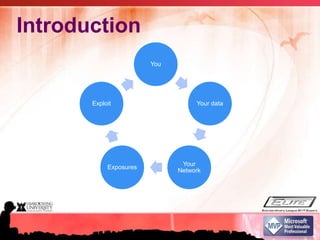
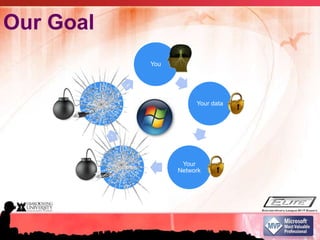
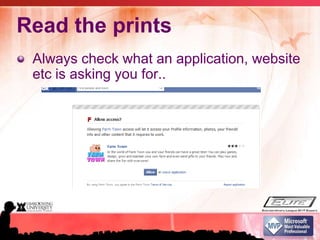
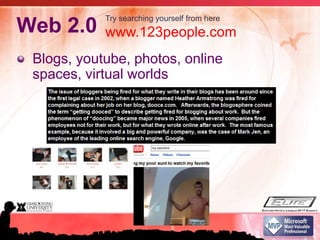
This document summarizes a presentation on information security and protecting privacy with Windows 7. It discusses why security is important, common security misconceptions like thinking antivirus is enough, emerging threats from social media and mobile devices, and how to strengthen security through practices like using strong passwords and keeping software updated. It also provides tips for securely using public networks and storing mobile data to help protect privacy and information.