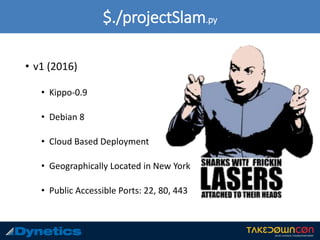
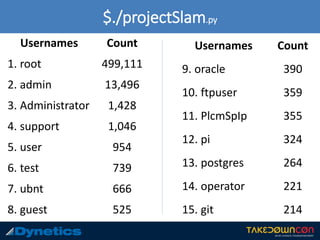
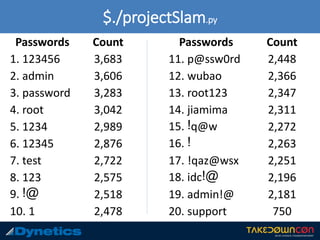
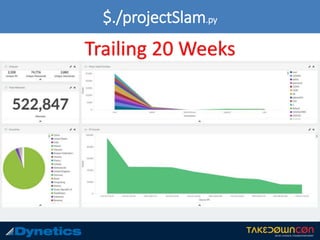
The document outlines the prevalence of cyber attacks, citing that up to 300 million attacks occur daily and focusing on government cybersecurity efforts. It describes Project Slam, which aims to research adversary behavior to generate wordlists and methodologies for combating cyber threats. Key takeaways emphasize the importance of using strong passwords, unique usernames, and enabling two-factor authentication.