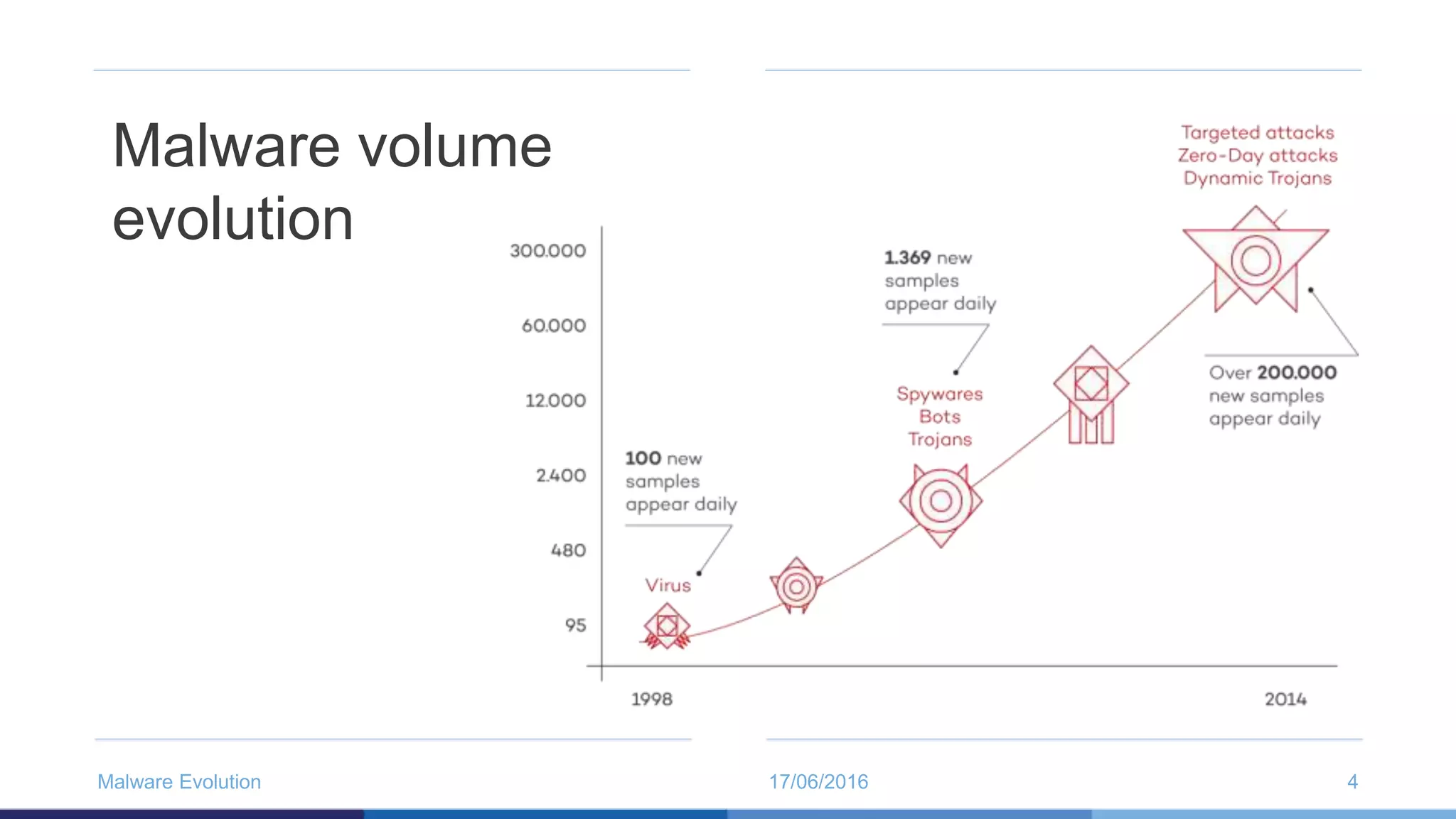
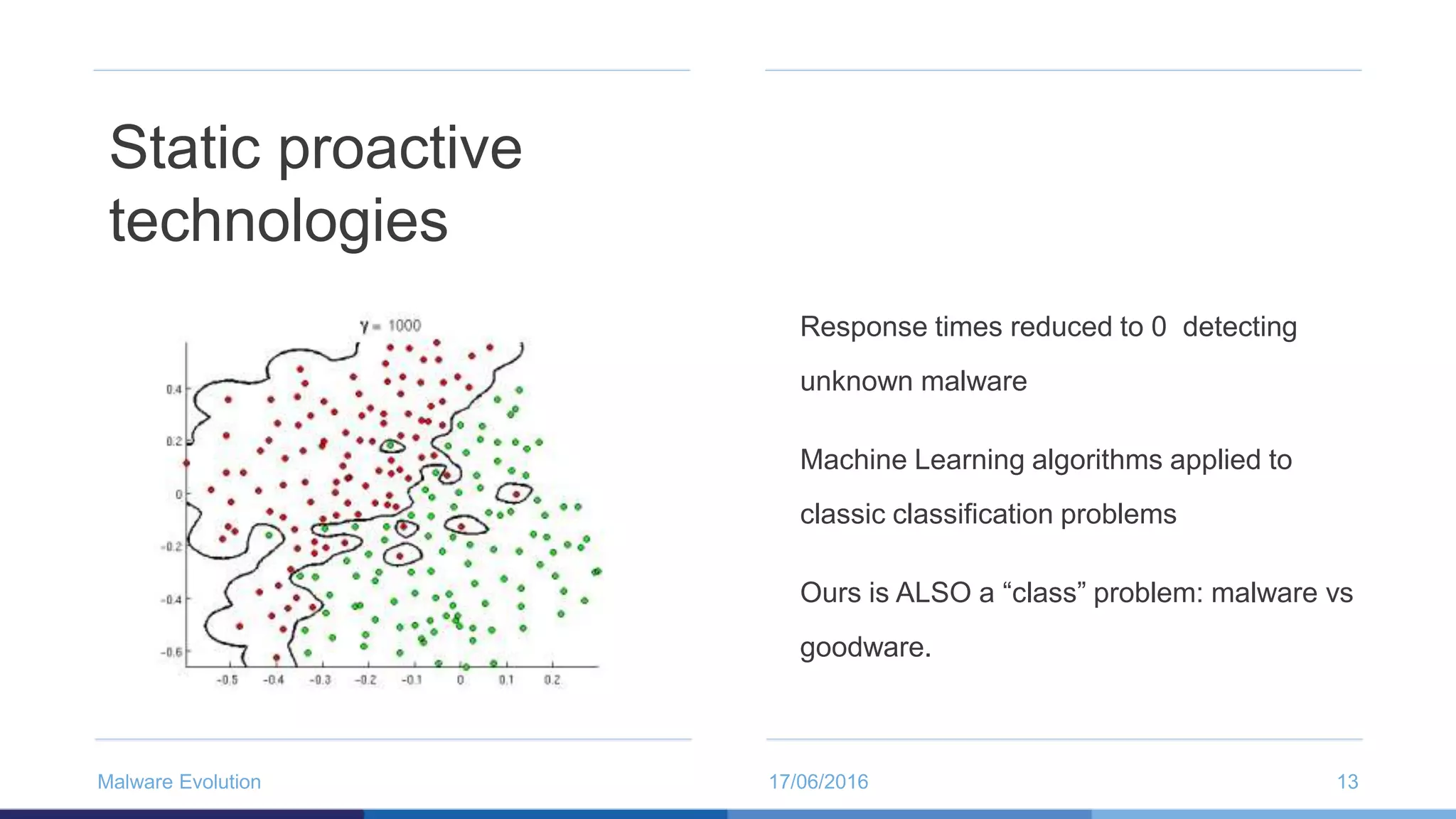
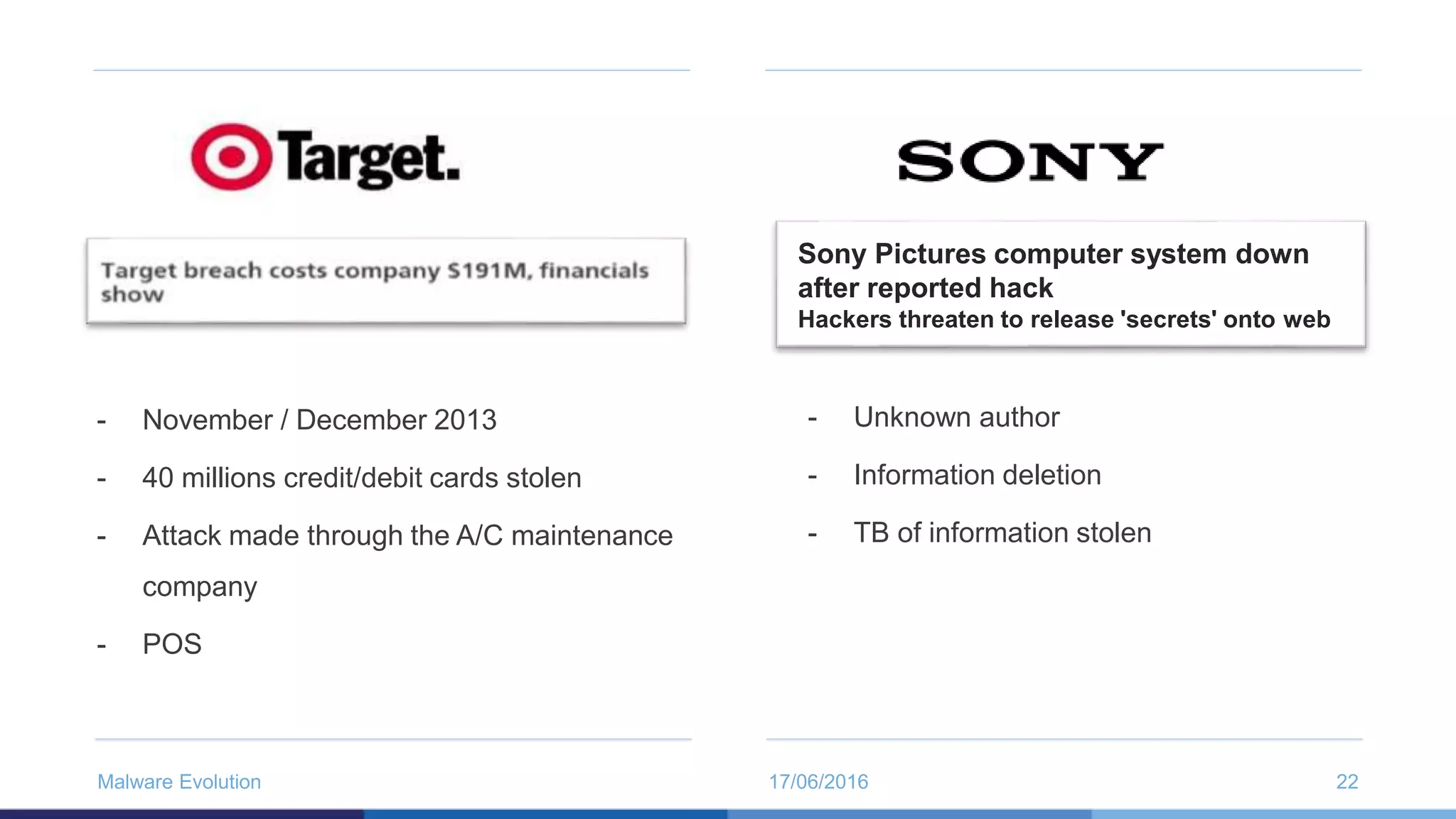
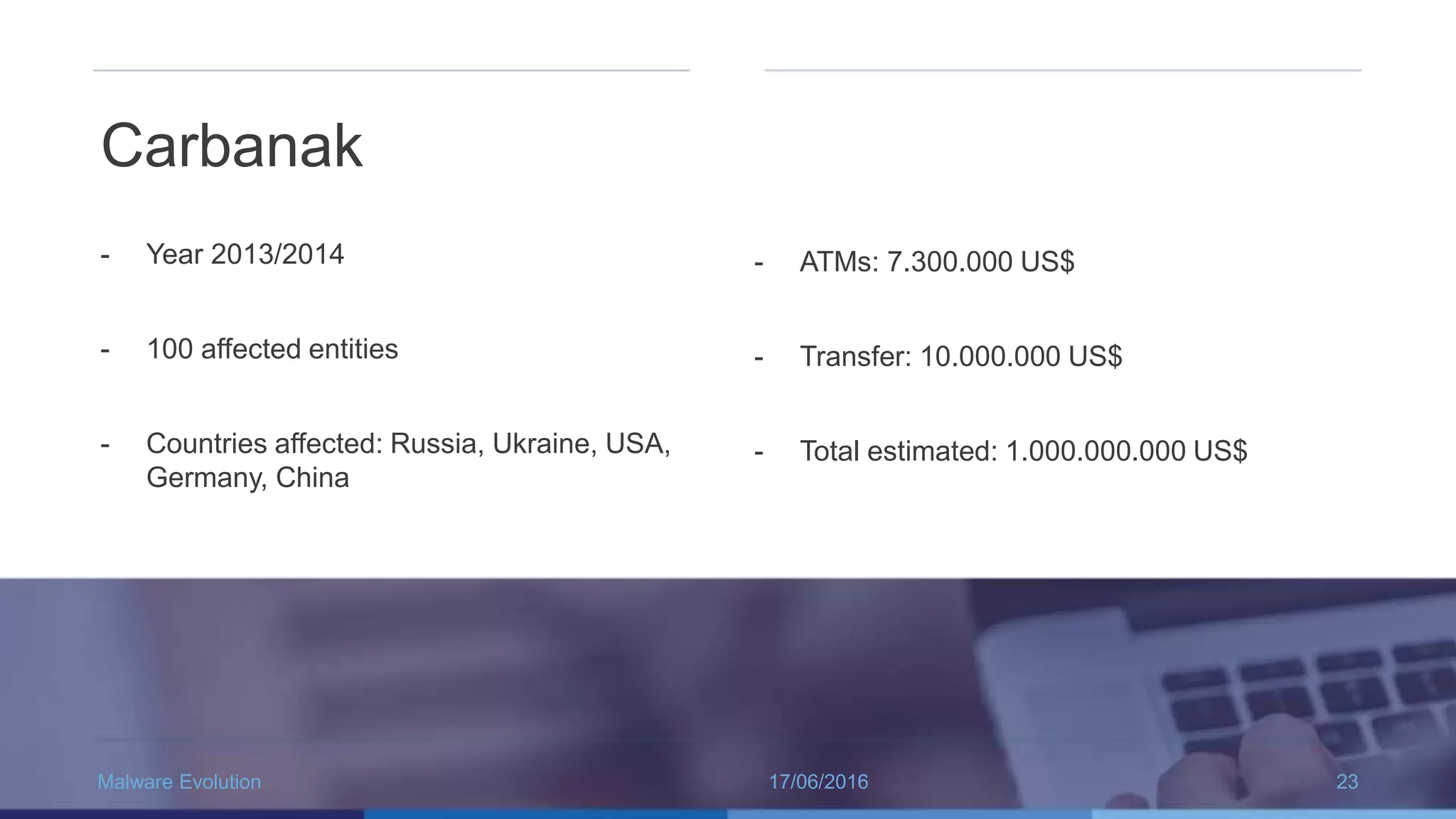
