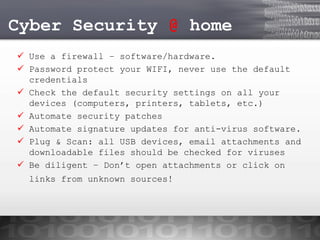
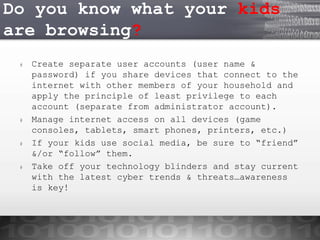
Patricia Watson, a digital forensics program manager, presented on cyber security threats. She discussed how the cyber landscape has changed with advances in technology and examples of common cyber crimes. Small and medium businesses often have a false sense of security, despite statistics showing they are vulnerable targets. Individuals can help mitigate risks at work by using strong passwords, encryption, locking devices, and being vigilant. The presentation concluded with tips for securing personal networks and devices at home.