This document discusses permissions and groups in Active Directory. It covers the different types of groups (distribution, security, etc.), and how a group's scope (domain local, global, universal) determines what objects it can include and what resources it can be assigned permissions for. The document also discusses domain and forest functional levels, inheritance and precedence of permissions, and how to use different types of groups effectively to structure access to resources.



![Domain Functional Levels[1]
• Limits what functionality domain controllers offer within the domain.
• All functional levels provide the default Active Directory Domain
Services feature set plus additional features depending on the operating
system.
Functional Level Features[1]
Windows 2000 Native Universal groups enabled for distribution and
Network Design & Administration
security groups; group nesting; group
conversion; SID history.
Windows Server 2003 Domain rename; last logon timestamp;
password setting on inetOrgPerson / User
objects; redirect users/computers containers;
authorisation manager policies; constrained
delegation; selective authorisation.
Windows Server 2008 Distributed File System replication of SYSVOL;
Advanced Encryption Services for Kerberos;
interactive logon info; fine-grained password 4
policies
Windows Server 2008 R2 Active Directory domain recycle bin.](https://image.slidesharecdn.com/lecture8-permissions-130204184329-phpapp01/75/Lecture-8-permissions-4-2048.jpg)
![Forest Functional Levels[1]
• Functional levels impact the forest functional level.
• Each Server version adds more features to basic forest
functionality.
Forest Functional Level Features[1]
Network Design & Administration
Windows 2000 Default AD feature set
Windows Server 2003 Forest trust; domain rename; linked value
replication; Read-only domain controllers
(RODC); improved knowledge consistency
checker; dynamic objects;
deactivation/redefinition of attributes and
classes in schema.
Windows Server 2008 No additional forest level features; will default
to a Server 2008 FL instead of a 2003 FL. 5
Windows Server 2008 R2](https://image.slidesharecdn.com/lecture8-permissions-130204184329-phpapp01/75/Lecture-8-permissions-5-2048.jpg)
![Group Scope Revisited![2]
• Scope can be domain local, global, or universal.
Group Scope Group Membership Can Include[2] Can be used to [2]
Domain Local User accounts from any domain in the Assign access to resources
forest; global groups or universal groups only in the local domain; on
from any domain in the forest; user all servers in domain
Network Design & Administration
accounts or global or universal groups running Windows Server
from any domain in trusted forest; 2000/2003/2008.
nested domain local groups from the
local domain.
Global User accounts from the domain where Assign access to resources in
the group is created; nested global all domains in forest or
groups from the local domain. between trusted forests;
member servers running
Windows Server.
Universal User accounts from any domain in Assign access to resources in 6
forest; global groups from any domain all domains in forest or
in forest; nested universal groups from between trusted forests; on
any domain in forest. all servers running 2000 +](https://image.slidesharecdn.com/lecture8-permissions-130204184329-phpapp01/75/Lecture-8-permissions-6-2048.jpg)






![Access Control Lists (ACL)
• An Access Control List is associated to an object being accessed, not
the object accessing it.
• Lists all permissions that can access that object. (e.g. users, groups,
etc.)
• Also lists what operations can be done to the object.
Network Design & Administration
• List made out of Access Control Entries (ACE’s) (i.e. the name of the
security principle and the permissions it has been granted)
• Example:
/home/cmp3robinj/
[ACL] Access Control Entry
(cmp3robinj, read)
(cmp3robinj, write)
(cmp3robinj, create)
(cmp3robinj, delete)
13
(admins, read)
(admins, write)](https://image.slidesharecdn.com/lecture8-permissions-130204184329-phpapp01/75/Lecture-8-permissions-13-2048.jpg)



