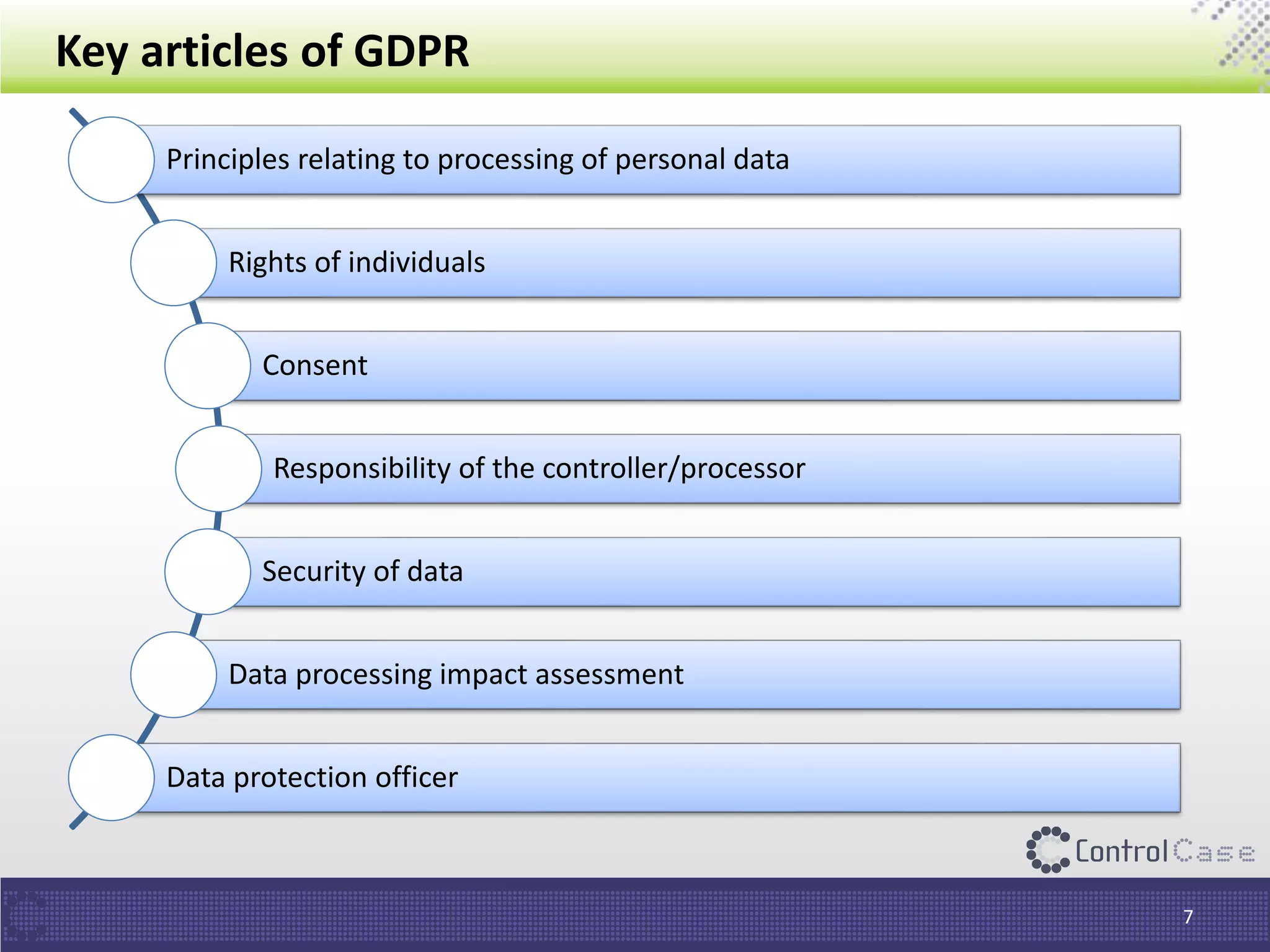
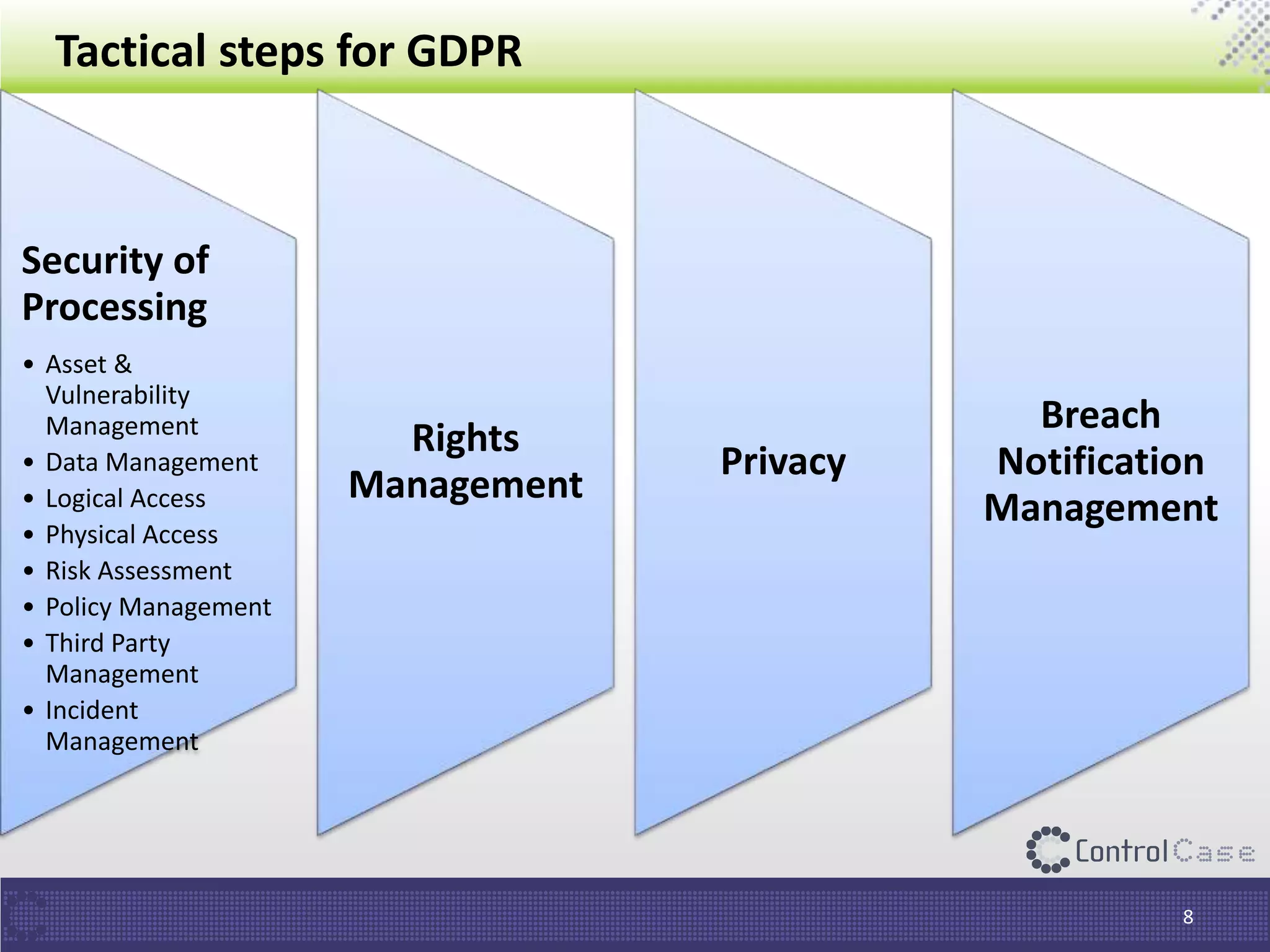
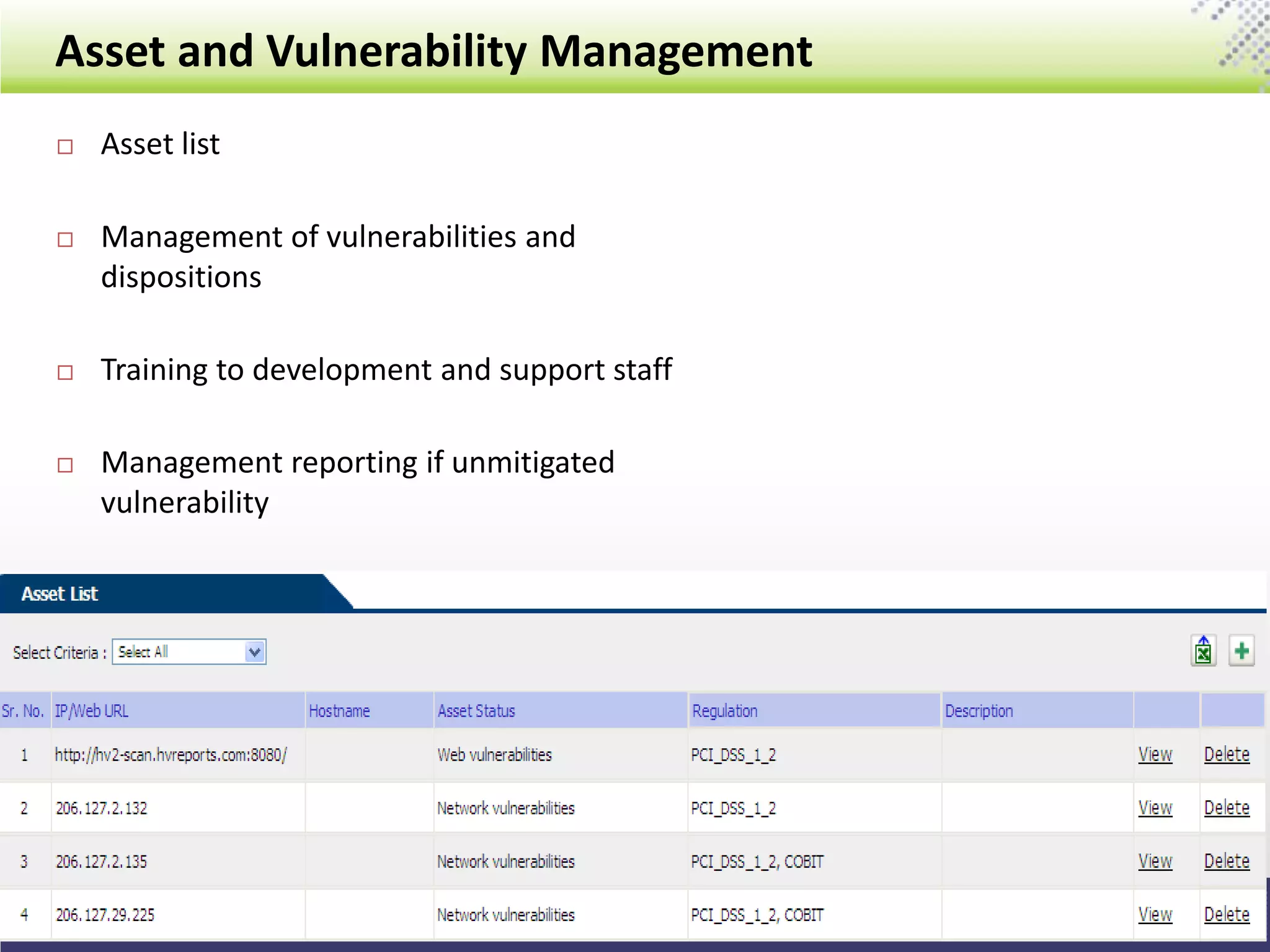
