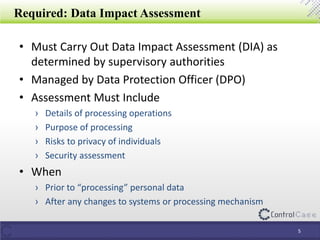
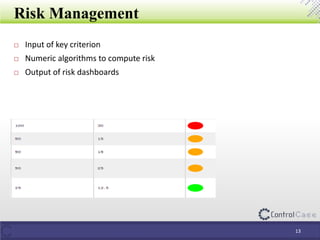
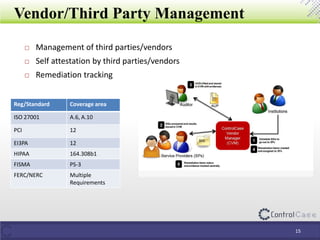
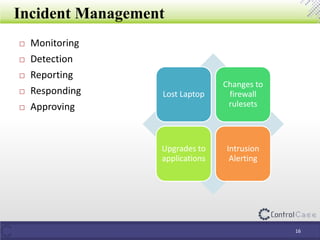
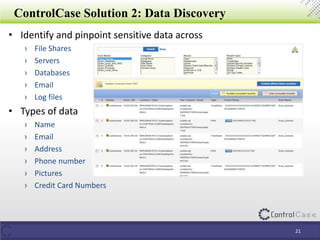
The document outlines the General Data Protection Regulation (GDPR) and its implications, including the definitions of data controllers and processors, compliance consequences for non-compliance, and the requirements for data impact assessments and data protection officers. It also details tactical steps for GDPR compliance, including security measures, rights management, and breach notification protocols. Controlcase offers solutions for GDPR compliance, including data impact assessments and data discovery services.