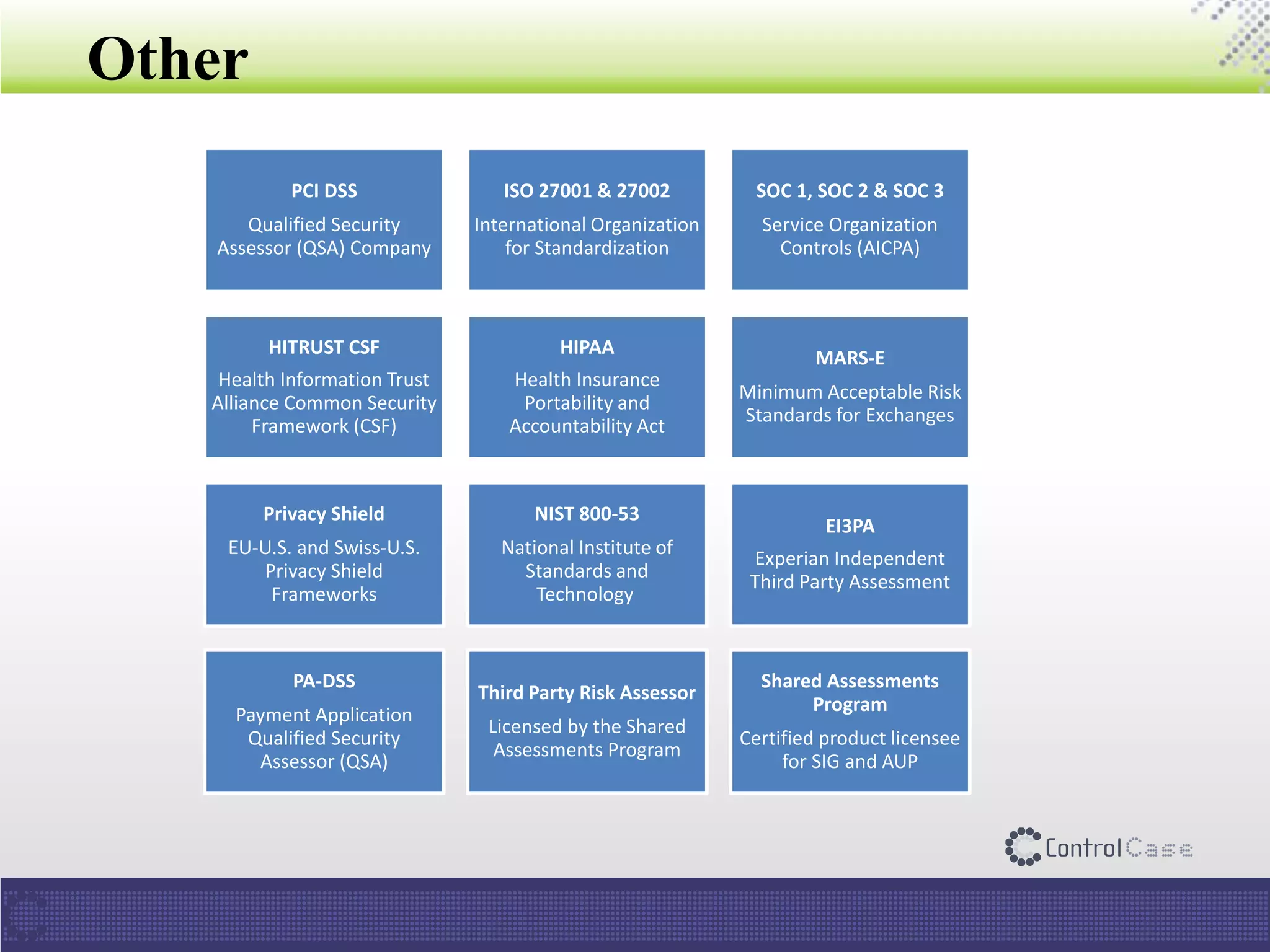
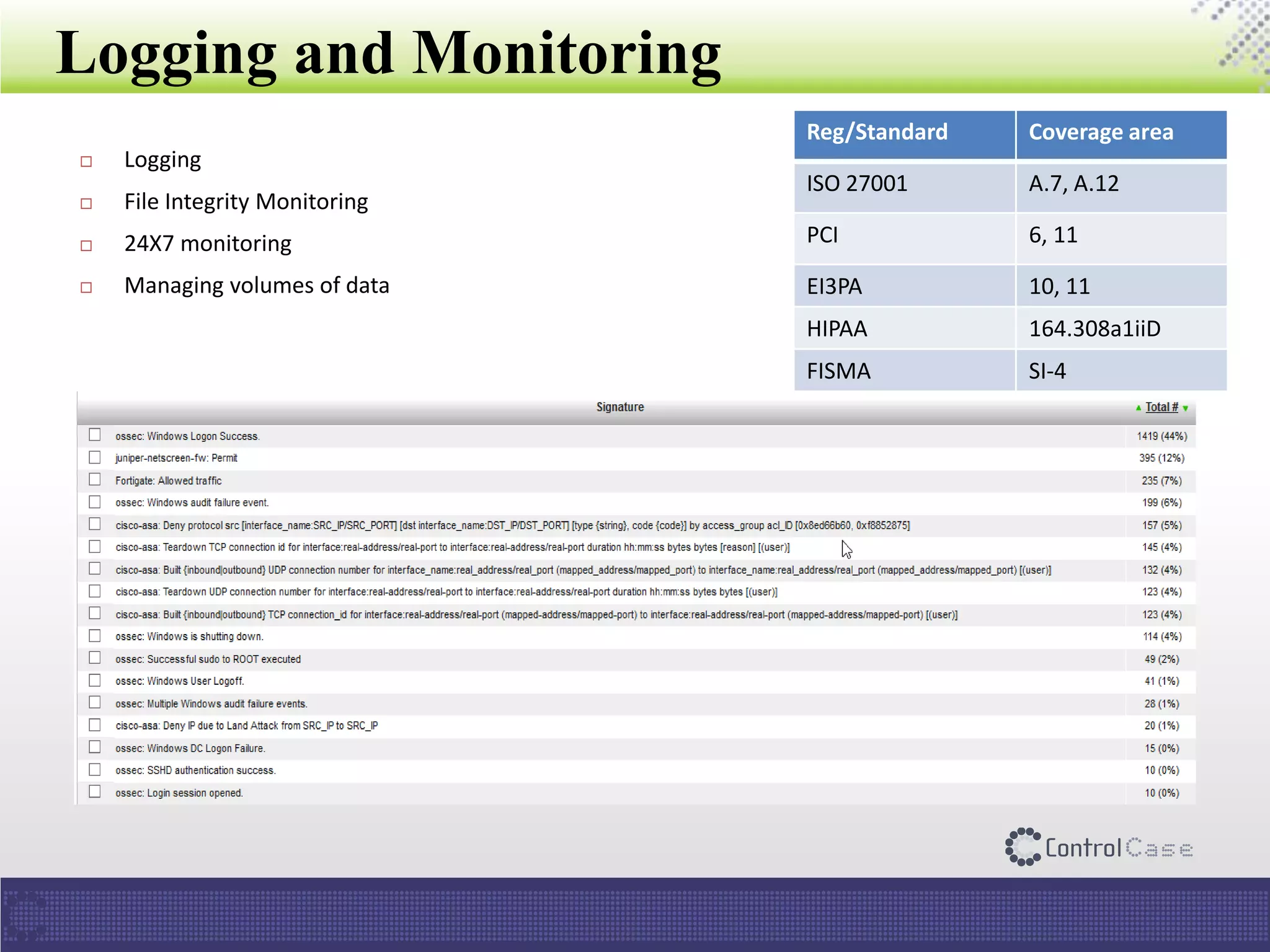
