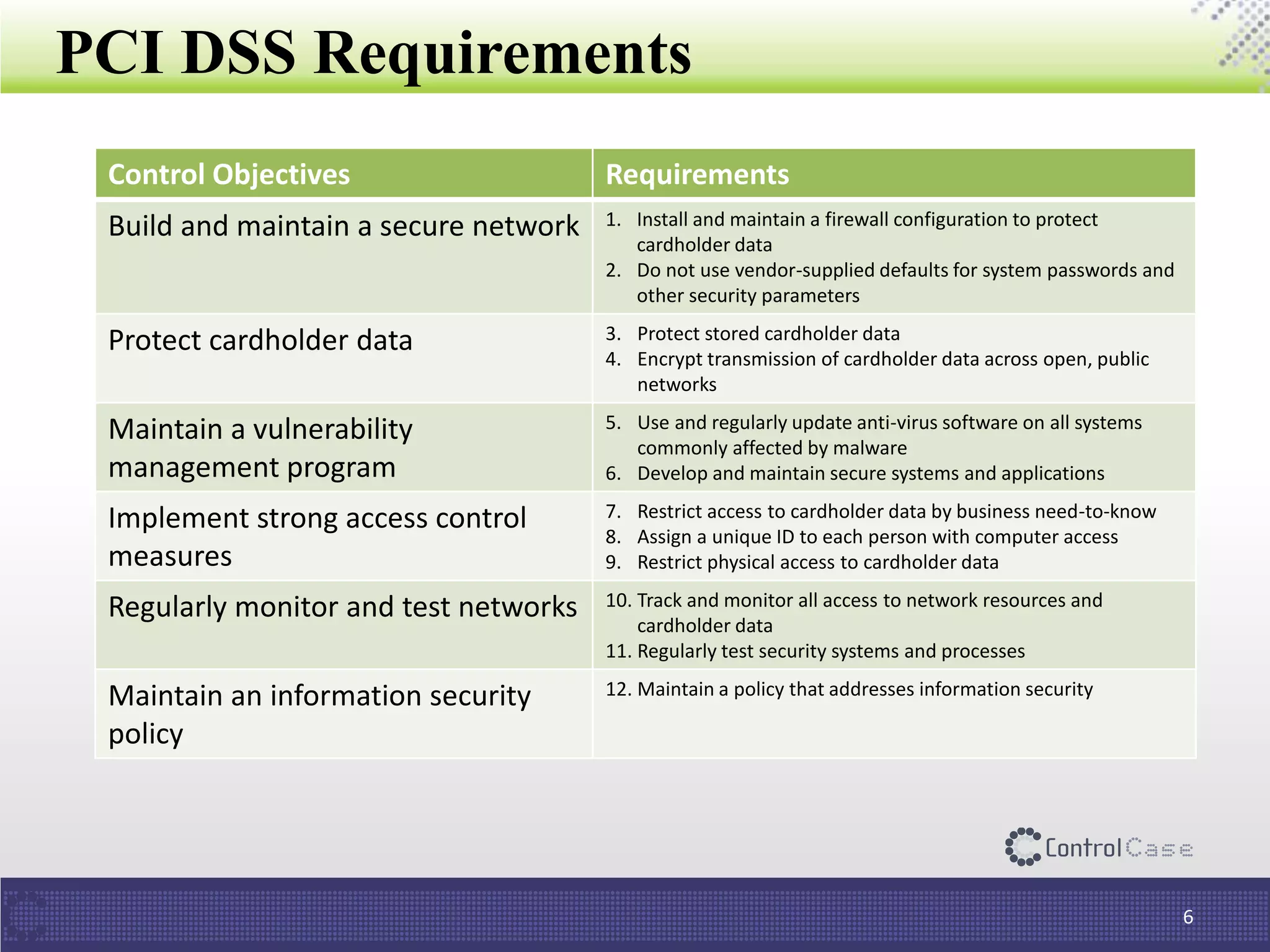
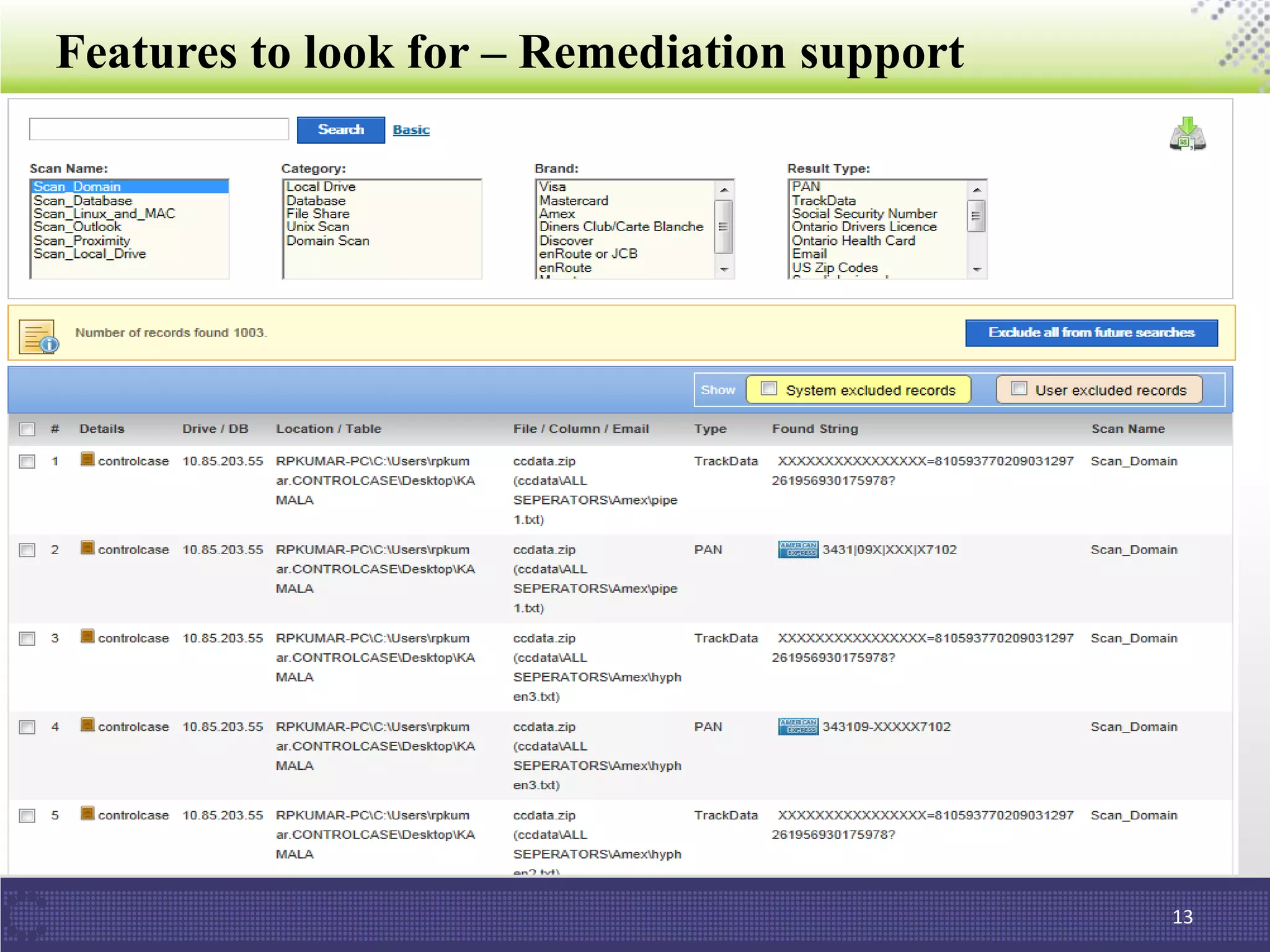
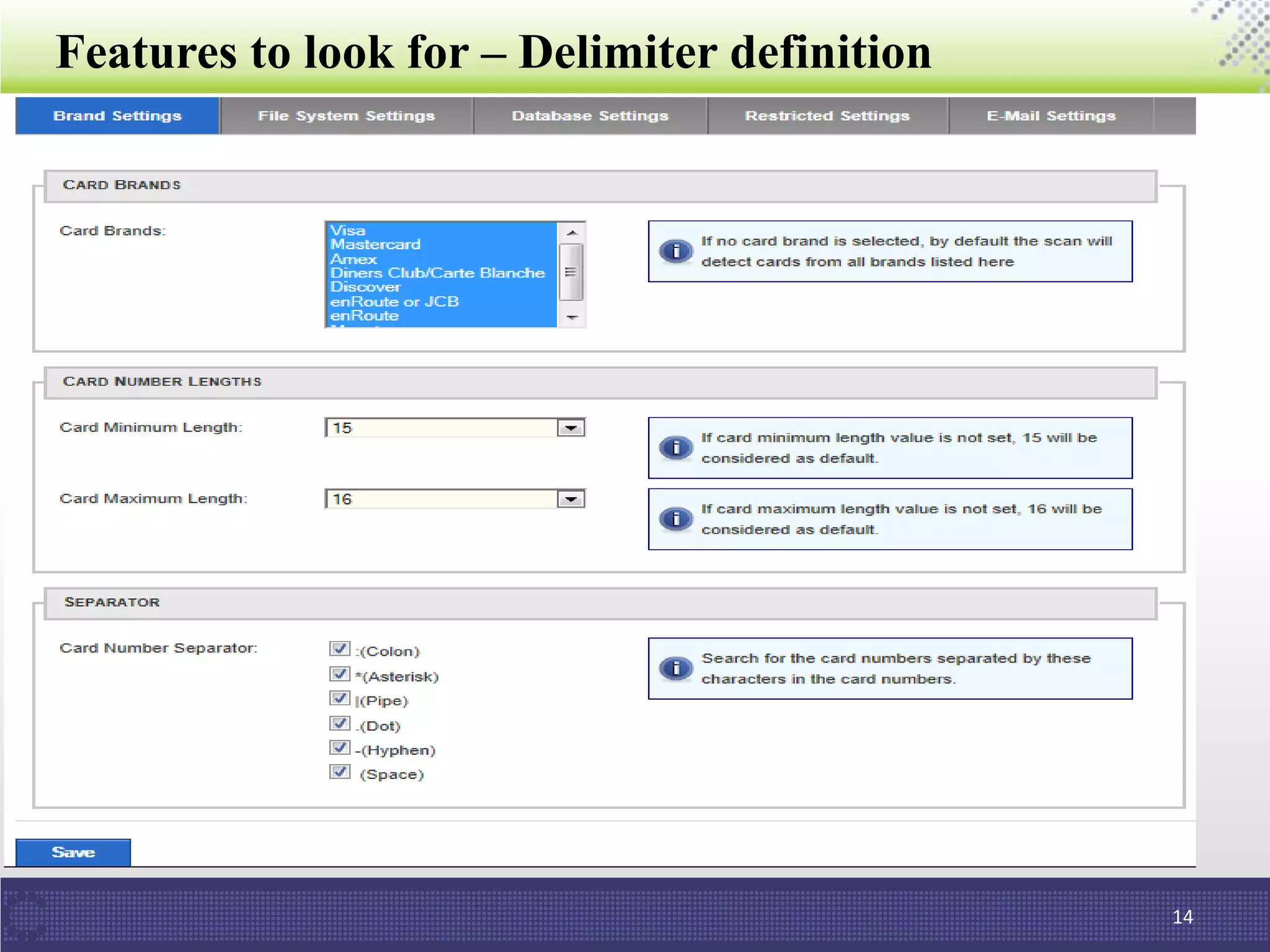