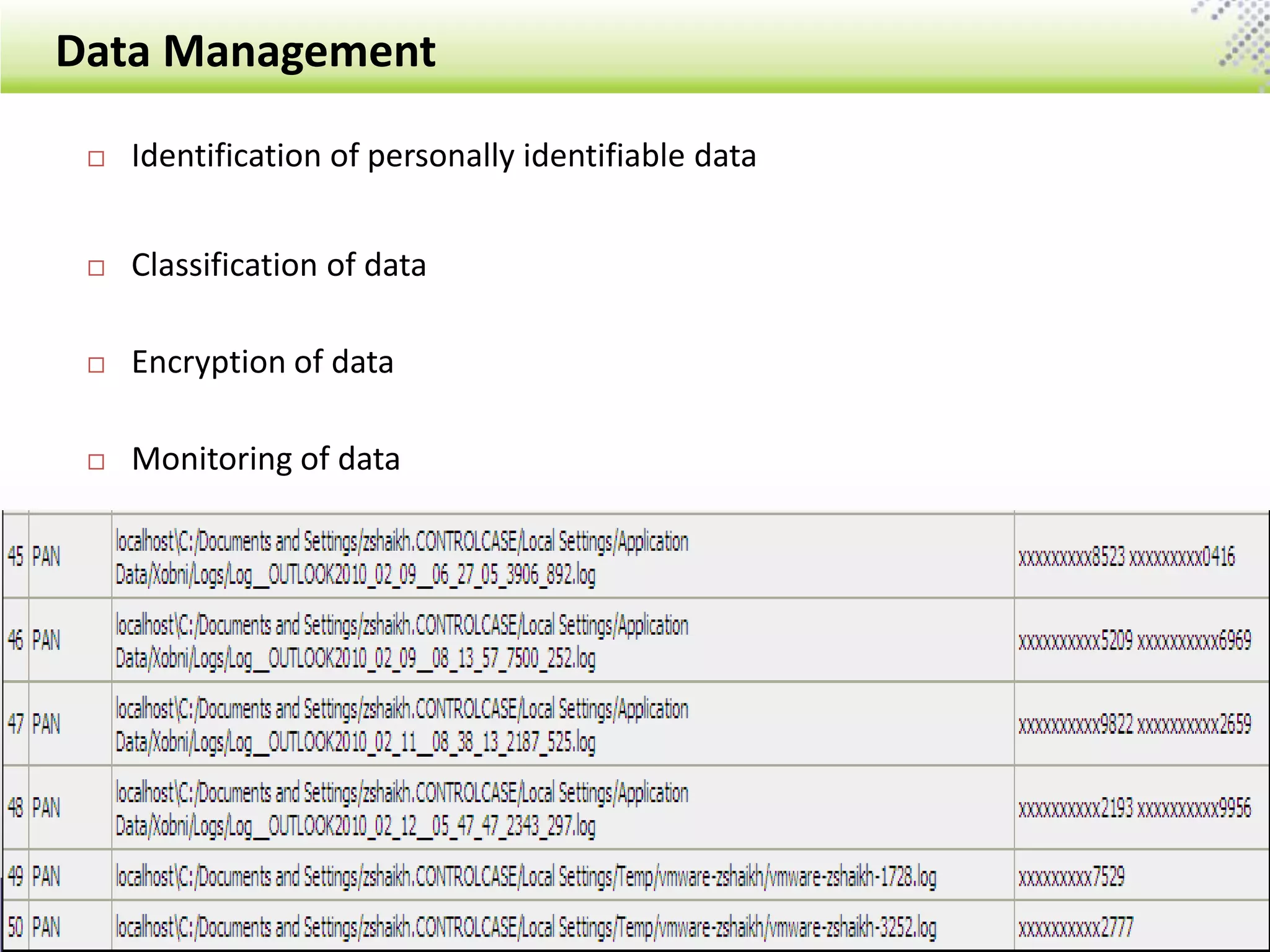
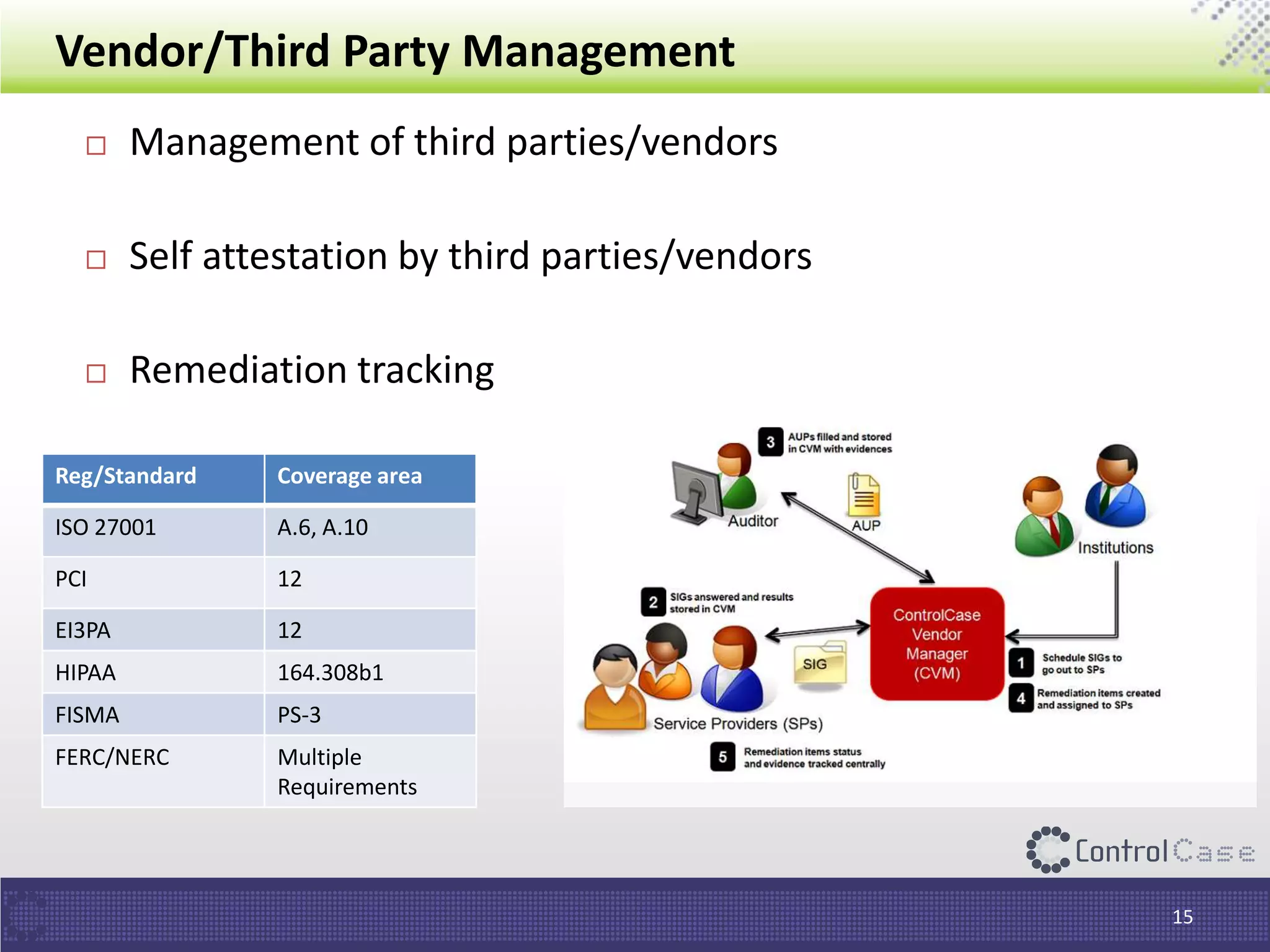
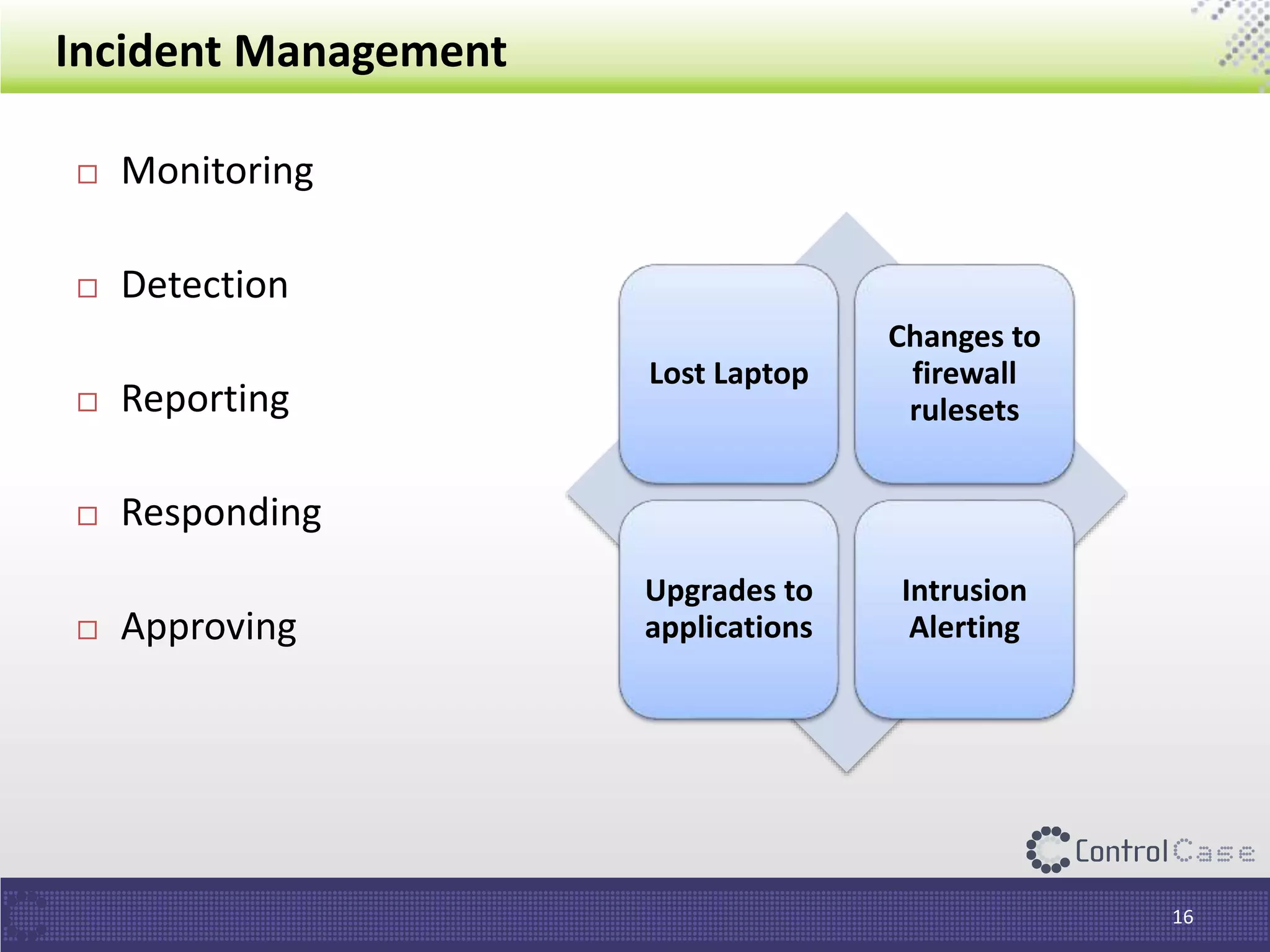