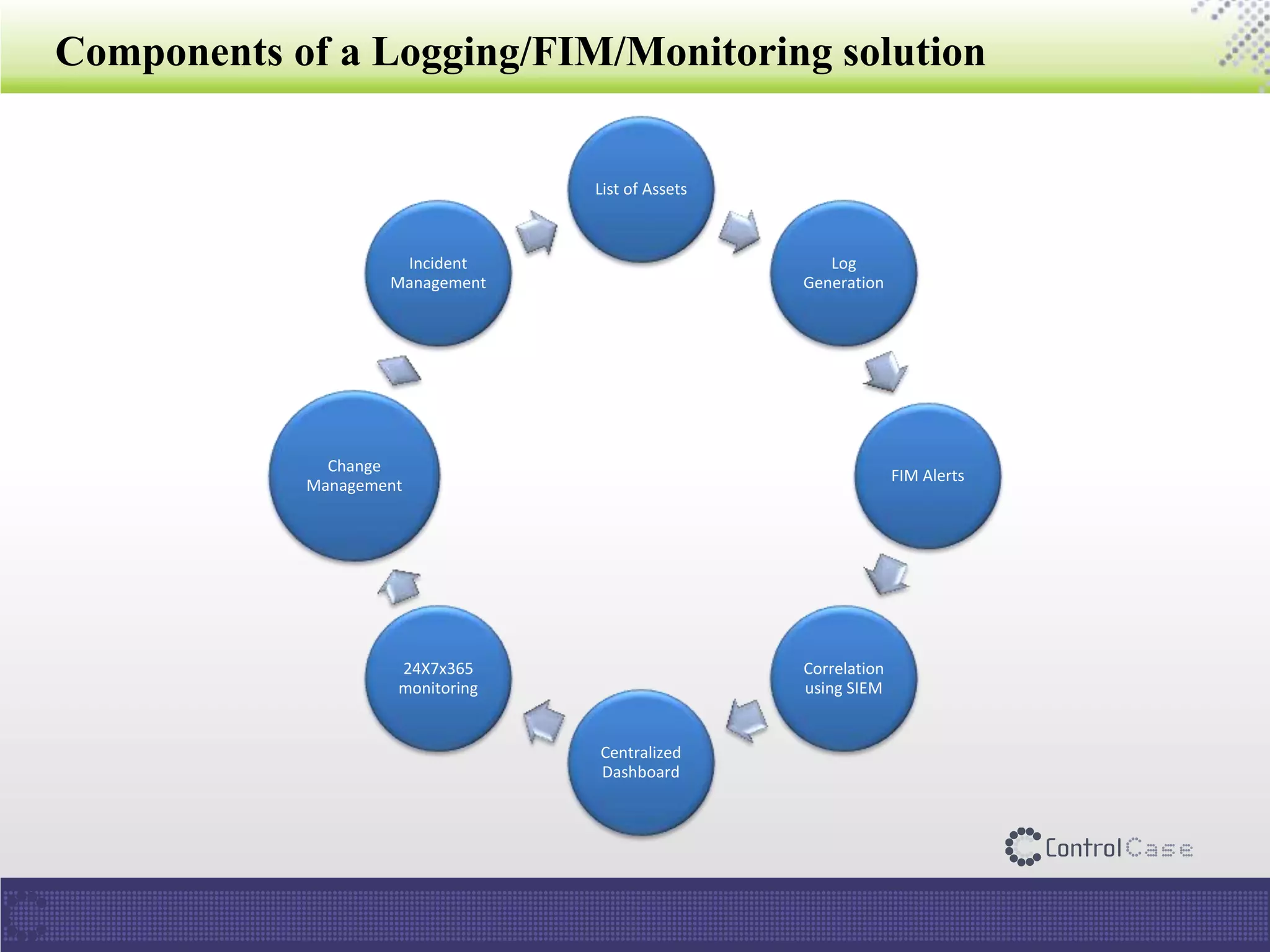
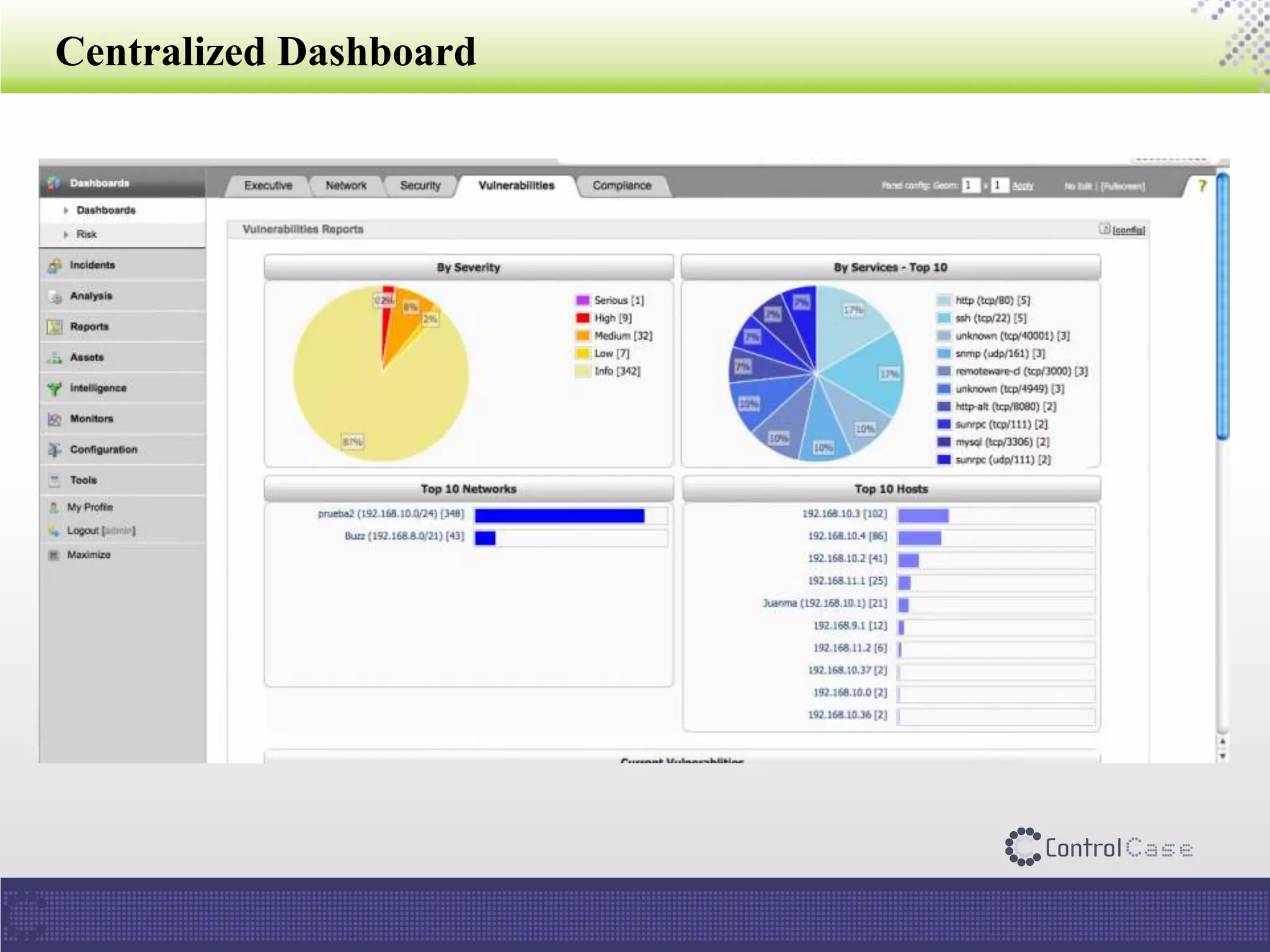
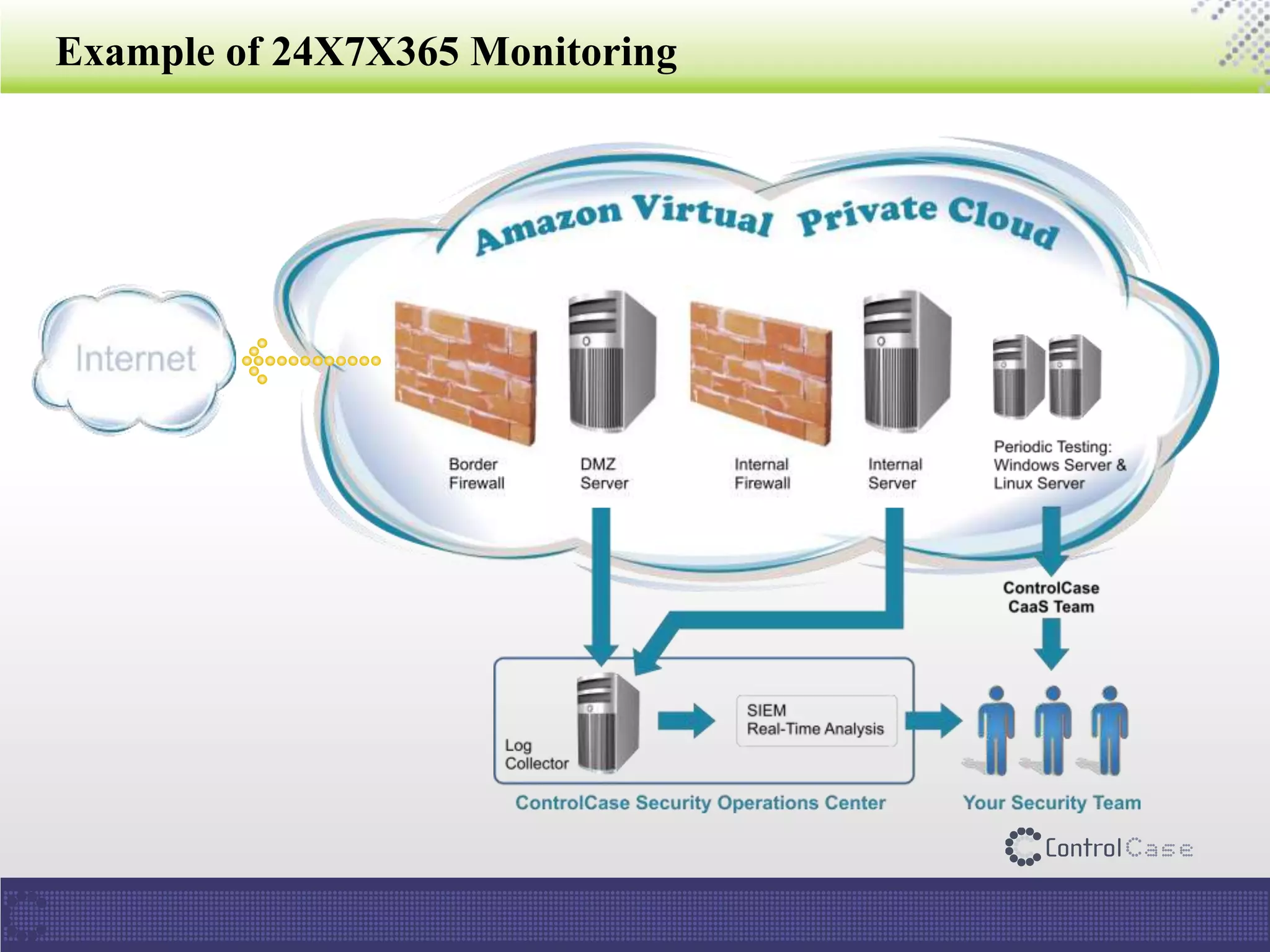
