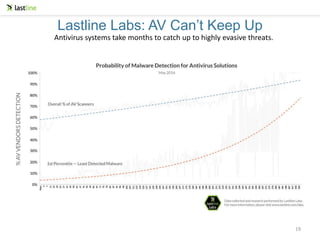
The document discusses the evolution of malware, highlighting that traditional detection methods have become ineffective against advanced threats that utilize sophisticated evasion techniques. It emphasizes the need for security professionals and the importance of behavior-based detection strategies, such as sandboxing, to combat these evolving threats. Finally, it underlines the critical role of technology integration and the necessity for continuous education and training in the security field.











![Copyright ©2015 Lastline, Inc. All rights reserved.
5B 00 00 00 00 pop ebx
8D 4B 42 lea ecx, [ebx + 42h]
51 push ecx
50 push eax
50 push eax
0F 01 4C 24 FE sidt [esp - 02h]
5B pop ebx
83 C3 1C add ebx, 1Ch
FA cli
8B 2B mov ebp, [ebx]
5B 00 00 00 00 8D 4B 42 51 50 50 0F 01 4C 24 FE 5B
83 C3 1C FA 8B 2B
Example: Chernobyl (CIH) Virus
SIGNATURE
13](https://image.slidesharecdn.com/sxsw-4-2-150317133128-conversion-gate01/85/Malware-in-the-Wild-Evolving-to-Evade-Detection-13-320.jpg)

![Copyright ©2015 Lastline, Inc. All rights reserved.
5B 00 00 00 00 pop ebx
8D 4B 42 lea ecx, [ebx + 42h]
51 push ecx
50 push eax
90 nop
50 push eax
40 inc eax
0F 01 4C 24 FE sidt [esp - 02h]
48 dec eax
5B pop ebx
83 C3 1C add ebx, 1Ch
FA cli
8B 2B mov ebp, [ebx]
5B 00 00 00 00 8D 4B 42 51 50 90 50 40 0F 01 4C 24
FE 48 5B 83 C3 1C FA 8B 2B
Disguising: Chernobyl (CIH) Virus
DIFFERENT
SIGNATURE
15](https://image.slidesharecdn.com/sxsw-4-2-150317133128-conversion-gate01/85/Malware-in-the-Wild-Evolving-to-Evade-Detection-15-320.jpg)