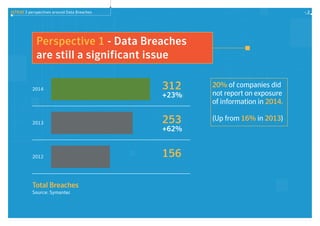
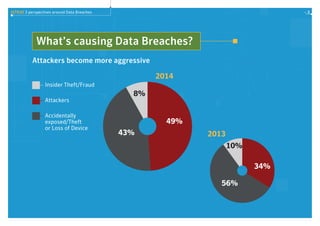
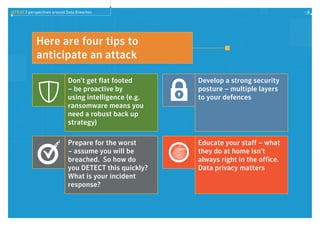
Data breaches are still a significant issue, with total breaches increasing 23% from 2013 to 2014. Ransomware attacks also grew significantly in 2014. Consumer attitudes toward data privacy are weakening information protection strategies, as many people are willing to share private information for free apps without understanding how their data will be used. The report discusses these trends in data breaches and privacy, and provides tips for improving defenses such as using security intelligence, preparing for breaches, developing layered defenses, and educating staff on data privacy.