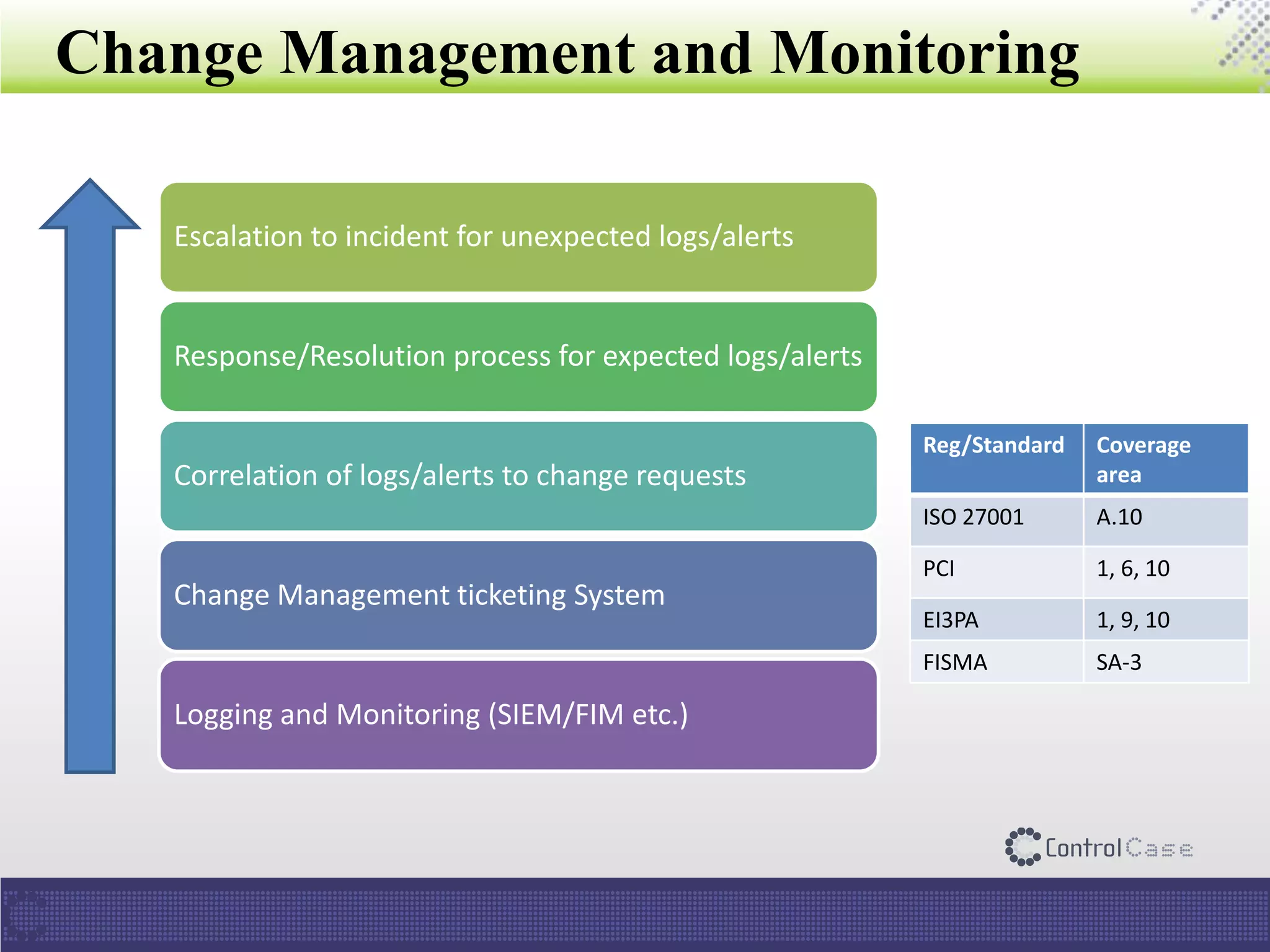
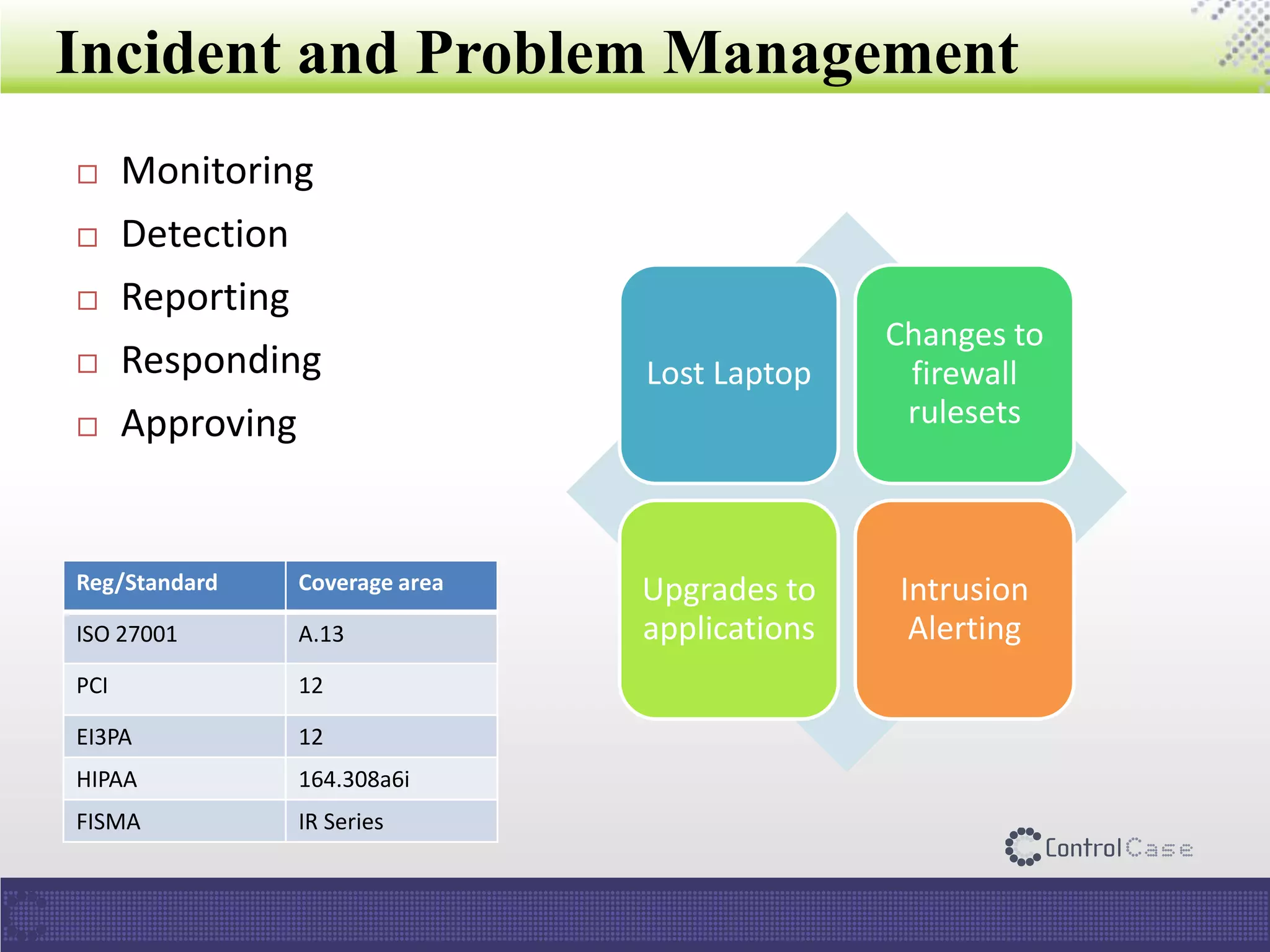