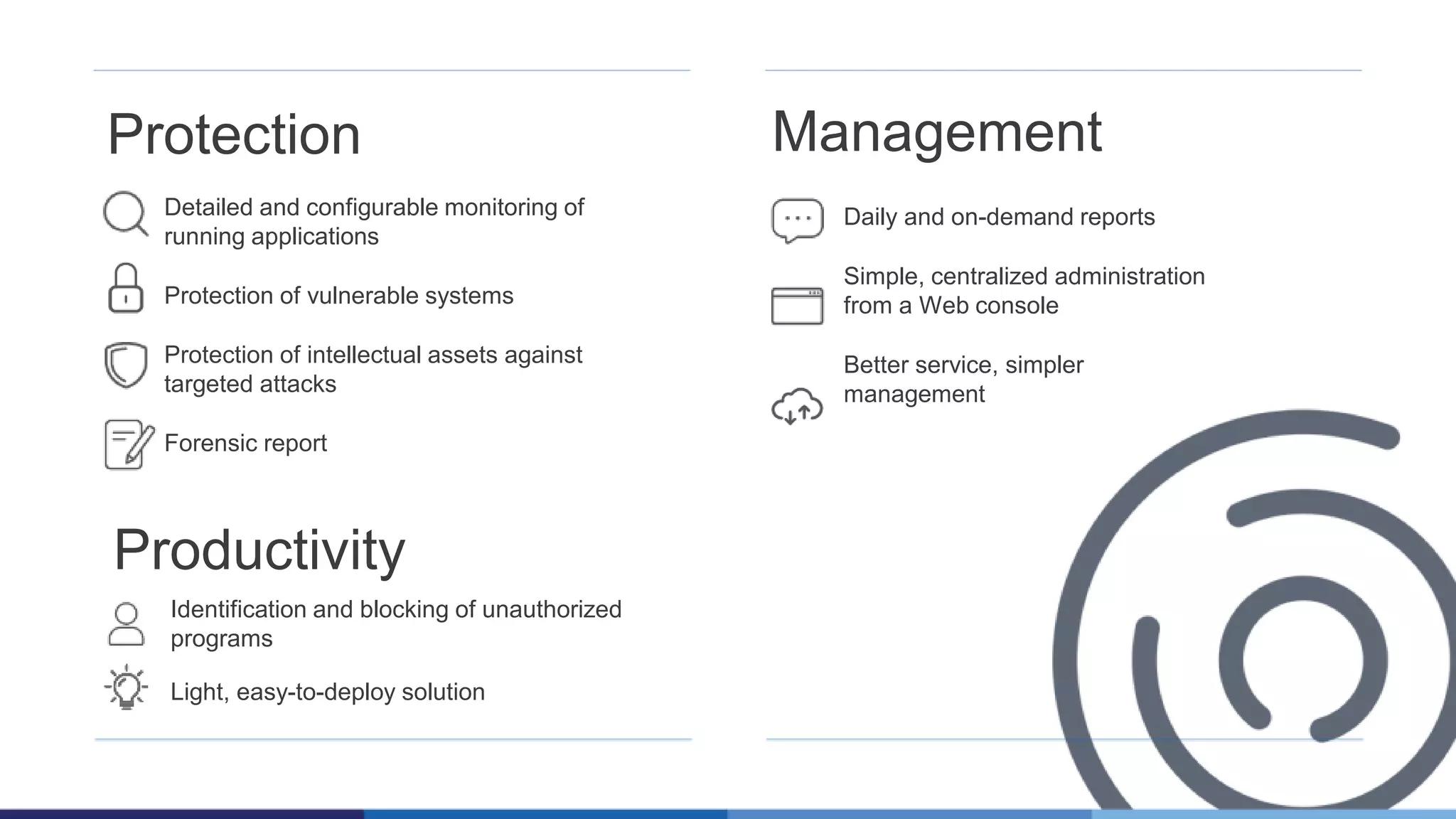
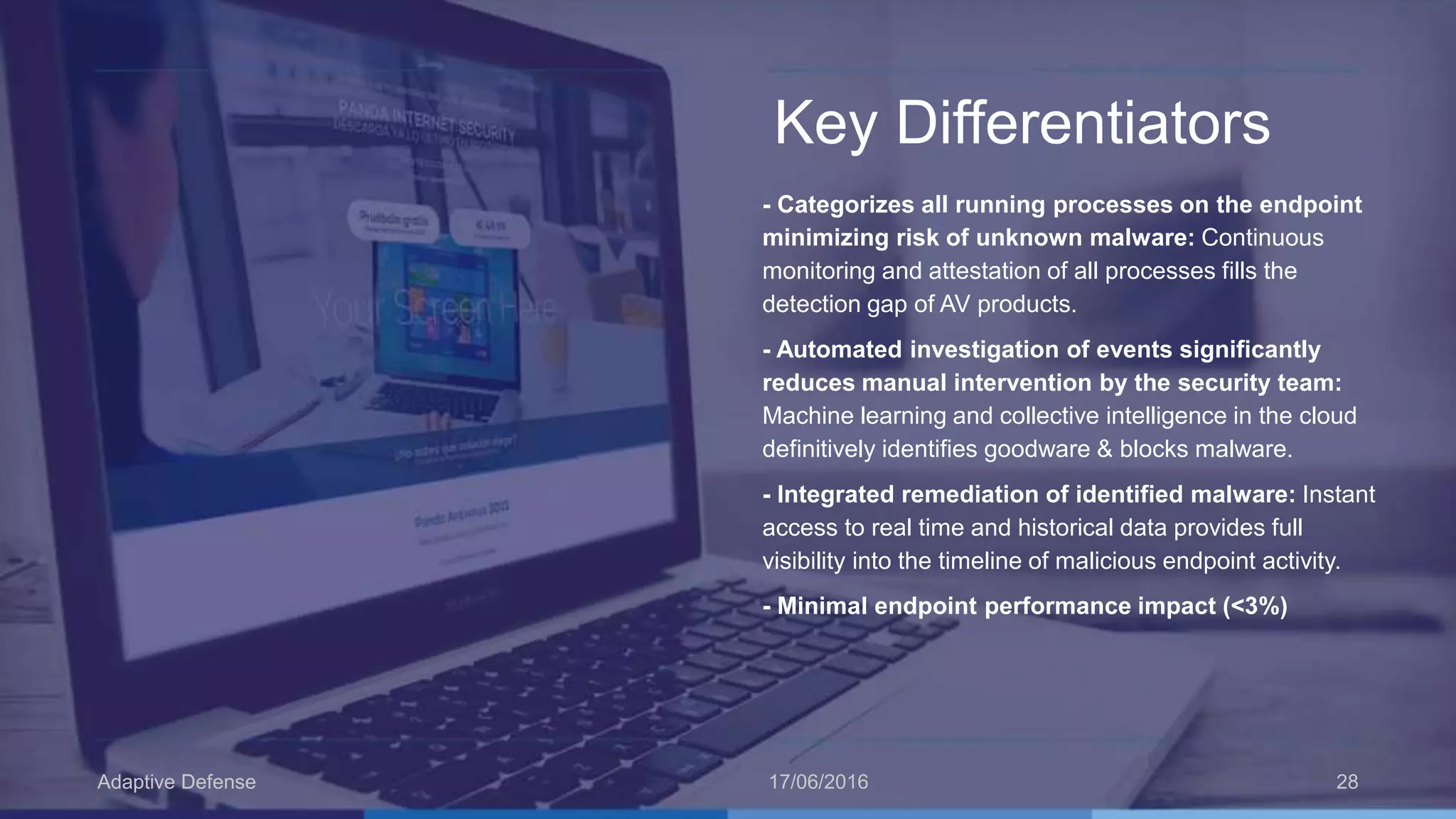
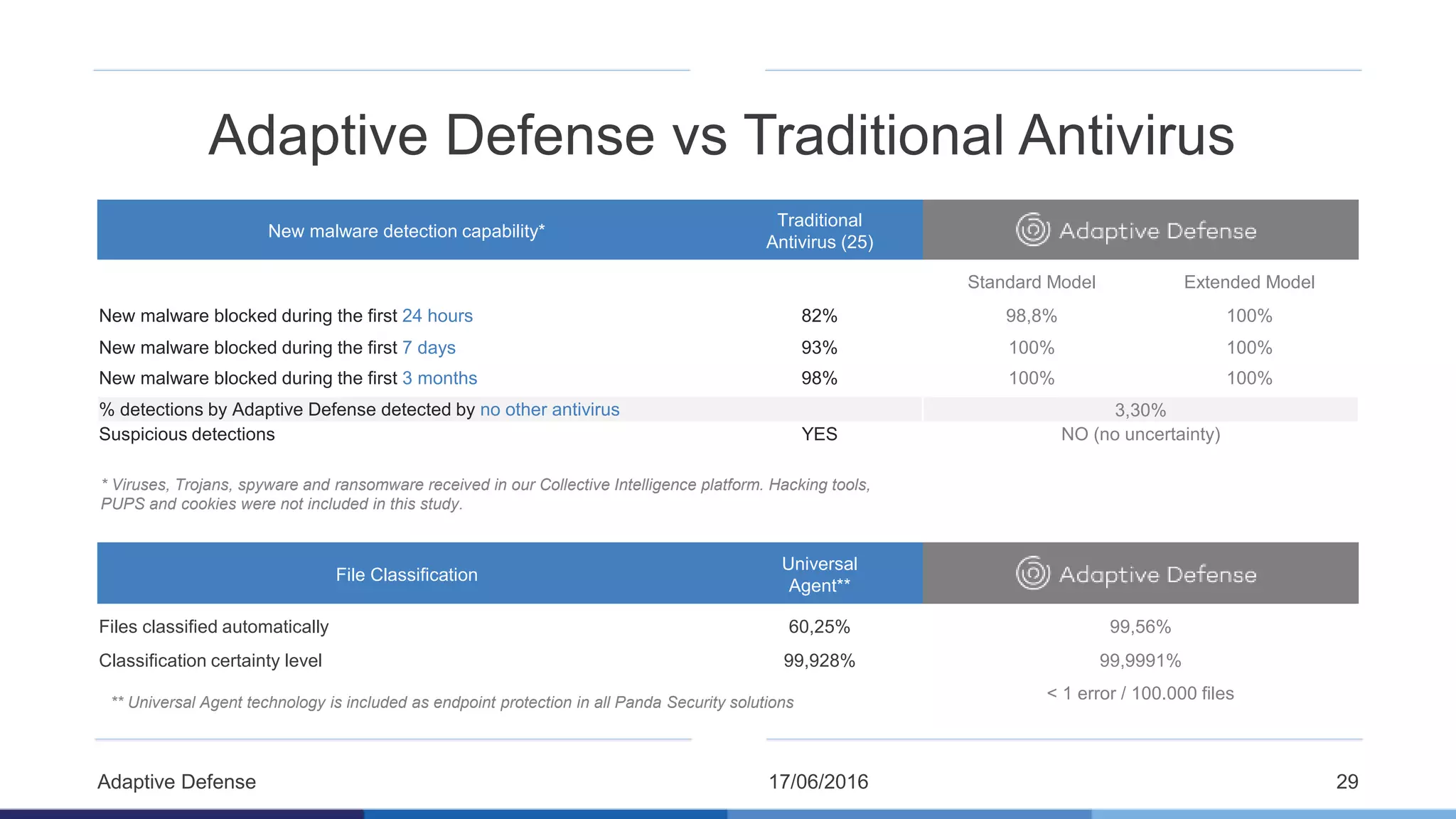
