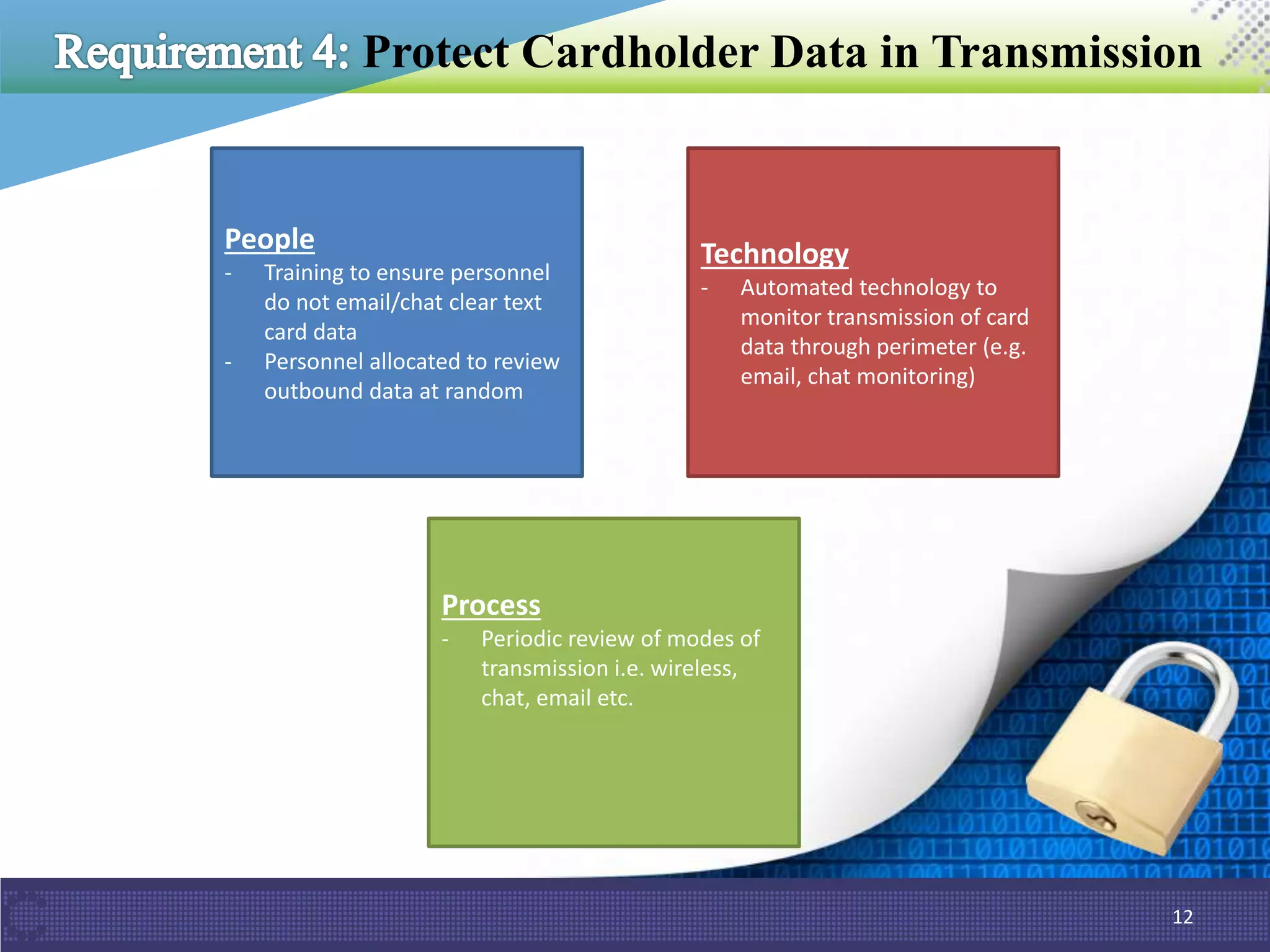
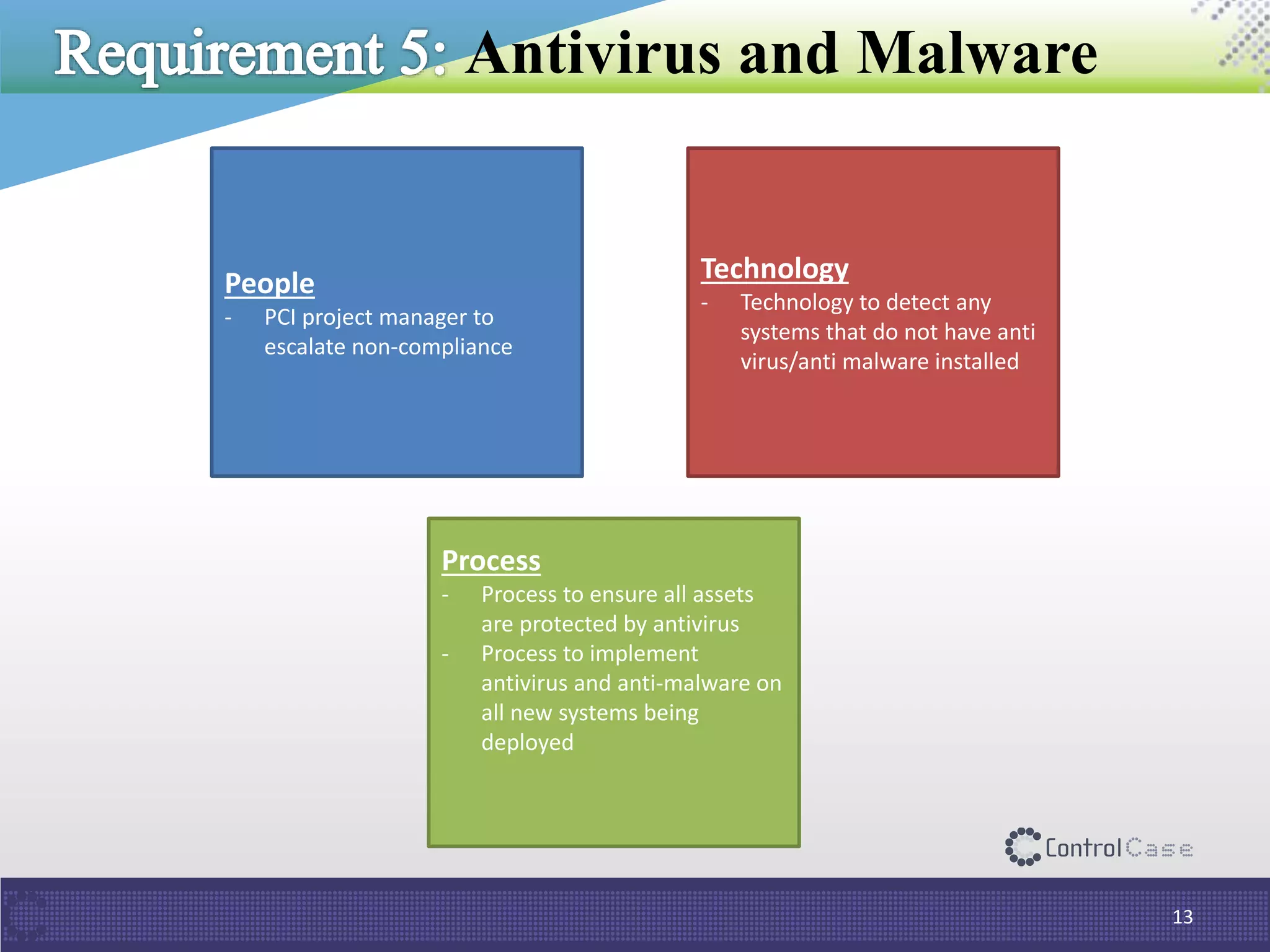