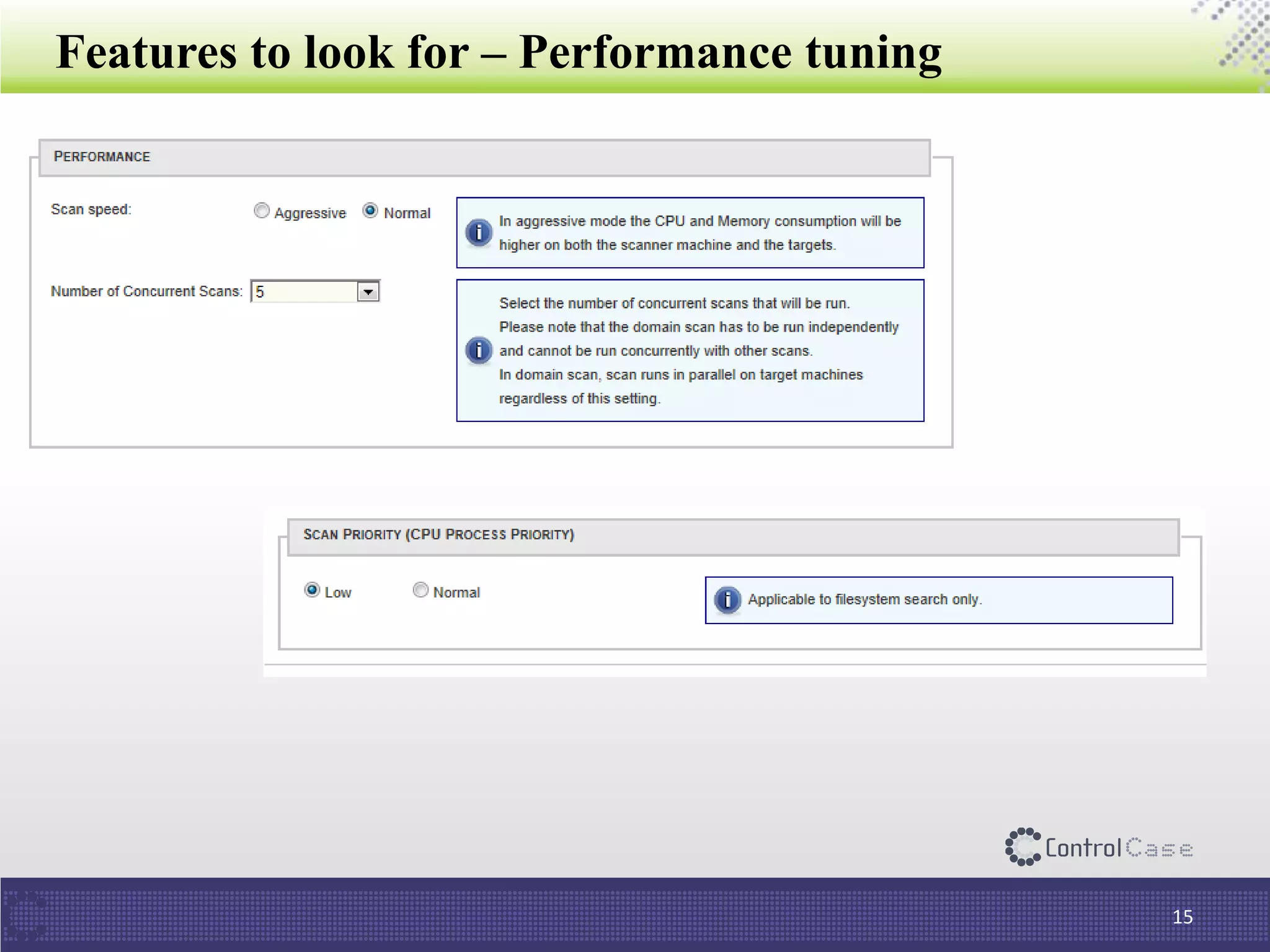
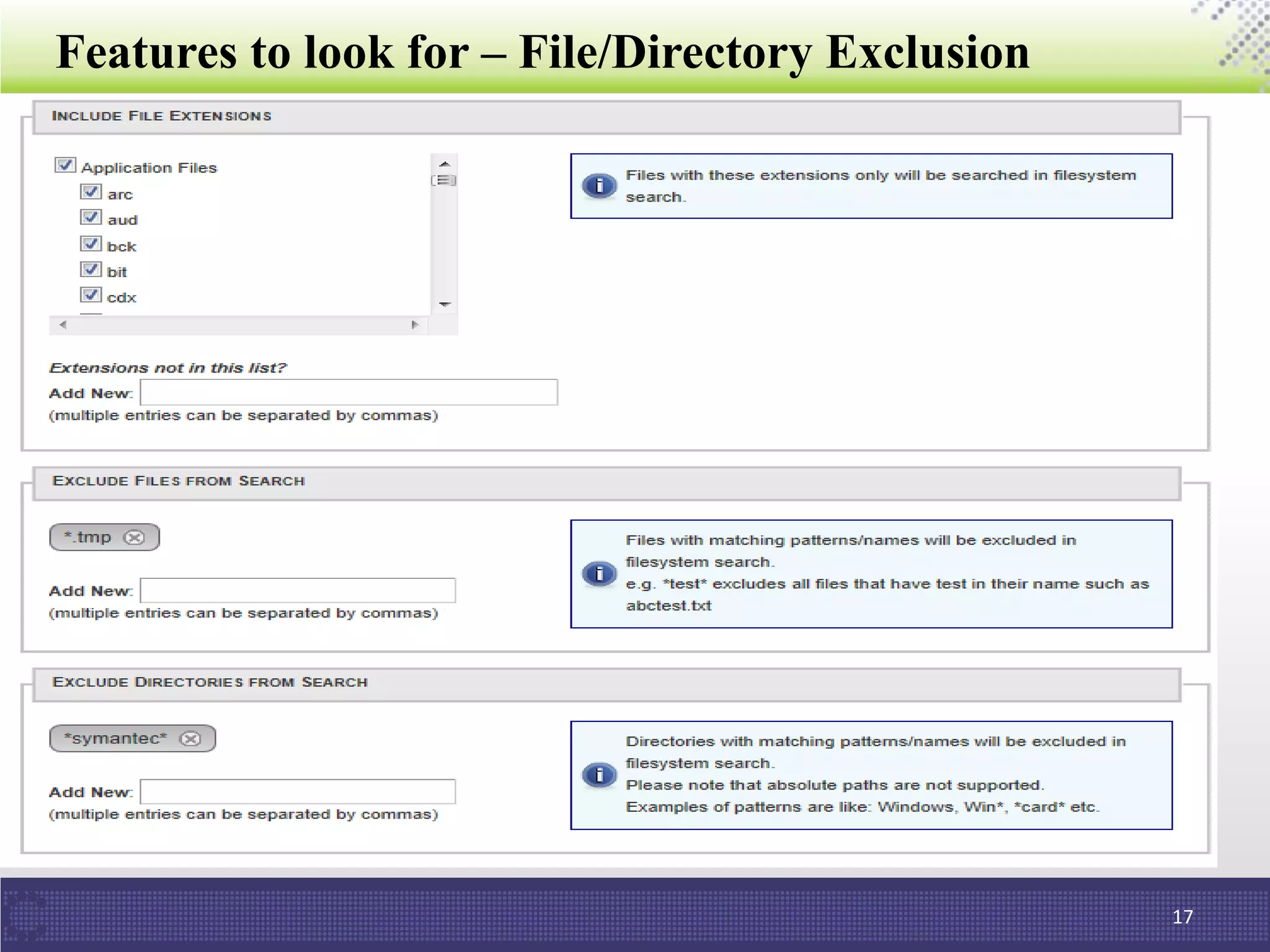
The document discusses the importance of data discovery in relation to PCI DSS requirements, highlighting the need to identify sensitive data for securing payment card information. It outlines PCI DSS guidelines and challenges in deploying data discovery technologies, such as false positives and performance issues. Additionally, the document promotes ControlCase's services and expertise in the field of data compliance and discovery.