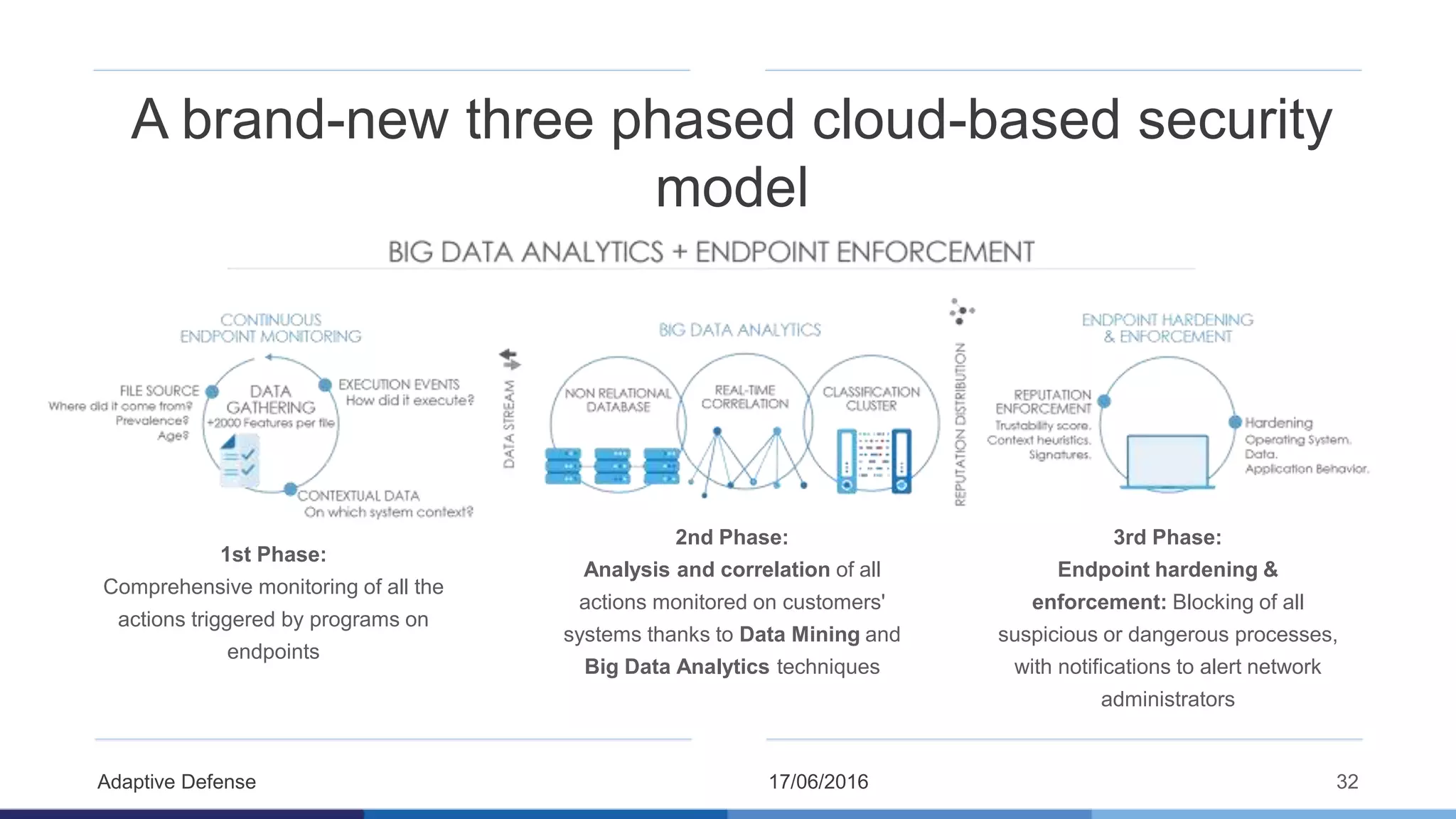
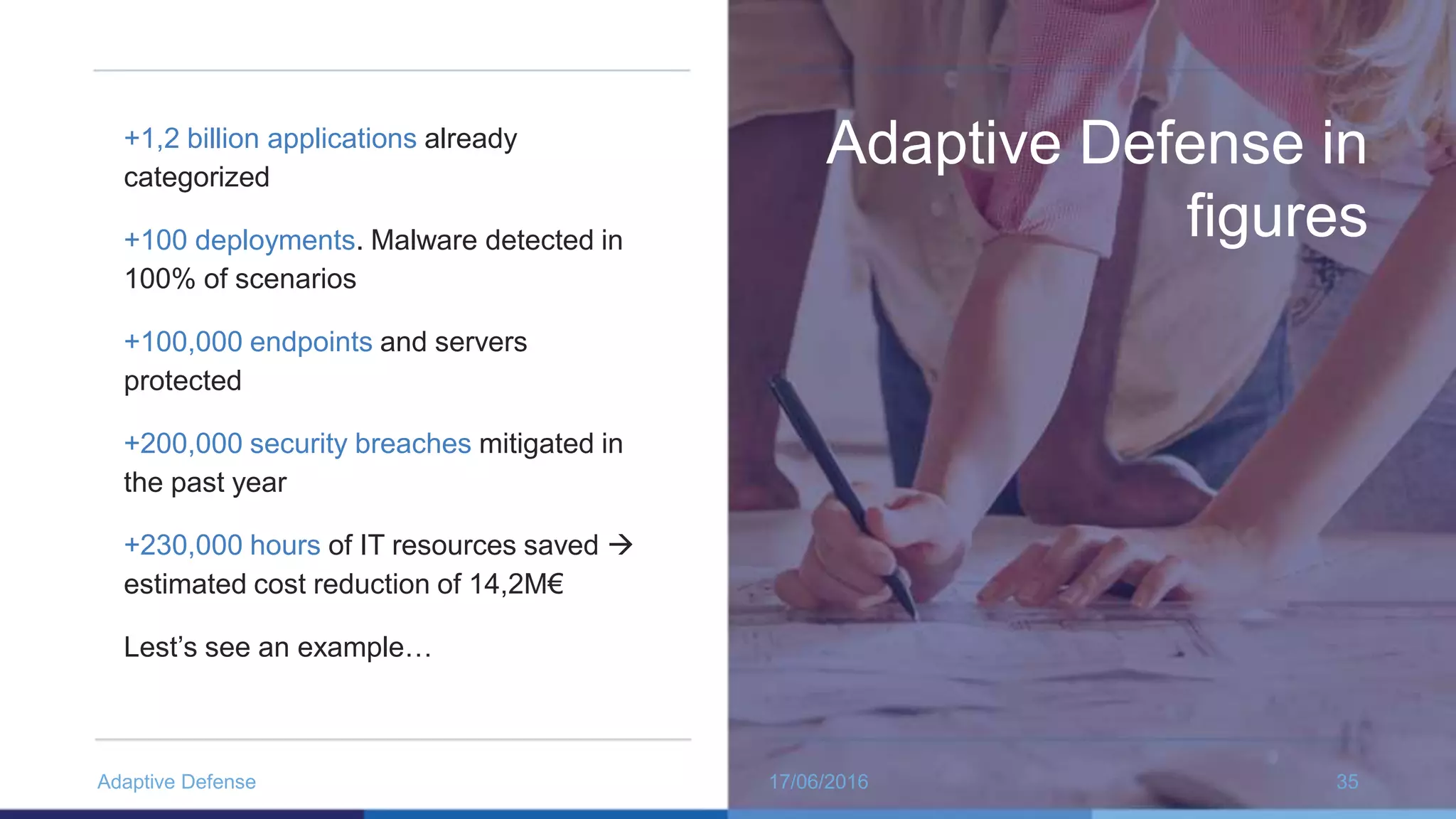
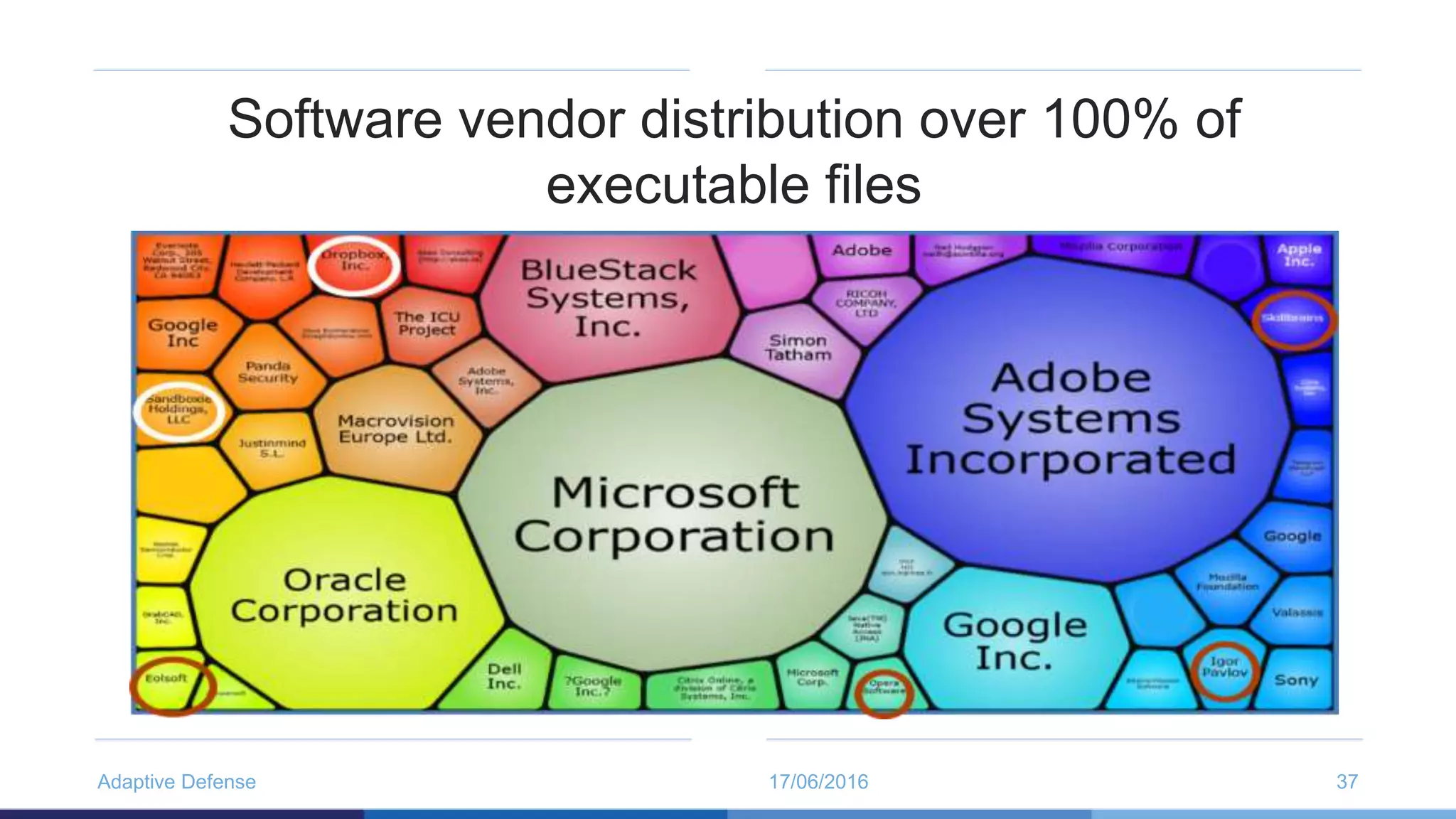
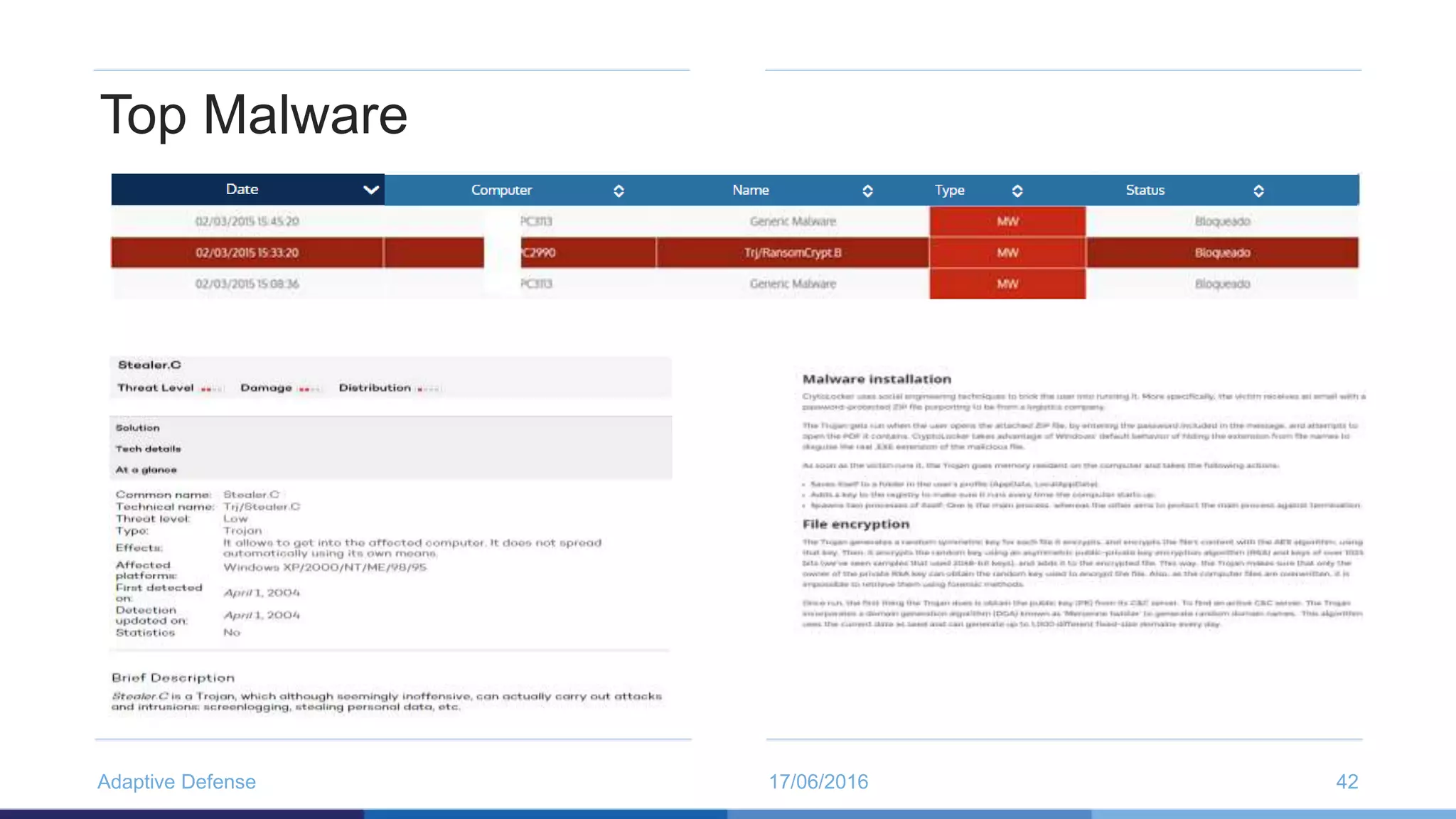