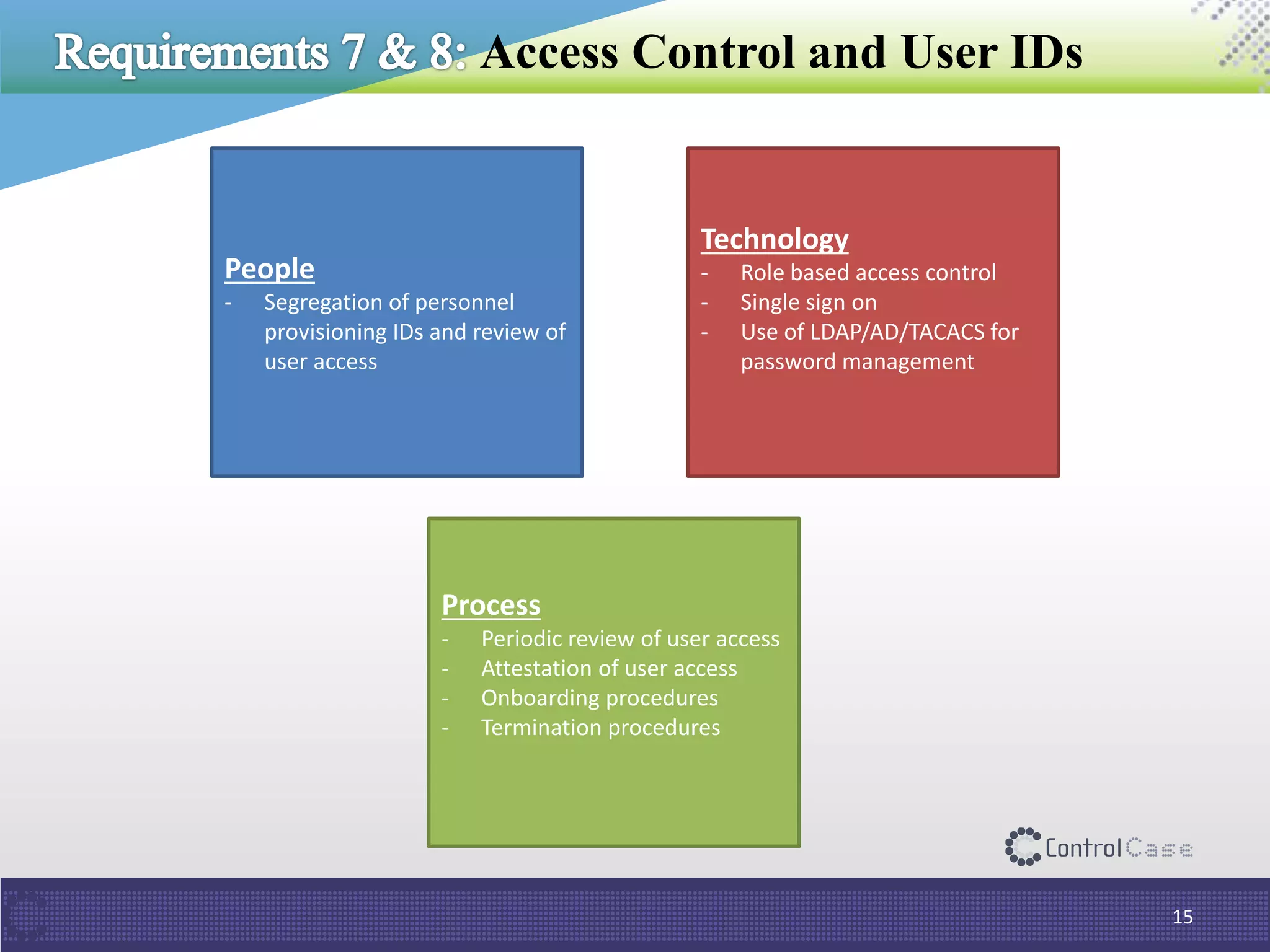
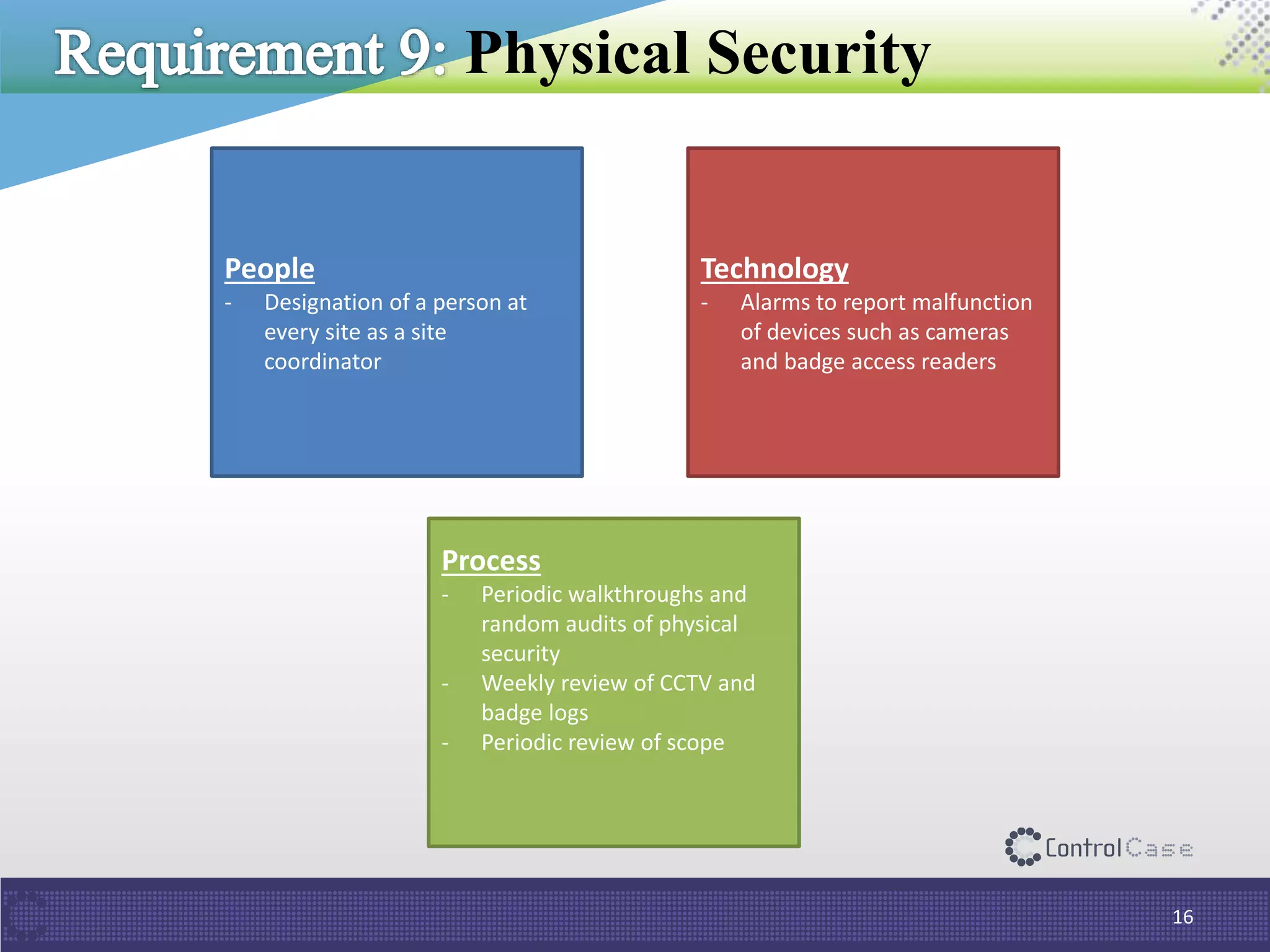
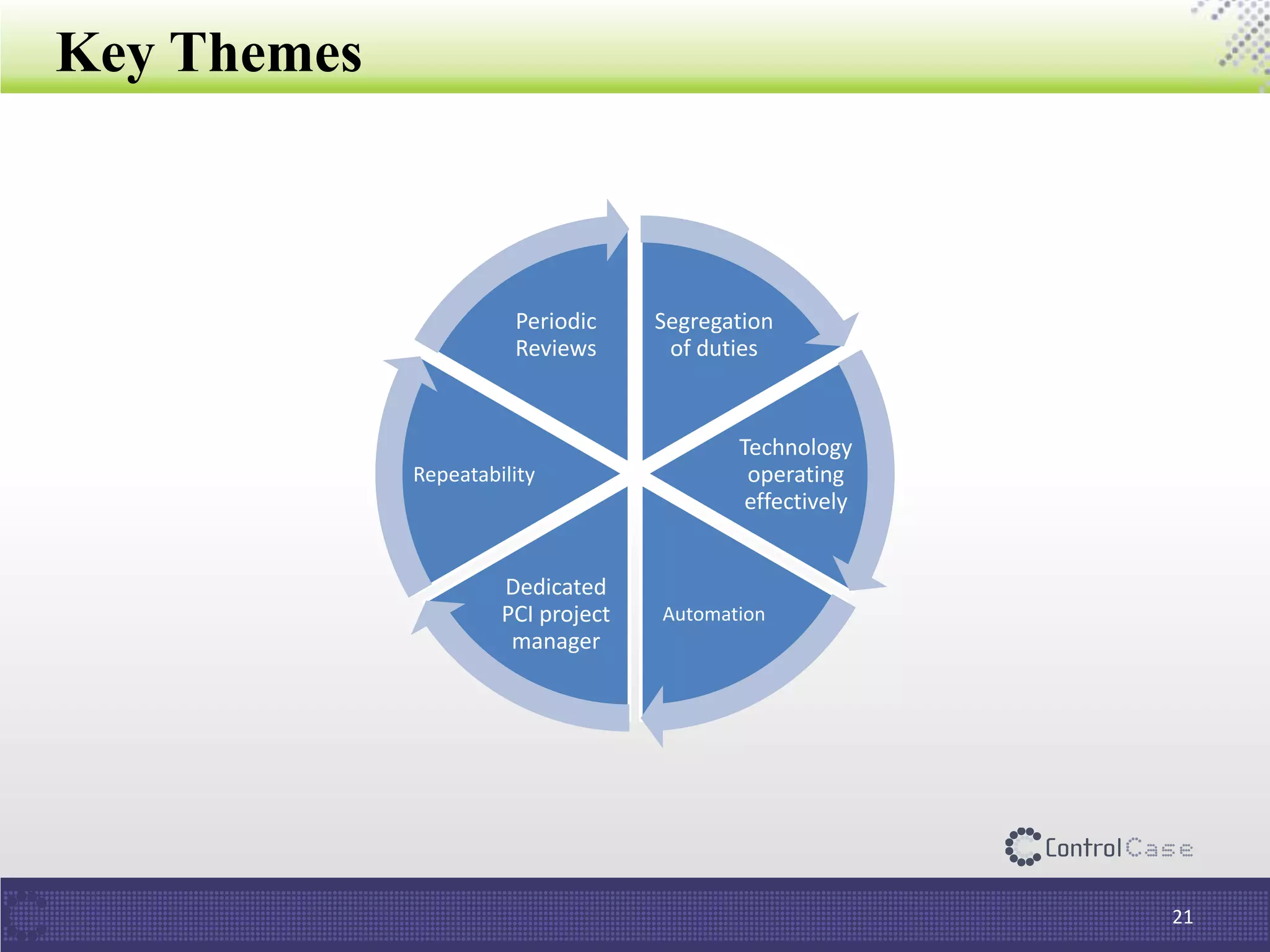