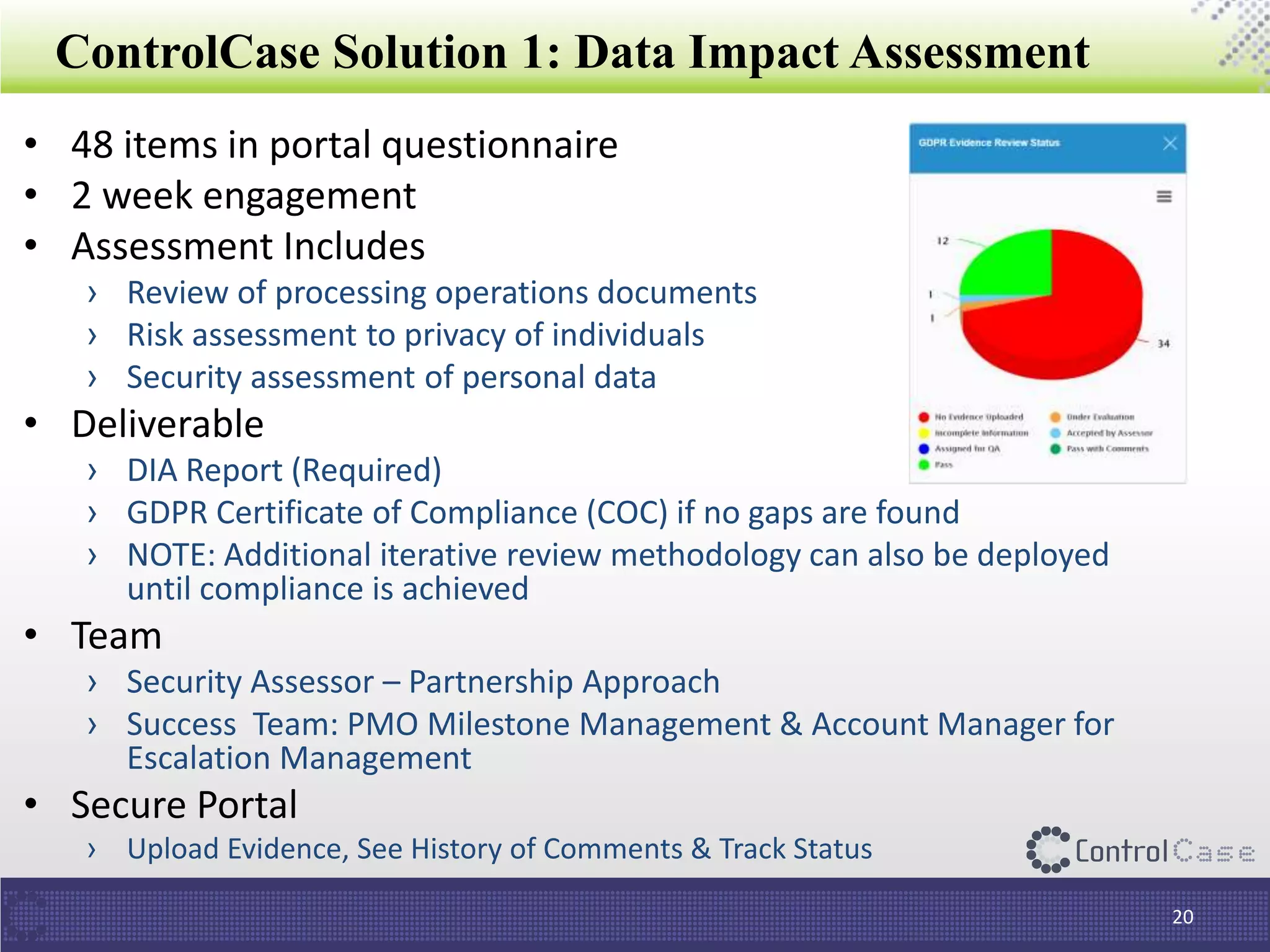
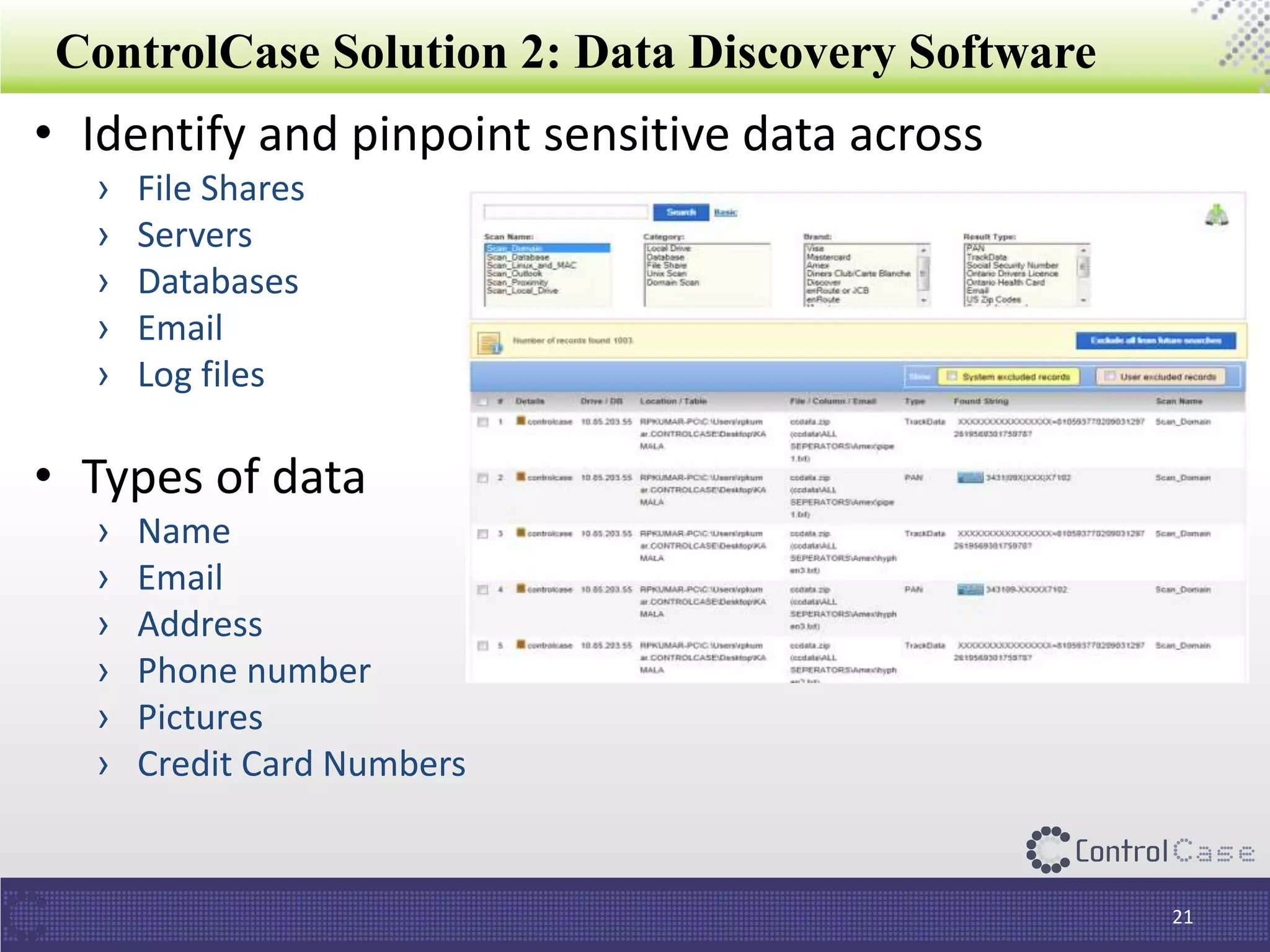
The document outlines the General Data Protection Regulation (GDPR), which standardizes data privacy laws across Europe, detailing the responsibilities of data controllers and processors, implications of non-compliance, and requirements for data impact assessments and appointing data protection officers. It includes tactical compliance steps for data security, privacy management, and breach notification, emphasizing the need for organizations to conduct thorough assessments and manage third-party relationships effectively. ControlCase offers solutions to help organizations meet GDPR compliance with services like data discovery and impact assessments.