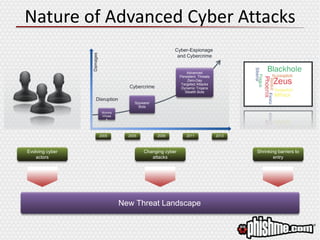
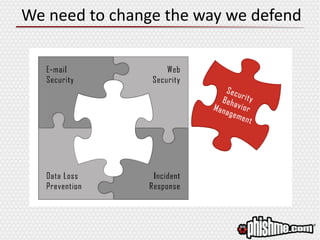
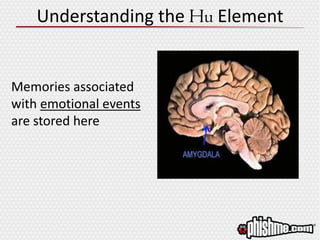
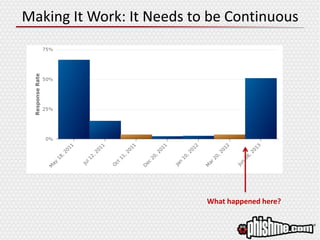
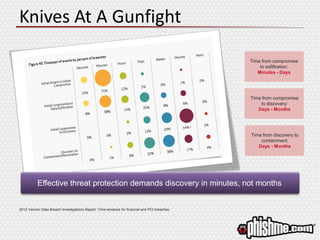
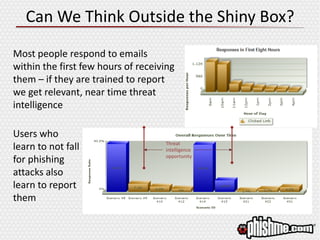
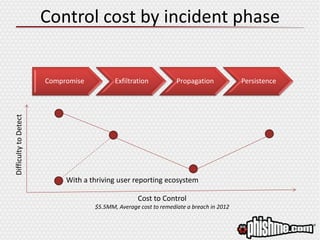
The document discusses the evolving landscape of advanced cyber attacks and the inadequacies of current security measures. It emphasizes the importance of enhancing human intelligence in threat detection through emotional engagement, continuous training, and user reporting. The need for quick incident response and the integration of user feedback are highlighted as essential components in combating cybersecurity threats effectively.