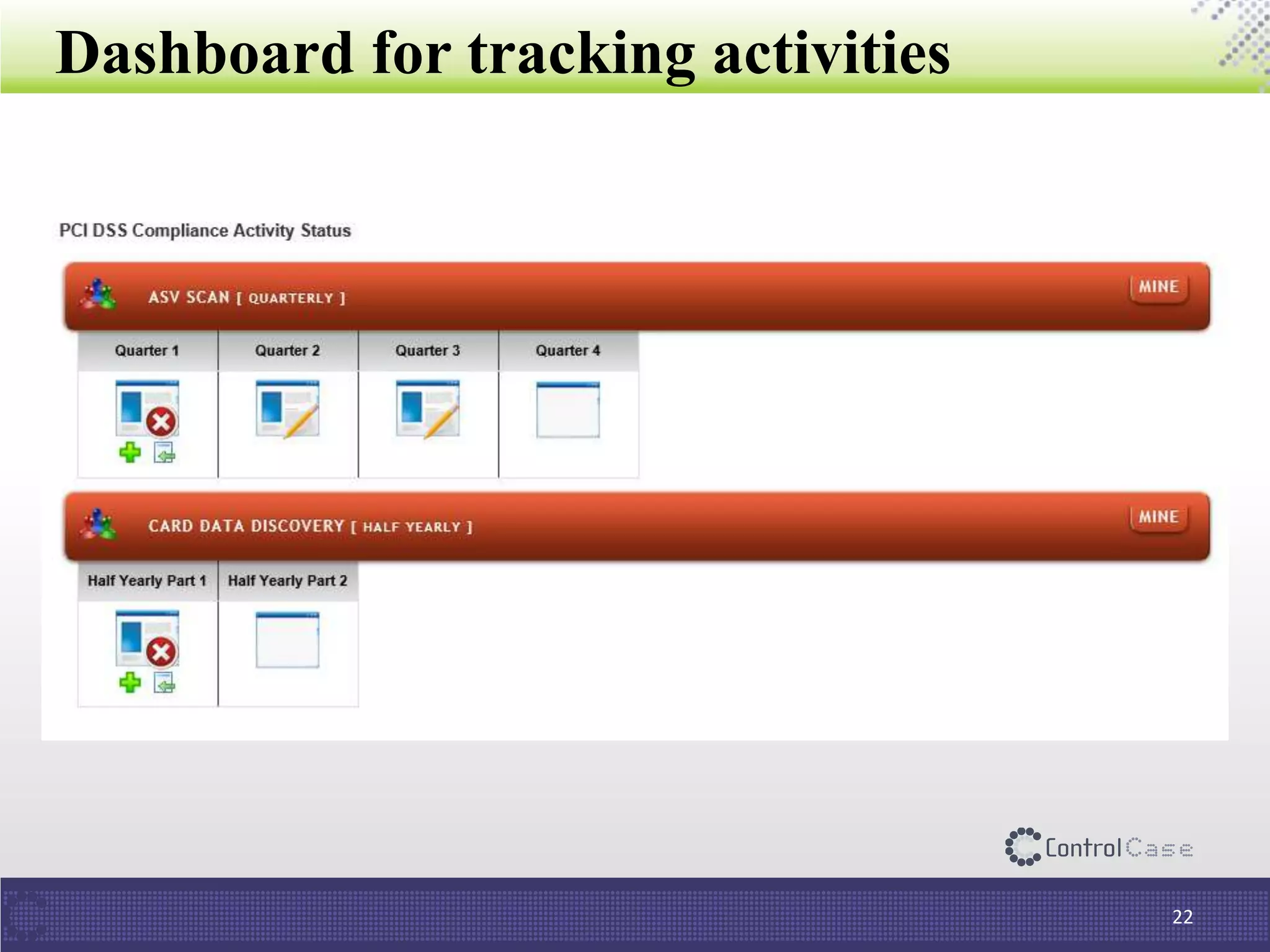
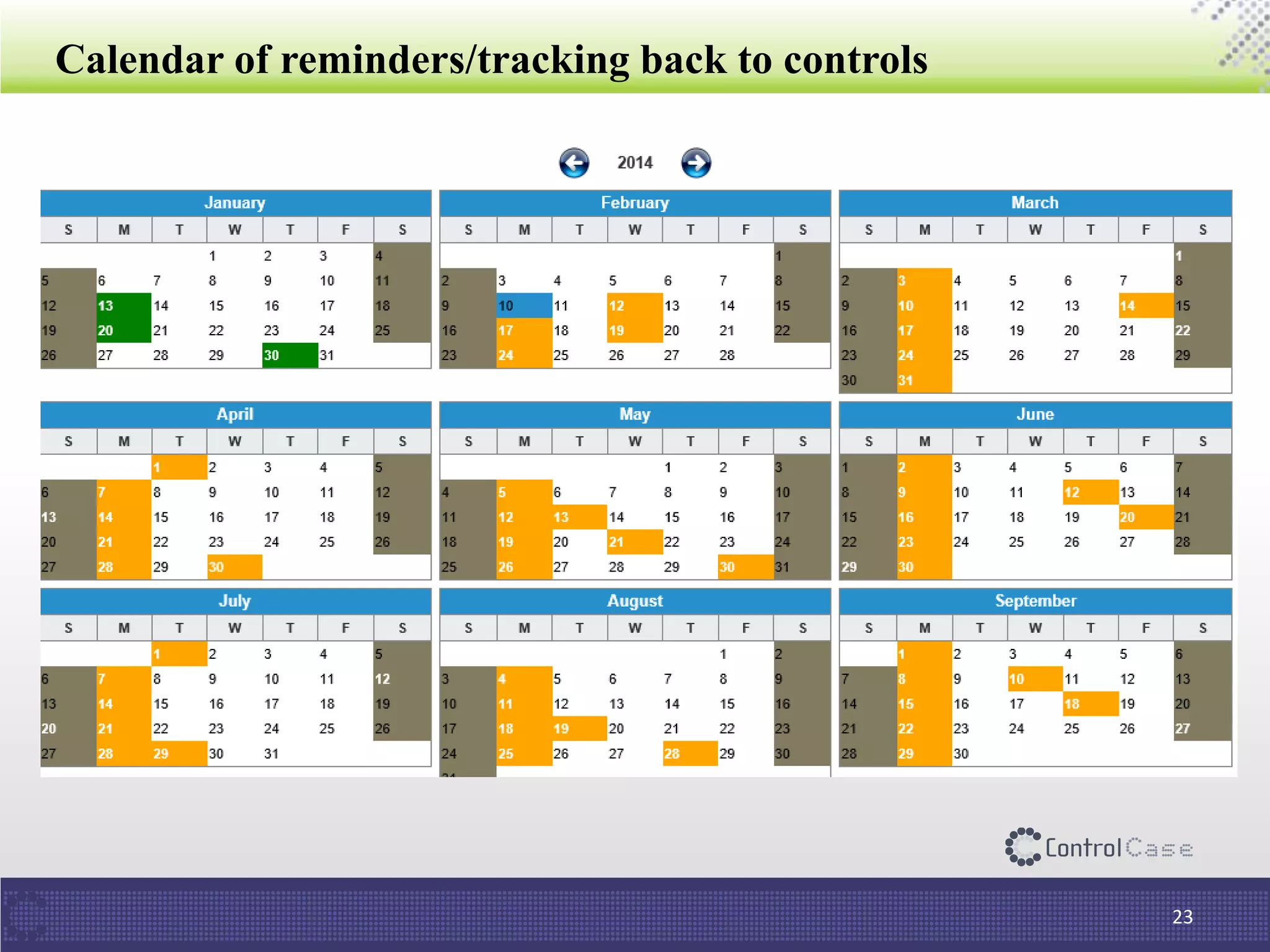
The document outlines PCI DSS 3.2, which establishes standards for securely processing, storing, and transmitting payment card data. Key changes include requirements for multi-factor authentication and the prohibition of SSL/early TLS after certain dates. It also discusses implementation tips and ControlCase solutions for maintaining compliance as a business-as-usual process.