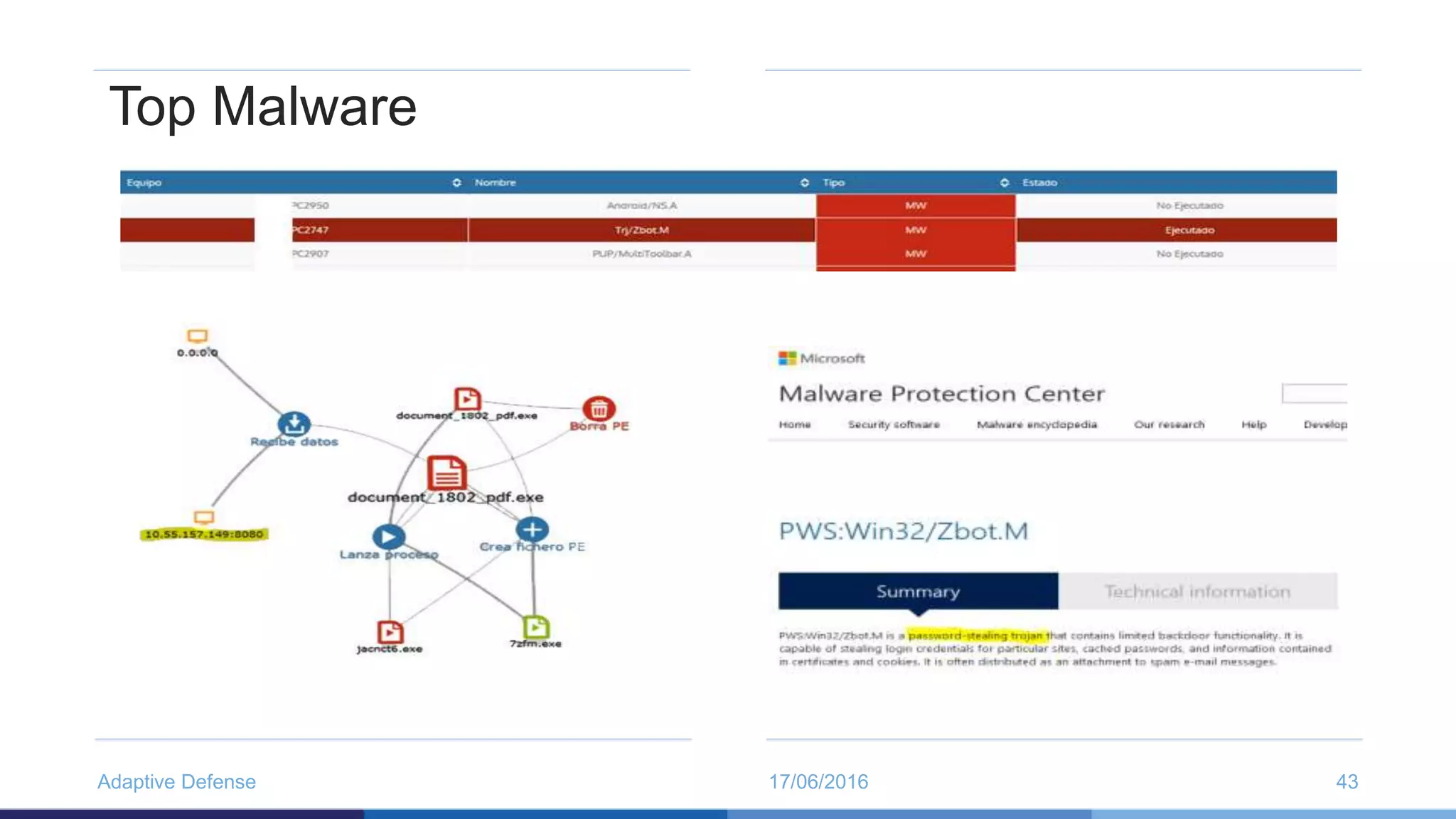
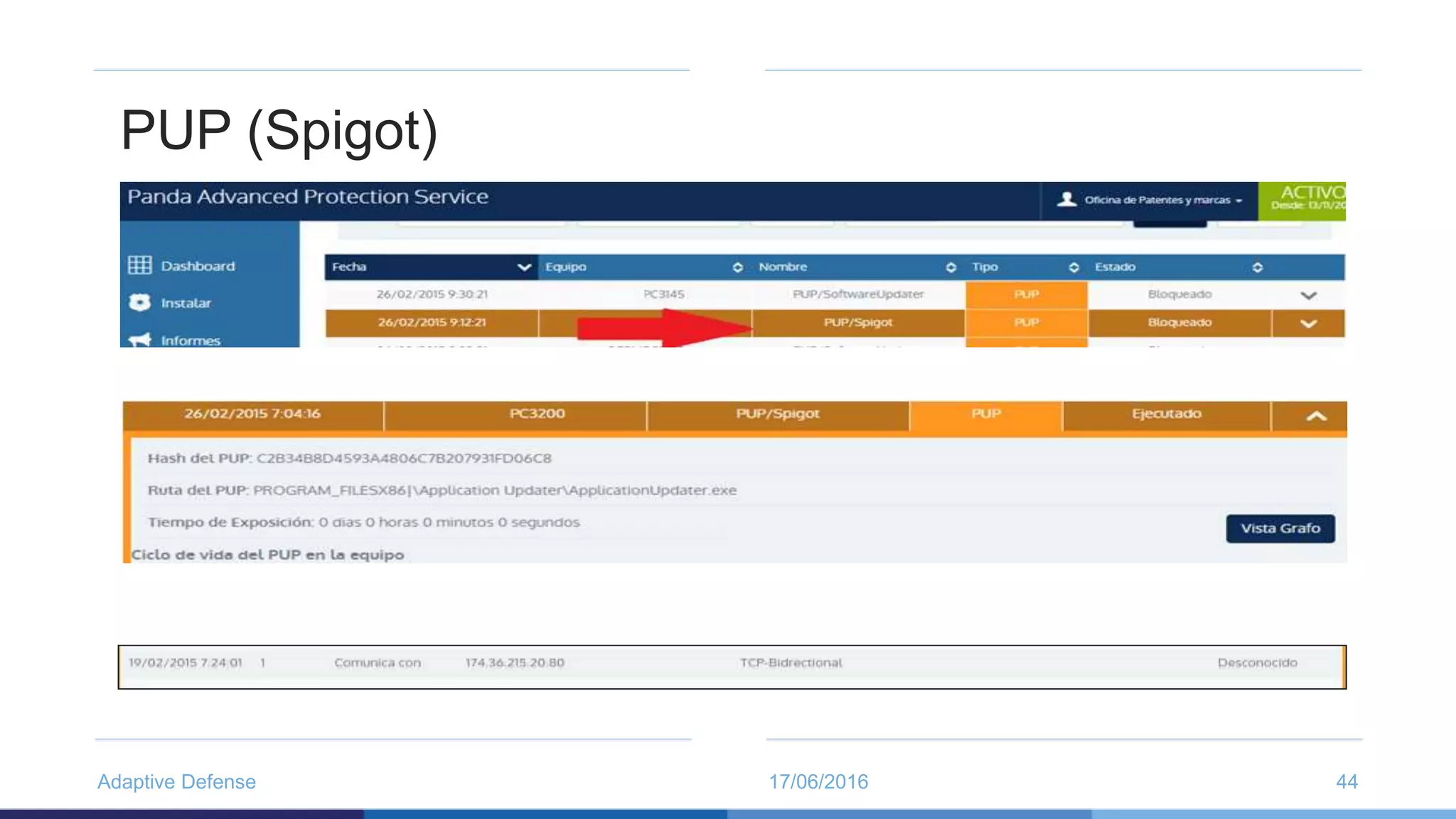
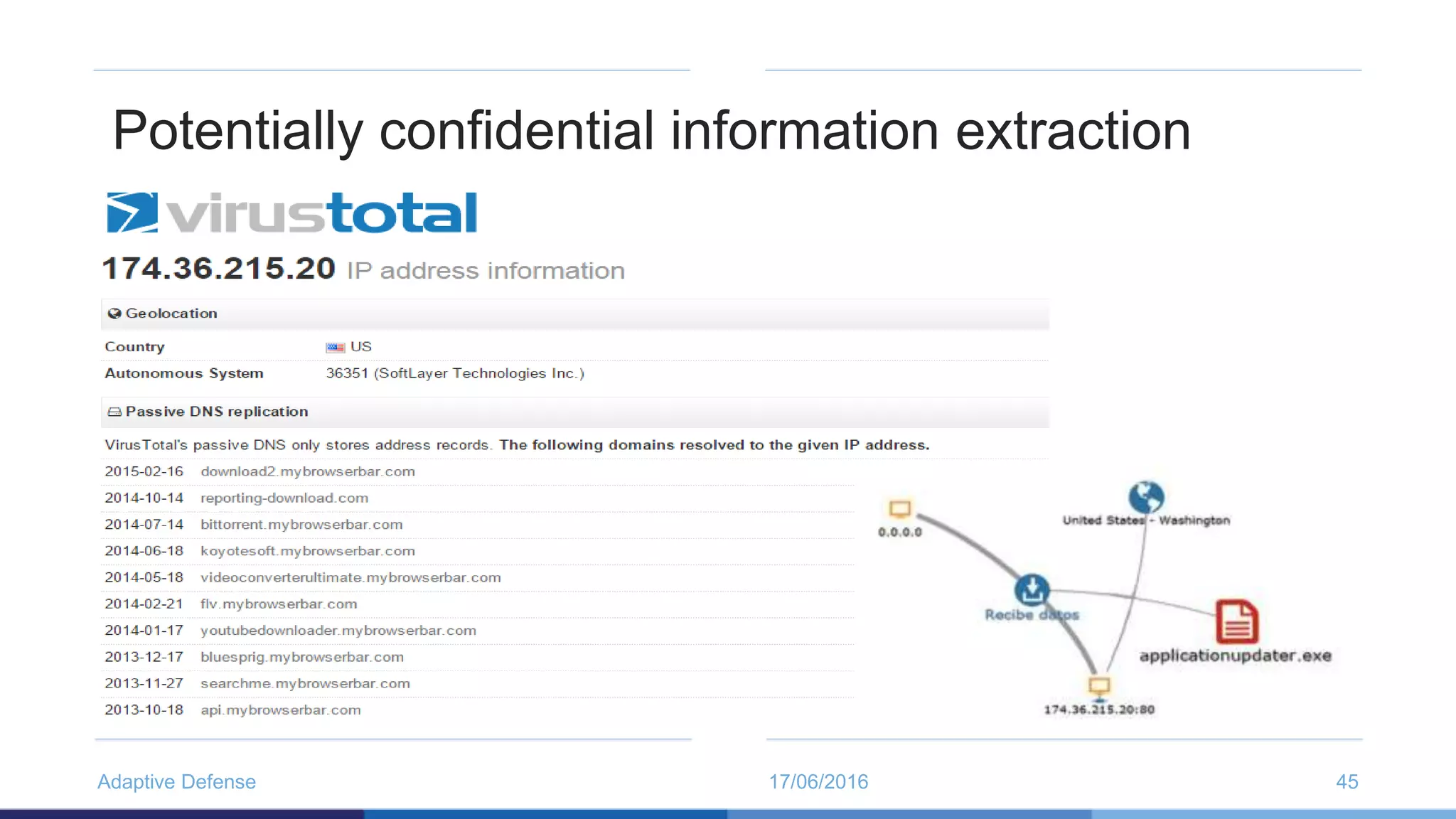
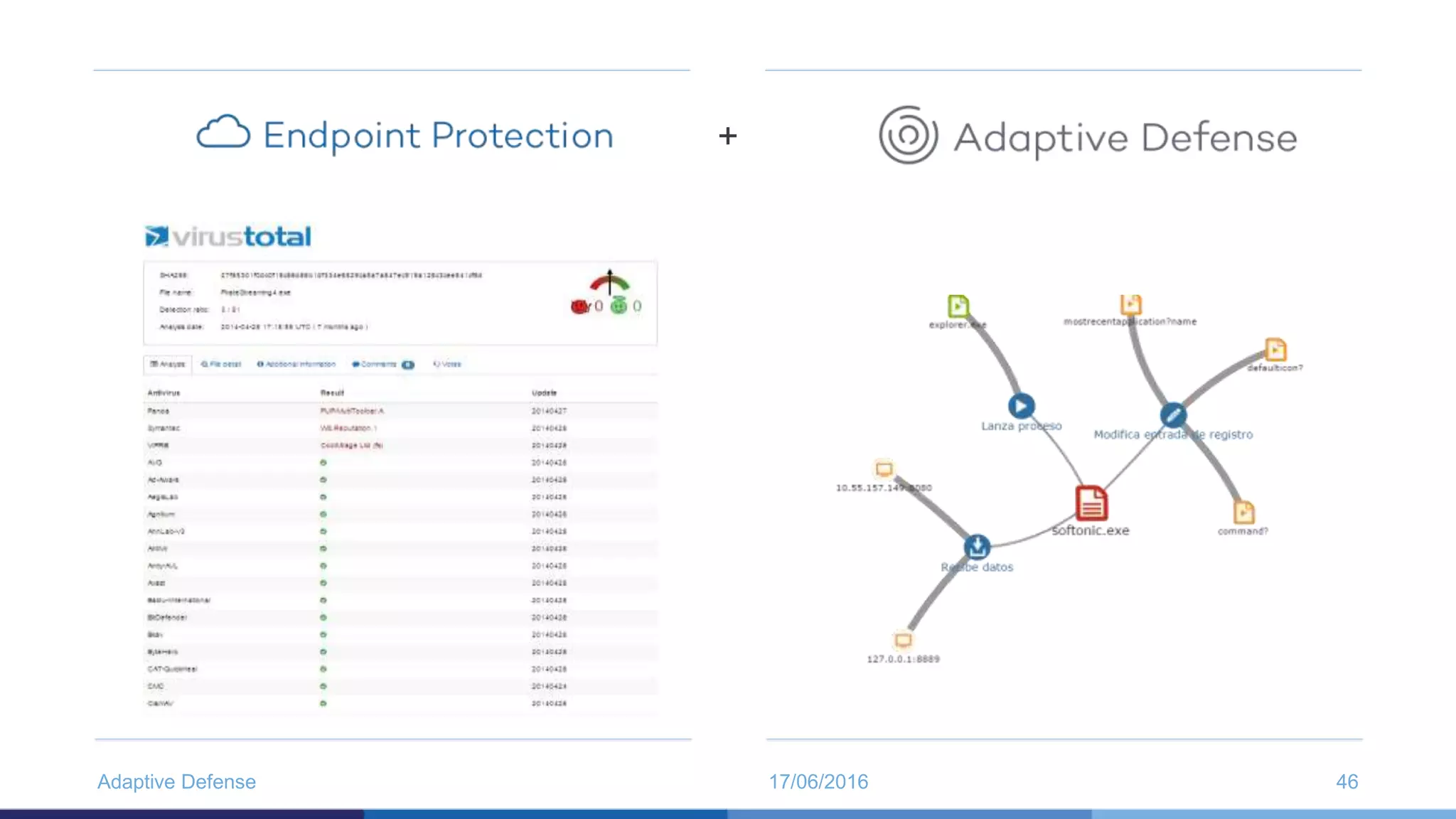
The document discusses the evolution of malware through five distinct eras, highlighting the increasing complexity and motivations behind cyber threats, including economic benefits and professionalization of attacks. It also introduces Panda Adaptive Defense, a next-generation endpoint protection that uses big data and machine learning to classify all running processes, enabling real-time detection and blocking of malware. The effectiveness of Adaptive Defense is demonstrated through impressive statistics on malware detection and successful mitigation of security breaches.