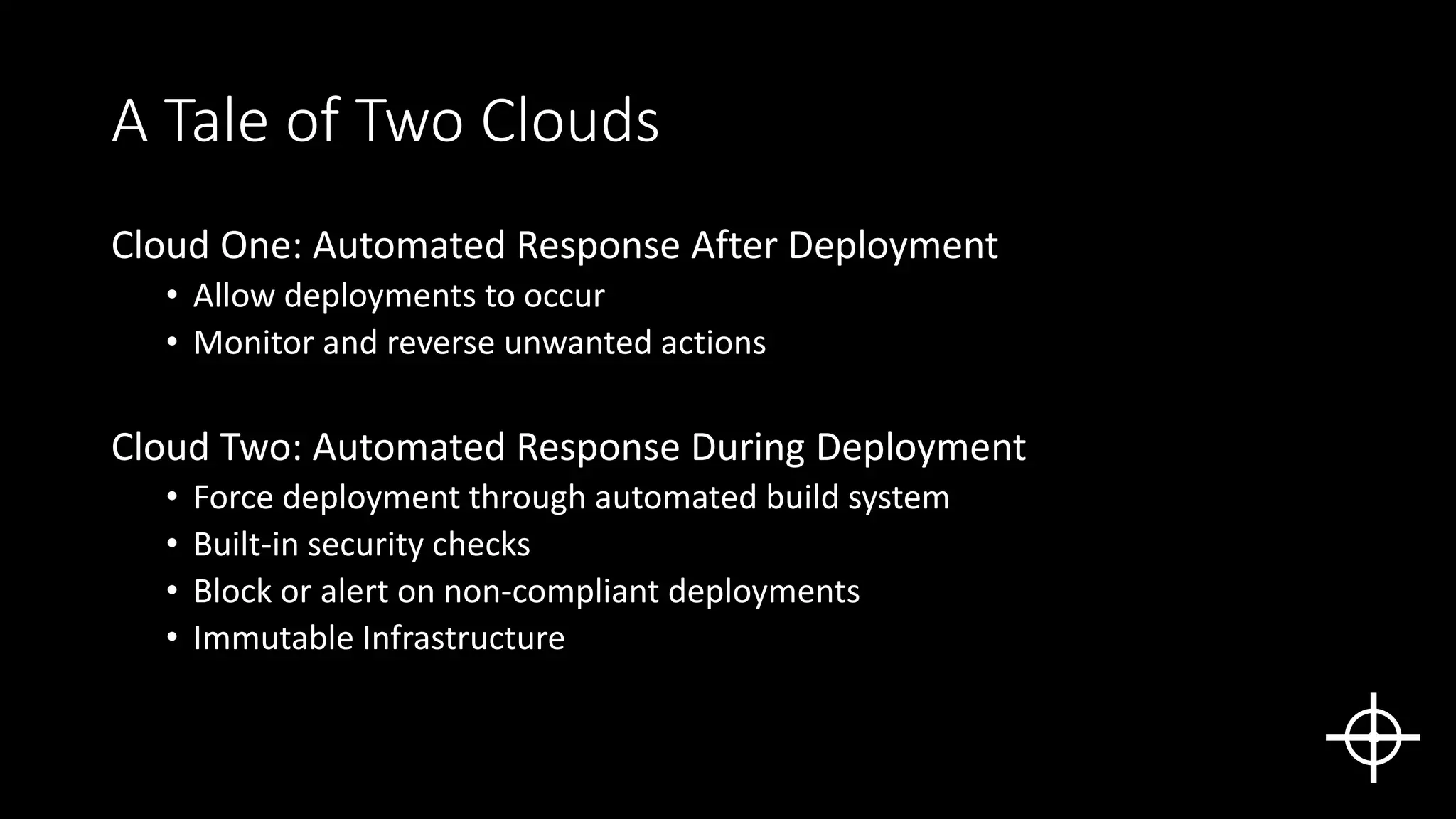
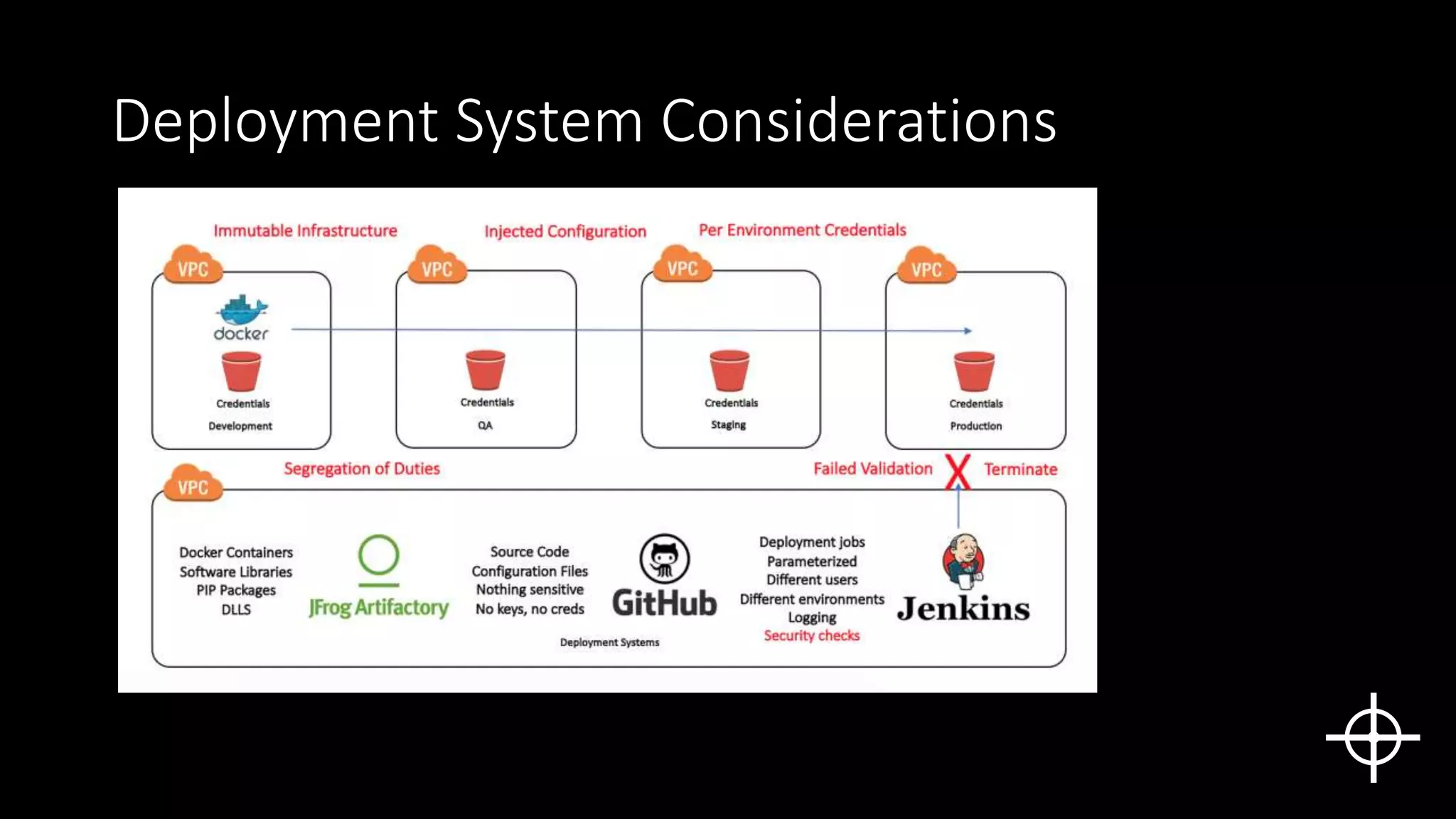
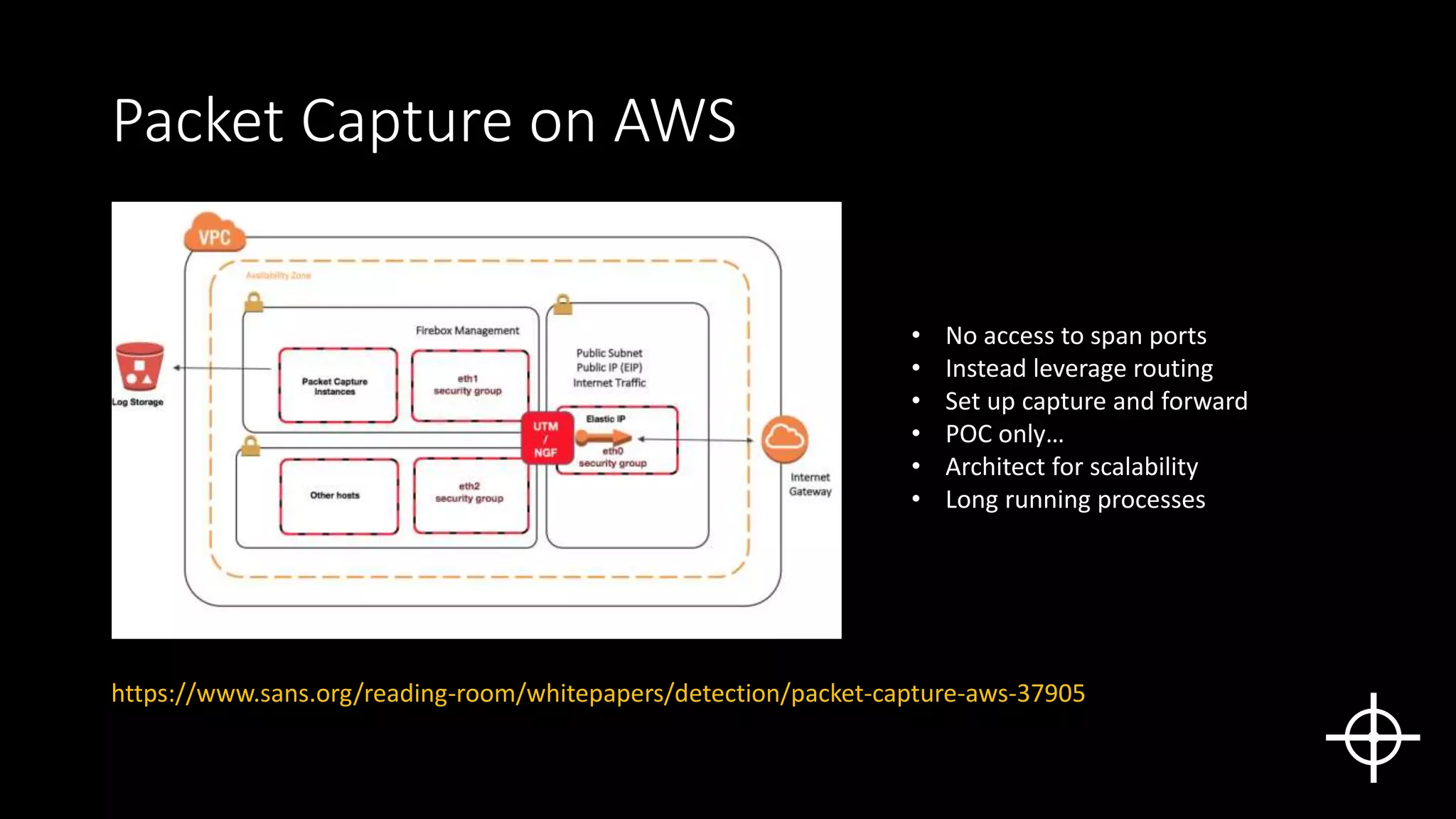
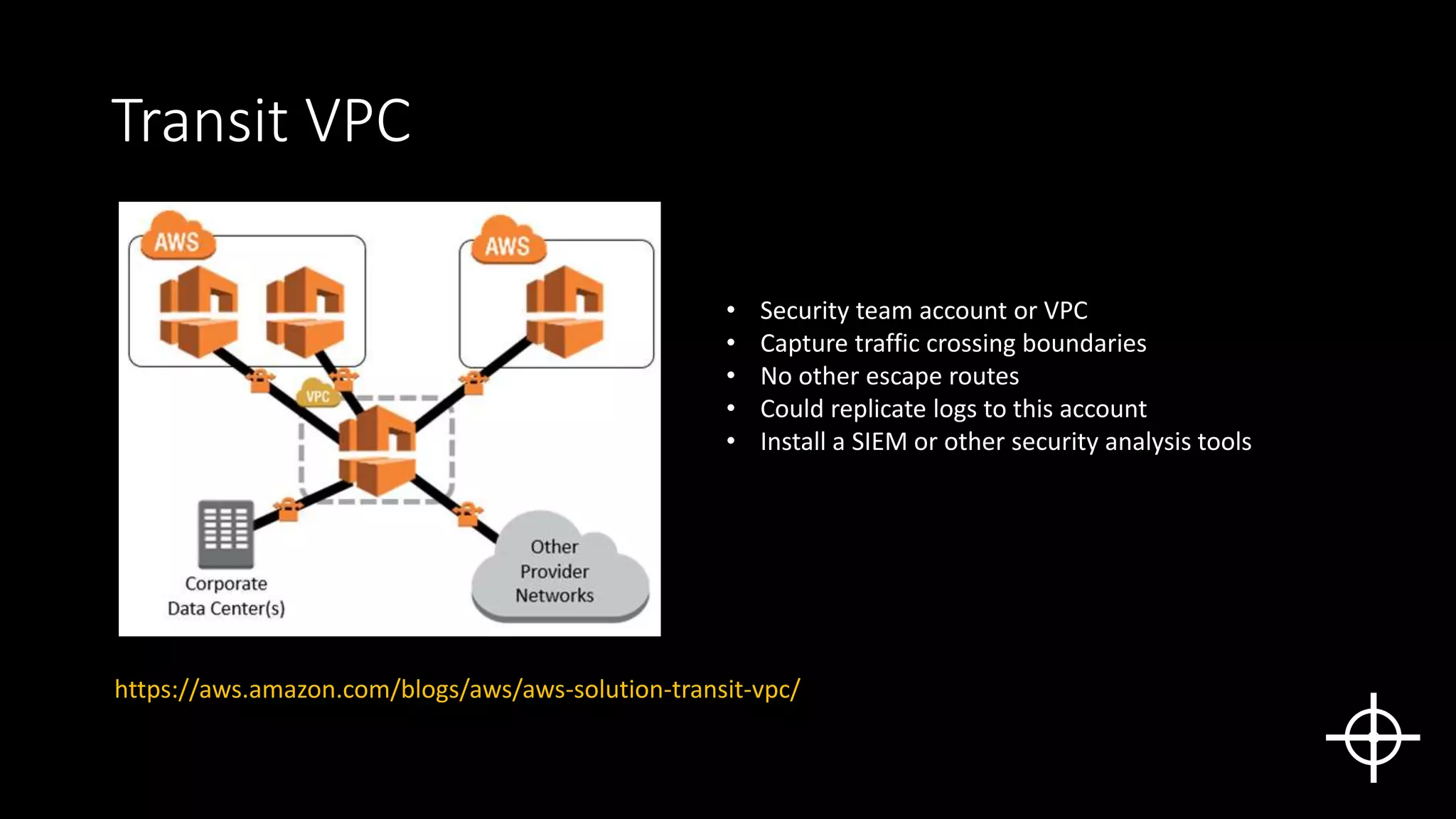
The document discusses securing deployments in the cloud through automated processes. It argues that manual security reviews of cloud deployments do not work and that organizations should instead implement immutable infrastructure with security checks built into automated deployment systems. This prevents insecure configurations and tracks all changes. The document outlines approaches like monitoring for unauthorized changes after deployment and blocking non-compliant deployments. While automated security has upfront costs, it helps reduce long-term costs from human errors and speeds issue resolution through prevention rather than rollback. Centralized logging and deployment tracking aids in security management and cost optimization.