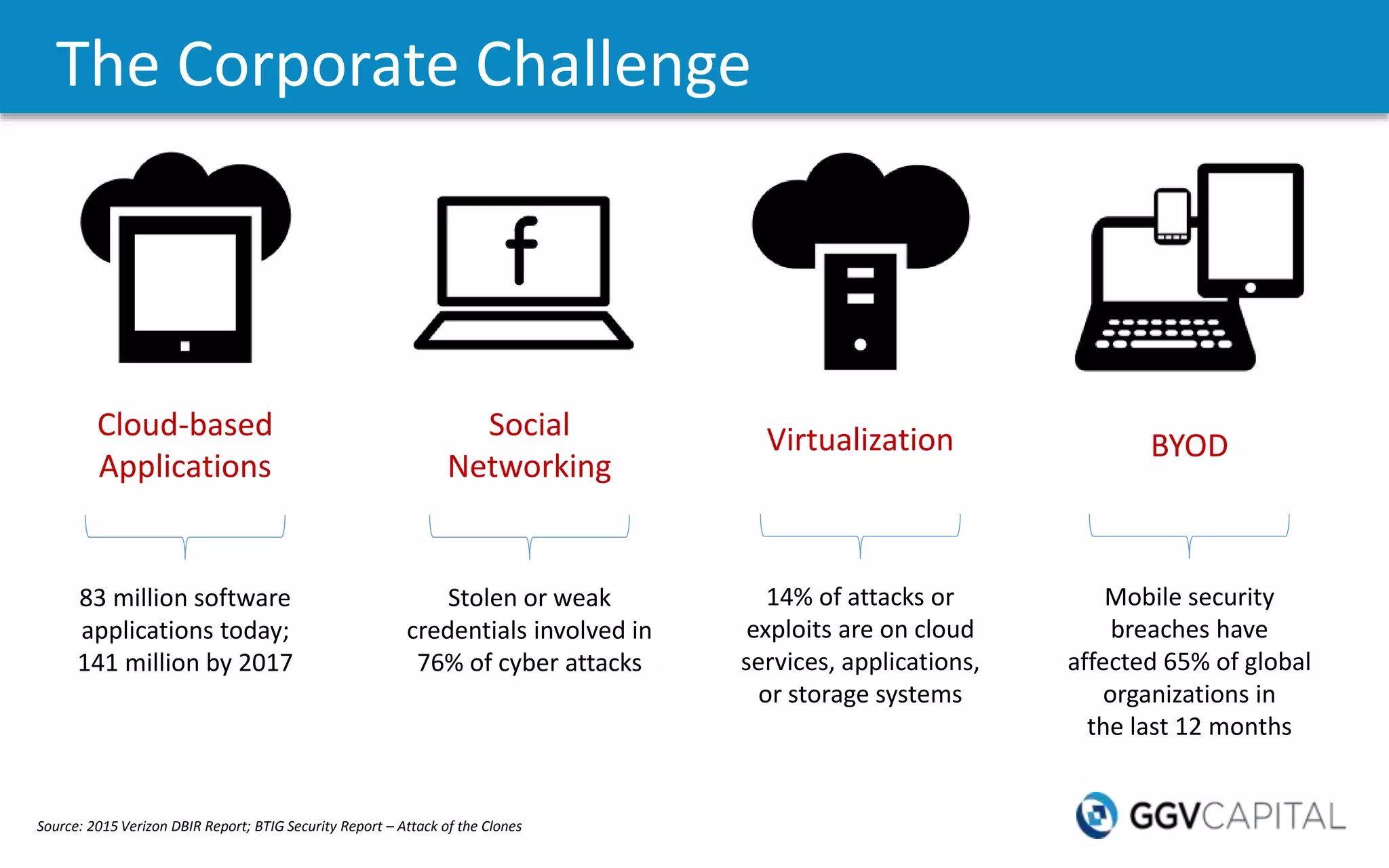
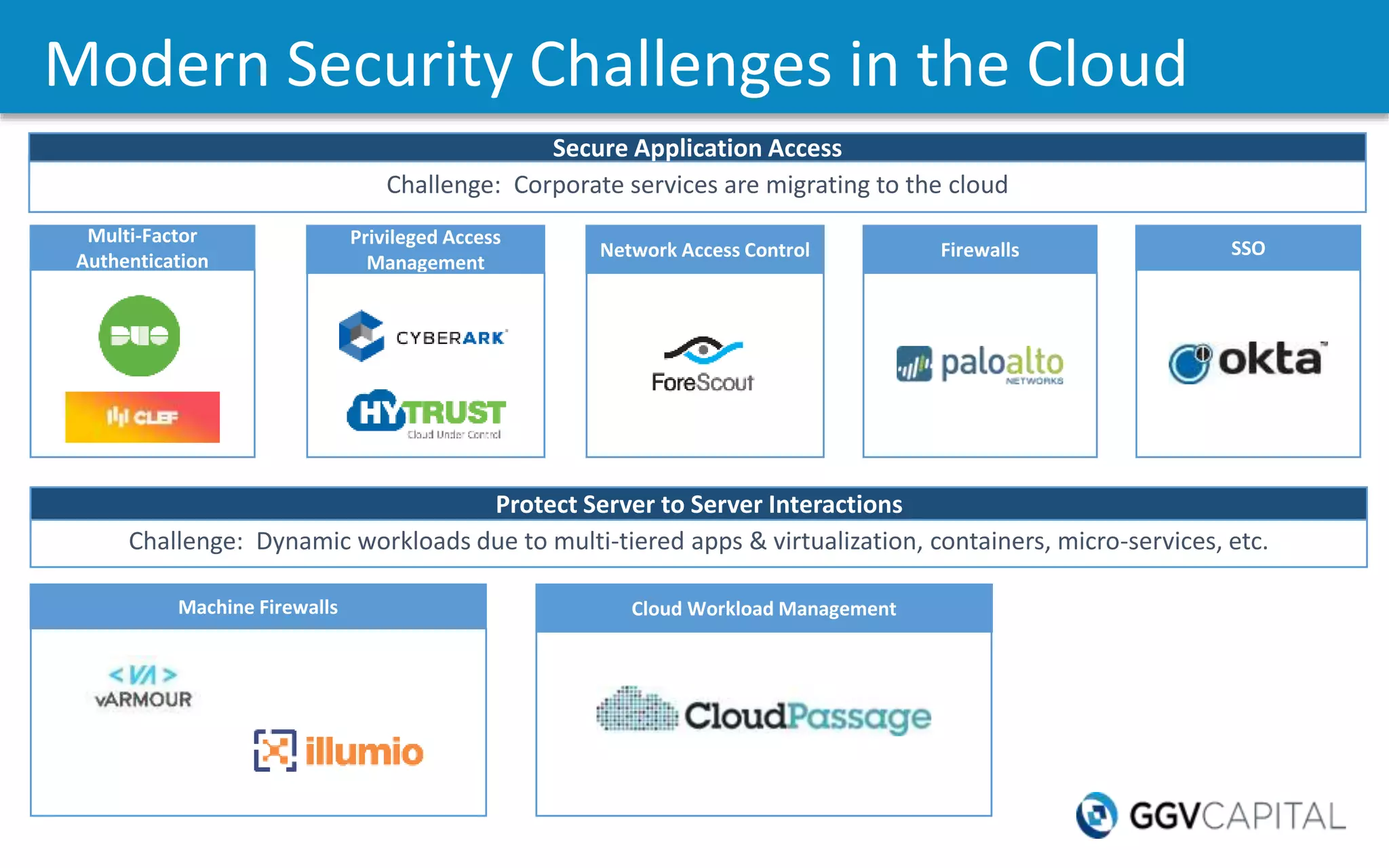
The document discusses the increasing threat of cybercrime, citing significant data breaches and the vast financial impact on the global economy. It highlights various cybersecurity challenges faced by organizations, including insider threats, mobile security issues, and the rise of new attack vectors such as the Internet of Things. The need for more advanced security measures and the evolution of threat detection strategies are emphasized, alongside the growing importance of cloud security and multi-factor authentication.