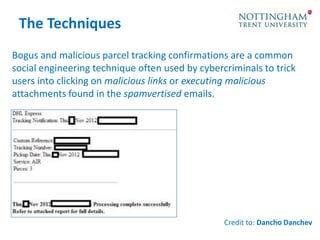
The document discusses the evolution of computer viruses and malware from early examples like Creeper and Brain to modern advanced threats like APTs and AETs. It notes that today's smart malware takes advantage of the insider role by compromising defenses and emulating the privileges of legitimate users. It argues that conventional security approaches are insufficient and that organizations must adopt unconventional thinking like red teaming to counter imaginative attacker techniques. The document provides examples of advanced evasion techniques used by malware and urges organizations to establish response capabilities and think outside the box to improve their security posture against evolving threats.