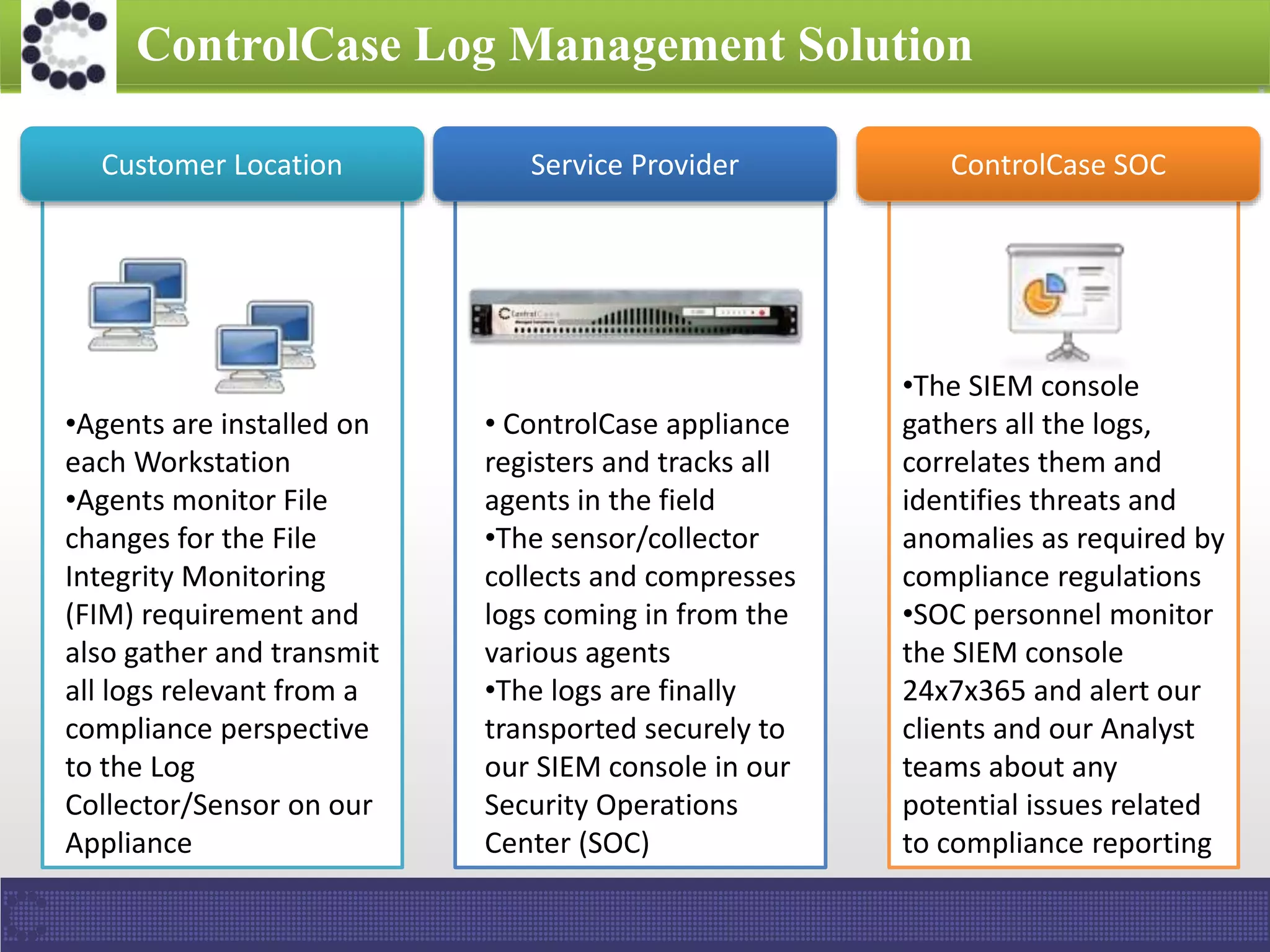
The document presents an overview of ControlCase, a compliance service provider specializing in various standards like PCI DSS, ISO 27001, HIPAA, FISMA, and EI3PA. It details their products and services, challenges in logging and monitoring, and their comprehensive solution for compliance logging. Additionally, it emphasizes ControlCase's global presence and certified resources available for compliance assessment.