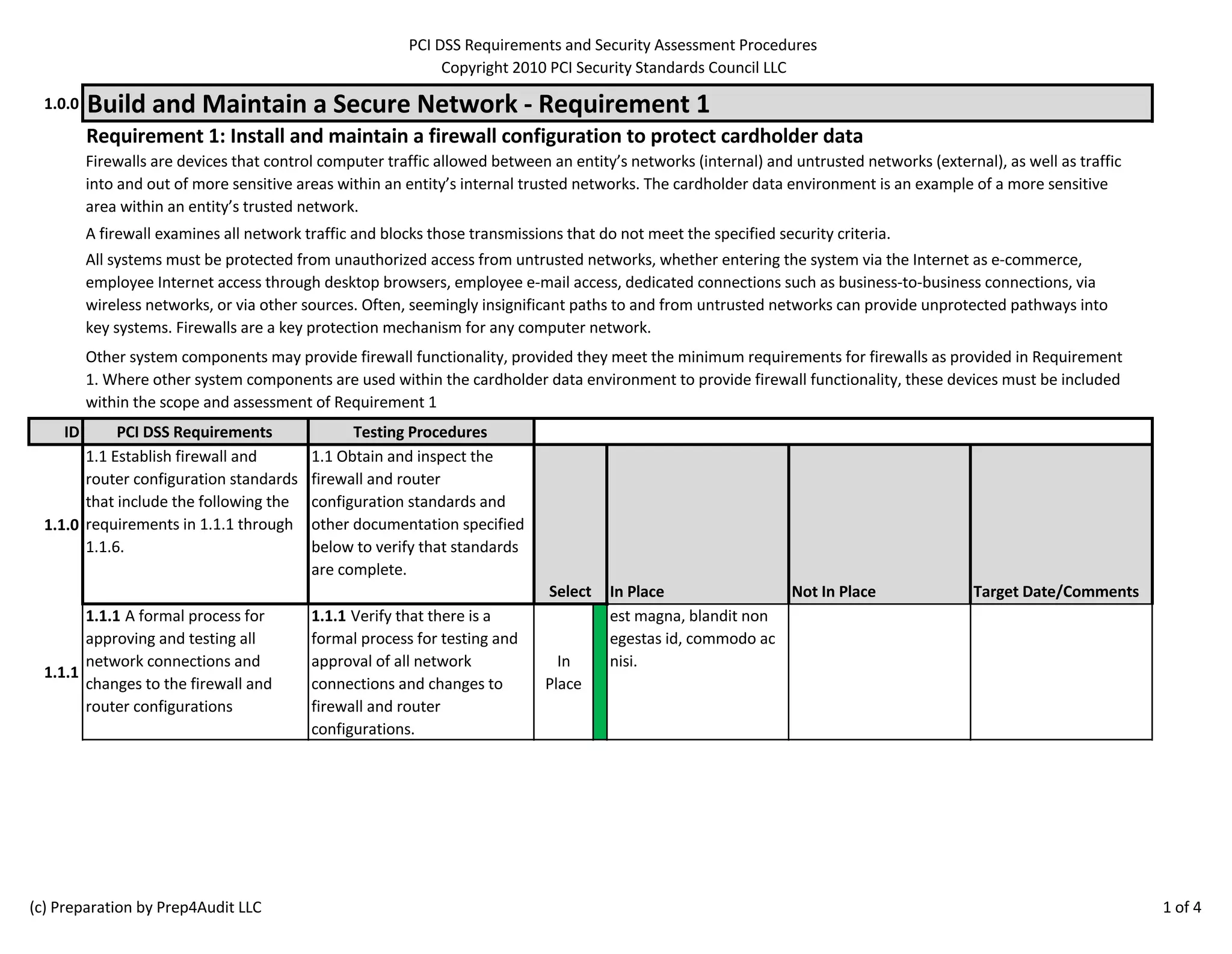
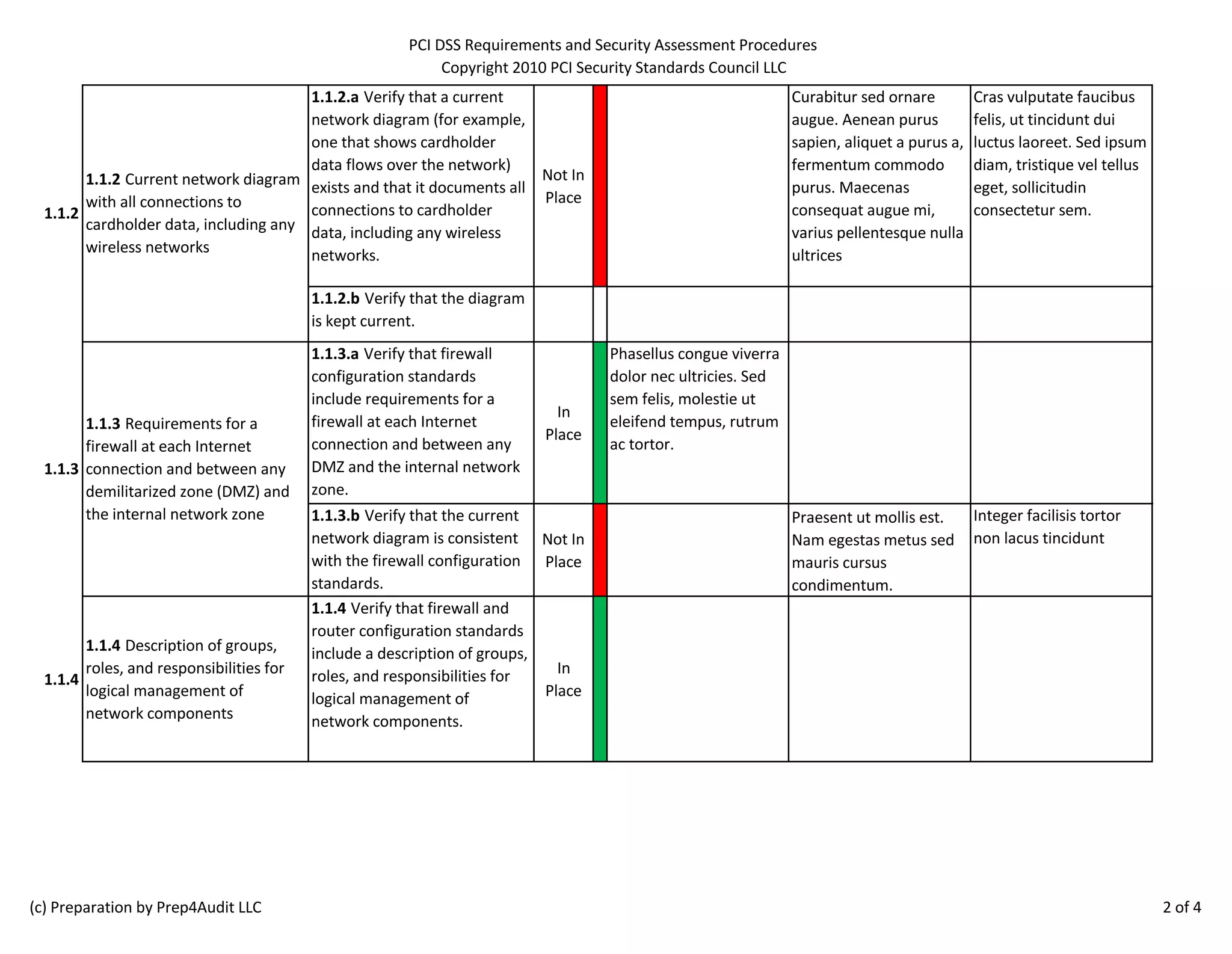
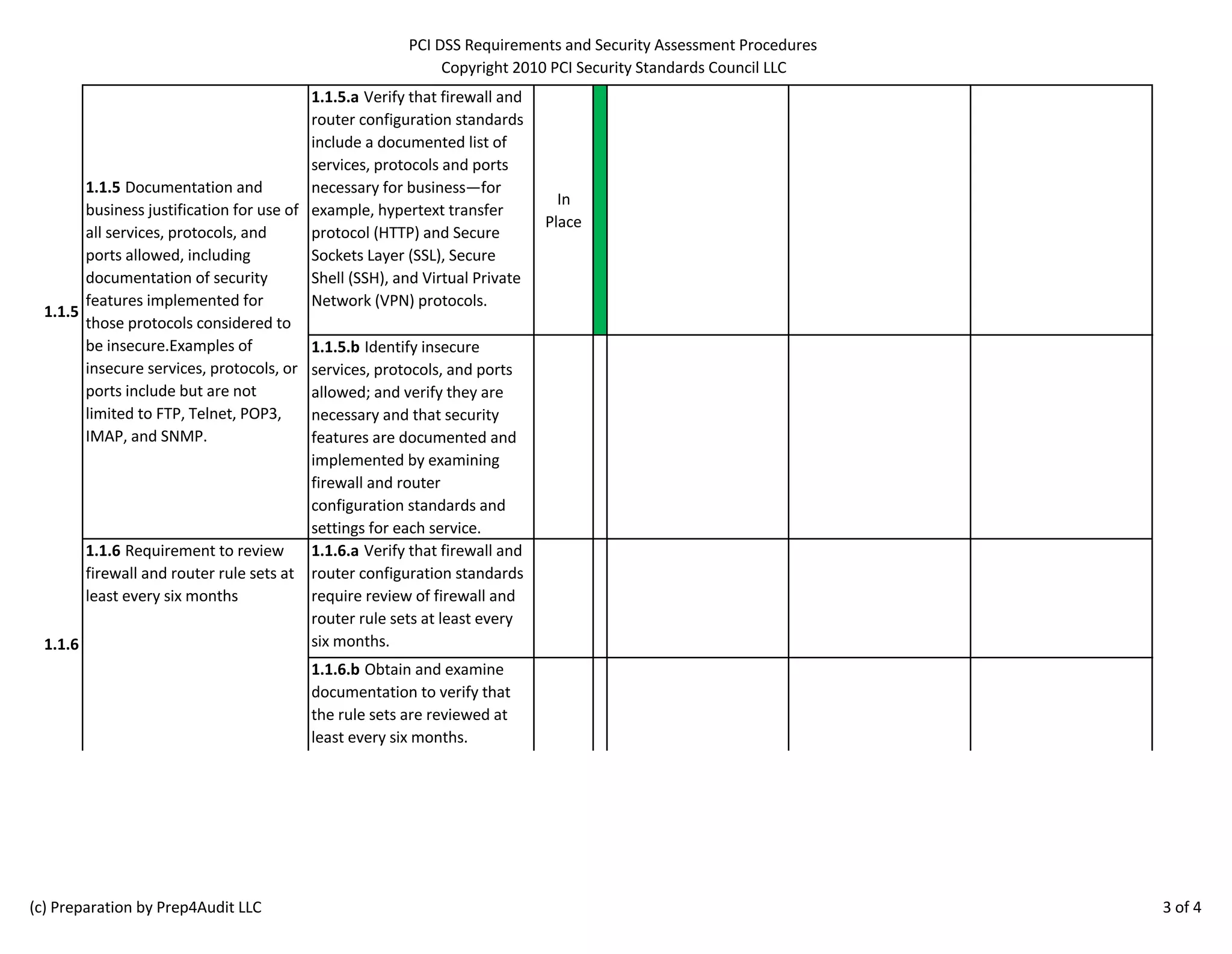
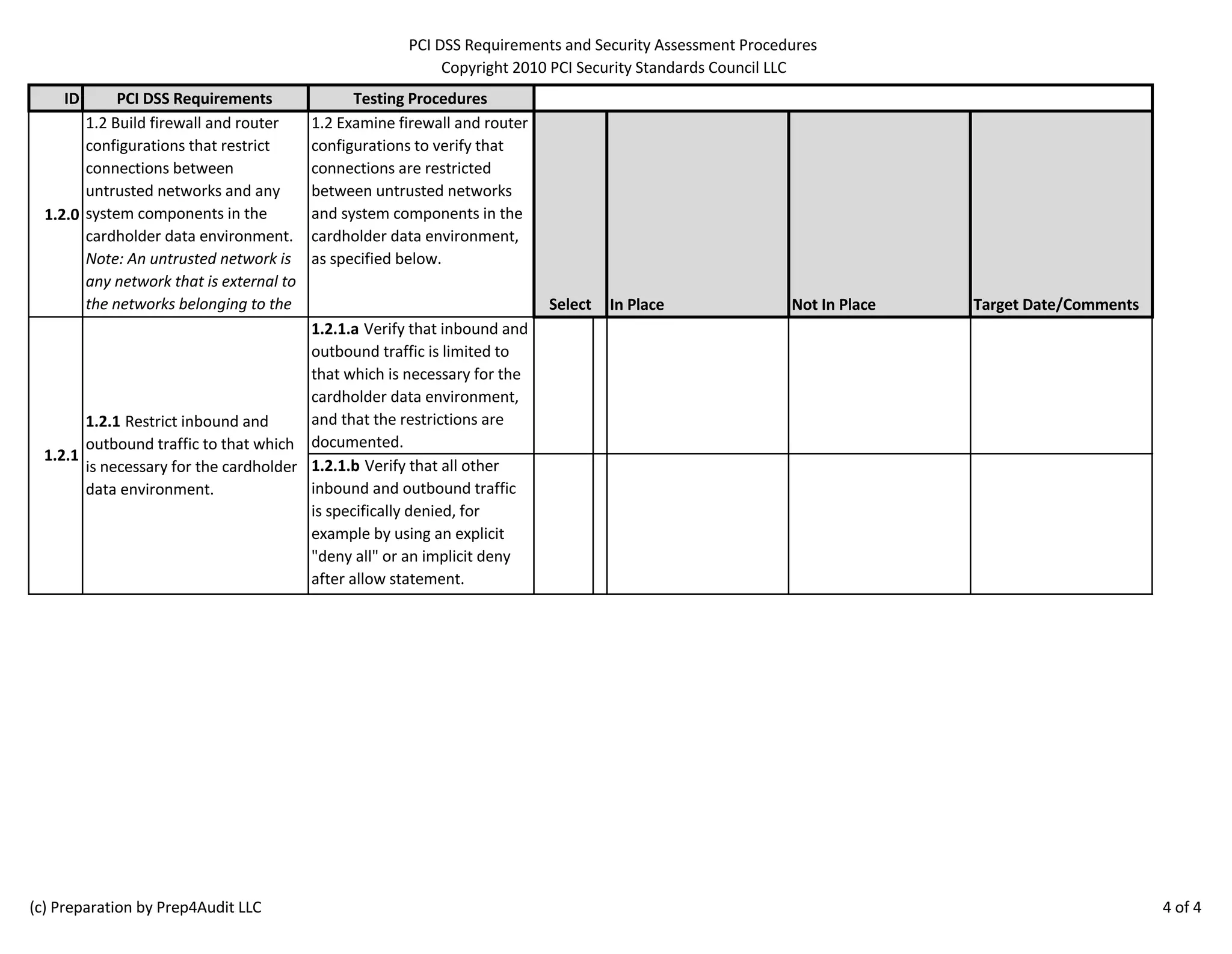
The document outlines the PCI DSS requirements, focusing on the establishment and maintenance of secure network configurations to protect cardholder data. It emphasizes the importance of firewalls in controlling network traffic and includes specific procedures for testing firewall and router configurations to ensure compliance. Key requirements include documenting security standards, maintaining current network diagrams, and regularly reviewing firewall rules.