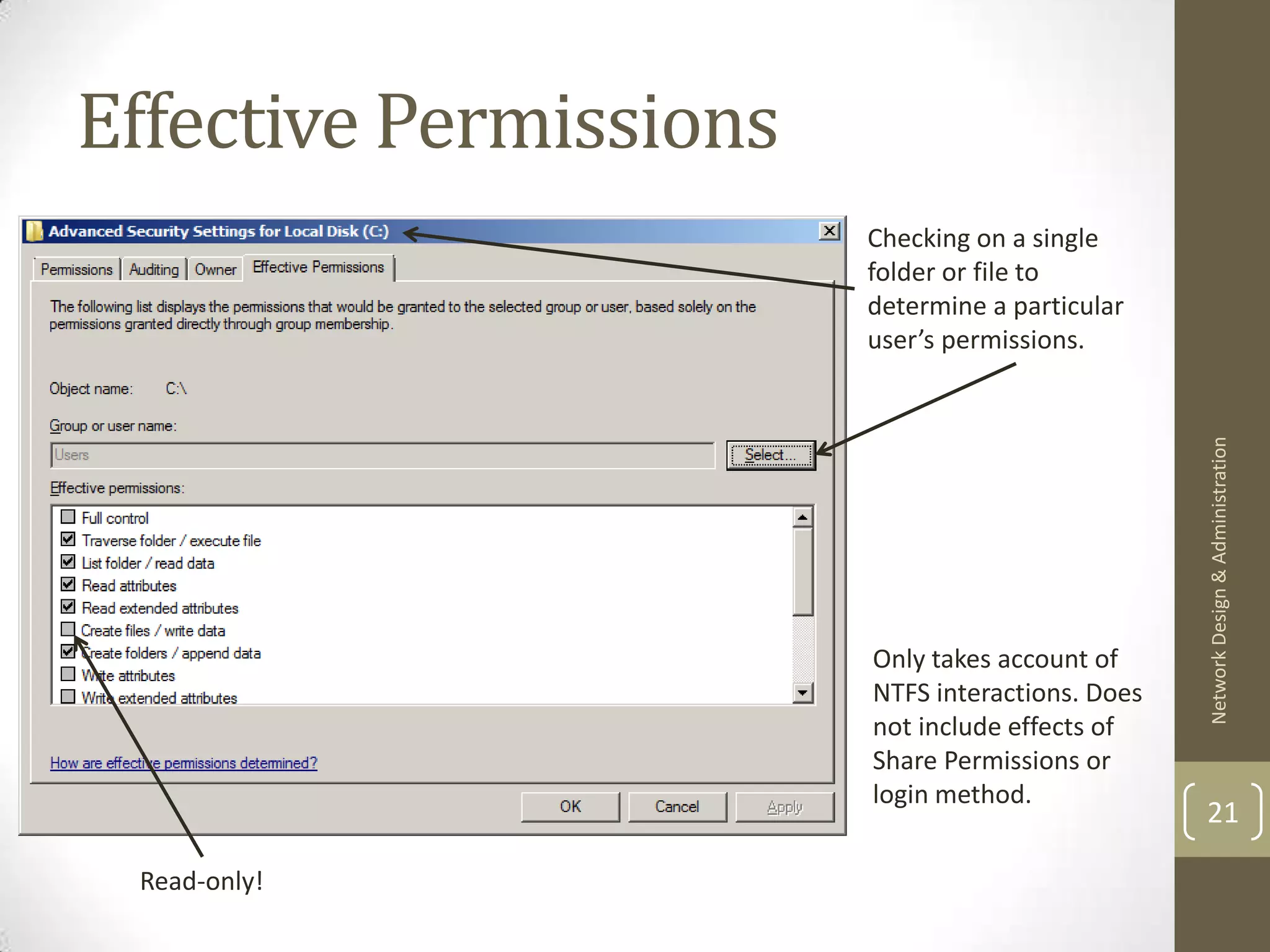
![Next time & References
• Further different sorts of permissions – including file shares.
[1] Windows Server 2008 Active Directory Resource Kit, page 181-
Network Design & Administration
[2] Windows Server 2008 Active Directory Resource Kit, page 368-
369
22](https://image.slidesharecdn.com/lecture8-permissions-130204184329-phpapp01/75/Lecture-8-permissions-22-2048.jpg)